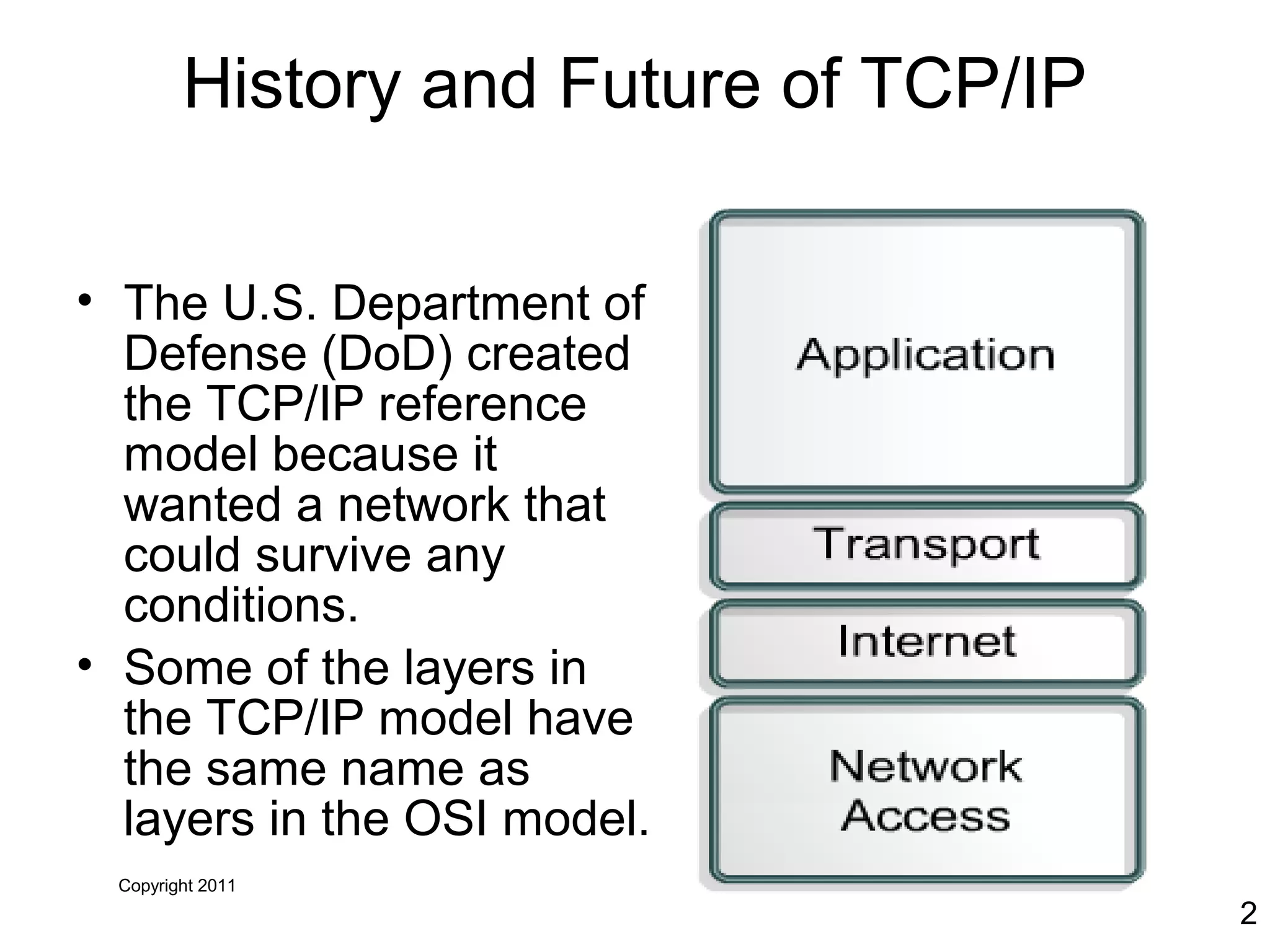
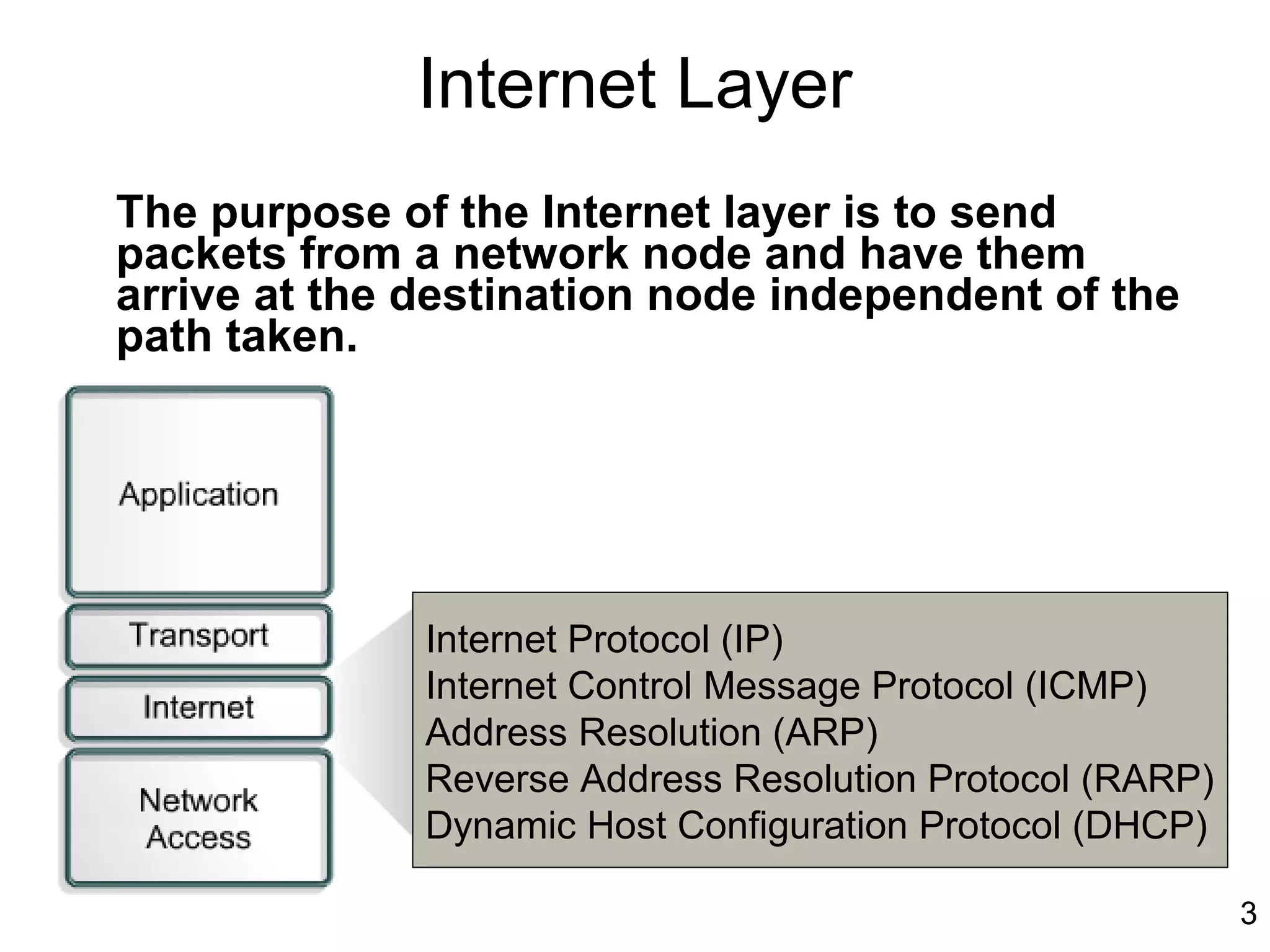
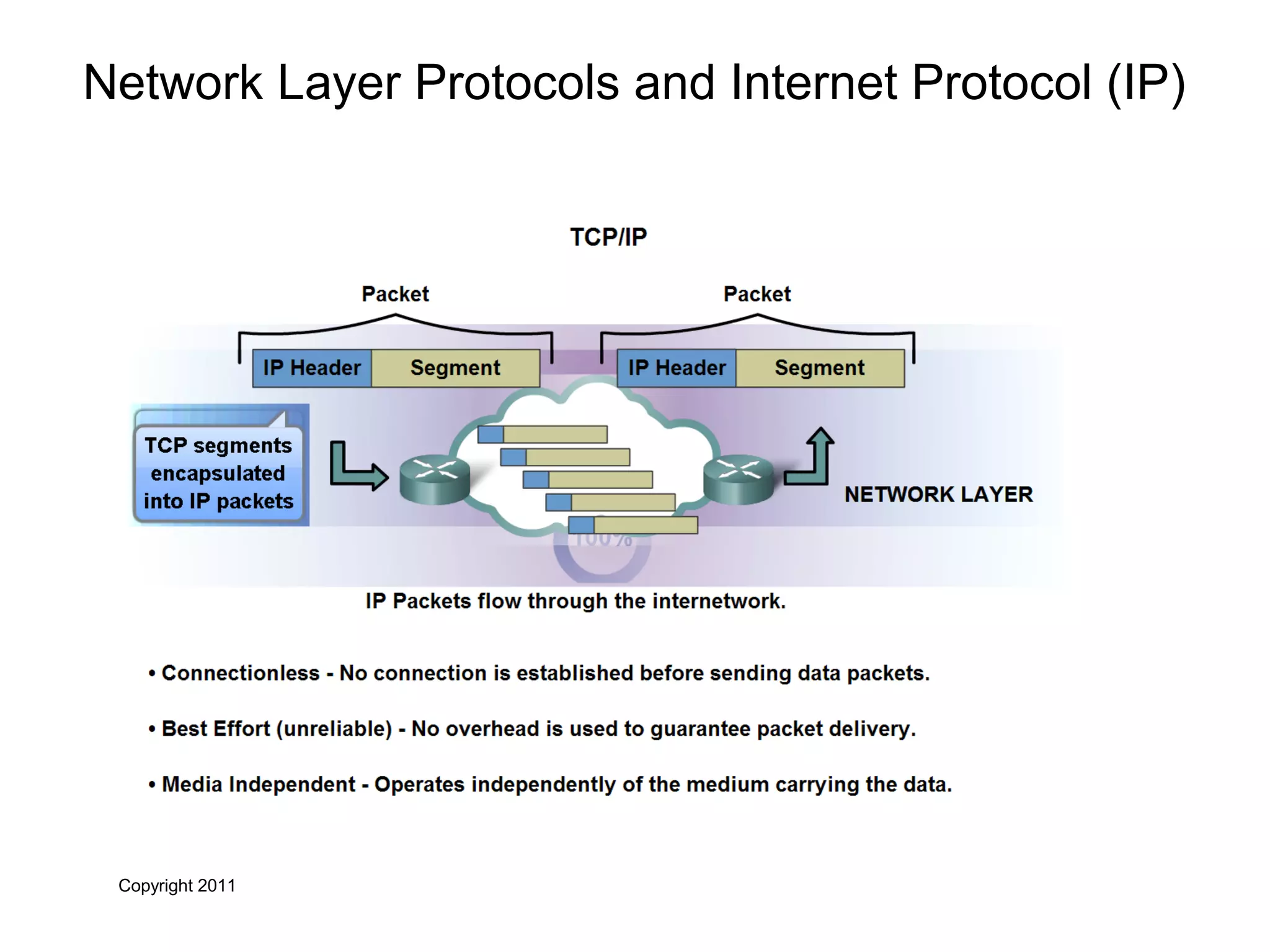
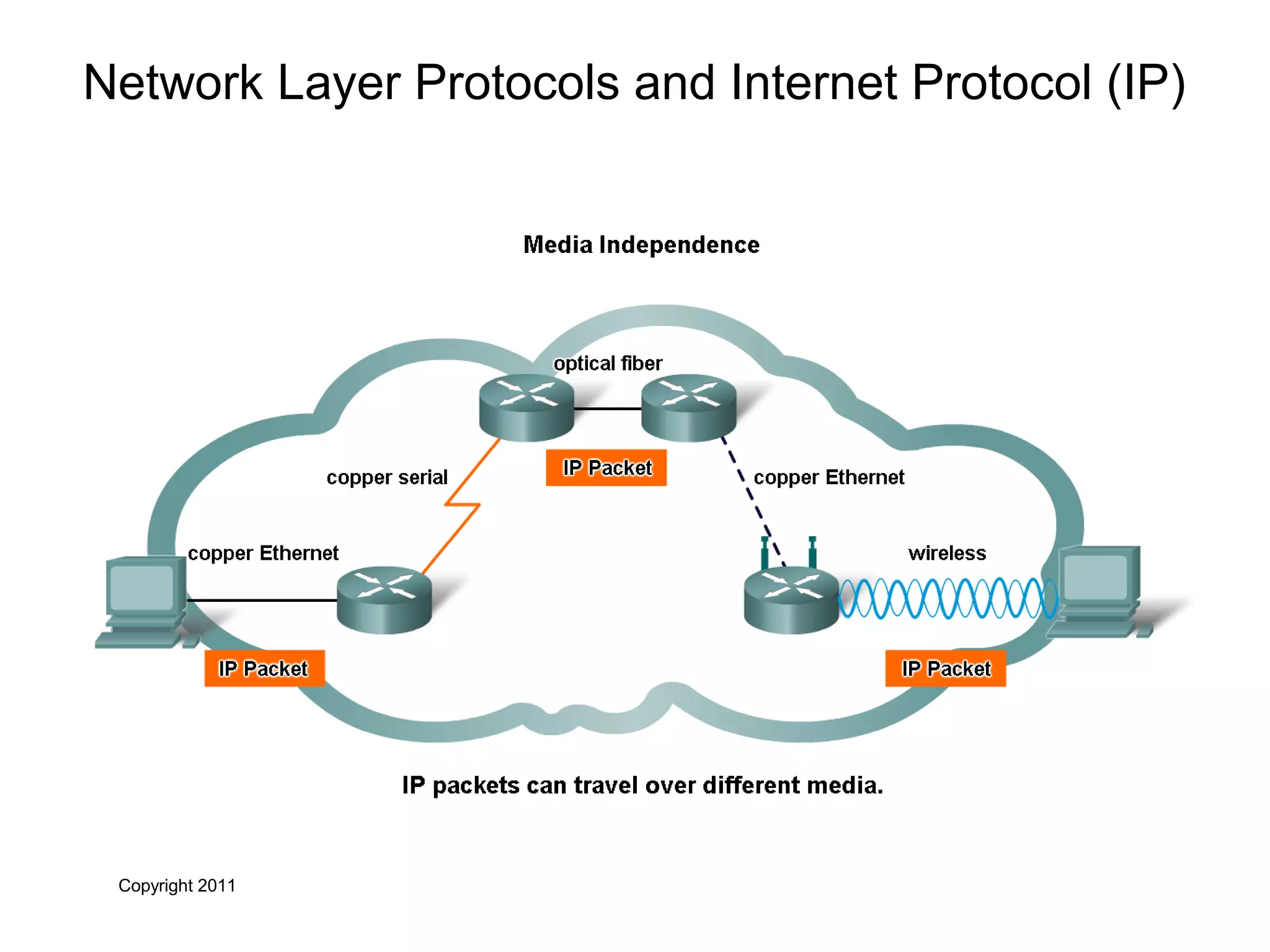
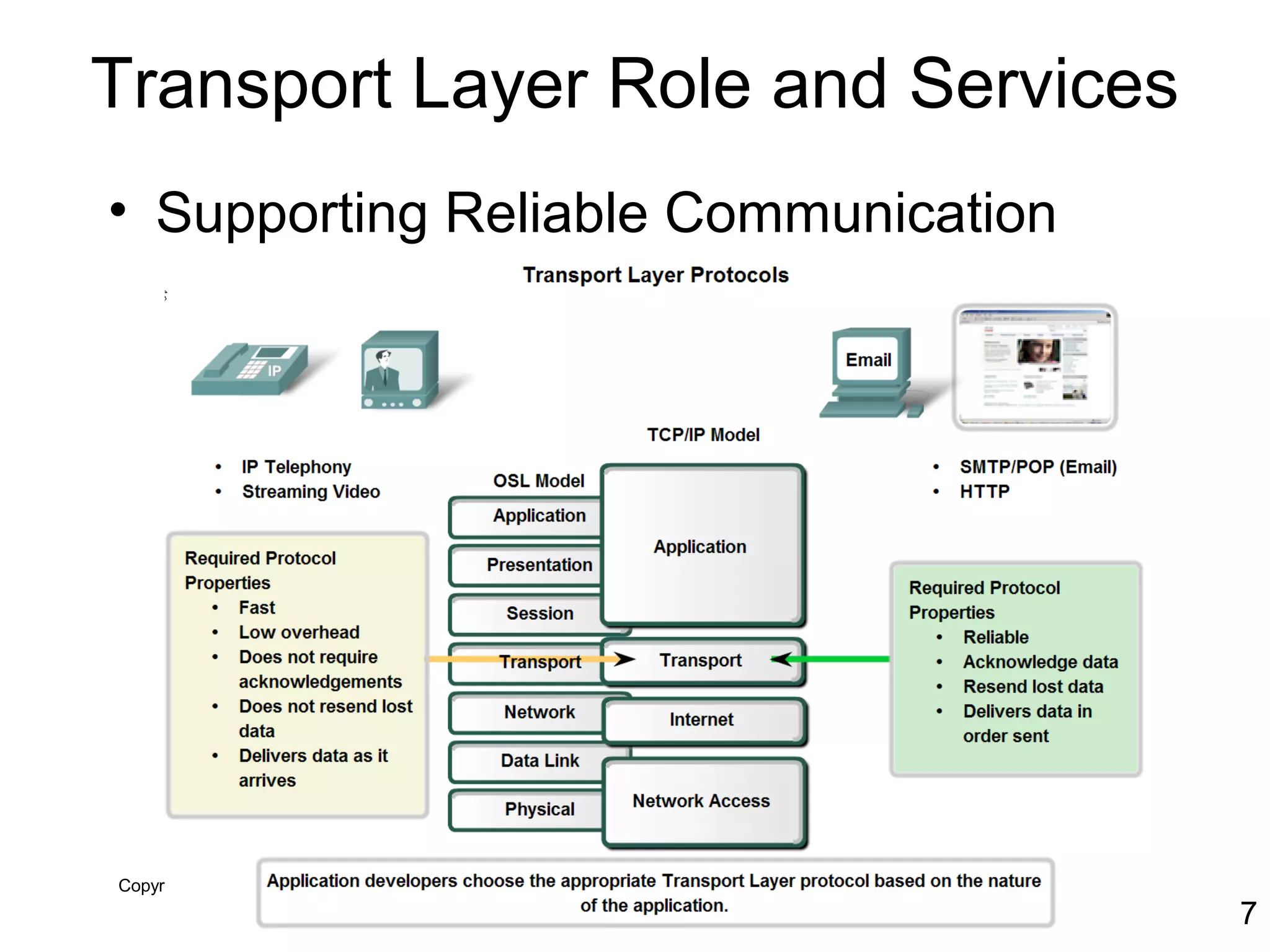
