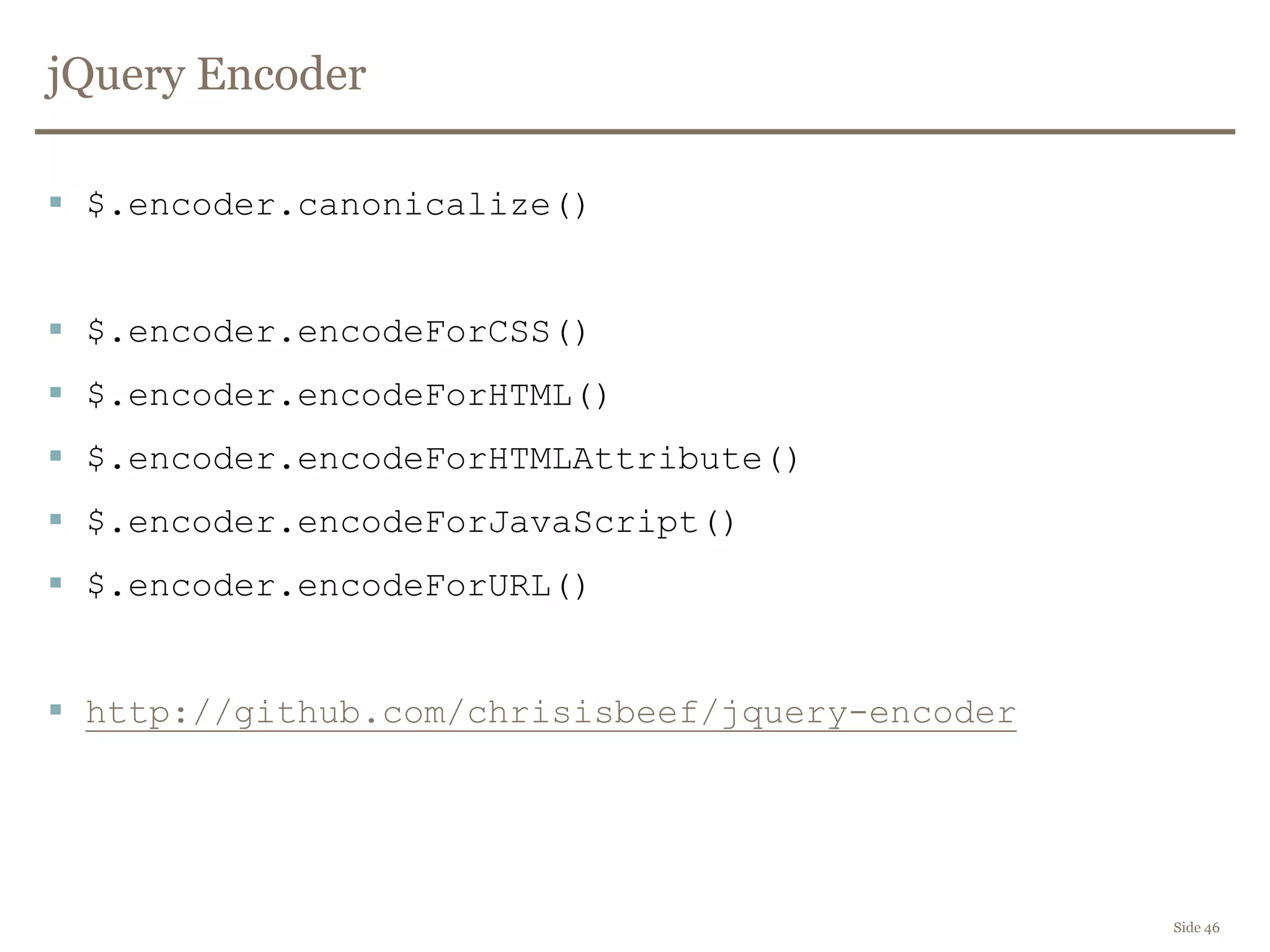
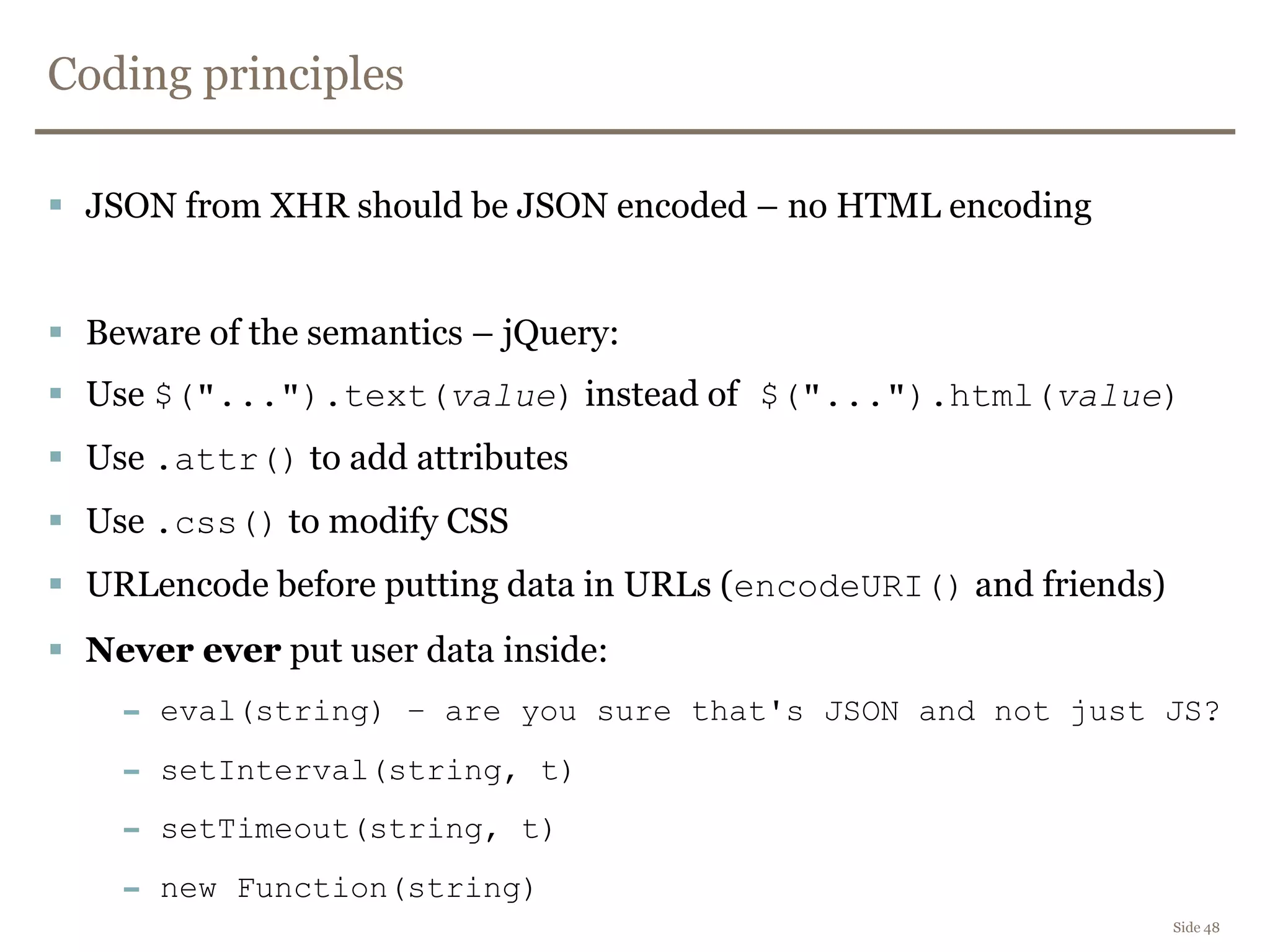
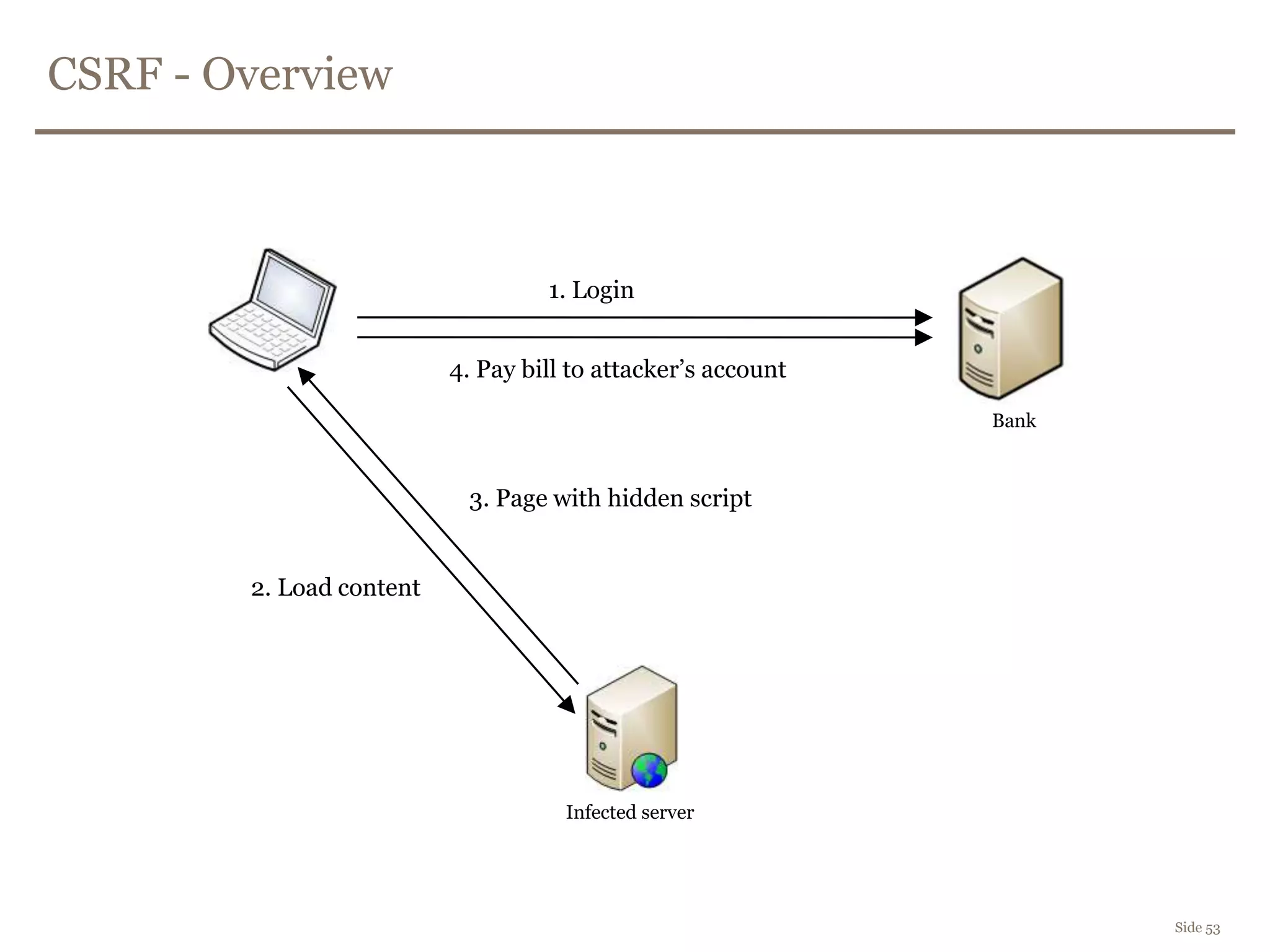
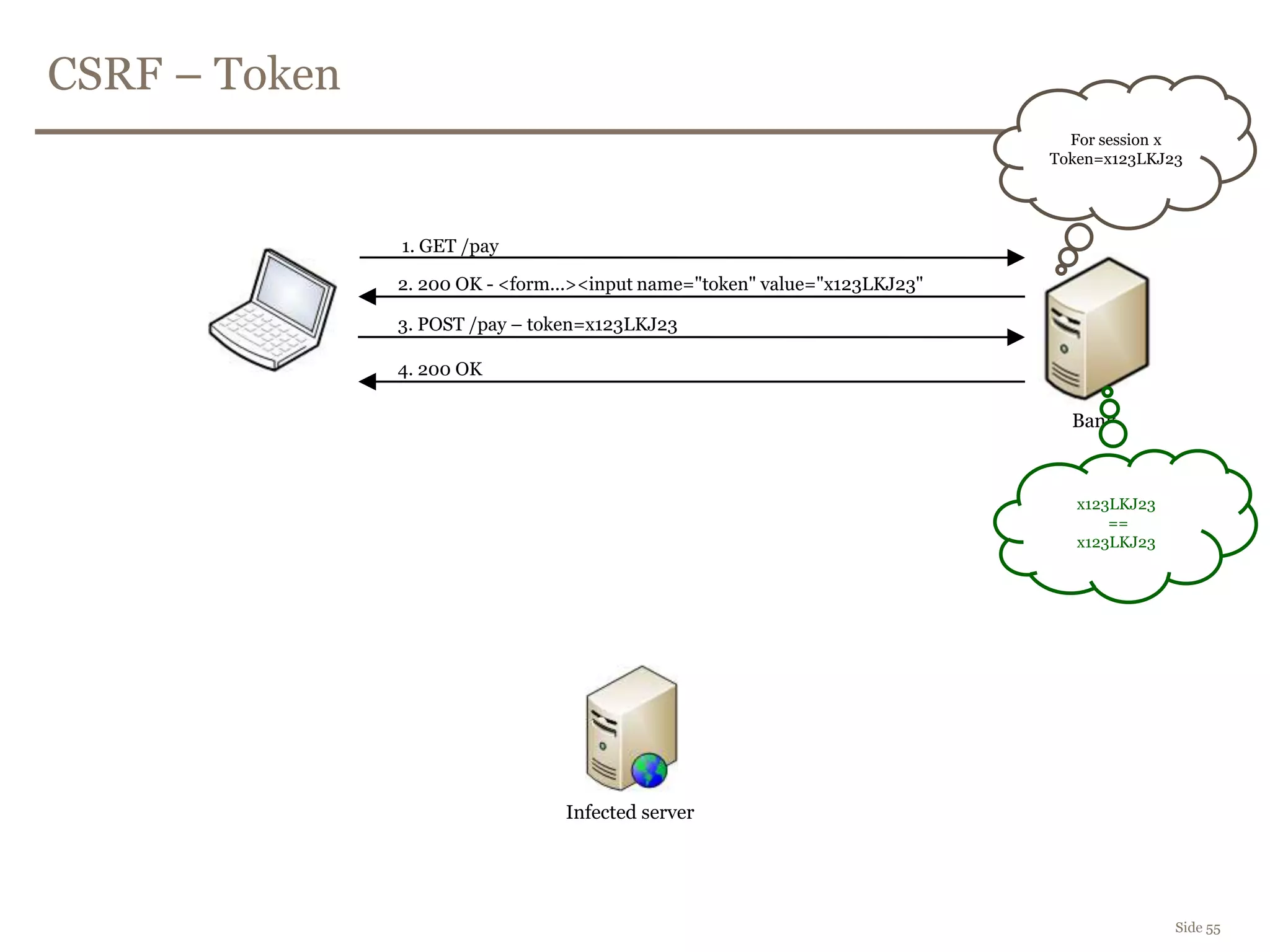
