The document presents an introductory presentation on implementing elliptic curve cryptography for data security. It discusses how ECC offers strong security with shorter key lengths and efficient computation. It outlines the objectives of understanding ECC basics, choosing an appropriate programming language and library, and implementing key generation, encryption, and decryption algorithms. It includes block diagrams, flow charts, and details on the methodology, advantages, applications, and references.
![VISVESVARAYA TECHNOLOGICAL UNIVERSITY
BELAGAVI, KARNATAKA – 590018
Main-Project[Phase -1]
Introductory Presentation on
“Implementation of Elliptic Curve Cryptography for data security”
By:
MOUNESH GOWDA R 4HG20EC020
PALLAVI J 4HG21EC412
RADHA K.S 4HG21EC416
SWATHI S.S 4HG21EC426
Under the guidance of:
Dr. Baby H T
Associate Professor and Head
Department of Electronics and Communication Engineering
Government Engineering College
Mosalehosahalli - 573212
Dept of E&CE, GECM](https://image.slidesharecdn.com/team3mainprojectphase12-240410141051-21c78ebd/75/Eliptic-Curve-cryptography-based-on-image-1-2048.jpg)





![Generation of ECC points.
Dept of E&CE, GECM
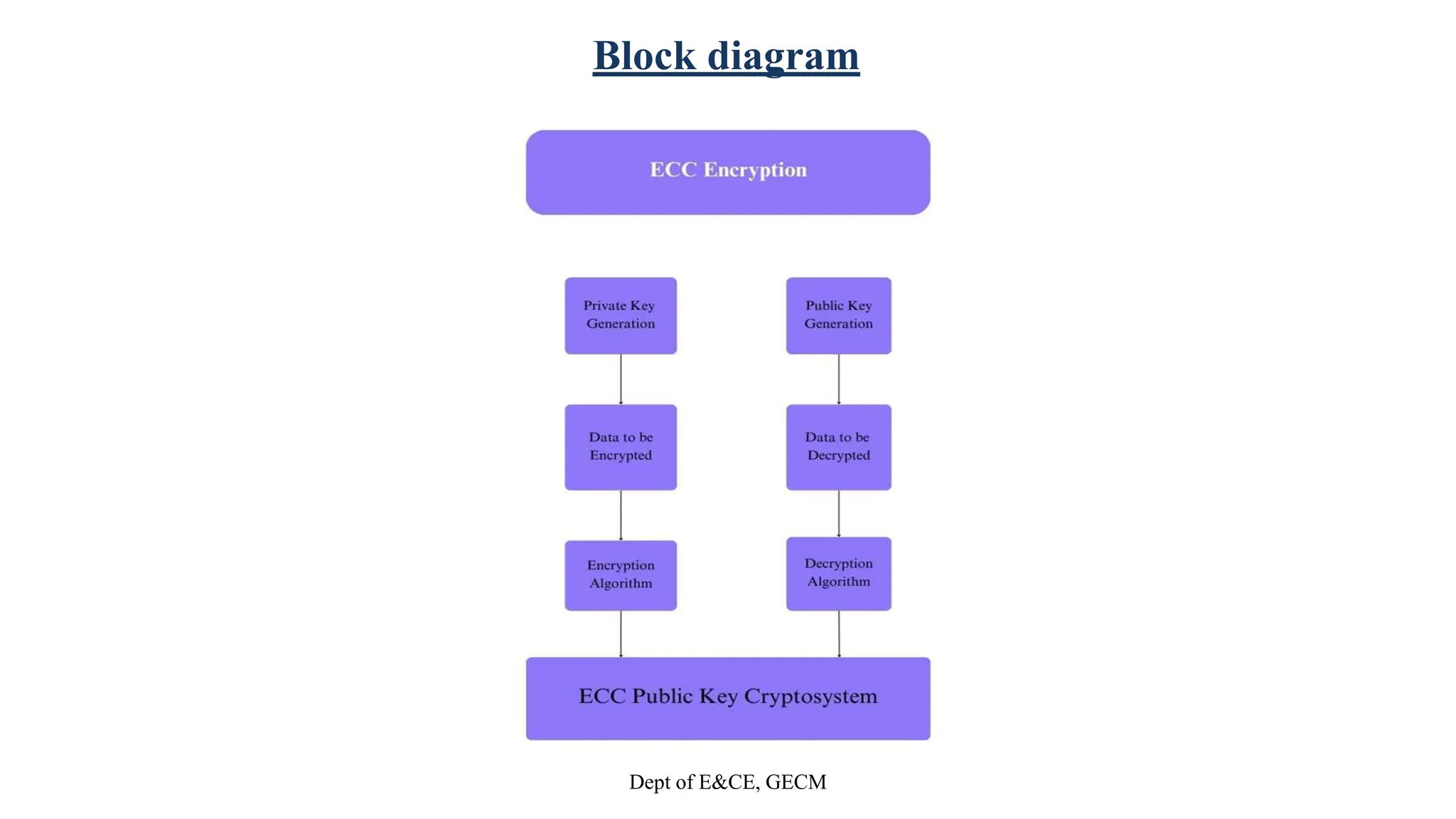
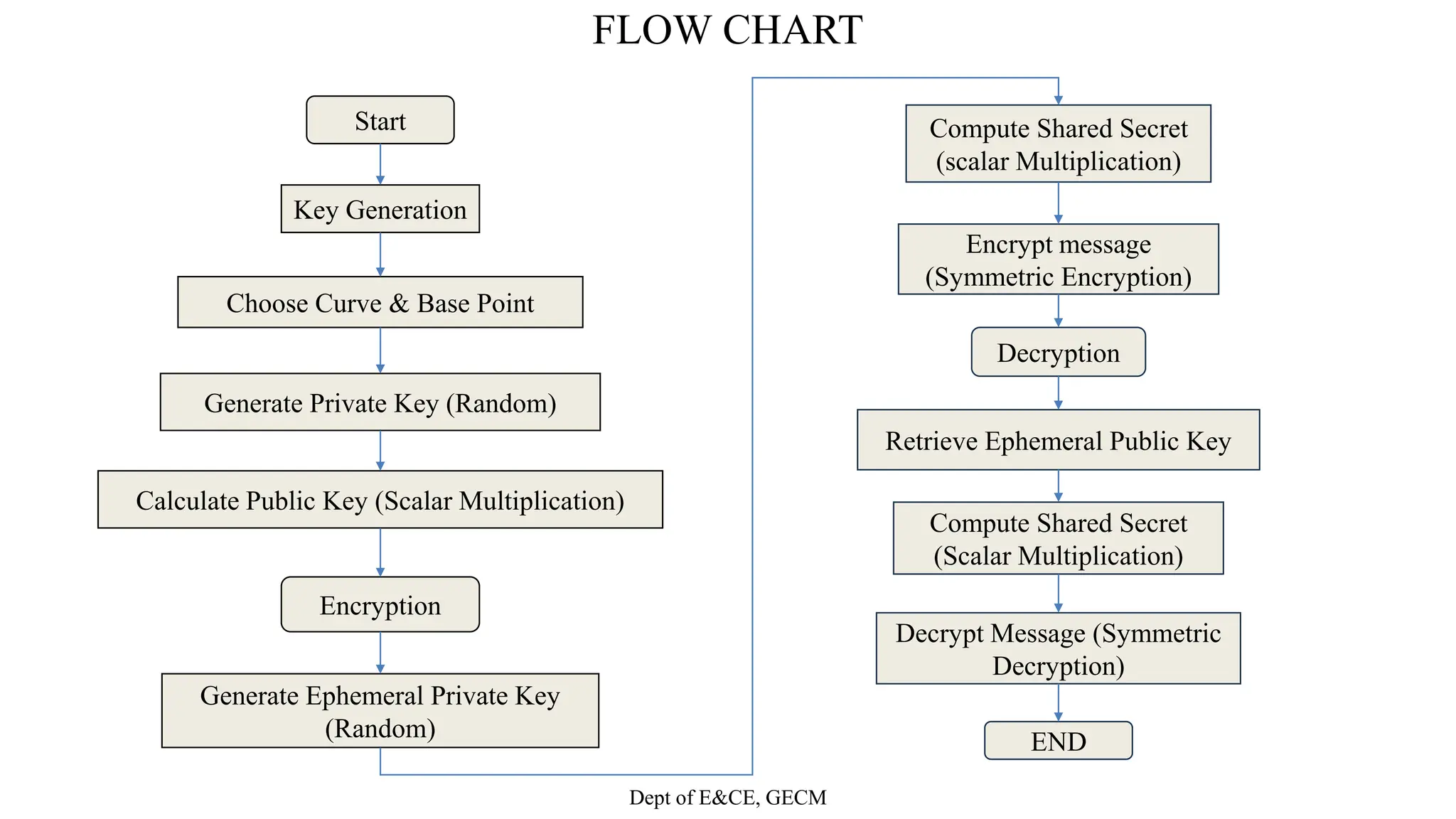
• Select (a and b)
• Eq (a,b) is of Elliptic Curve with parameters a,b&q. where q is the
prime or an integer of the term 2m
• User A key generation
Select private nA nA<n
Calculate Public PA=nAλG
• User B Key Generation
