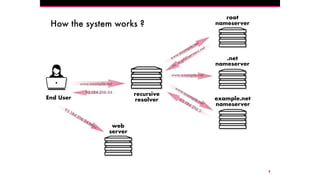
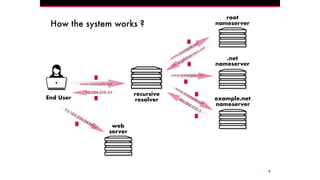
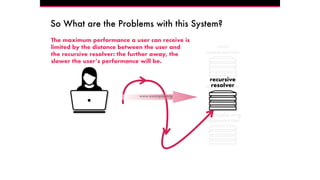
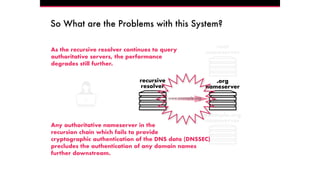
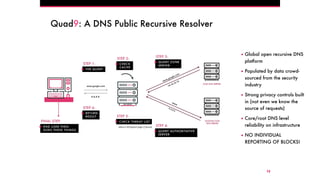
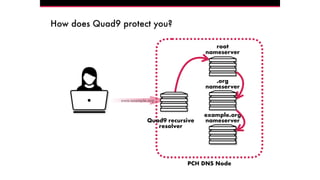
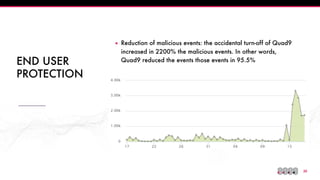
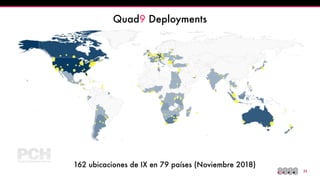
The document discusses the Domain Name System (DNS) and its vulnerabilities, emphasizing the issues with recursive resolvers and the importance of maintaining user privacy. It introduces Quad9, a public DNS resolver that enhances security by blocking malware and preventing data leaks, while stressing the significance of cryptographic authentication. Furthermore, it outlines Quad9's infrastructure and recent deployments across various countries to improve DNS reliability and performance.