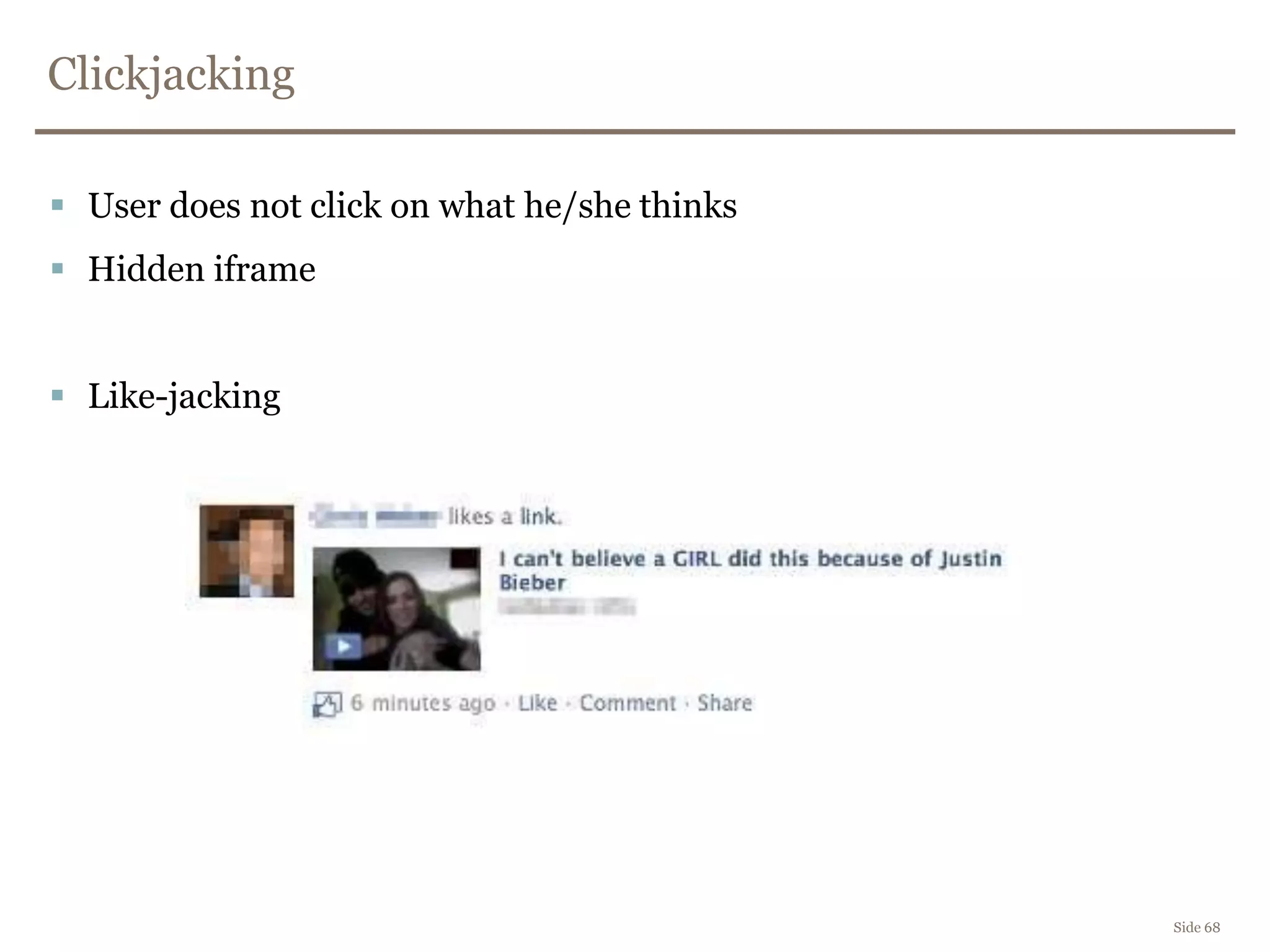
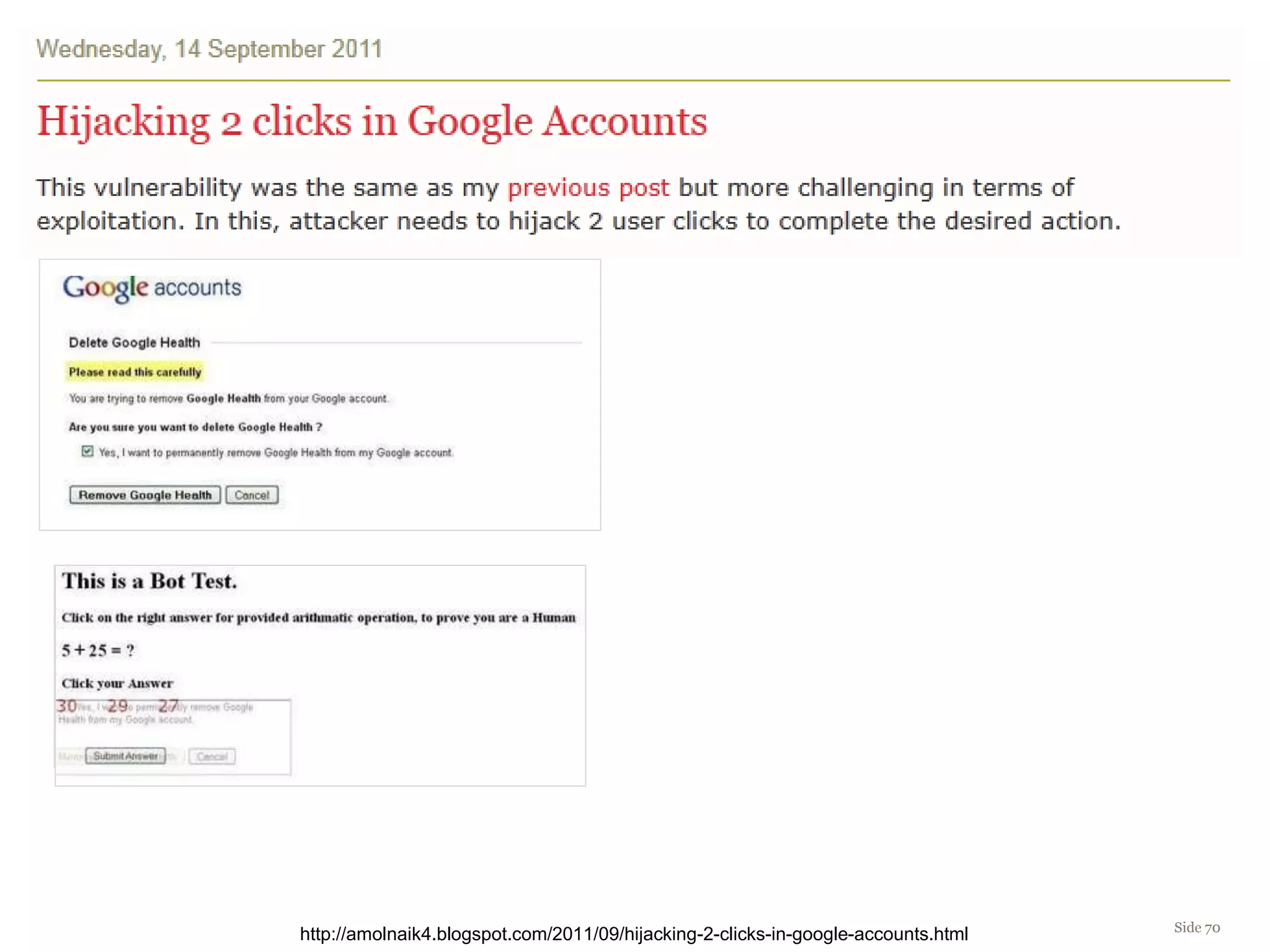
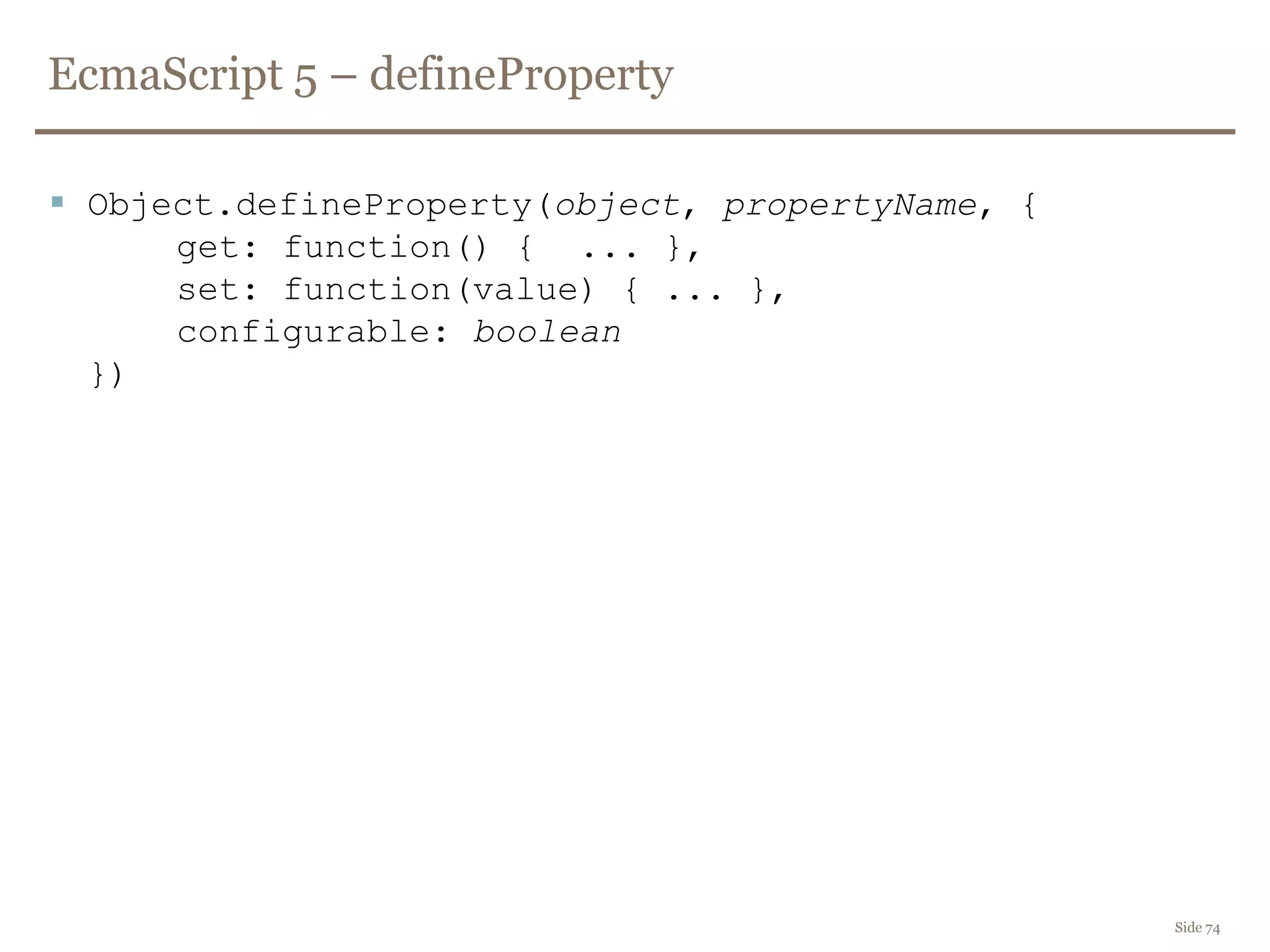
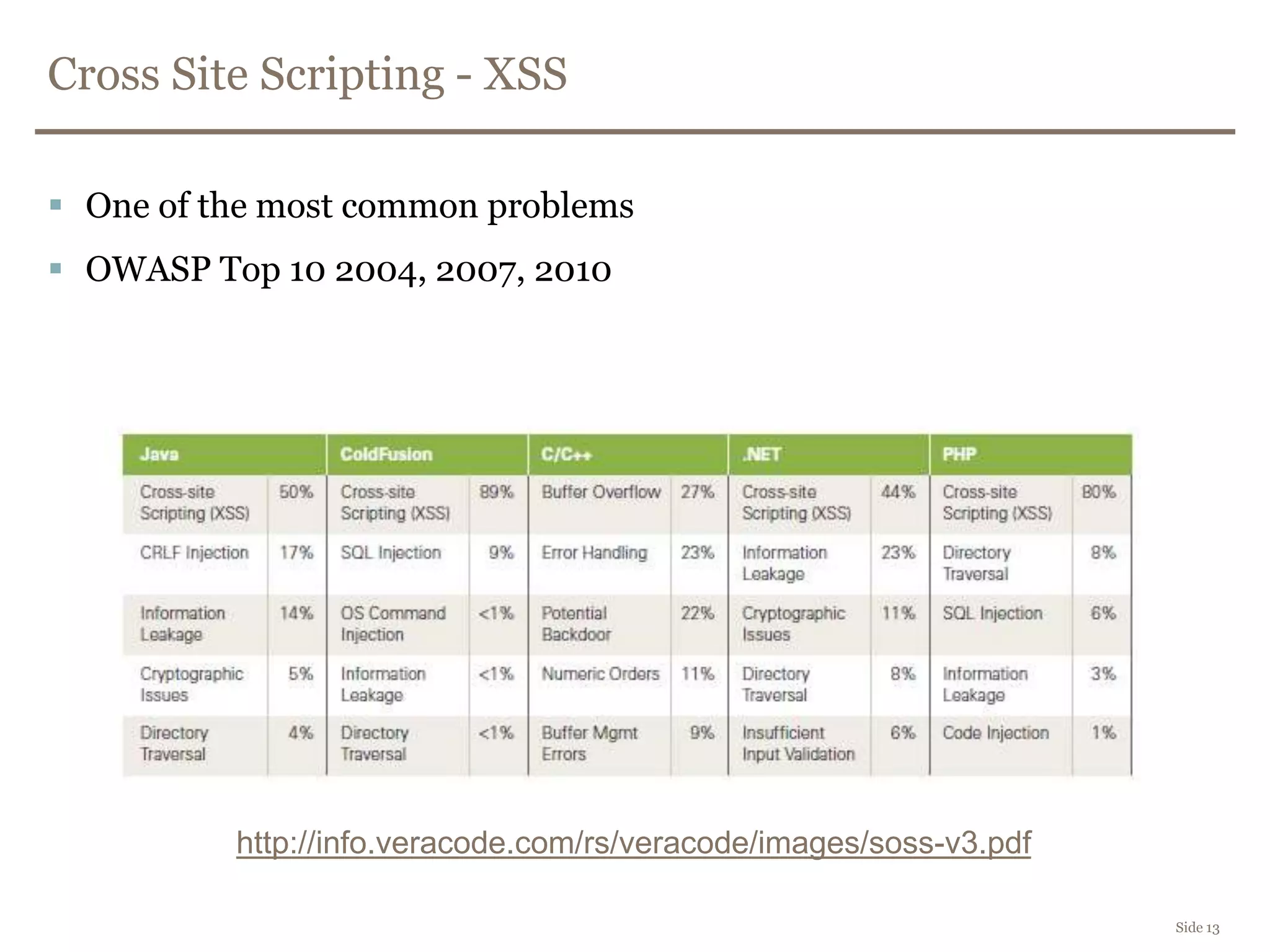
