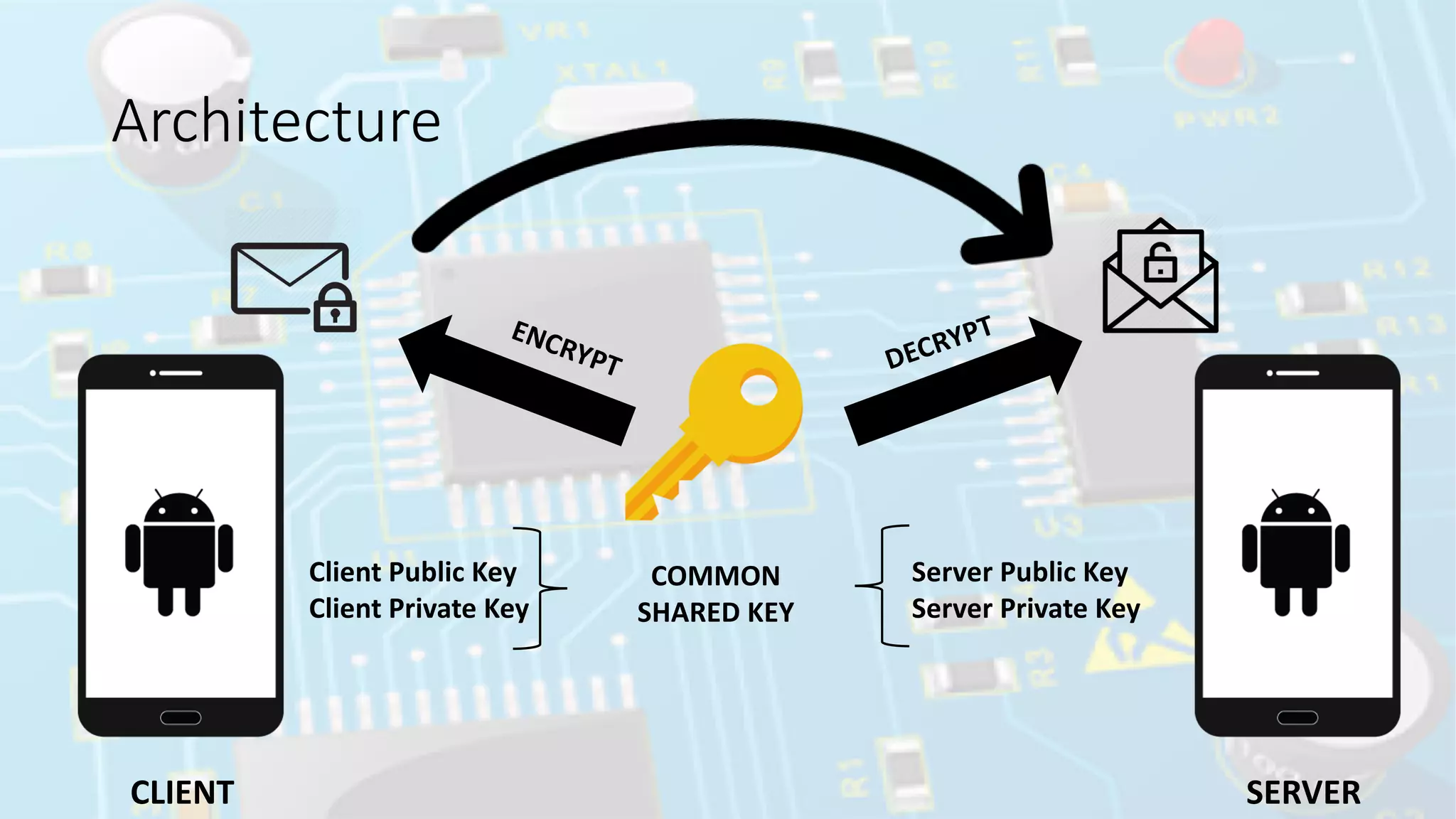
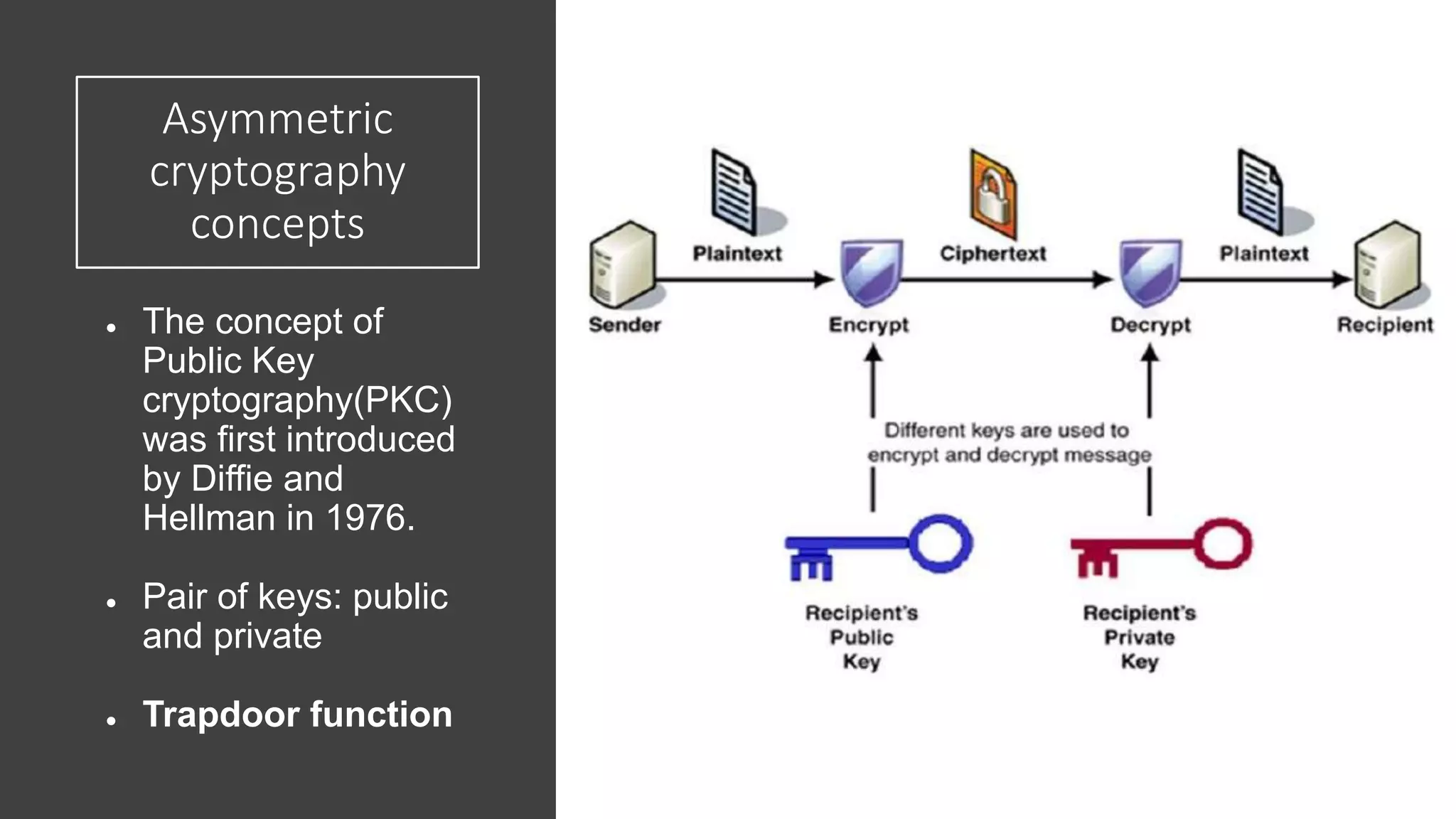
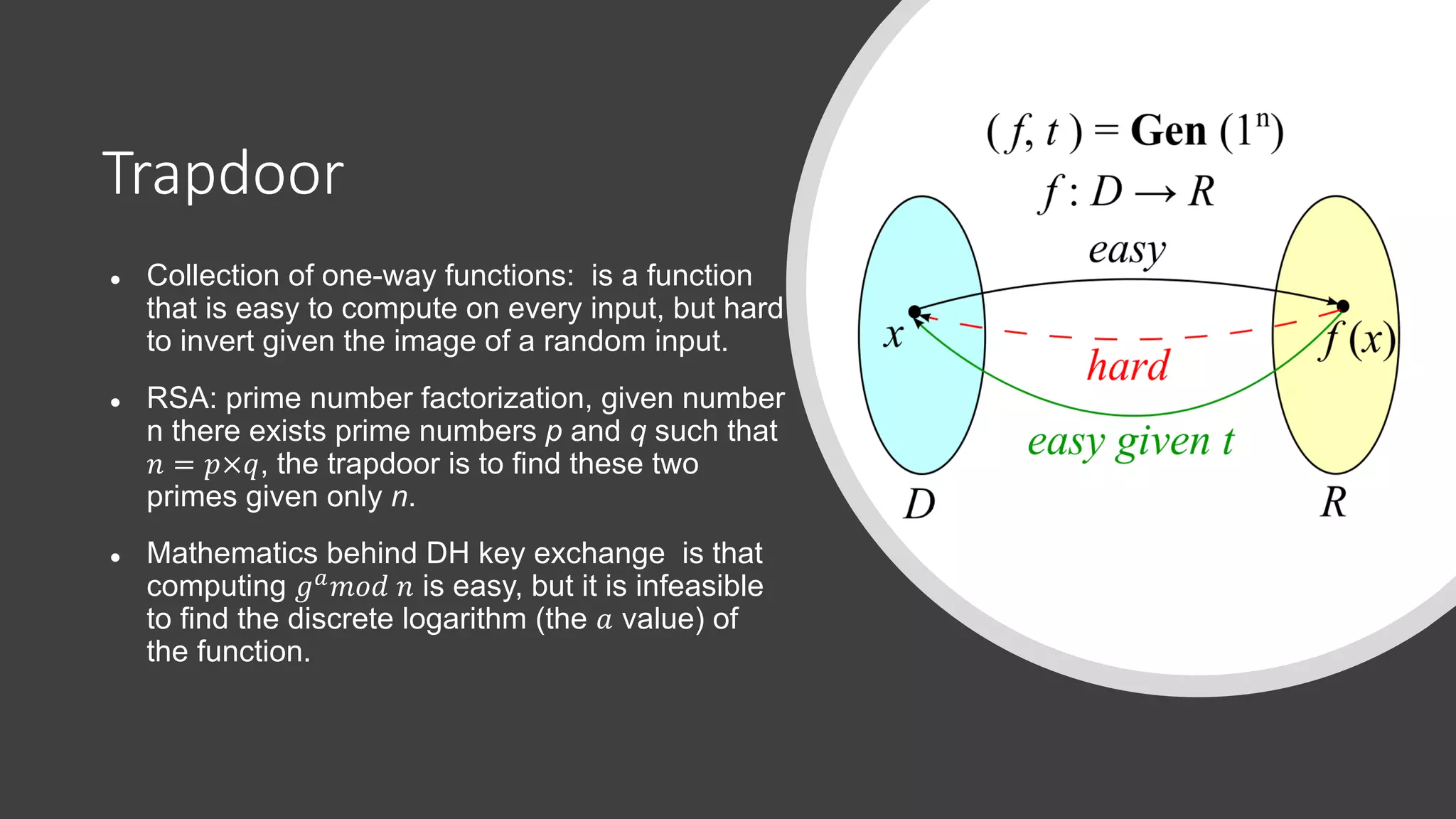
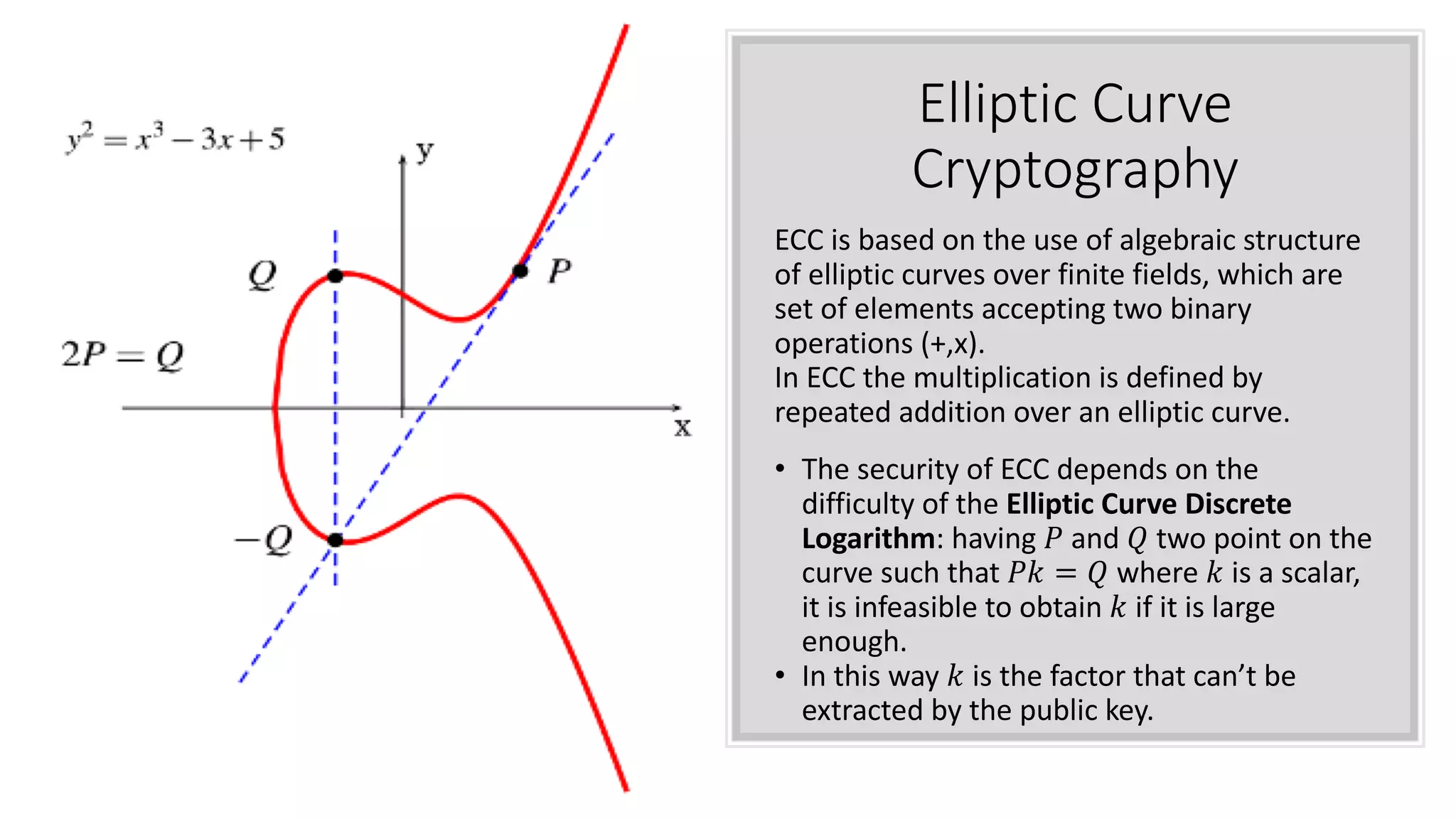
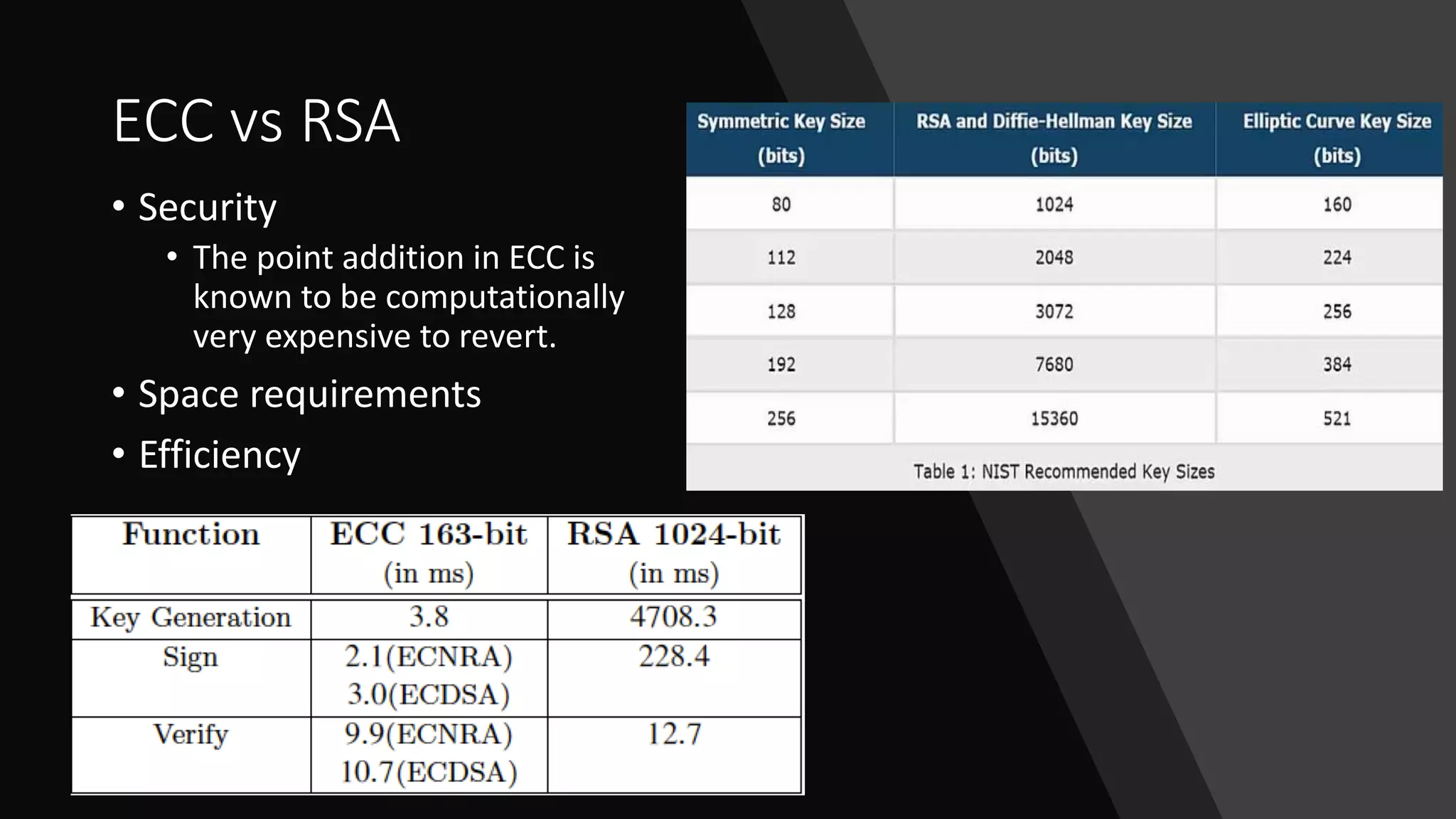
The document discusses elliptic curve cryptography (ECC), an approach to public-key cryptography based on the discrete logarithm problem of elliptic curves over finite fields, introduced by Neal Koblitz and Victor Miller in 