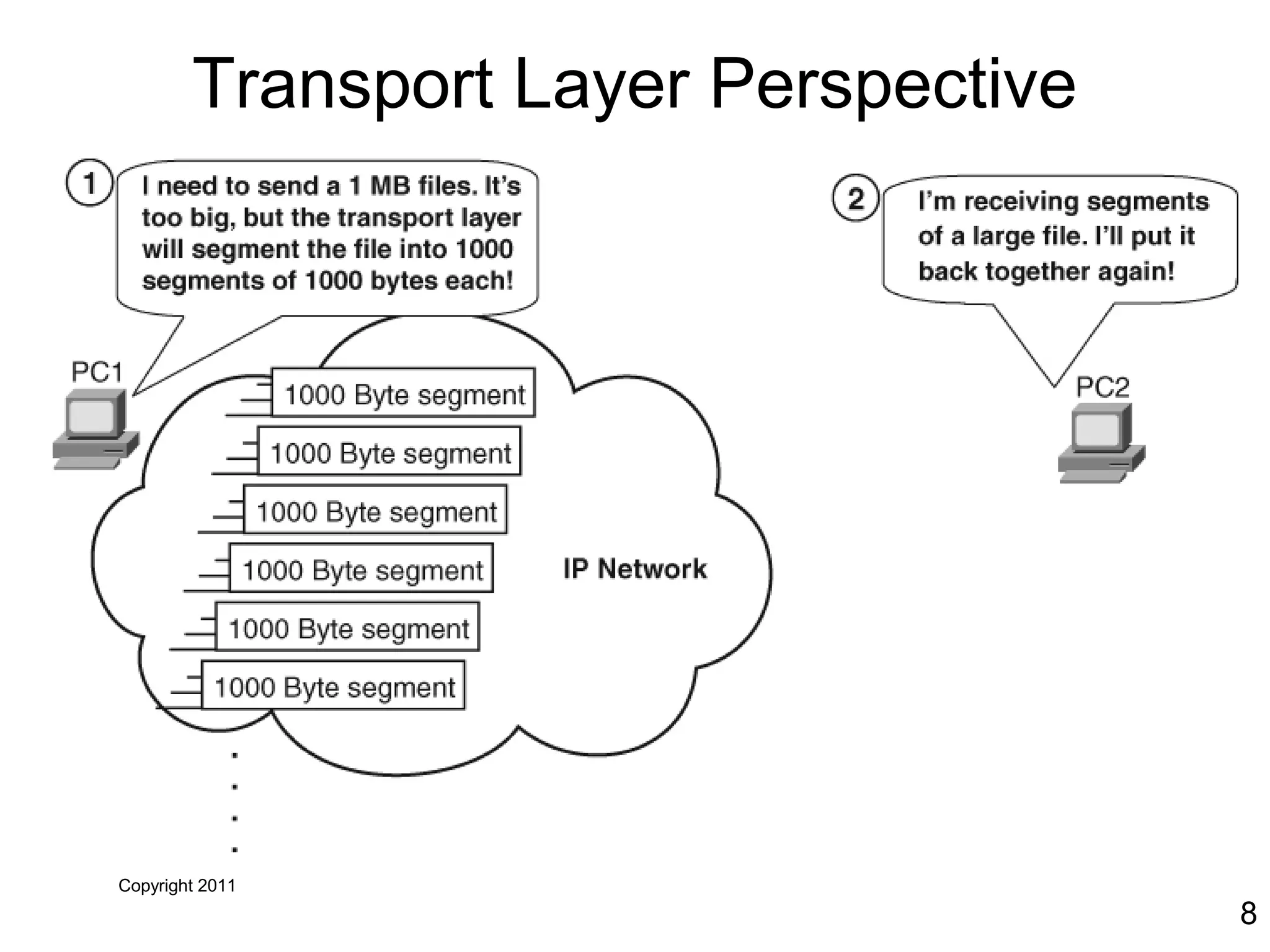
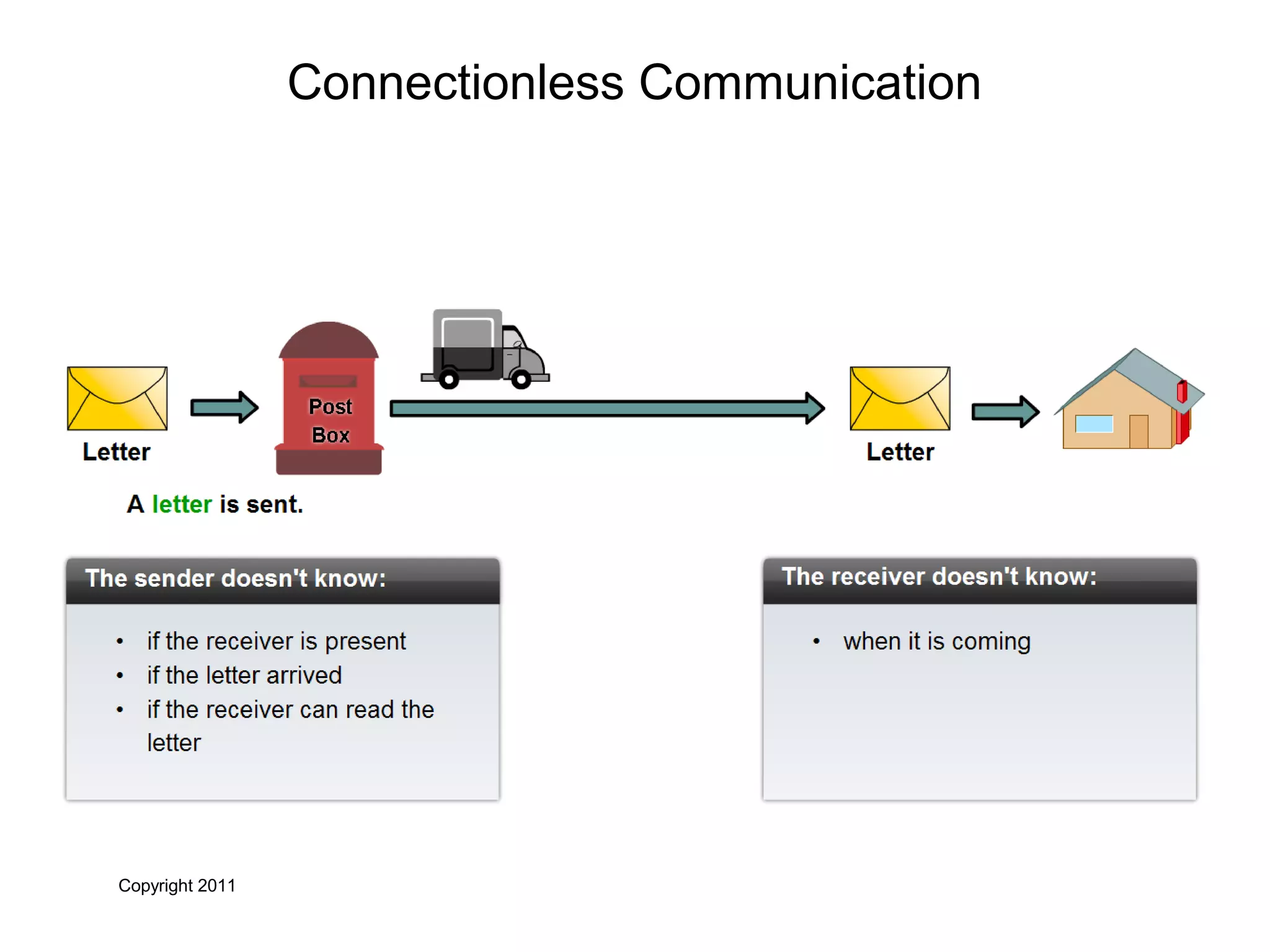
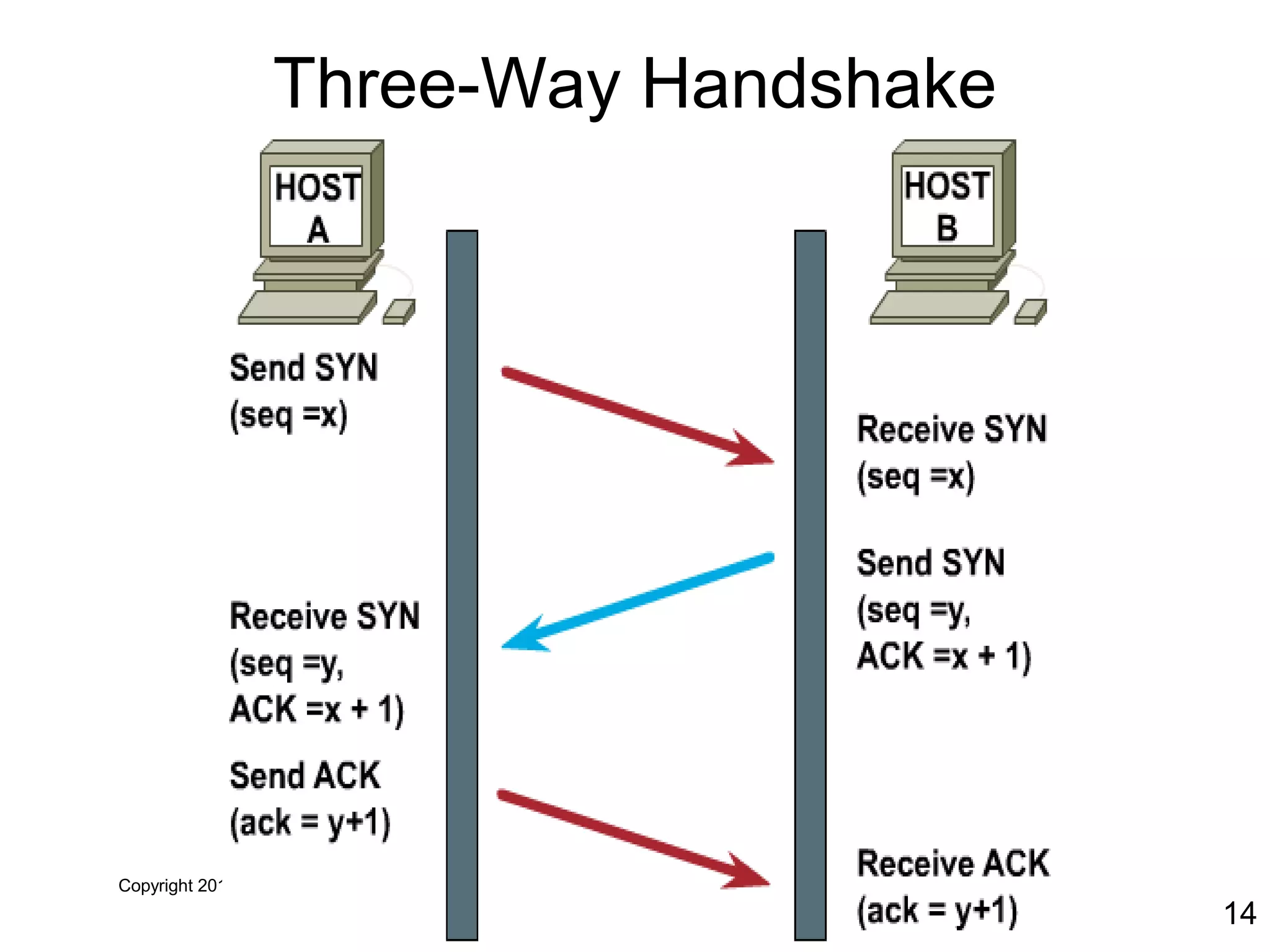
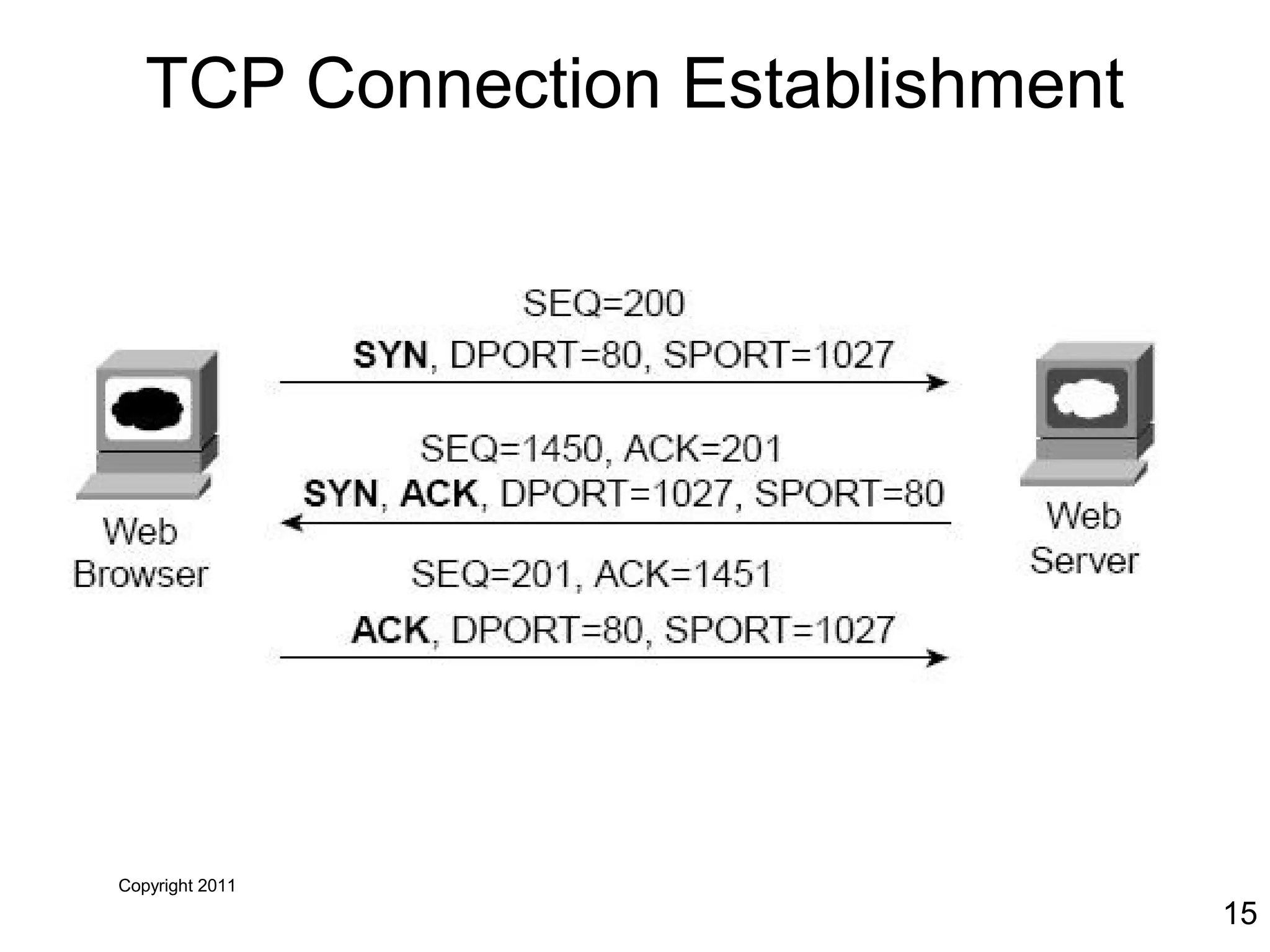