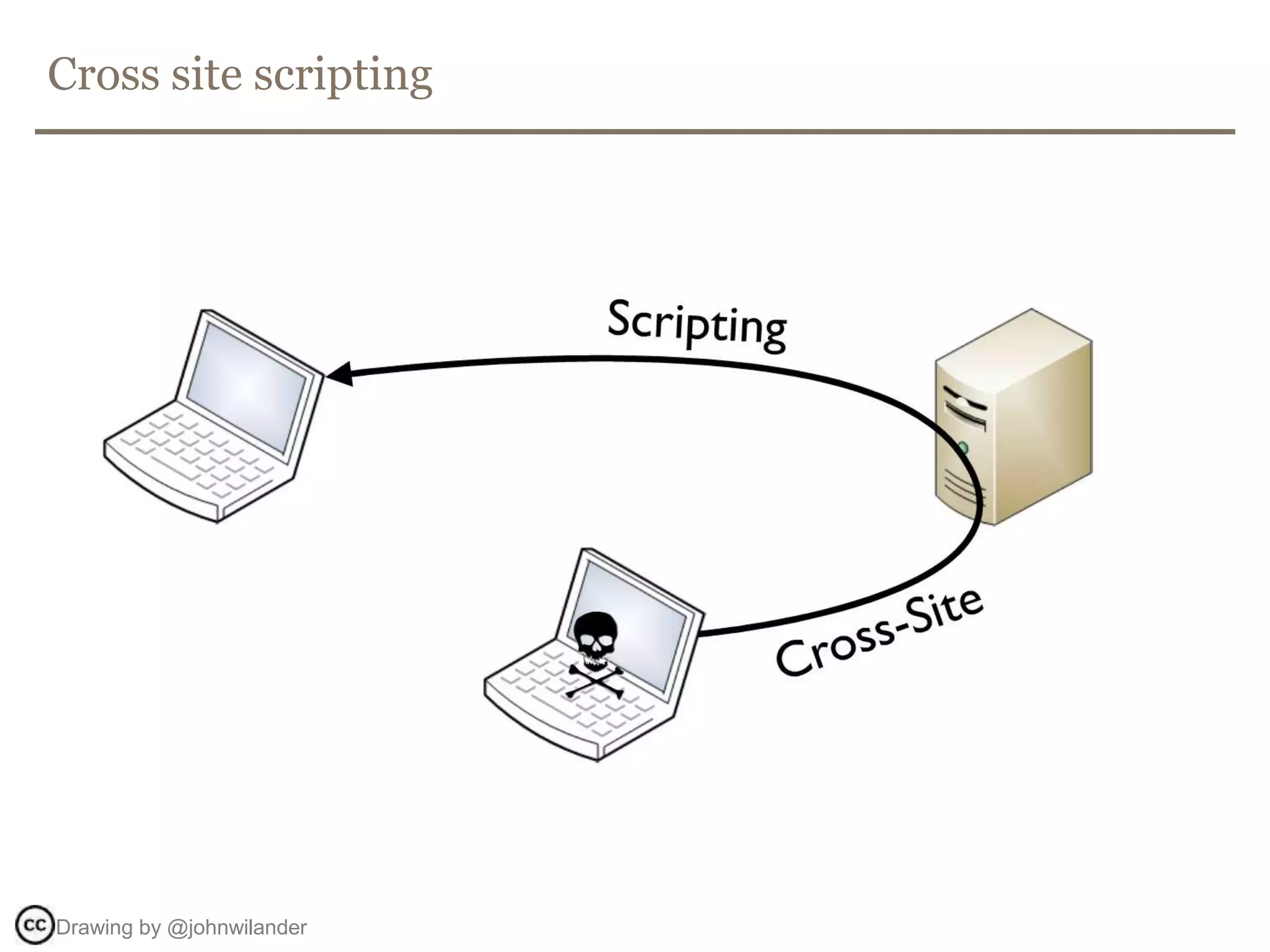
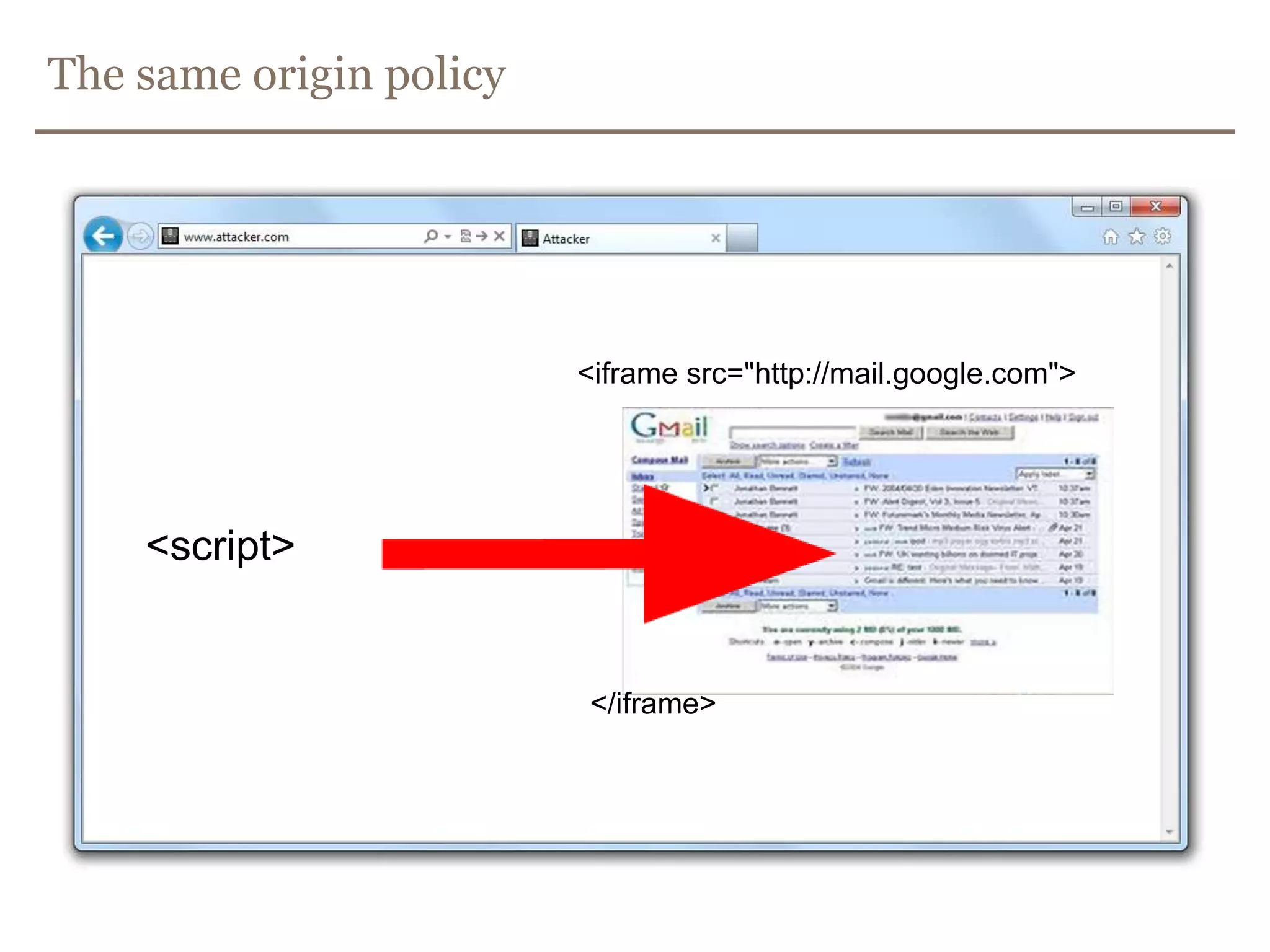
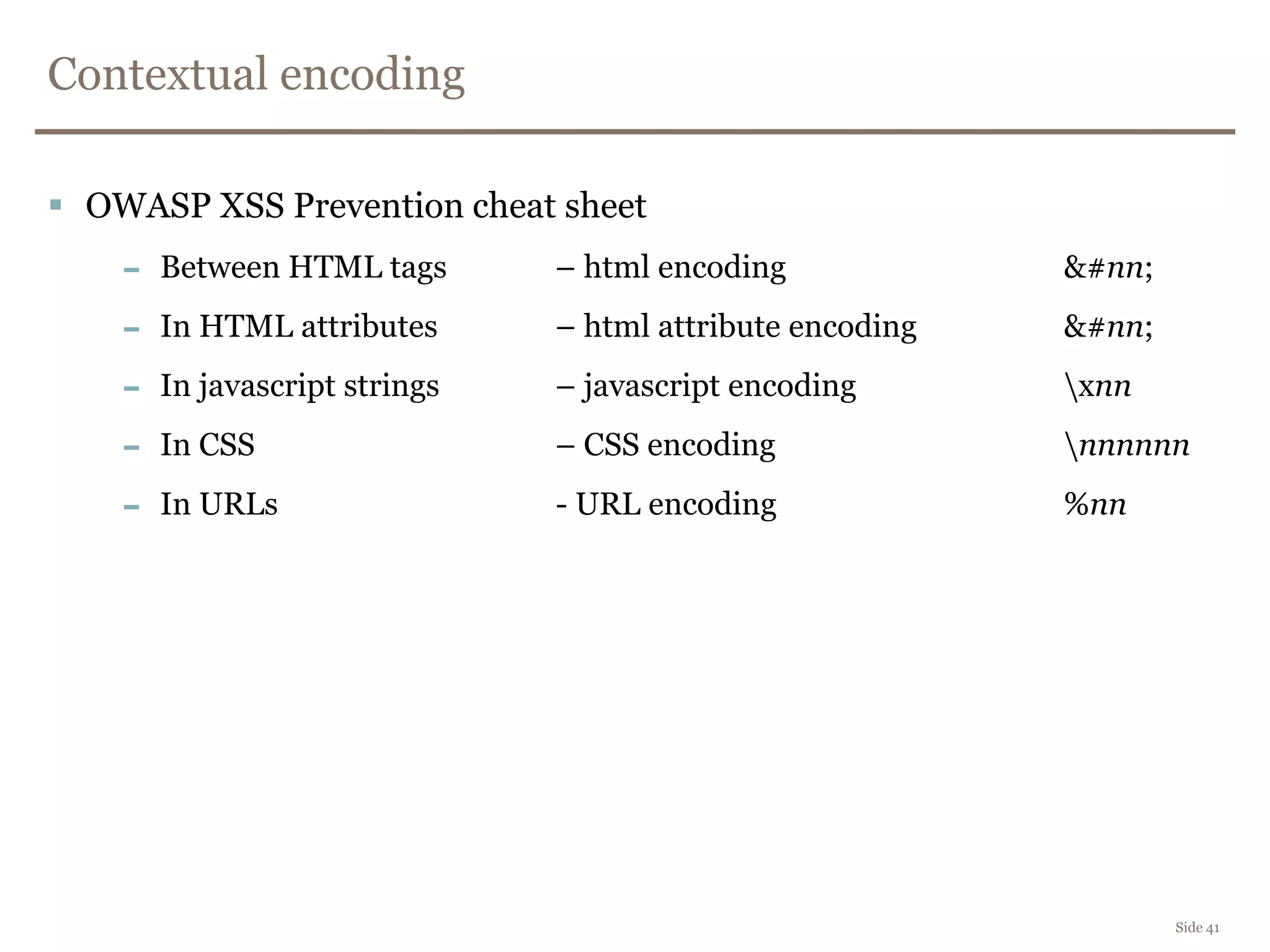
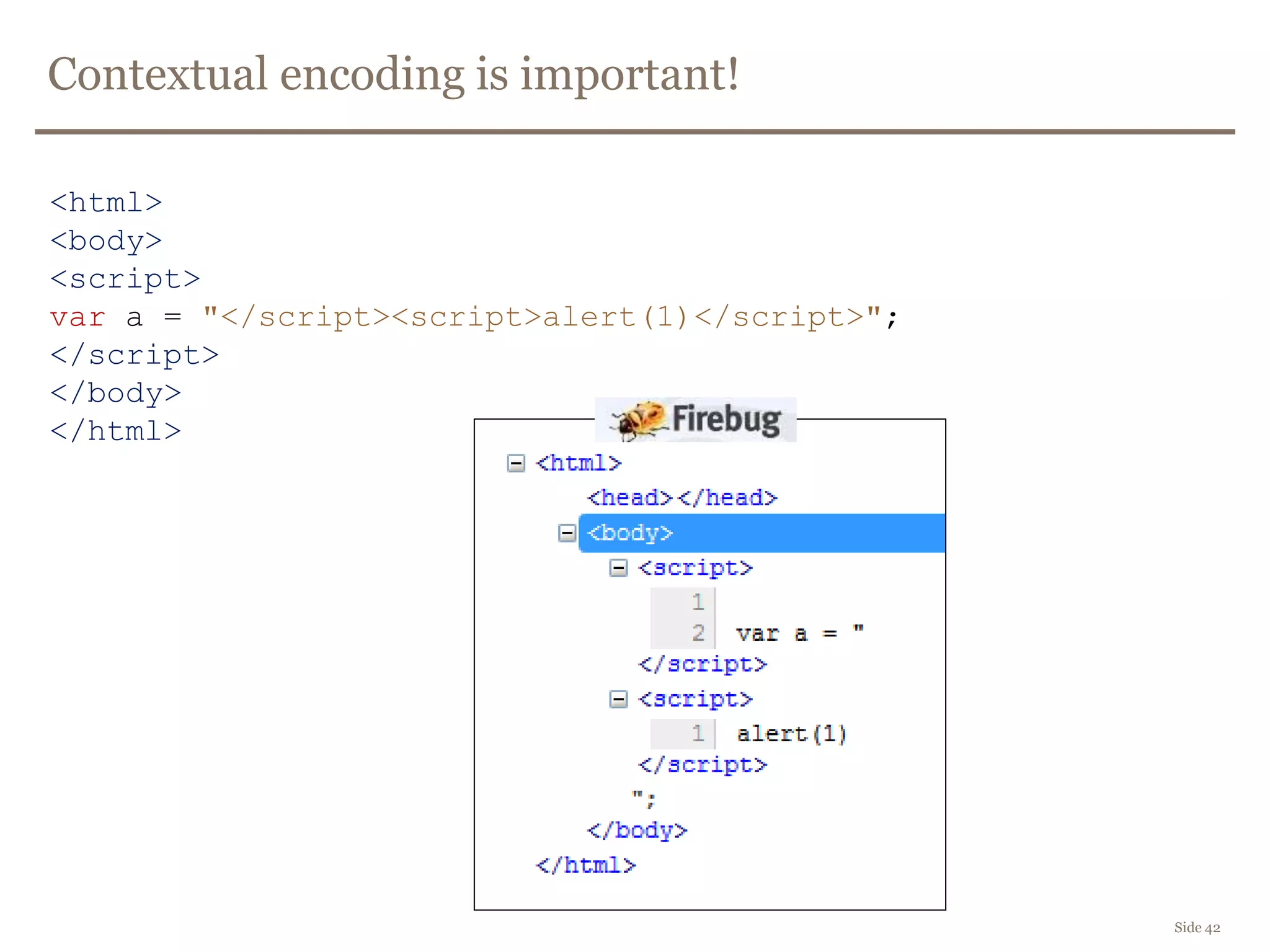
