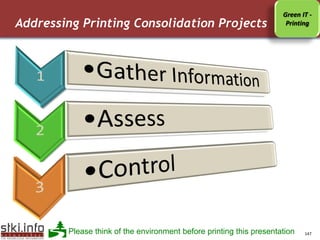
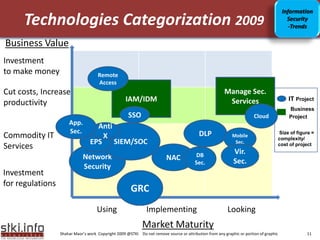
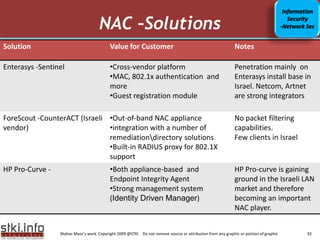
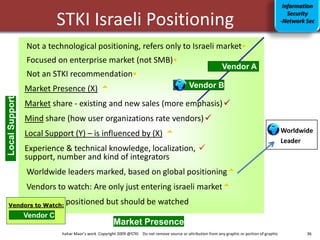
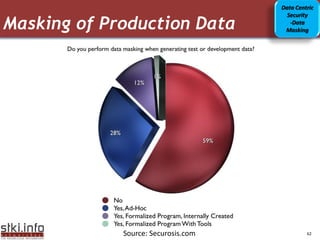
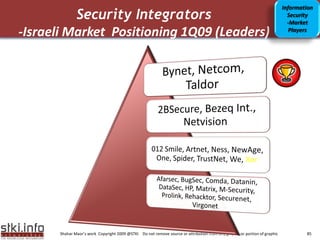
This document discusses various topics related to information security. It provides an agenda that includes information security, communication/networking, and green IT. It also includes to-do lists for 2009 related to applications and infrastructure. Additionally, it discusses trends in information security such as the security market size, security in the news, and security trends. It provides information on various security-related topics such as the underground economy, technologies categorization, security ratios in Israel, and sophisticated threat environments.




































































































![VOIP Israeli Market
Networking
-VOIP
There are two kinds of project possible: enterprise IPTel
and IP based Call-Centers
Israeli VOIP market is dominated by three main players:
Cisco, Nortel and Avaya
Your Text here Your Text here
Other players in Israel:
• Tadiran Telecom –Large install base (Mostly non IP based)
• 3COM, Alcatel –Lucent –Few implementations
• Siemens is back in Israel??? (Gores [Enterasys] acquired 51% of
Siemens, Oct 2008)
Shahar Maor’s work Copyright 2009 @STKI Do not remove source or attribution from any graphic or portion of graphic 106](https://image.slidesharecdn.com/infrastructureservices-summit2009-forpresentationv2-090325081107-phpapp02/85/STKI-Summit-2009-Infrastructure-Services-Trends-106-320.jpg)