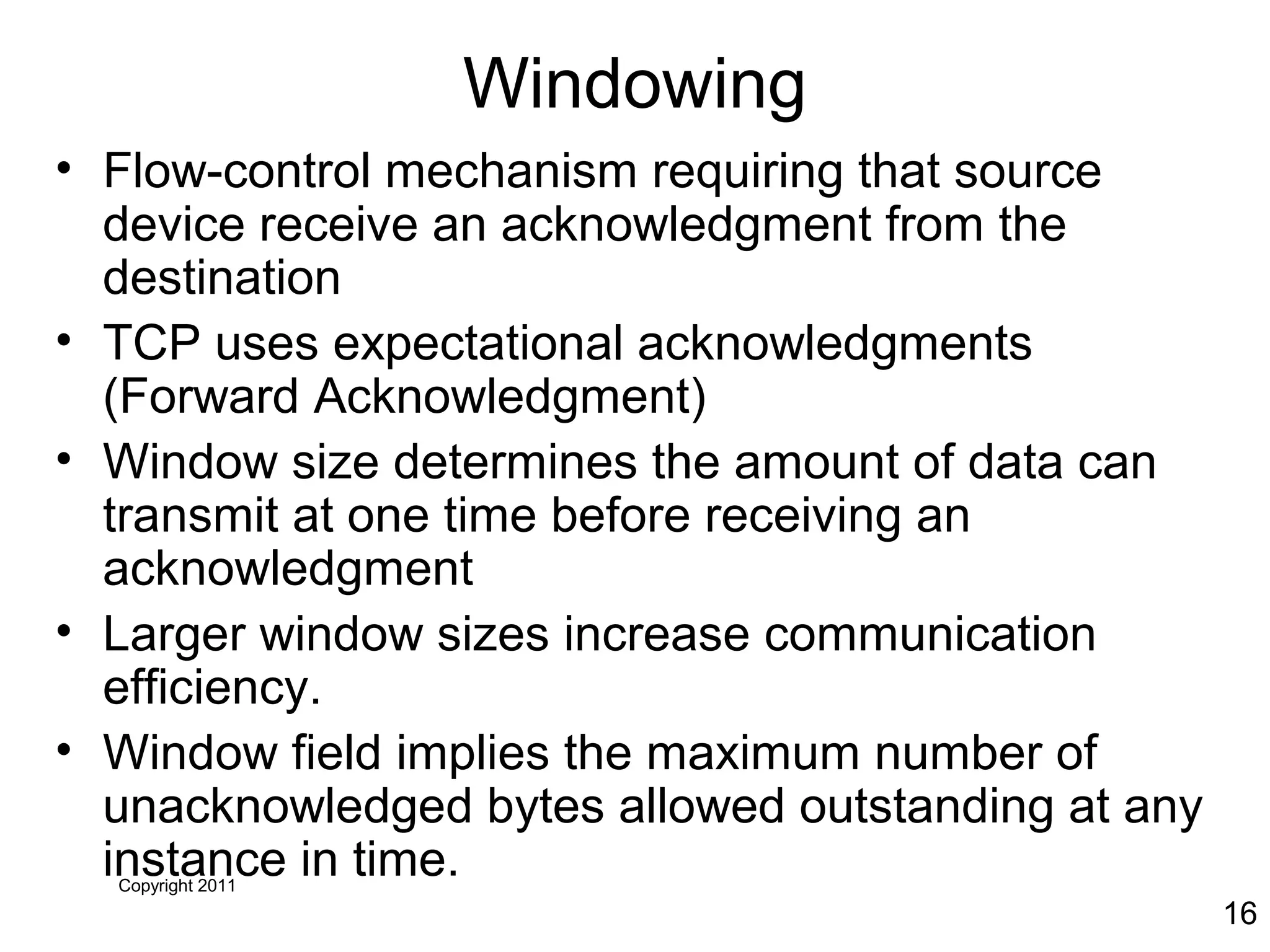
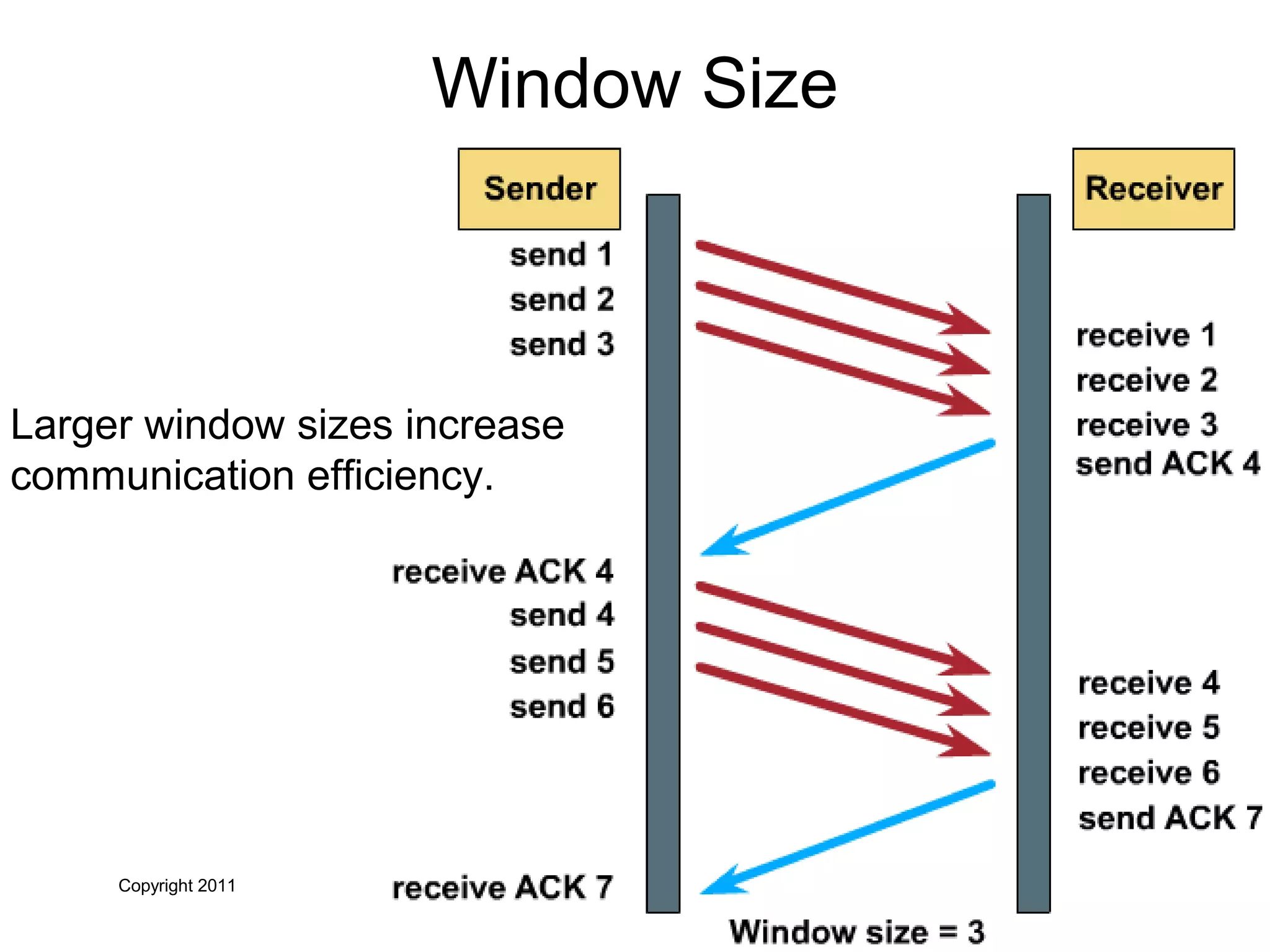
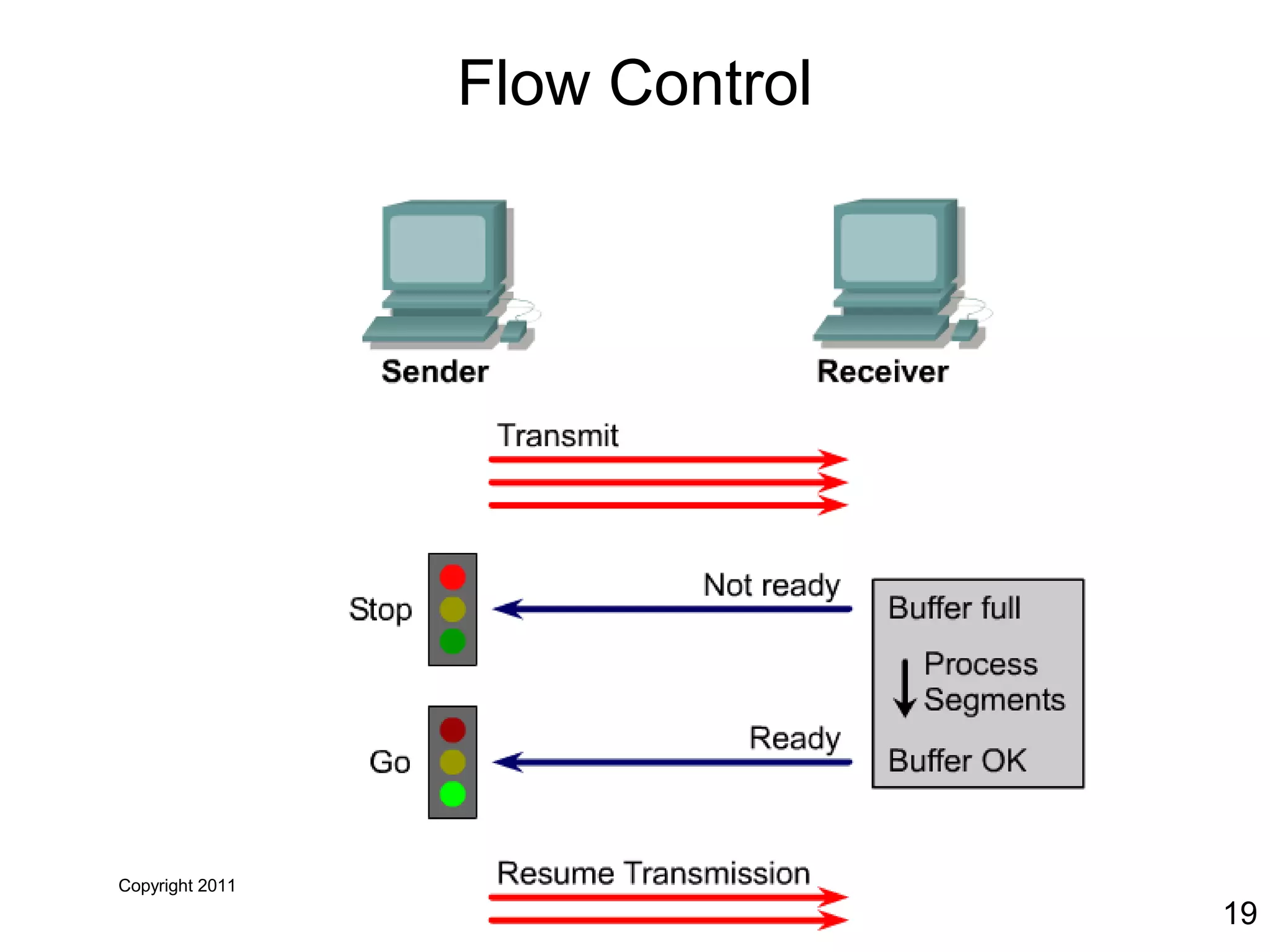
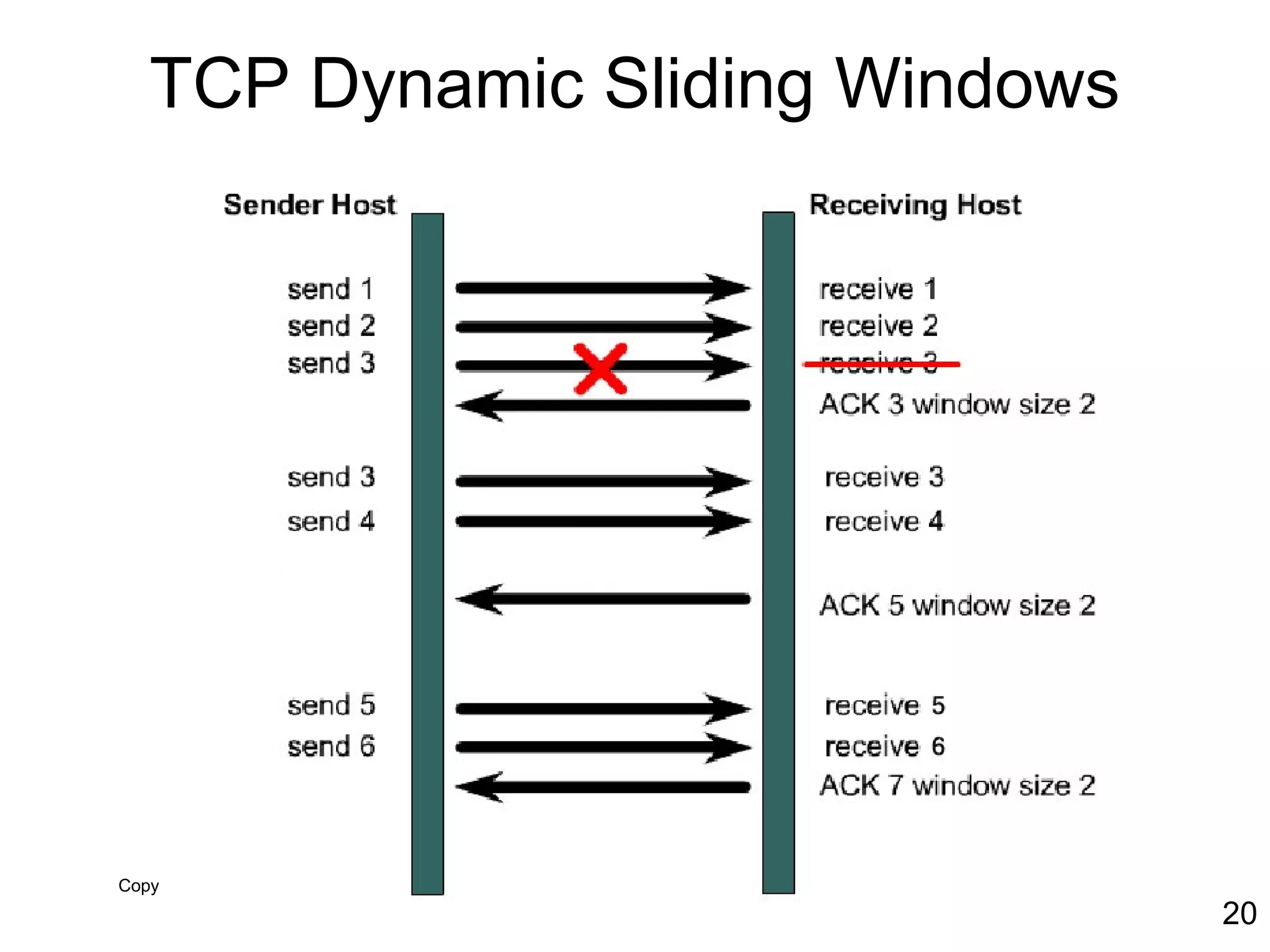
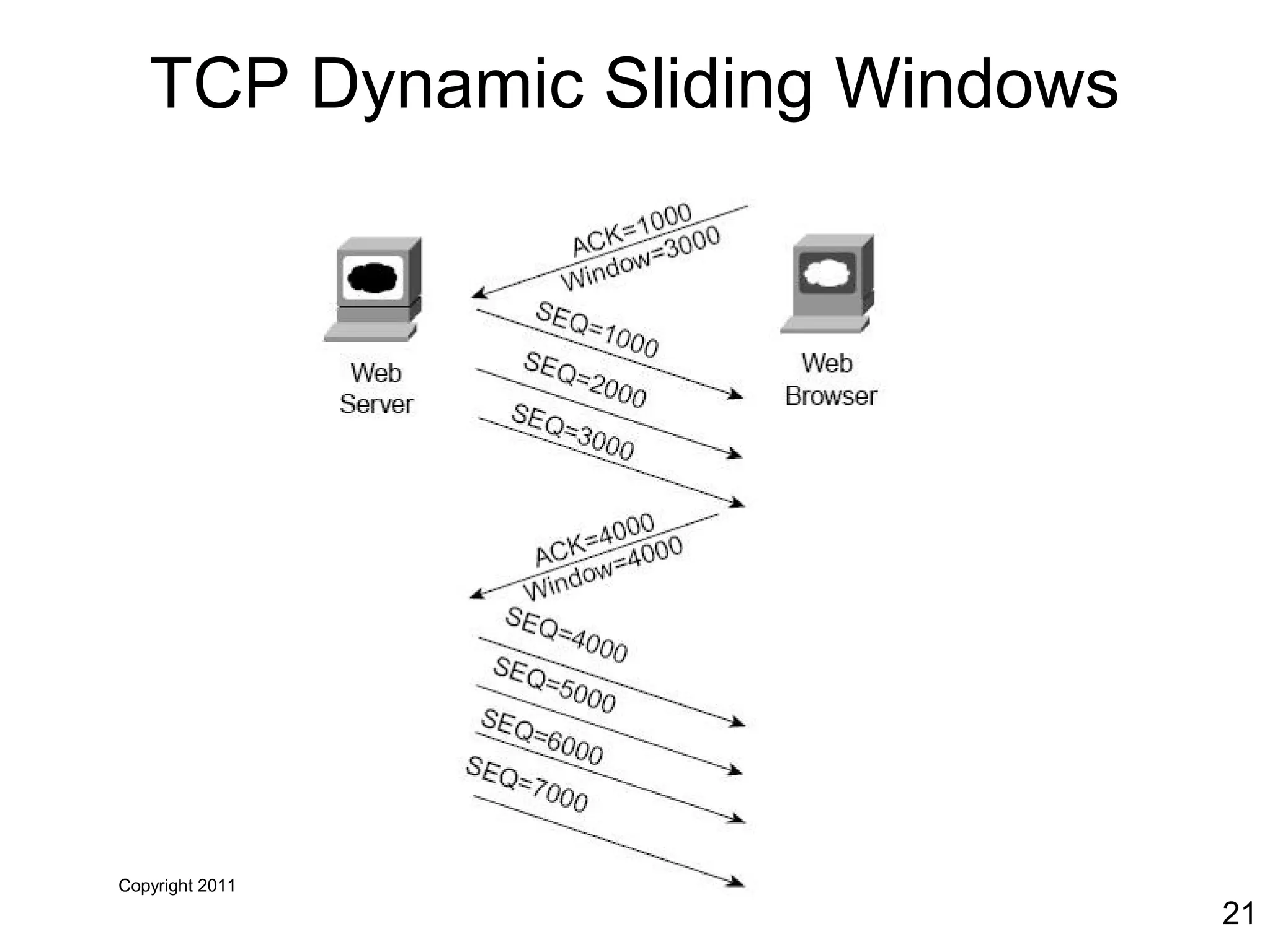
