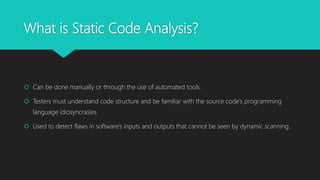
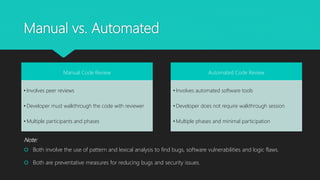
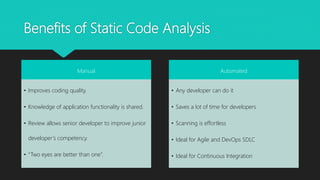
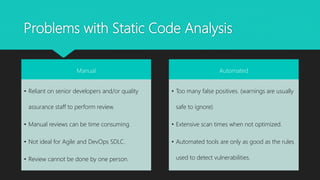
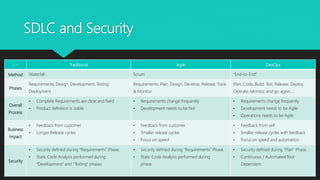
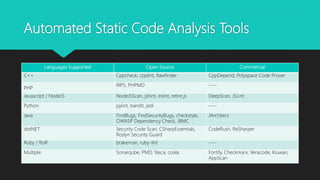
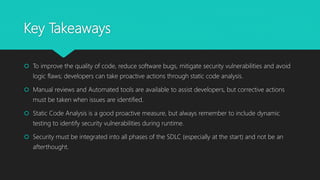
The document presents a comprehensive overview of static code analysis, including its definition, manual versus automated processes, benefits, and challenges. It highlights the importance of integrating security throughout the software development lifecycle (SDLC) and discusses various automated tools for analysis across different programming languages. Key takeaways emphasize the need for developers to proactively address code quality and security vulnerabilities while incorporating dynamic testing along with static analysis.