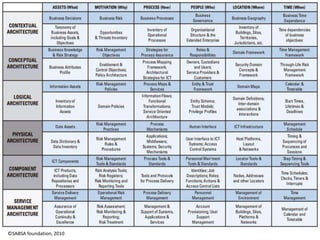
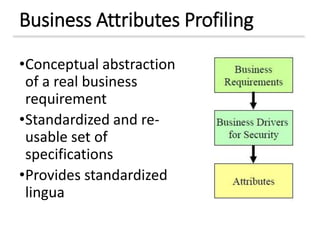
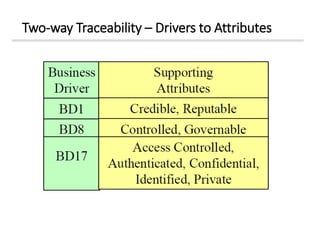
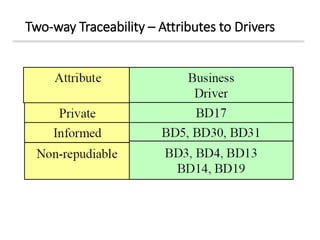
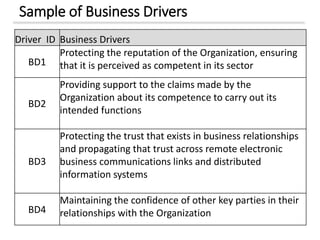
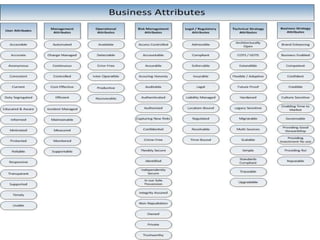
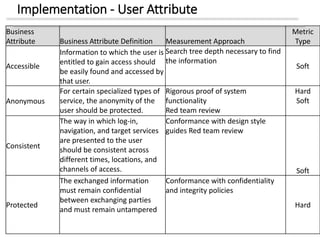
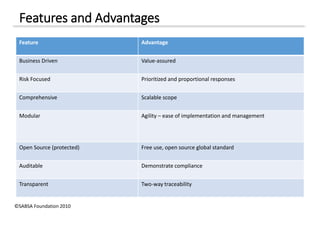
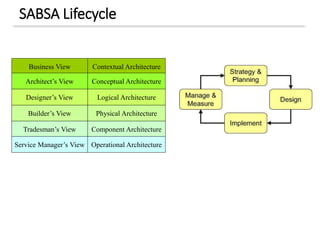
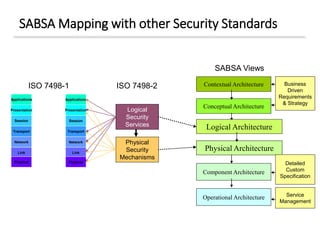
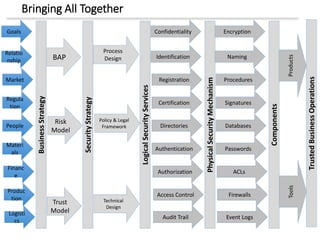
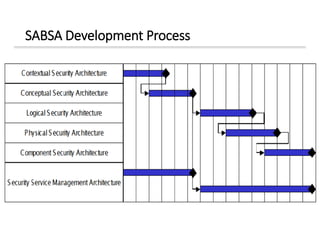
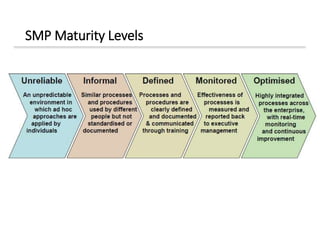
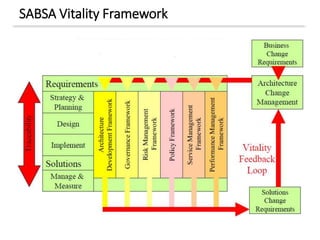
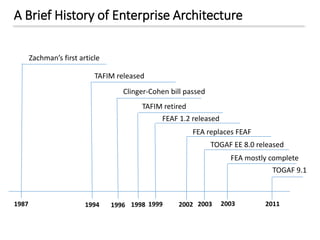
The document discusses enterprise security architecture, highlighting the importance of comprehensive methods for defining security across systems. It explores the Zachman framework for organizing architectural artifacts and introduces the SABSA model as a business-driven approach to security architecture. SABSA emphasizes alignment with business goals, risk management, and provides a detailed lifecycle for security architecture development.





![Zachman Framework
Source: zachmaninternational.com
[Executive Mgmt
Perspective]
[Business Mgmt
Perspective]
[Architect’s
Perspective]
[Engineer’s
Perspective]
[Technician’s
Perspective]](https://image.slidesharecdn.com/1-161114084643/85/Enterprise-Security-Architecture-7-320.jpg)