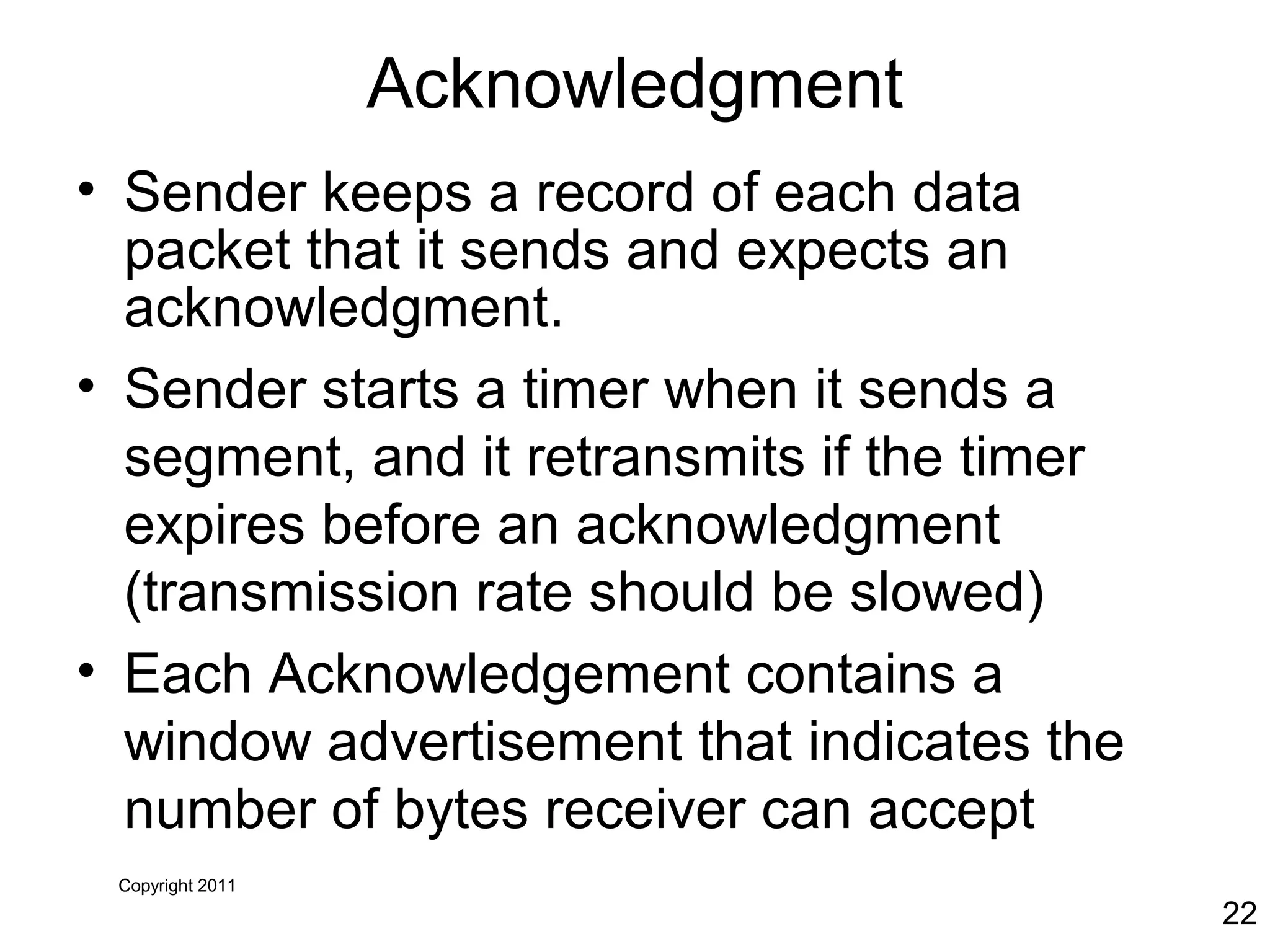
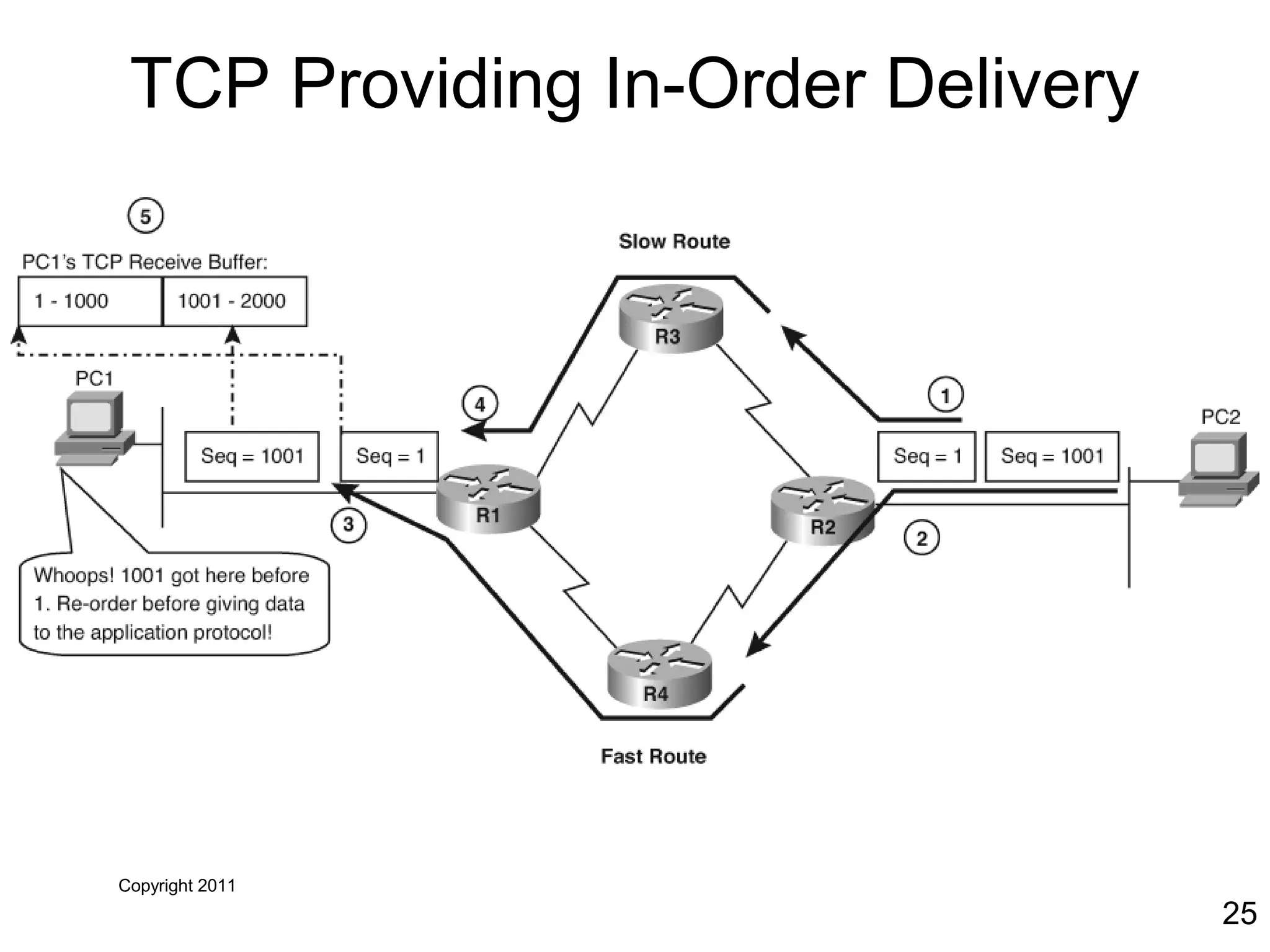
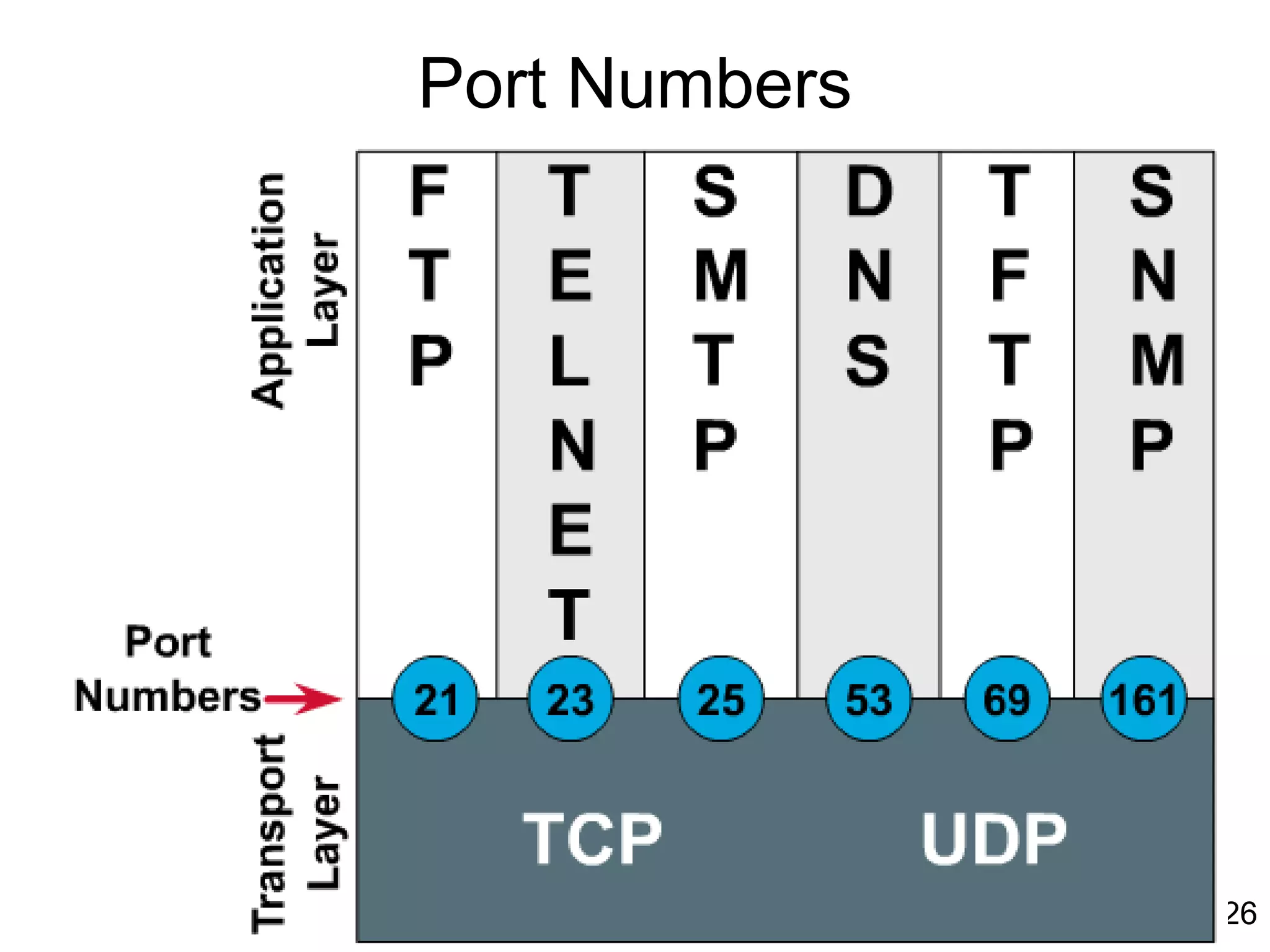
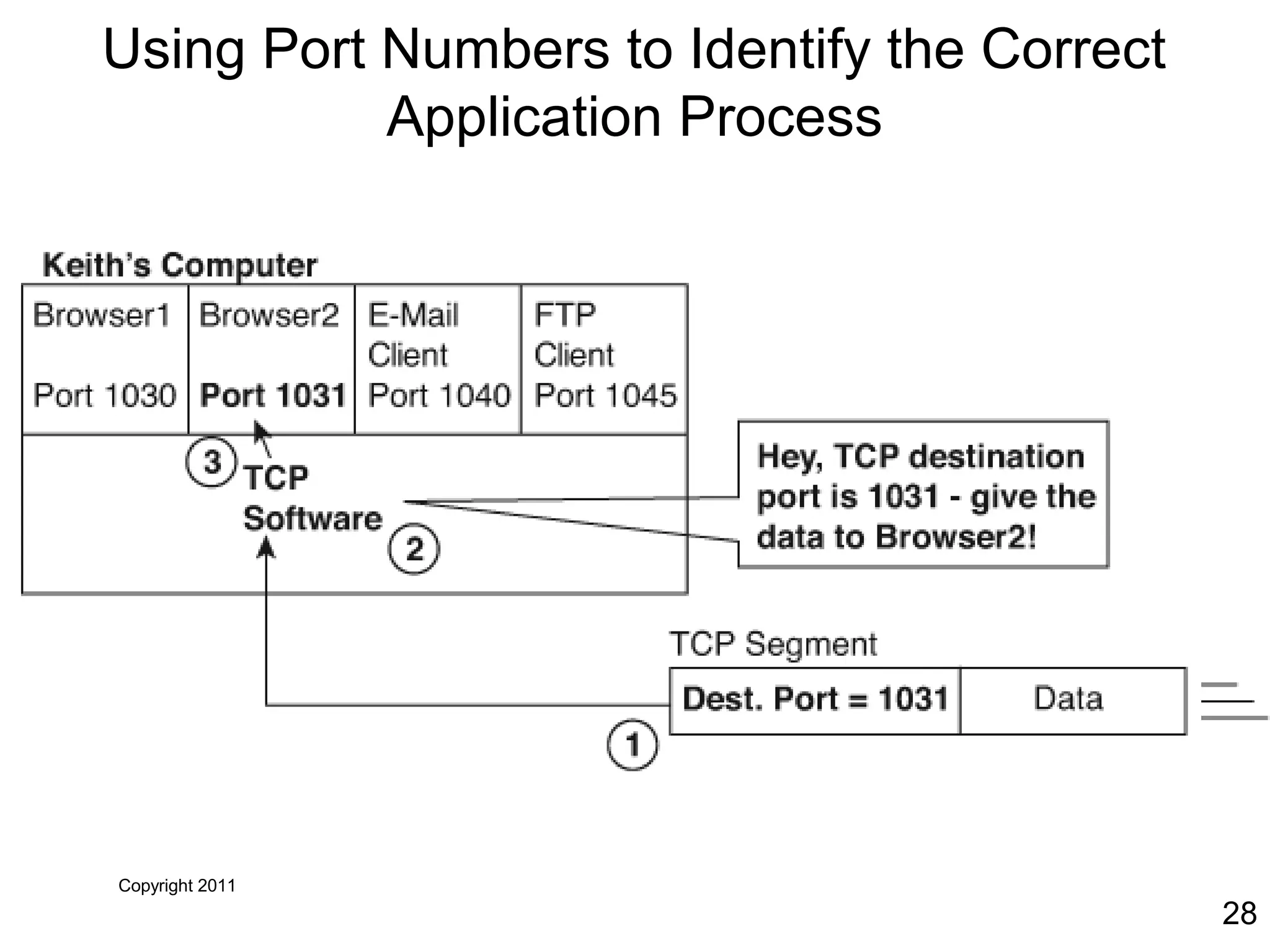
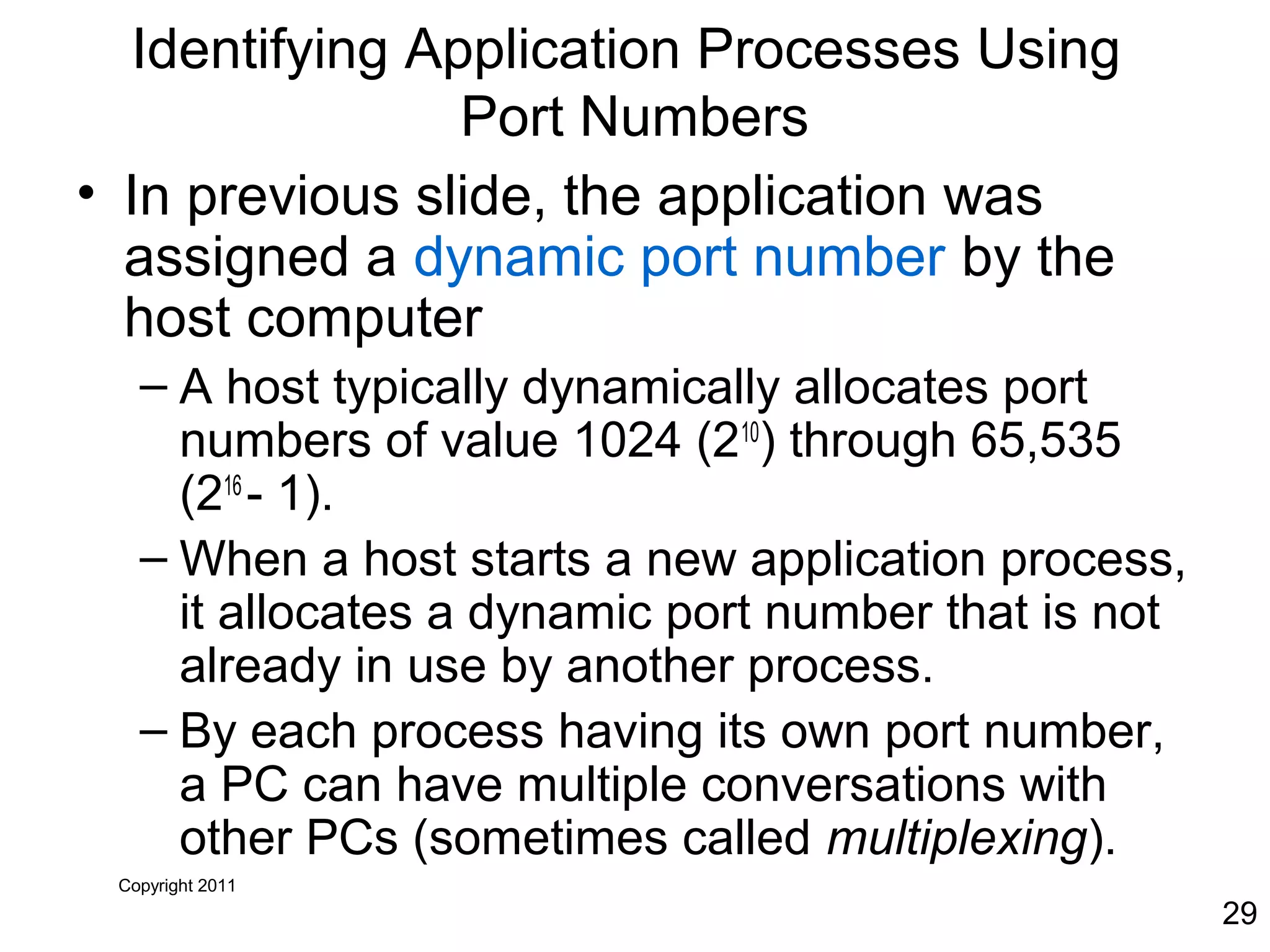
