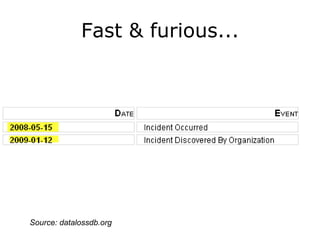
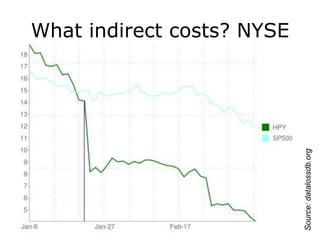
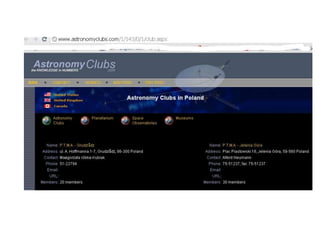
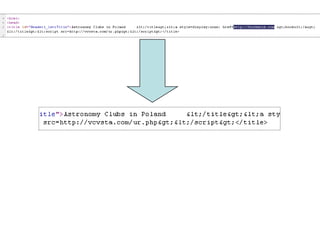
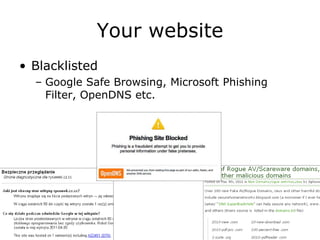
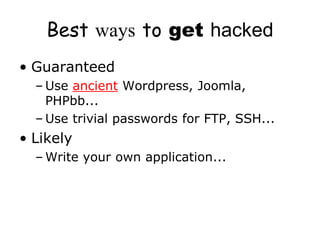
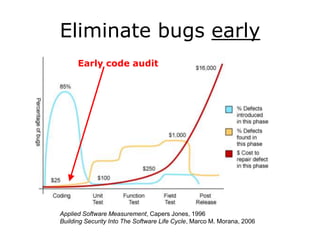
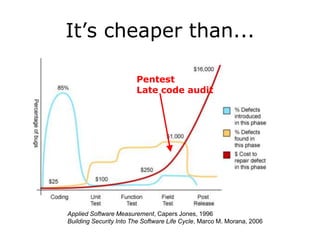
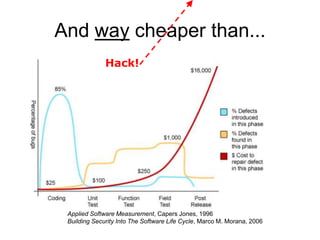
The document discusses the importance of application security, highlighting significant data breaches and their financial implications for companies, such as Sony's losses from the 2011 PSN outage. It emphasizes the necessity of building security into the software development life cycle to reduce costs associated with vulnerabilities and data loss. The presentation also touches on strategies for improving security practices and the potential economic impact of inadequate security measures.