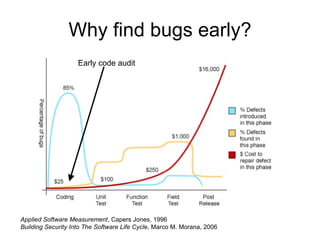
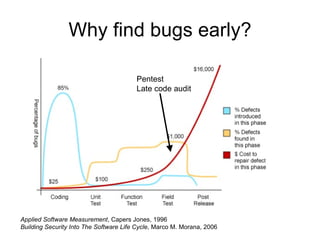
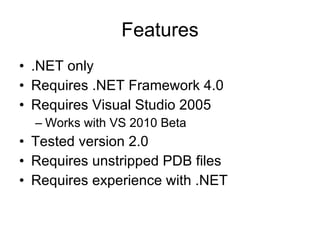
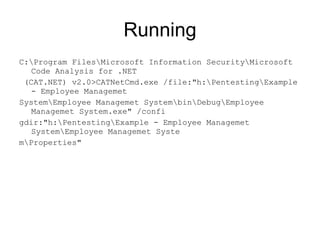
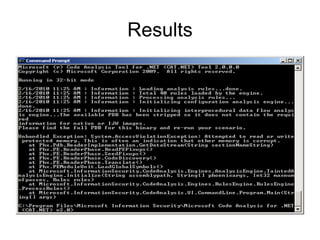
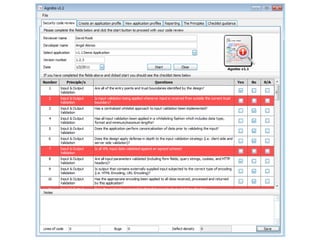
The document discusses the importance of source code analysis tools for early bug detection in software development, emphasizing that automated scanning can improve the efficiency and standardization of testing compared to manual methods. It reviews different tools such as Yasca, Owasp Code Crawler, Microsoft FxCop, and Agnitio, along with their functionality, requirements, and performance issues. Additionally, it includes insights on security integration in the software life cycle and highlights the limitations of black-box testing.