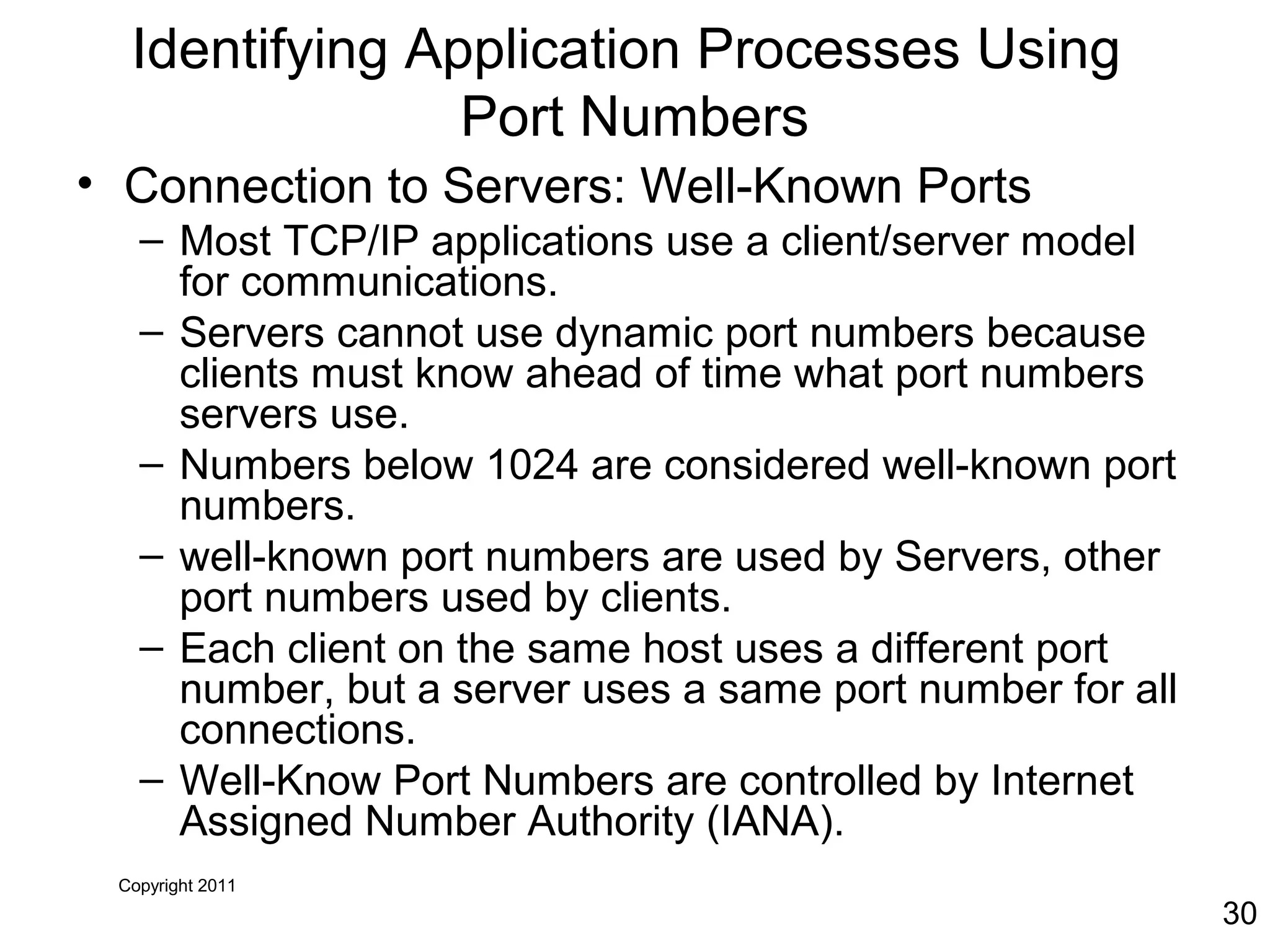
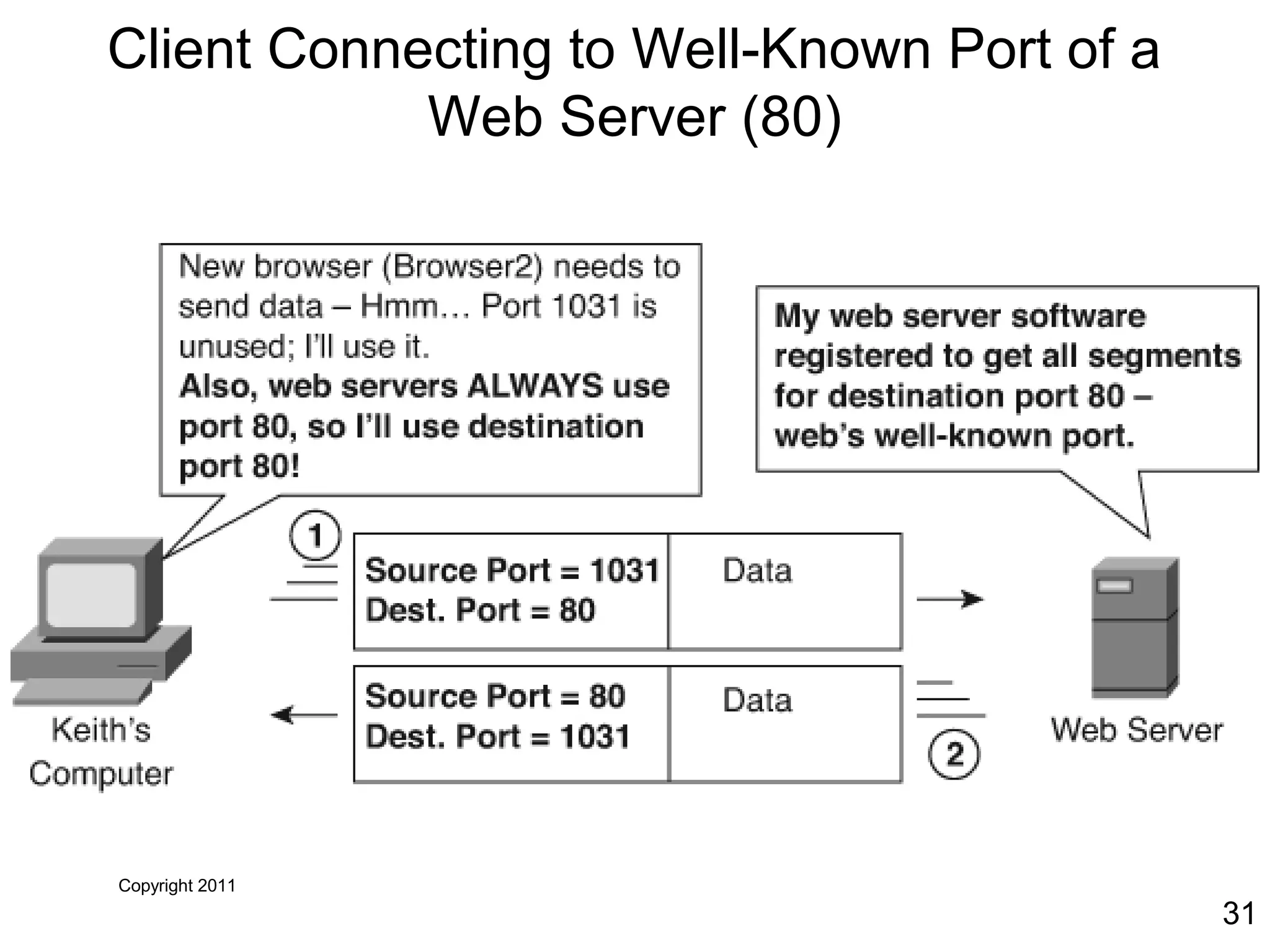
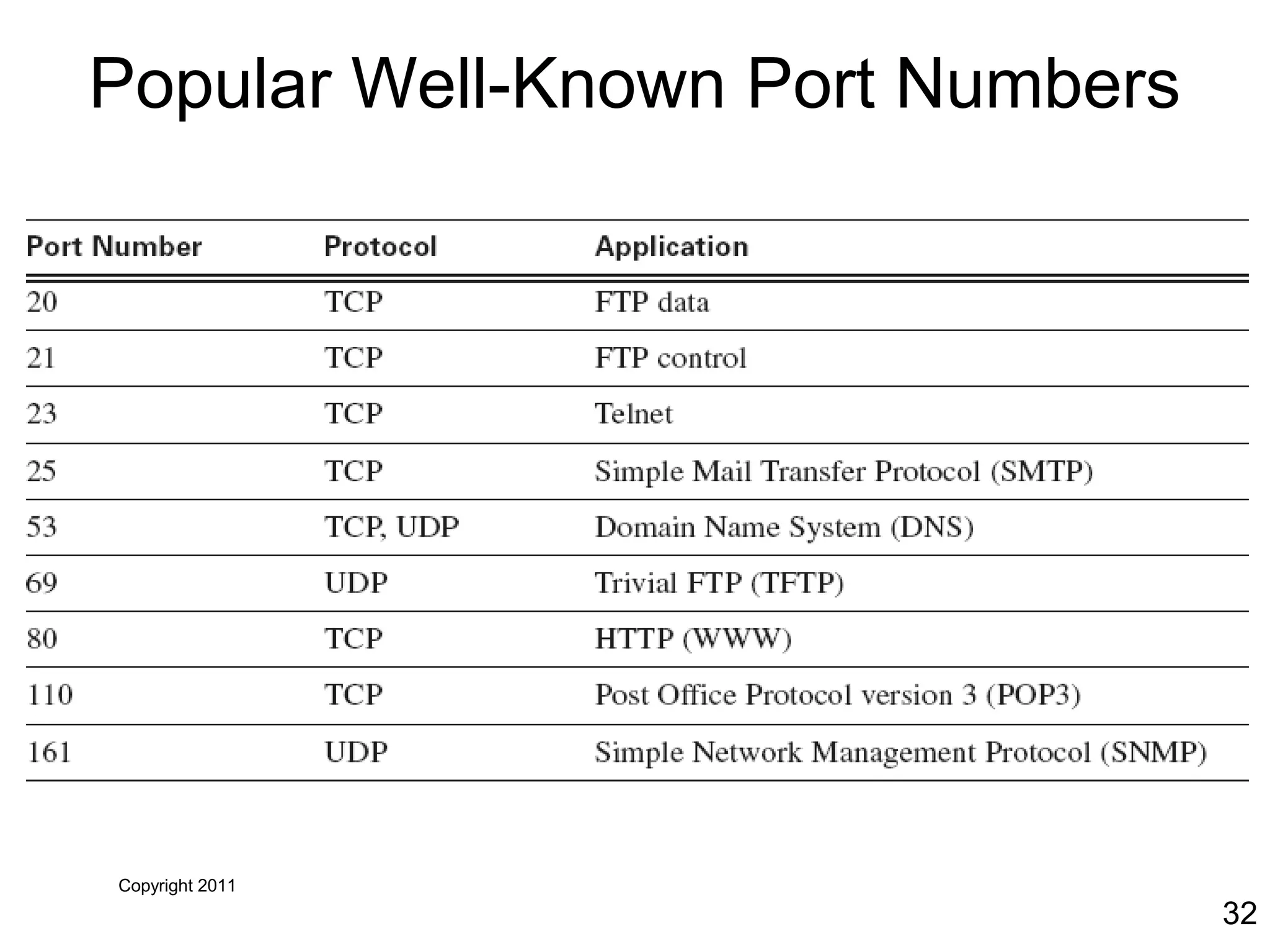
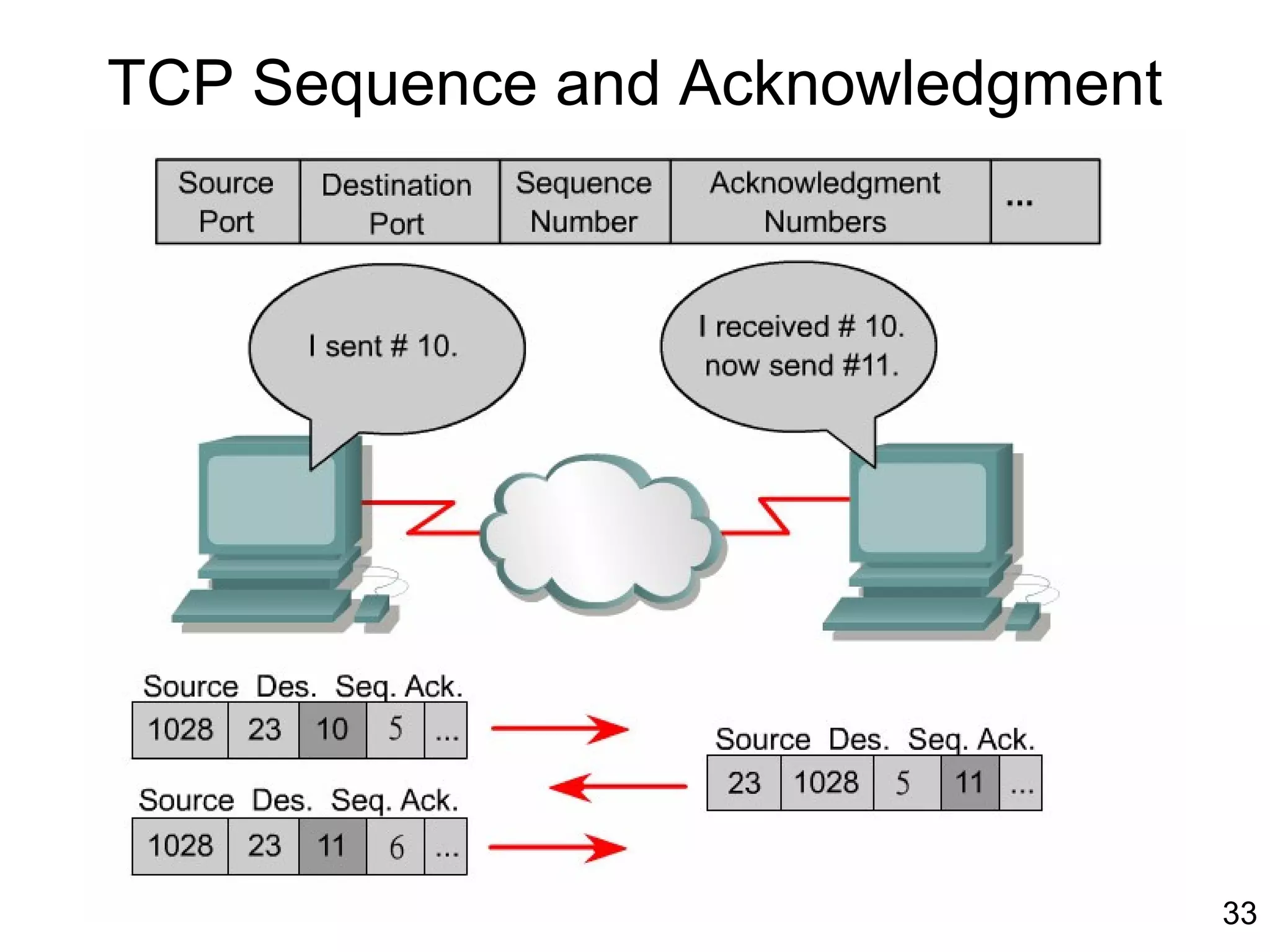
