This document discusses secure software engineering practices, including:
1) Using architecture to structure applications so they mitigate exploits by limiting the impact of vulnerabilities.
2) Conducting code reviews with a variety of reviewers to catch issues and avoid "inbred" groupthink.
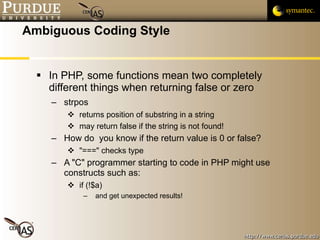
3) Using automated code checkers and complexity metrics to efficiently find security bugs, though their results still require manual review.































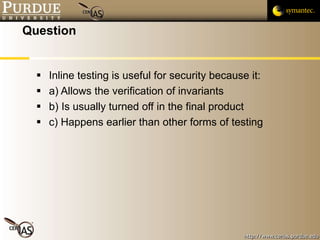
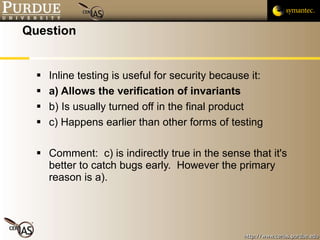
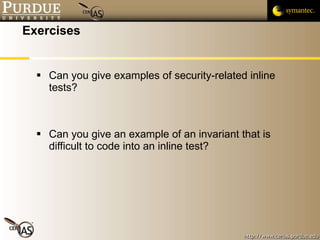
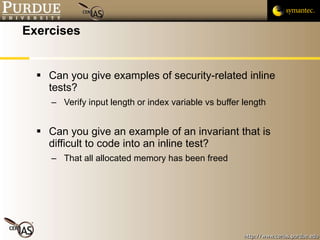




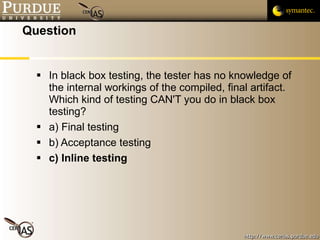
![Pascal Meunier [email_address] Contributors: Jared Robinson, Alan Krassowski, Craig Ozancin, Tim Brown, Wes Higaki, Melissa Dark, Chris Clifton, Gustavo Rodriguez-Rivera](https://image.slidesharecdn.com/4-securityassessmentandtesting-091013224326-phpapp02/85/4-Security-Assessment-And-Testing-58-320.jpg)