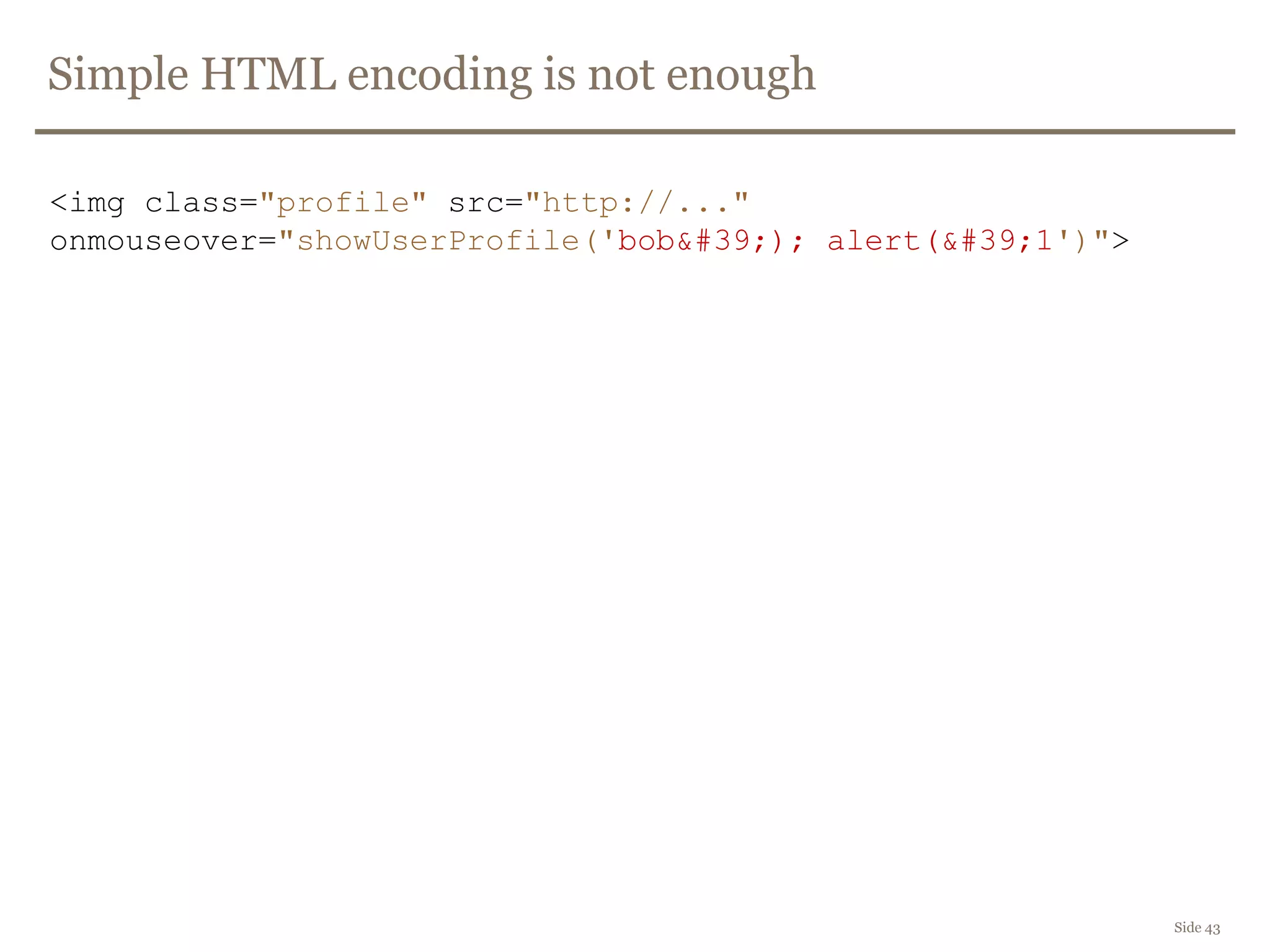
The document discusses web security, focusing on frontend vulnerabilities such as cross-site scripting (XSS) and cross-site request forgery (CSRF). It emphasizes the importance of contextual encoding, proper input validation, and secure coding practices to mitigate threats. Additionally, it introduces concepts like content security policy (CSP) and various HTML5 features to enhance security in web applications.