1985. It compares ECC to RSA in terms of security and efficiency, highlighting how ECC's security relies on the difficulty of operations involving elliptic curves. The implementation details for a native Android library for Diffie-Hellman key exchange using ECC are provided, along with the current hesitance in the crypto community to fully trust and implement ECC compared to RSA.


![ECDH-Curve25519-Mobile
Implements Diffie-Hellman
key exchange based on the
Elliptic Curve 25519 for
Android devices.
It is a native Android library
since NaCl is implemented in
C rather than Java. However,
it can be easily compiled for
all Android platforms like
ARM or x86, so this is not a
practical limitation compared
to a Java implementation.
// Create Alice's secret key from a big random number.
SecureRandom random = new SecureRandom();
byte[] alice_secret_key = ECDHCurve25519.generate_secret_key(random);
// Create Alice's public key.
byte[] alice_public_key =ECDHCurve25519.generate_public_key(alice_secret_key);
// Bob is also calculating a key pair.
byte[] bob_secret_key = ECDHCurve25519.generate_secret_key(random);
byte[] bob_public_key = ECDHCurve25519.generate_public_key(bob_secret_key);
// Assume that Alice and Bob have exchanged their public keys.
// Alice is calculating the shared secret.
byte[] alice_shared_secret = ECDHCurve25519.generate_shared_secret(
alice_secret_key, bob_public_key);
// Bob is also calculating the shared secret.
byte[] bob_shared_secret = ECDHCurve25519.generate_shared_secret (
bob_secret_key, alice_public_key);
https://github.com/duerrfk/ecdh-curve25519-mobile](https://image.slidesharecdn.com/ecc-180531085725/75/Elliptic-Curve-Cryptography-Message-Exchange-9-2048.jpg)