Select Private nB nB<n
Calculate Public PB PB=nBxG
Check the condition
• At the transmitter side
User A collects Public Key of User B
i.e PB,choose random +we integer k
Cm=[KG,Pm+kPB]
where Cm = Cipher text
Pm = Plain text
• At the Receiver side
User B decrypts using its Private Key nB
i.e Pm+KPb – nB(kg) = Plain text Pm
Equation
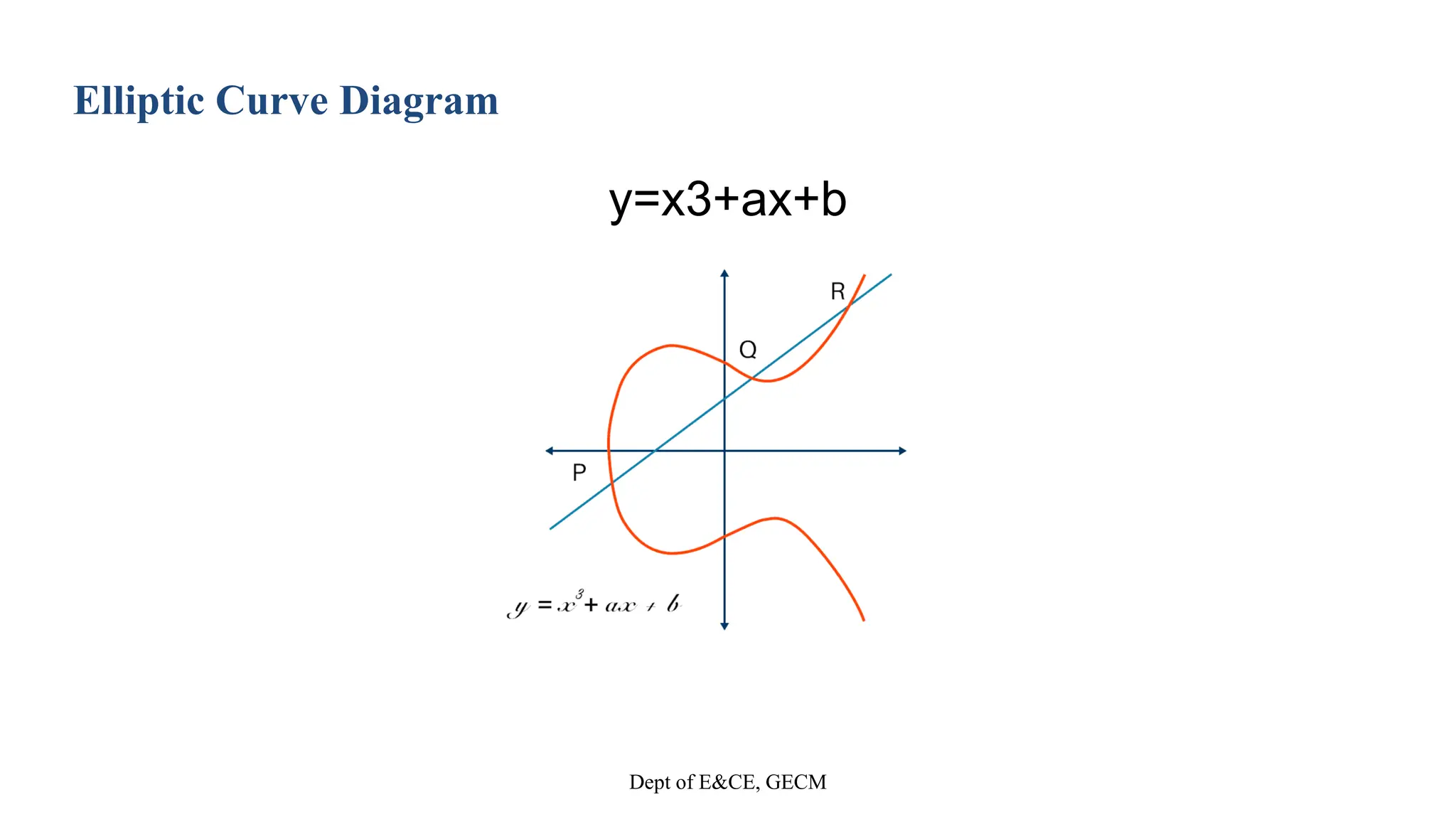
y² = x³+ax+b](https://image.slidesharecdn.com/team3mainprojectphase12-240410141051-21c78ebd/75/Eliptic-Curve-cryptography-based-on-image-12-2048.jpg)



![REFRENCES
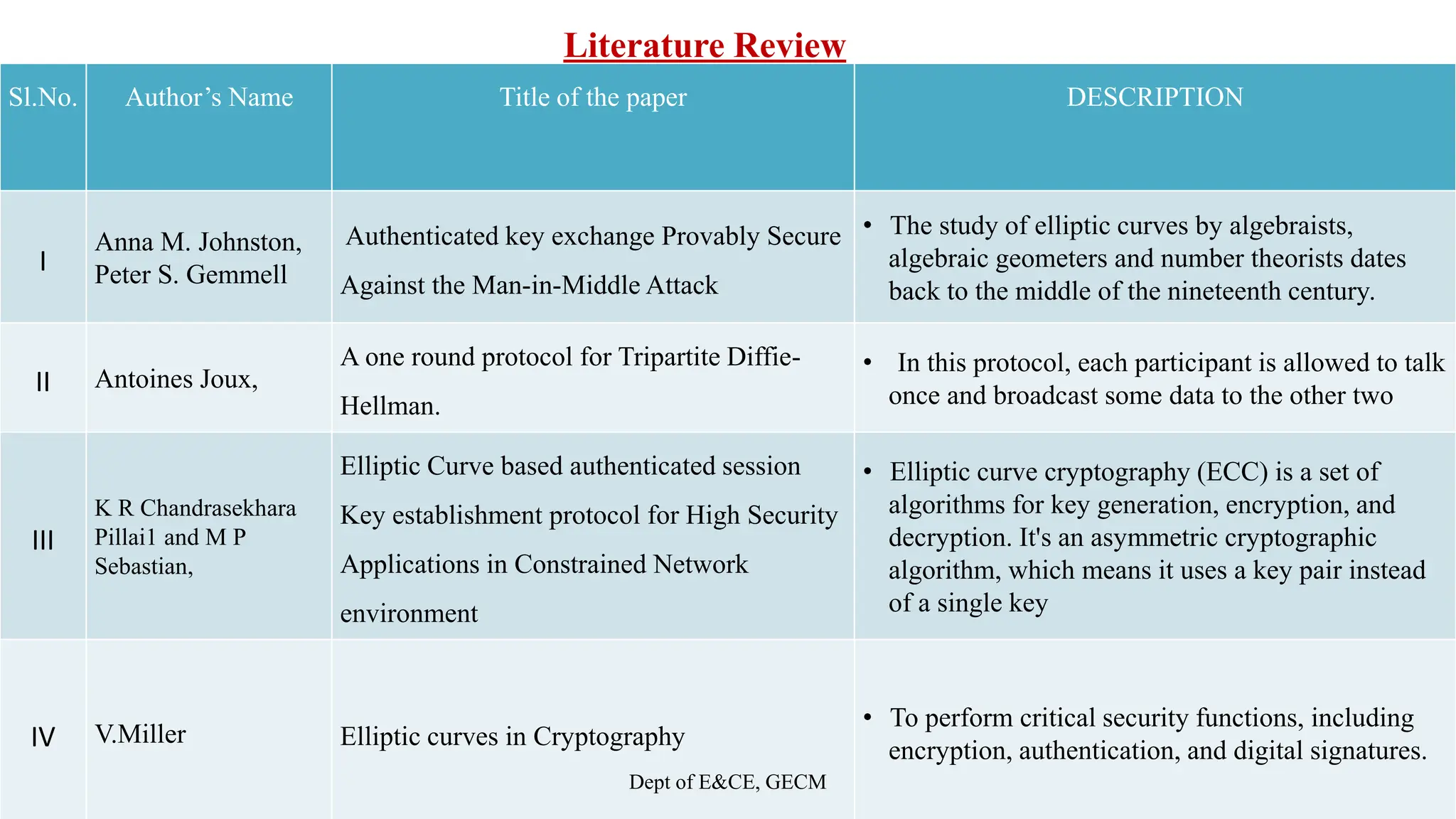
[1]. Anna M. Johnston, Peter S. Gemmell, “Authenticated key exchange Provably Secure Against the
Man-in-Middle Attack”, Journal of Cryptology (2002) Vol. number 2 pages 139-148.
[2]. Antoines Joux, “A one round protocol for Tripartite Diffie-Hellman”, Journal of Cryptology,
2004, Volume 17, Number 4,pages 263-276.
[3].K R Chandrasekhara Pillai1 and M P Sebastian, “Elliptic Curve based authenticated session Key
establishment protocol for High Security Applications in Constrained Network environment”
International Journal of Network Security & its Applications (IJNSA), Vol.2, No.3, July 2010.
[4]. V.Miller, “Uses of Elliptic curves in Cryptography”.In advances in Cryptography
(CRYPTO 1985), Springer LNCS 218,417-4 26, 1985.
Dept of E&CE, GECM](https://image.slidesharecdn.com/team3mainprojectphase12-240410141051-21c78ebd/75/Eliptic-Curve-cryptography-based-on-image-17-2048.jpg)