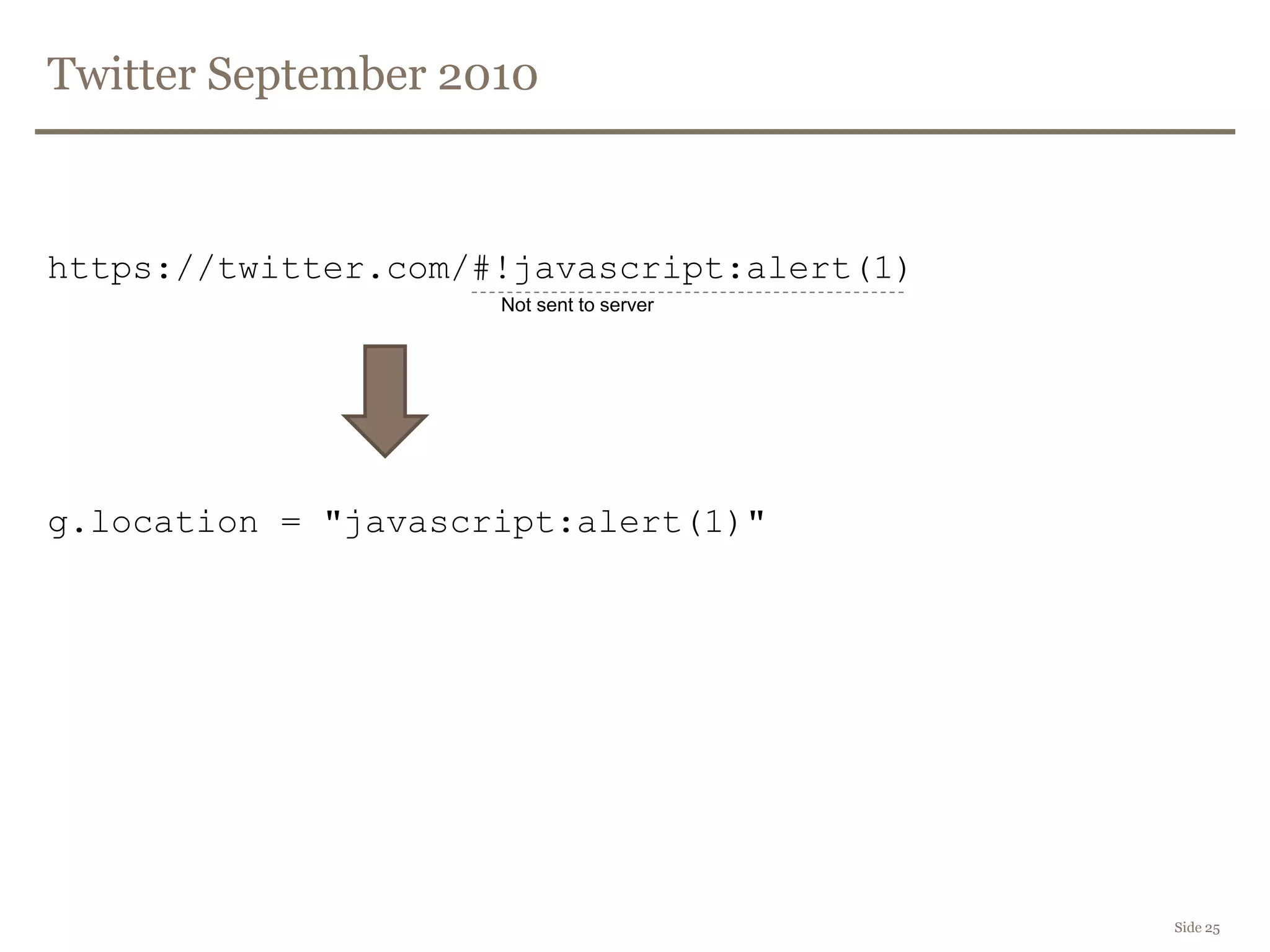
![Twitter September 2010
(function(g) {
var a = location.href.split("#!")[1];
if(a){
g.location = a;
}
})(window);
Goal:
https://twitter.com/#!/framsia
https://twitter.com/framsia
Side 24
http://blog.mindedsecurity.com/2010/09/twitter-domxss-wrong-fix-and-something.html](https://image.slidesharecdn.com/framsiaforslideshare-111110062153-phpapp02/75/Web-Application-Security-in-front-end-24-2048.jpg)
![First attempt to patch
var c = location.href.split("#!")[1];
if(c) {
window.location = c.replace(":", "");
} else {
return true;
}
Side 26
Replaces first occurence of
the search string.](https://image.slidesharecdn.com/framsiaforslideshare-111110062153-phpapp02/75/Web-Application-Security-in-front-end-26-2048.jpg)

![2nd attempt
(function(g){
var a = location.href.split("#!").[1];
if(a) {
g.location = a.replace(/:/gi, "");
}
})(window);
Side 28](https://image.slidesharecdn.com/framsiaforslideshare-111110062153-phpapp02/75/Web-Application-Security-in-front-end-28-2048.jpg)
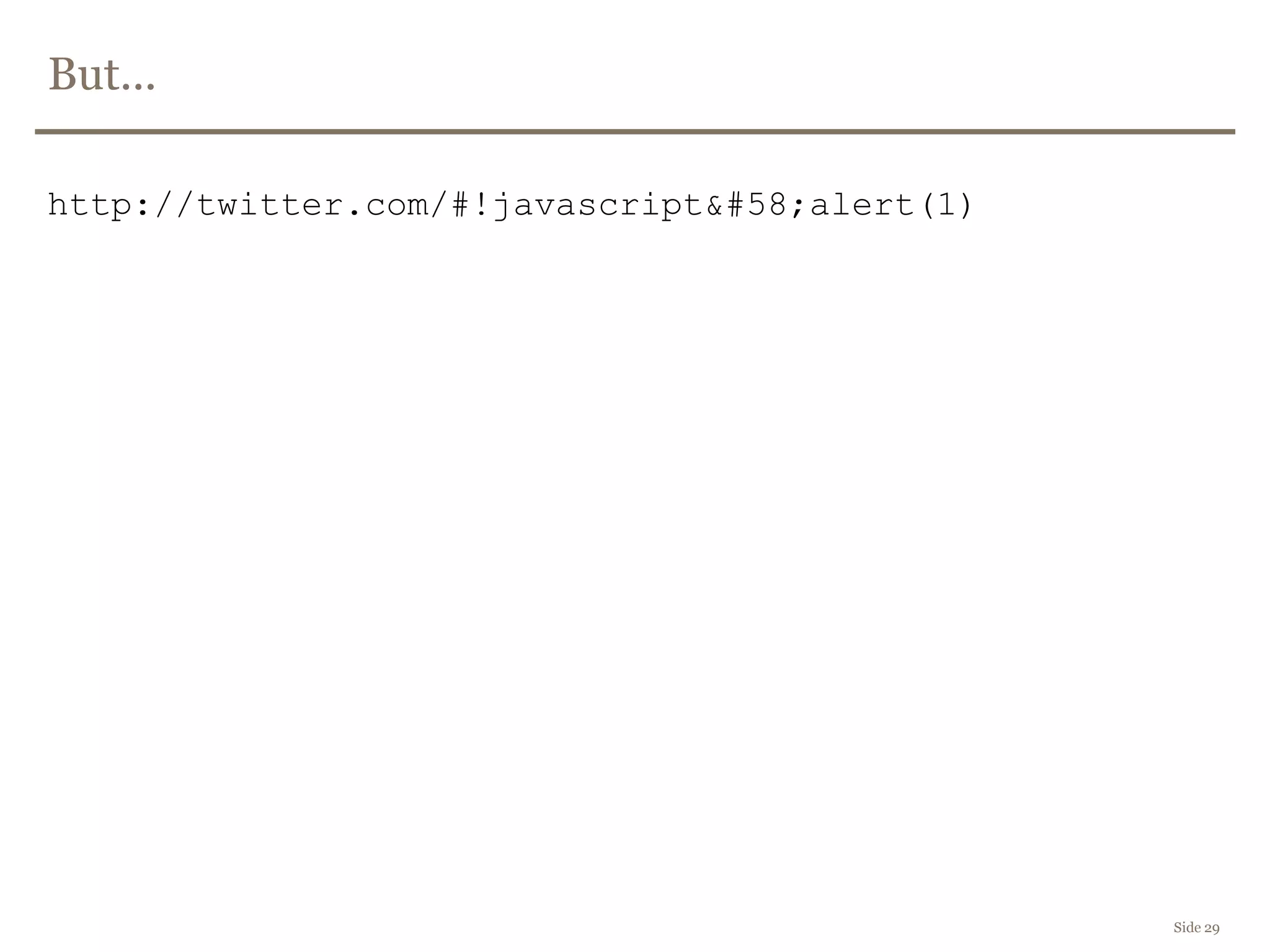
![Working patch
(function(g){
var a = location.href.split("#!")[1];
if(a) {
g.location.pathname = a;
}
})(window);
Side 30](https://image.slidesharecdn.com/framsiaforslideshare-111110062153-phpapp02/75/Web-Application-Security-in-front-end-30-2048.jpg)



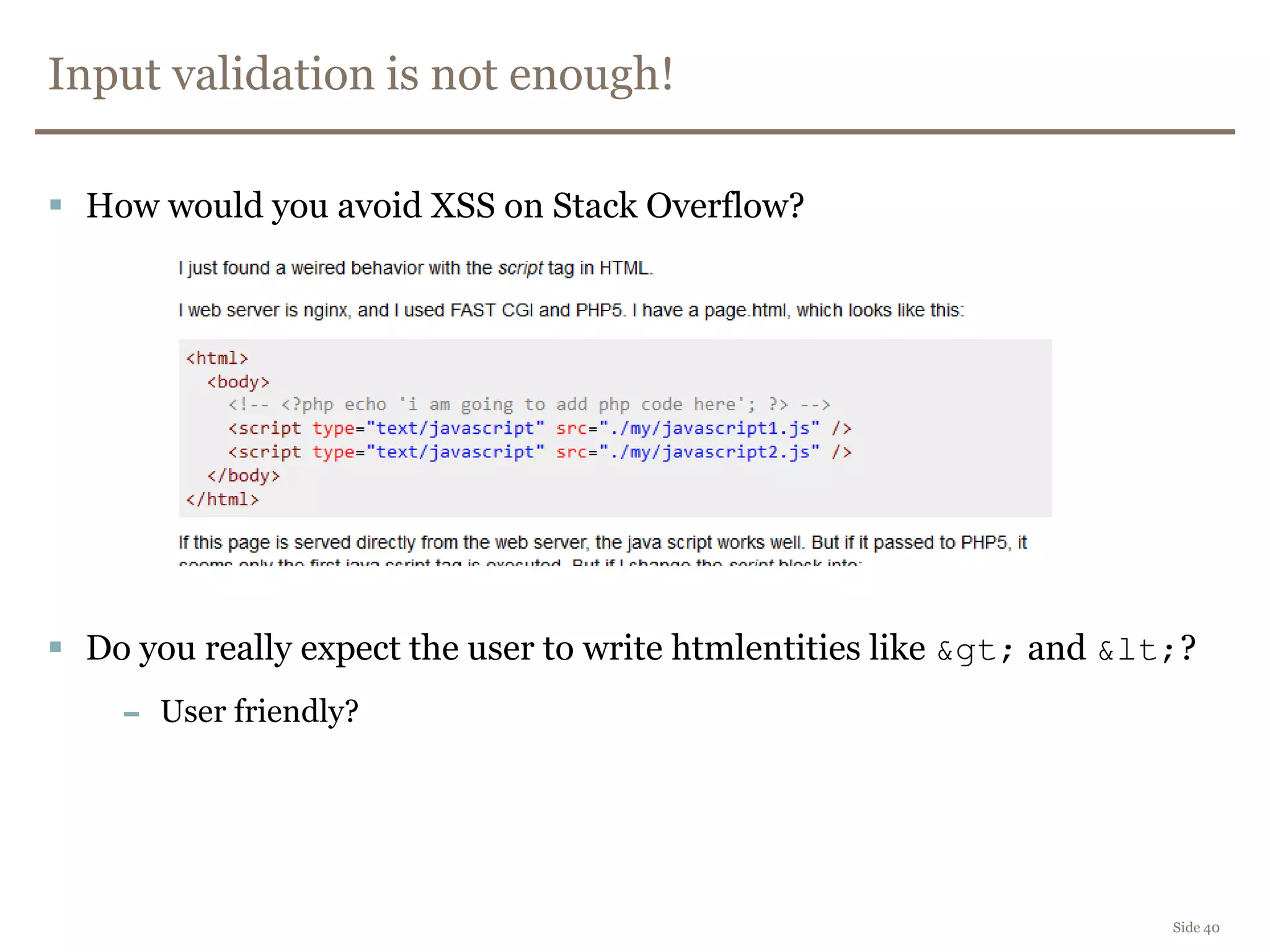
![Is input validation enough?
How do you validate an email address?
[a-z]+@[a-z]+.[a-z]{2,3}
[a-z'-A-ZæøåÆØÅ.]+@[a-z0-9-.]+.[a-z]{2,3}
Side 37](https://image.slidesharecdn.com/framsiaforslideshare-111110062153-phpapp02/75/Web-Application-Security-in-front-end-37-2048.jpg)
![From Wikipedia
