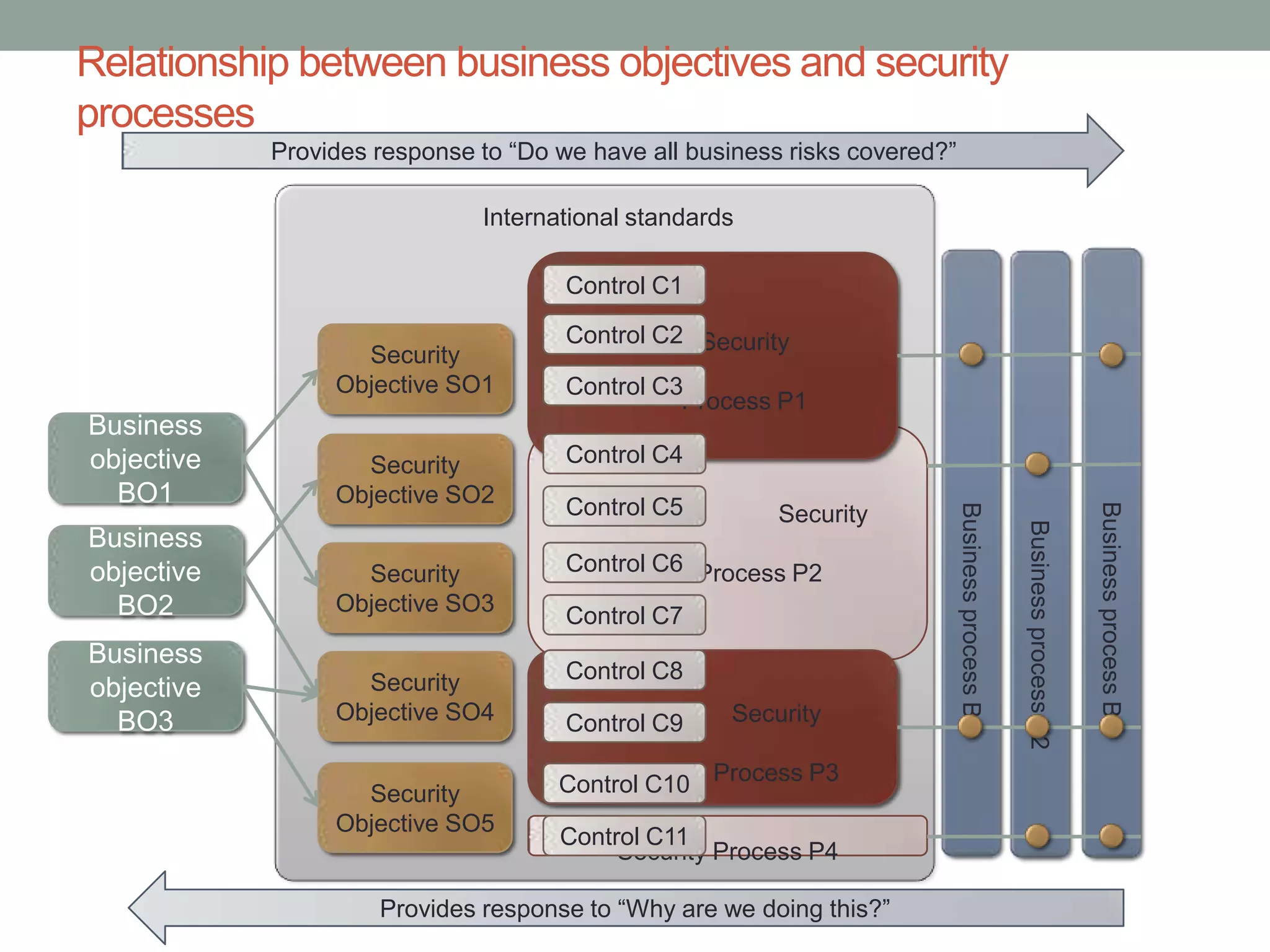
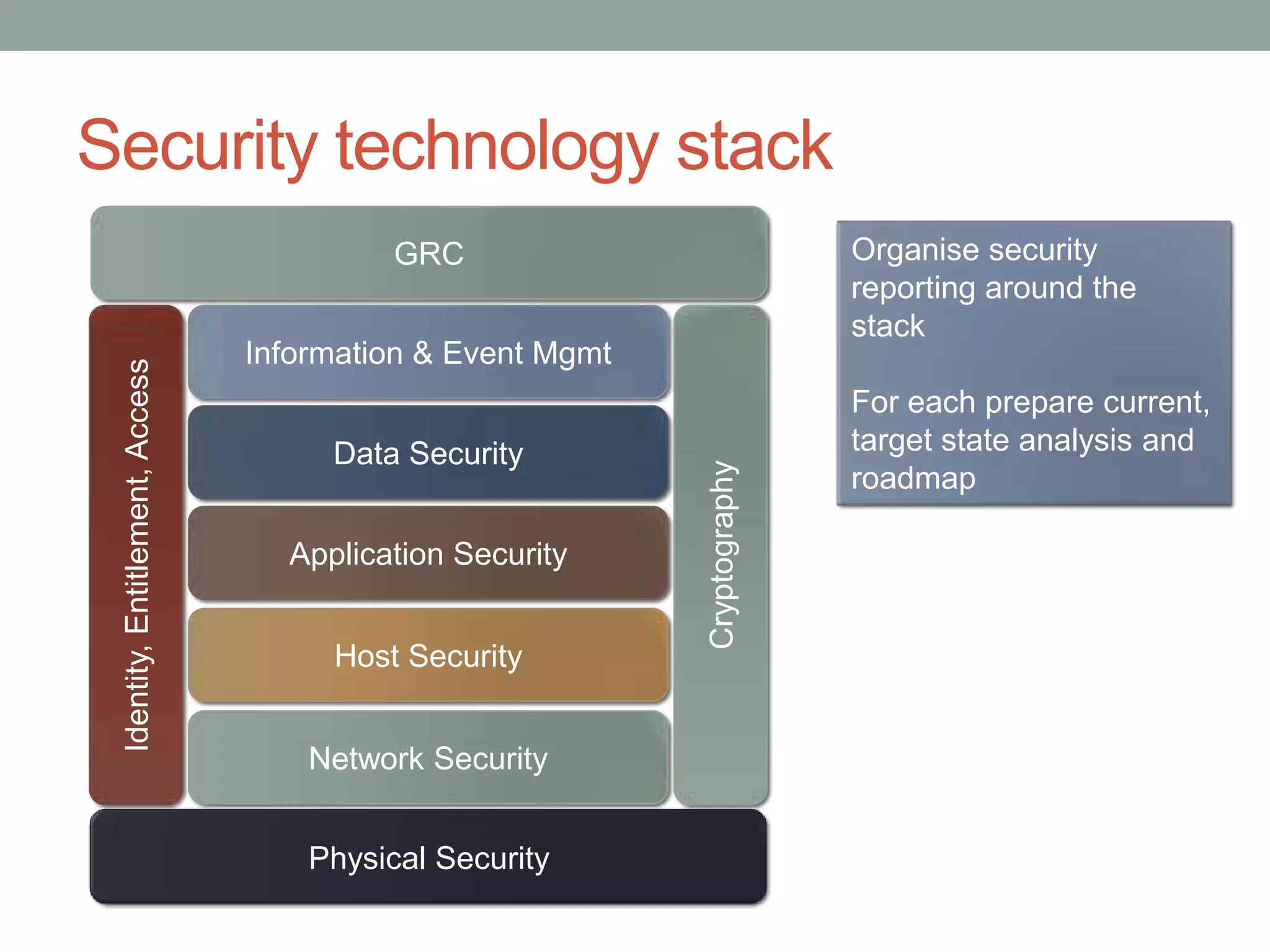
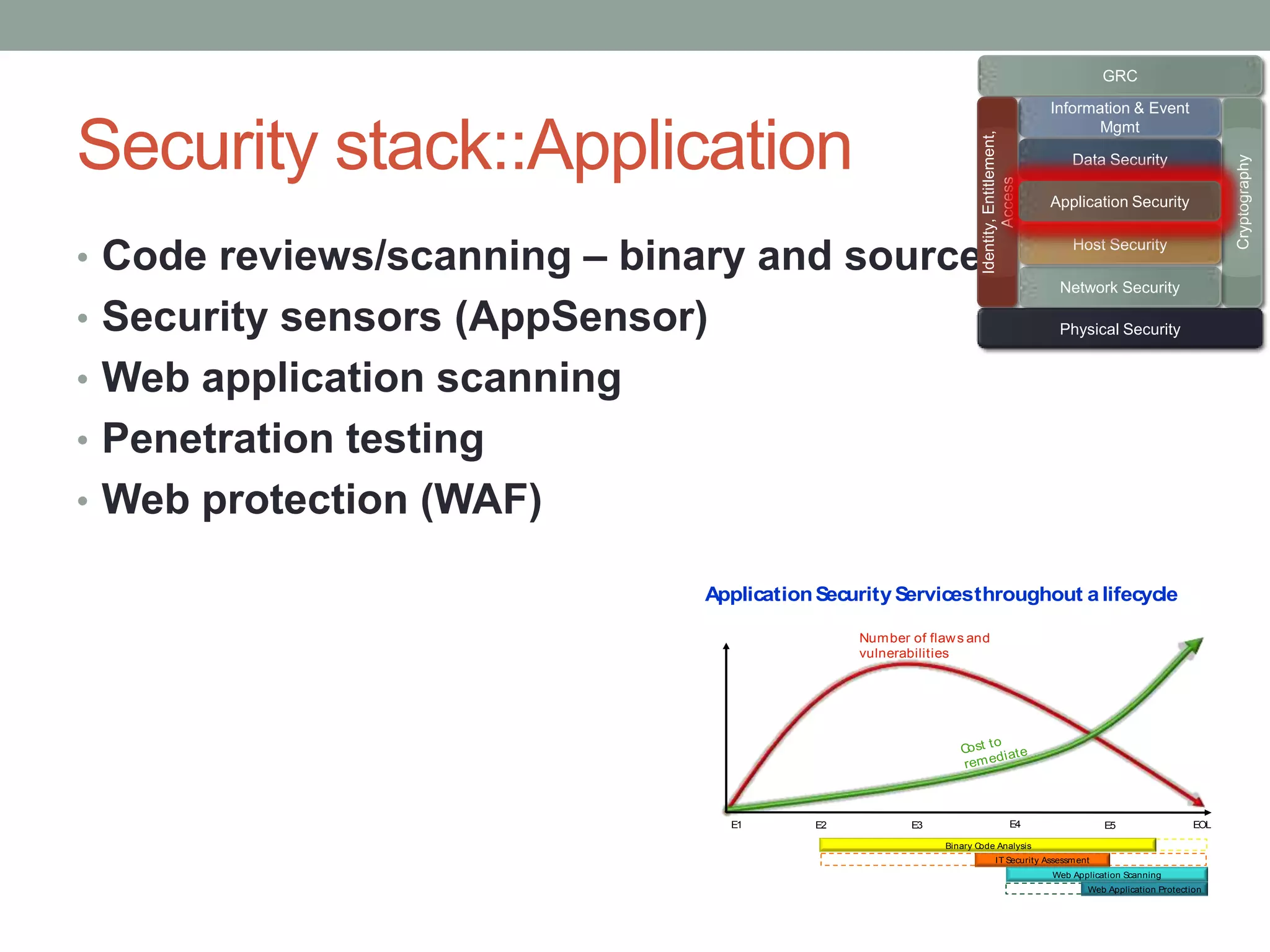
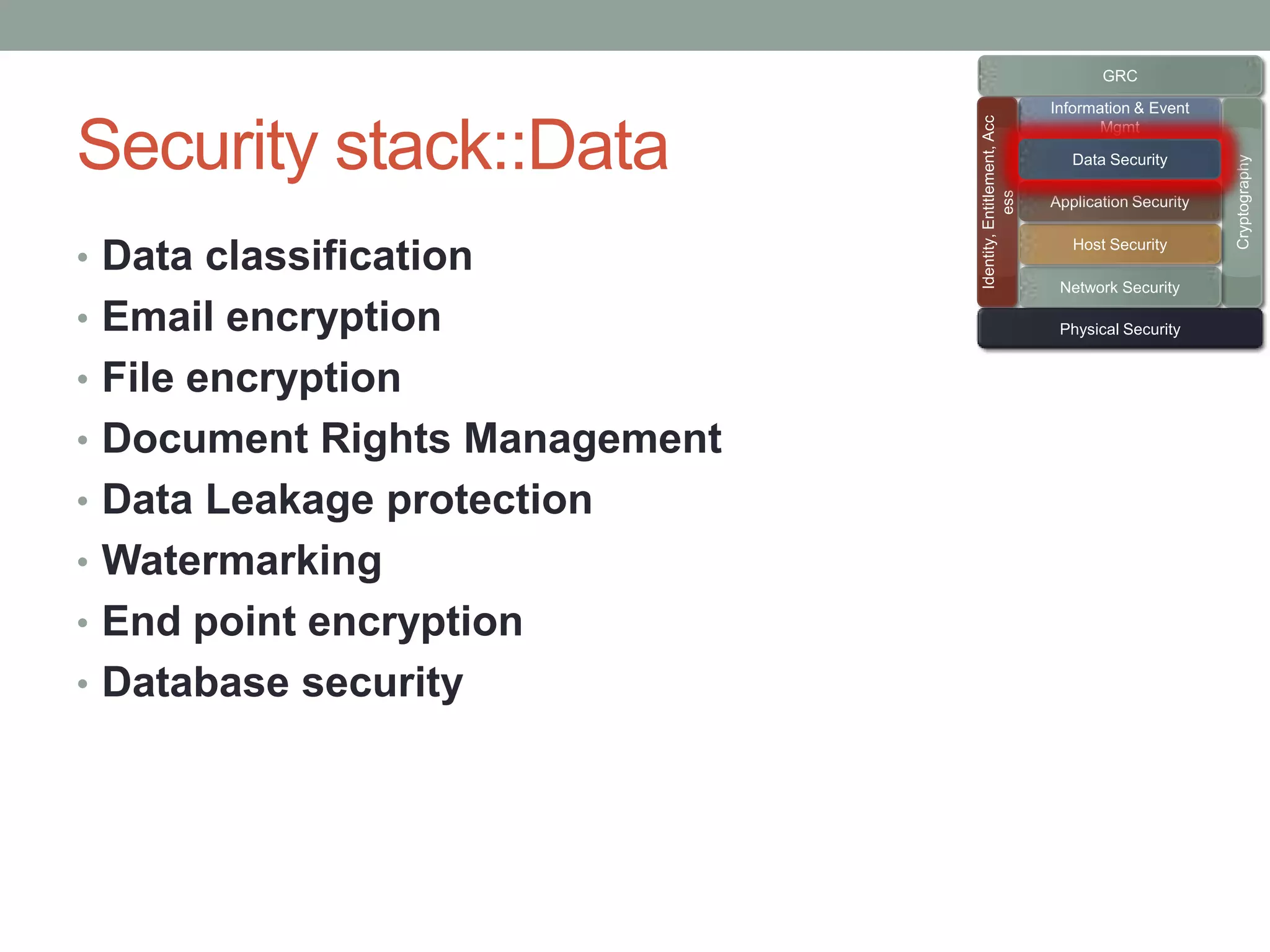
