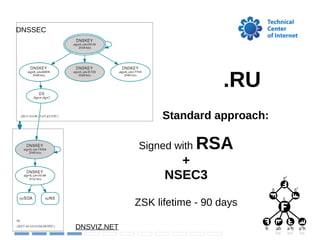
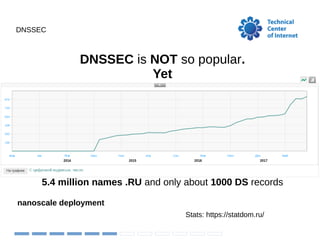
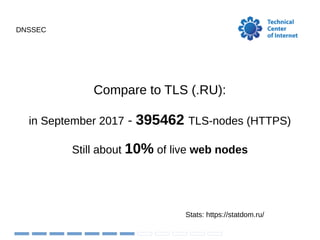
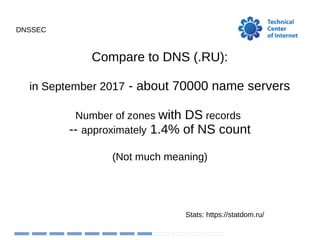
The document discusses the implementation and challenges of DNSSEC in the .ru domain managed by the Technical Center of the Internet (TCI). It highlights the low adoption rates of DNSSEC compared to TLS, with only about 1.4% of name servers having DS records, as well as operational challenges such as expired domain records and the need for registrars to support automatic DNSSEC. TCI provides support for DS records in EPP and aims to educate end users on the importance of DNSSEC.