The local-part of the email address may use any of these ASCII characters
RFC 5322 Section 3.2.3:
– Uppercase and lowercase English letters (a–z, A–Z) (ASCII: 65-90, 97-122)
– Digits 0 to 9 (ASCII: 48-57)
– Characters !#$%&'*+-/=?^_`{|}~ (ASCII: 33, 35-39, 42, 43, 45, 47, 61, 63, 94-96, 123-126)
– Character . (dot, period, full stop) provided that it is not the first or last
character, and provided also that it does not appear two or more times
consecutively (e.g. John..Doe@example.com).
– Special characters are allowed with restrictions including:
– Space and "(),:;<>@[] (ASCII: 32, 34, 40, 41, 44, 58, 59, 60, 62, 64, 91-93)](https://image.slidesharecdn.com/framsiaforslideshare-111110062153-phpapp02/75/Web-Application-Security-in-front-end-38-2048.jpg)
![From Wikipedia
Valid email addresses
– niceandsimple@example.com
– a.little.unusual@example.com
– much."more unusual"@example.com
– very.unusual."@".unusual.com@example.com
– very."(),:;<>[]".VERY."very @"very".unusual@cool.example.com](https://image.slidesharecdn.com/framsiaforslideshare-111110062153-phpapp02/75/Web-Application-Security-in-front-end-39-2048.jpg)
![Why you do NOT write your own HTML-cleaner/sanitizer
<IFRAME SRC="javascript:alert('XSS');"></IFRAME>
<SCRIPT/SRC="http://ha.ckers.org/xss.js"></SCRIPT>
<BODY onload!#$%&()*~+-_.,:;?@[/|]^`=alert("XSS")>
<META HTTP-EQUIV="Set-Cookie"
Content="USERID=<SCRIPT>alert('XSS')</SCRIPT>">
¼script¾alert(¢XSS¢)¼/script¾
<charset="x-mac-farsi">☼script ☾alert(1)//☼/script ☾
http://ha.ckers.org/xss.html](https://image.slidesharecdn.com/framsiaforslideshare-111110062153-phpapp02/75/Web-Application-Security-in-front-end-45-2048.jpg)