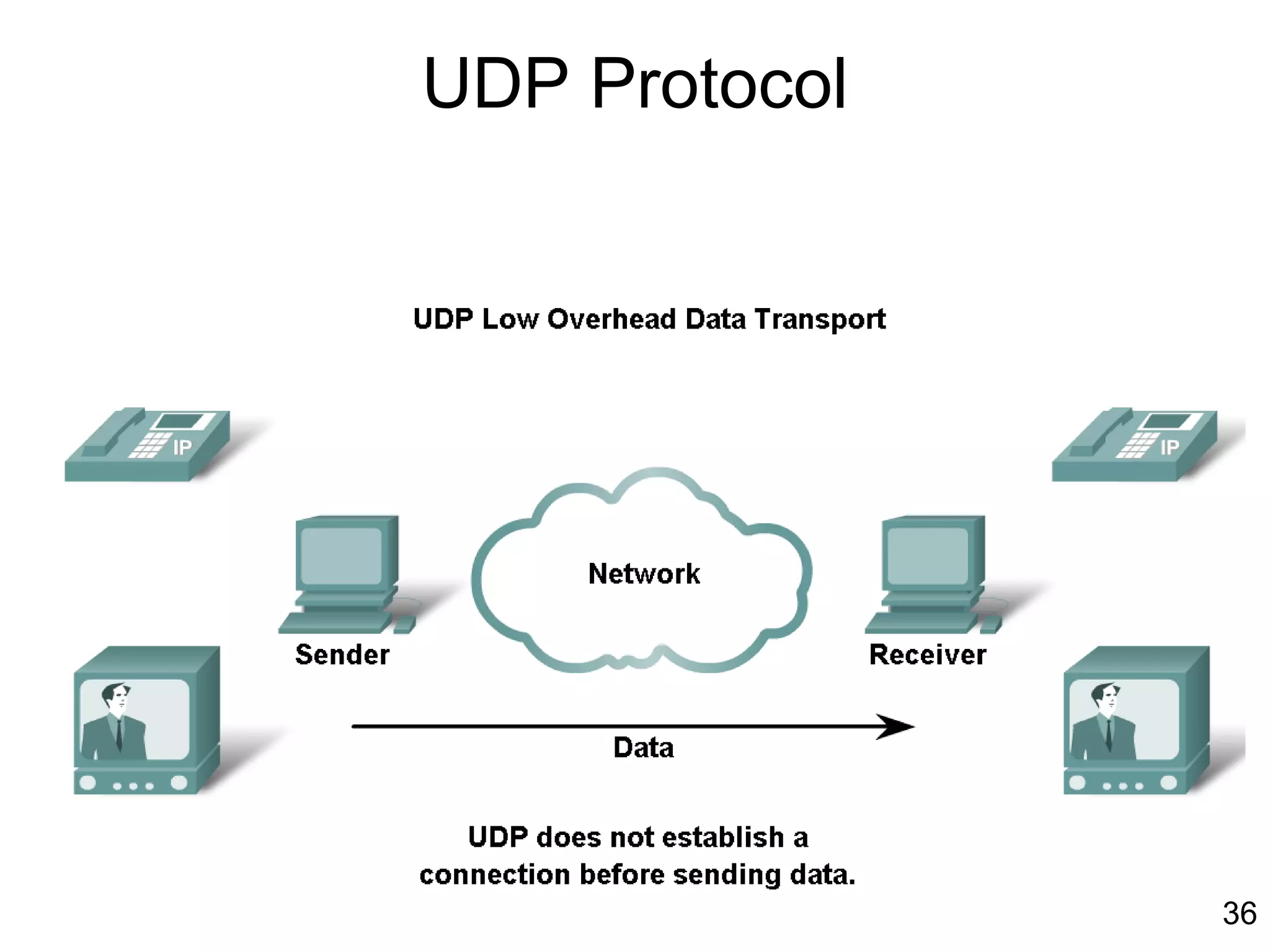
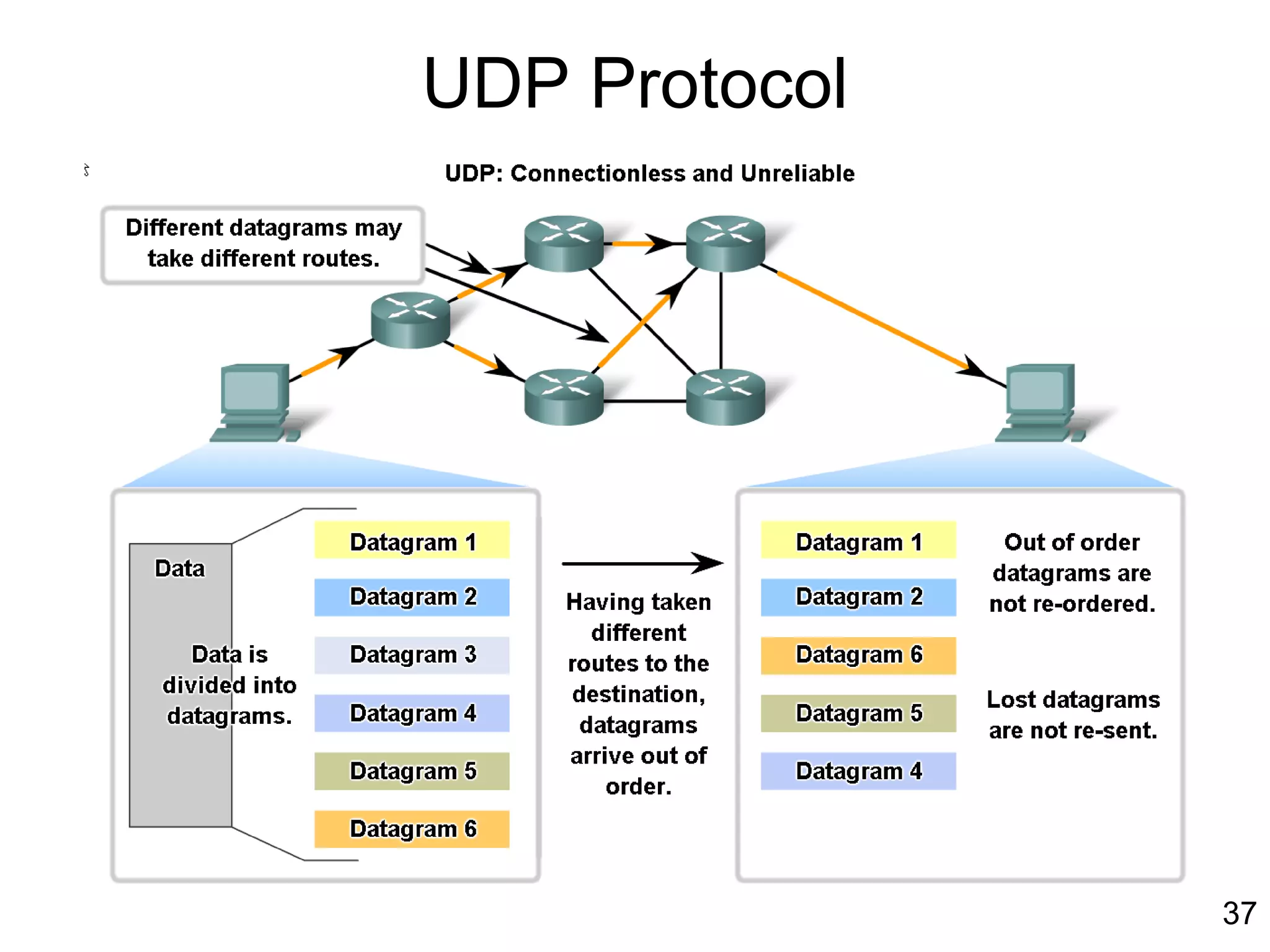
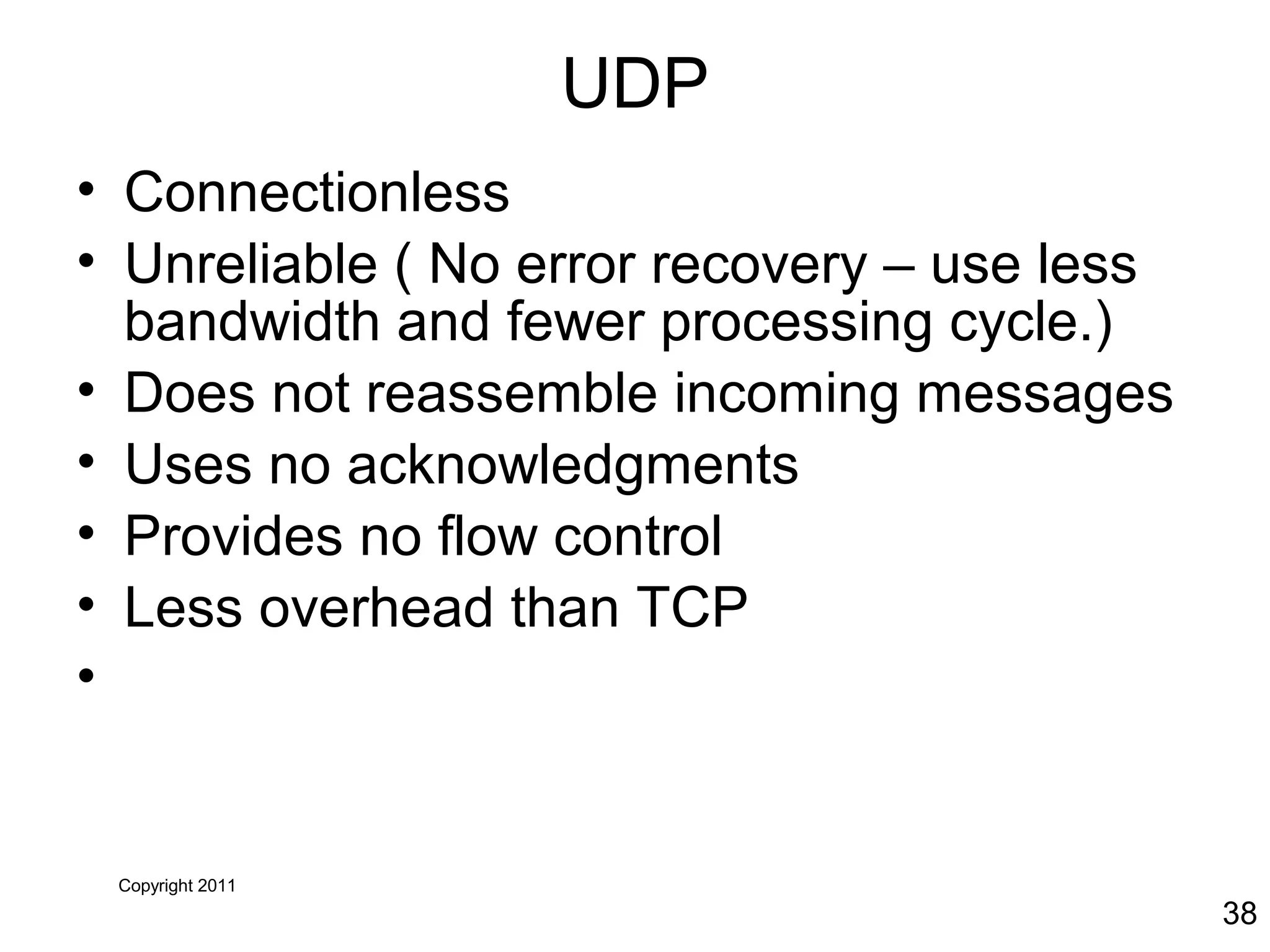
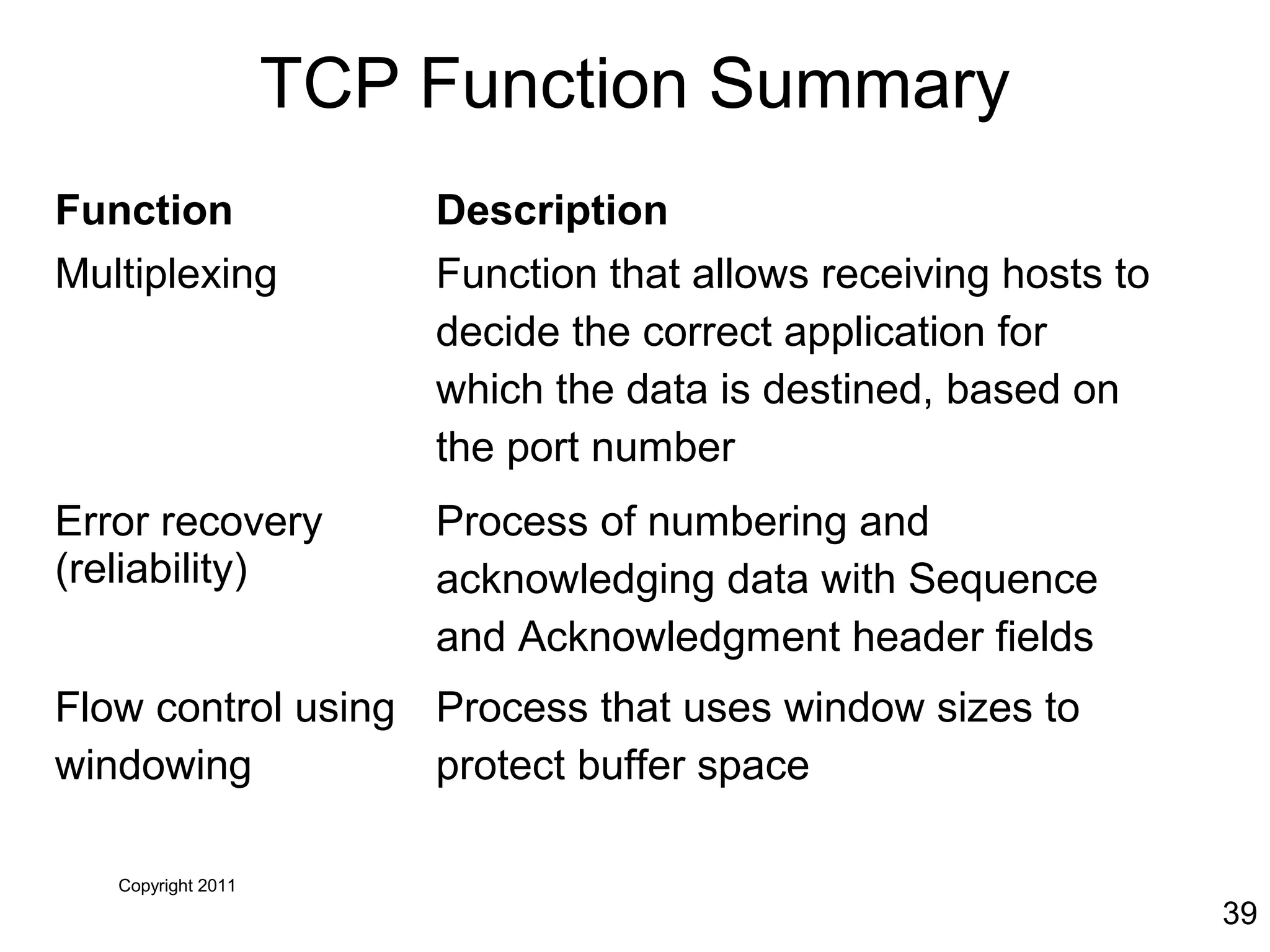
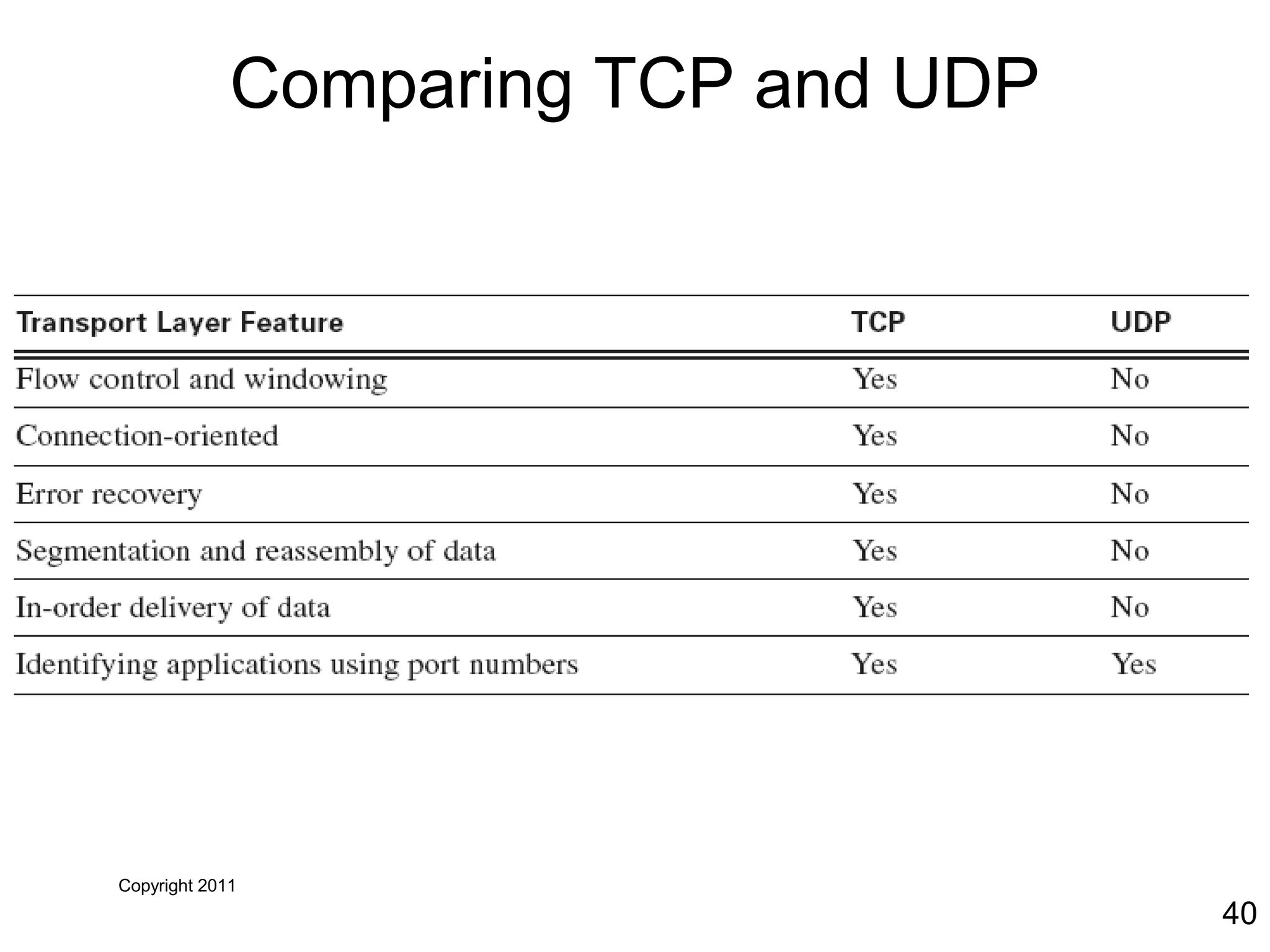
The document discusses TCP/IP and its transport and internet layers. It describes how TCP/IP provides reliable, connection-oriented communication using mechanisms like three-way handshakes, windowing, acknowledgments and retransmissions. It also discusses UDP, a connectionless protocol that does not provide reliability. Well-known ports allow clients to identify server applications.