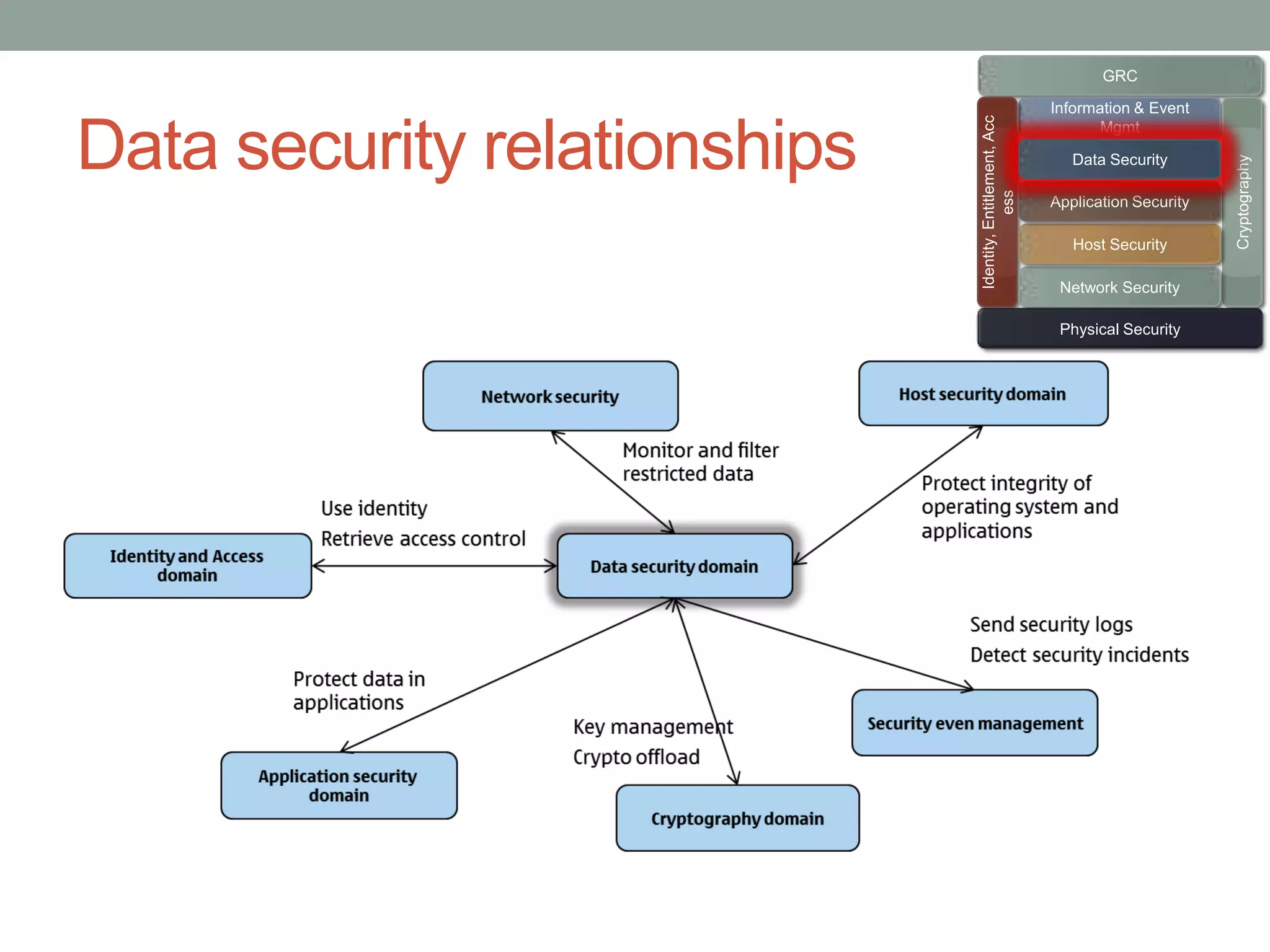
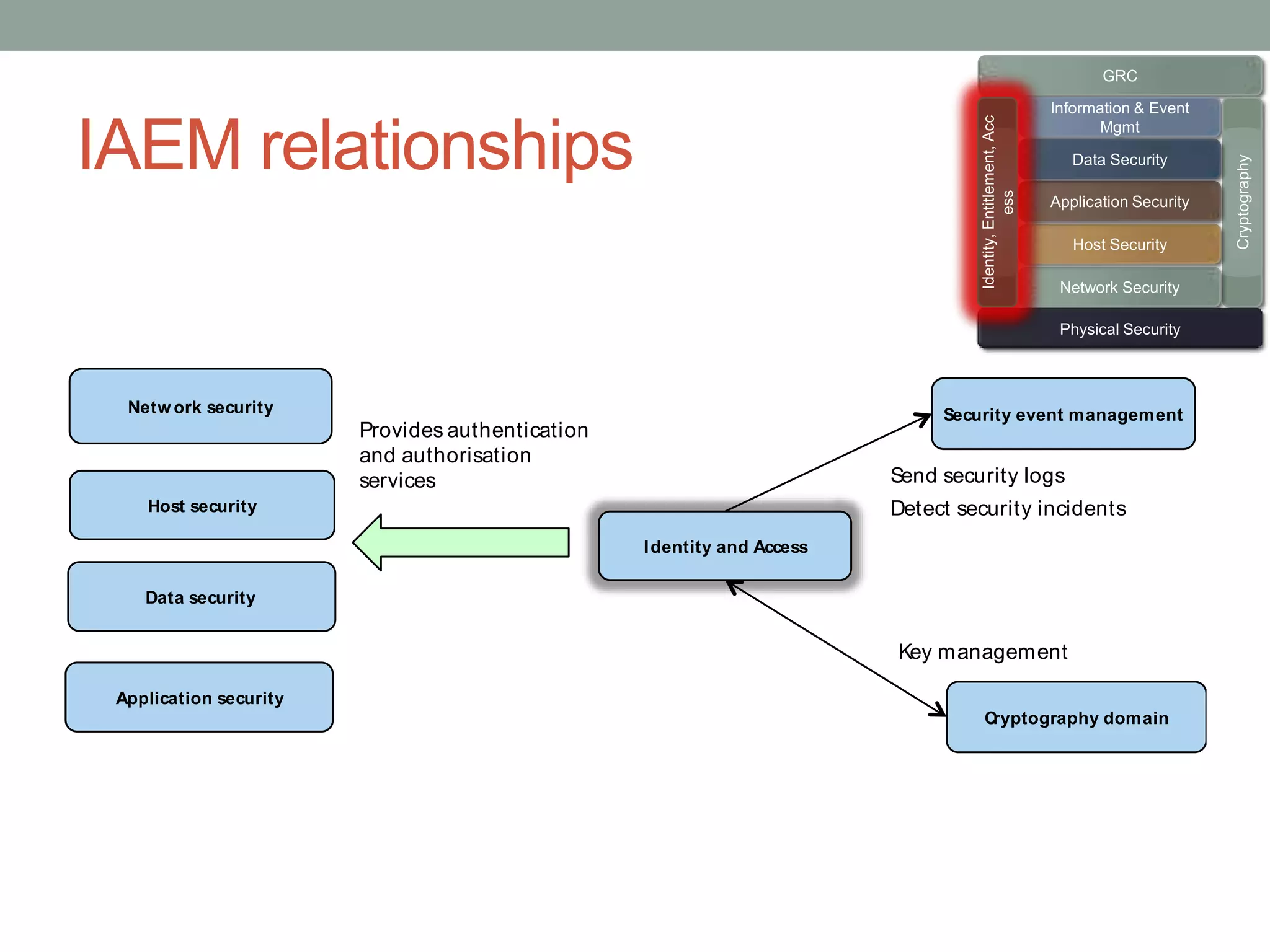
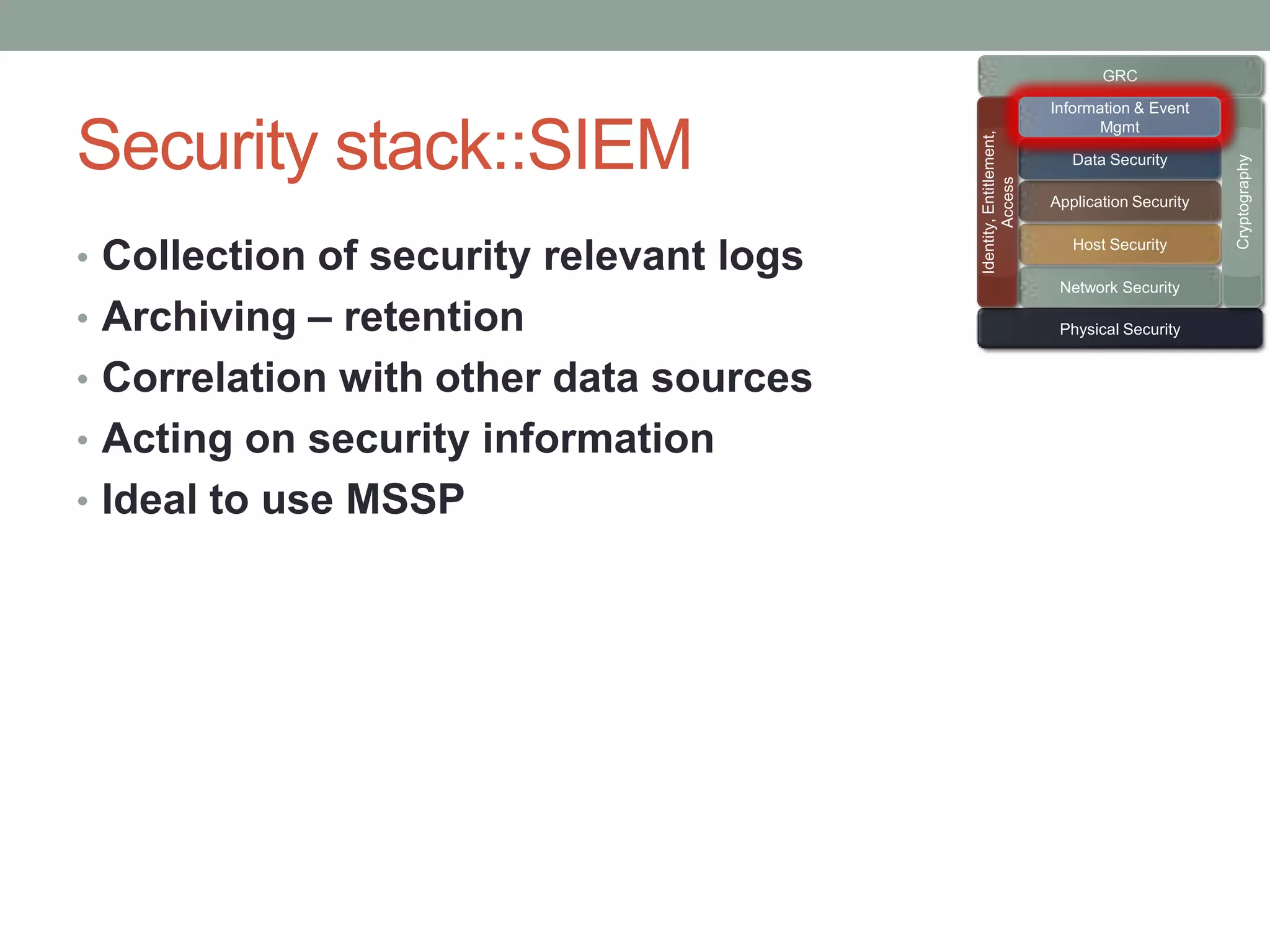
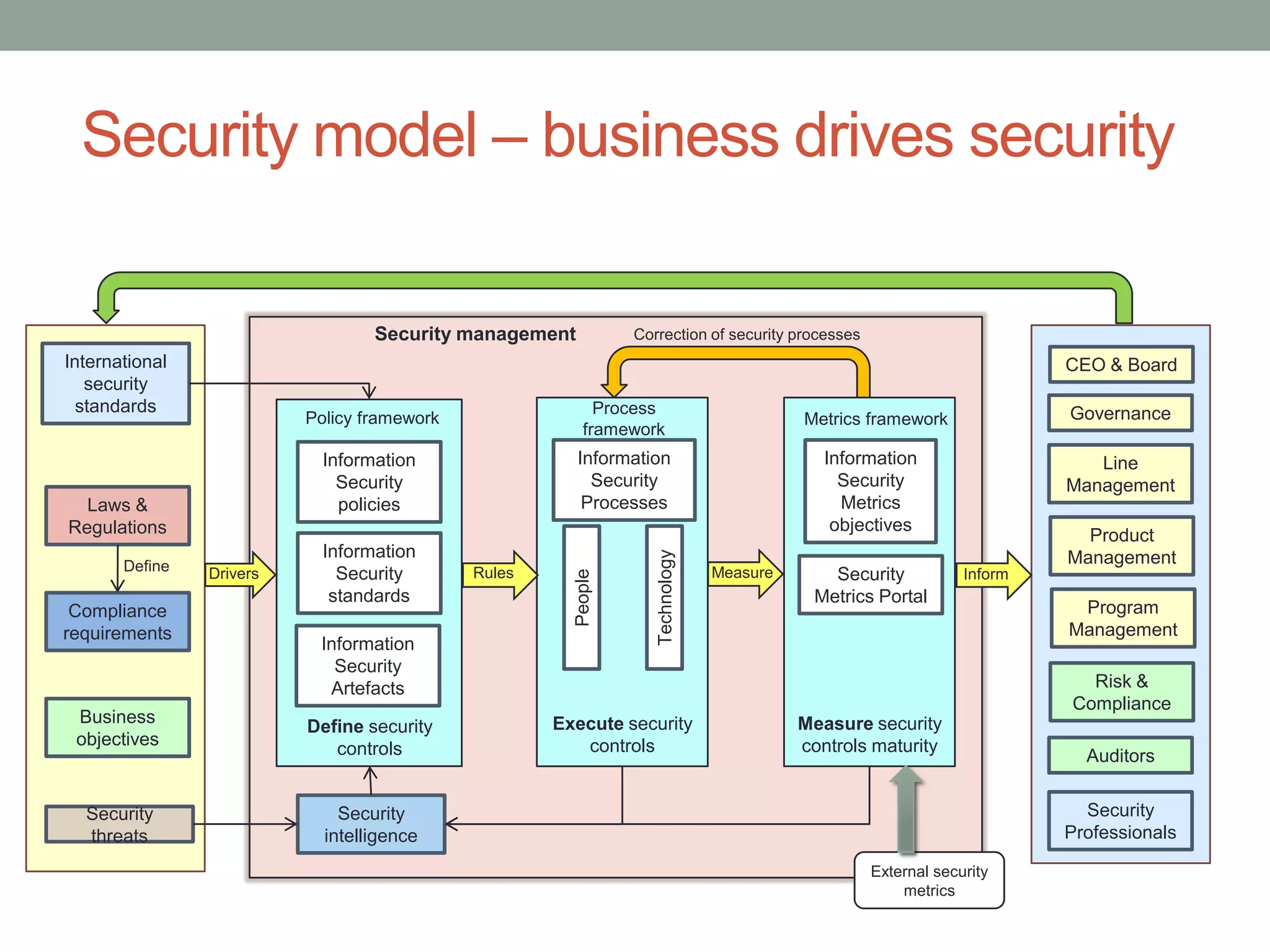
The document discusses security models essential for enhancing an organization's defense posture and strategy. Key topics include the relationship between business objectives and security processes, the implementation of a security policy framework, and the use of various security technologies and metrics. Ultimately, it emphasizes the importance of aligning security measures with business goals and leveraging established standards and controls to manage risks effectively.



![Information Security Policy framework
CIS
Business and
O
Information Security Policy Security
objectives
Data classification Employee Acceptable
policy Use Policy
CIO
Security
Information Technology Security Policy
objectives
IT
Security
IT security
standards
[reuse Architecture
internationally
accepted controls]
Technology Controls and
Technical Security processes
teams
architecture
repository
Security Processes
guidelines](https://image.slidesharecdn.com/securitymodelsforthreatmanagement-111109035725-phpapp01/75/Security-models-for-security-architecture-5-2048.jpg)