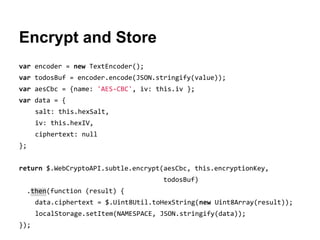
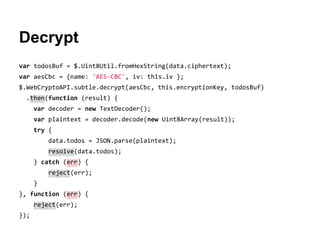
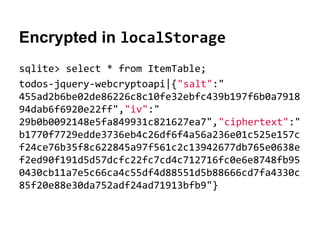
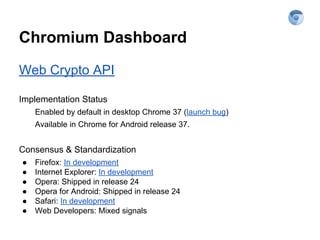
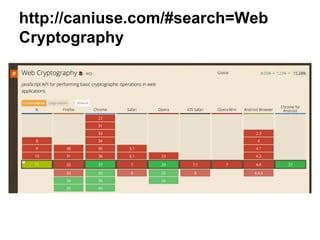
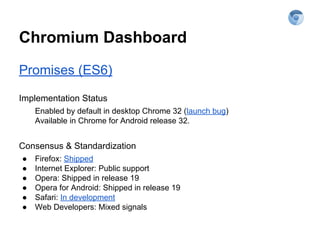
The document explores securing the TodoMVC application using the Web Cryptography API, focusing on cryptography concepts and potential vulnerabilities like sensitive data exposure. It discusses various cryptography methods such as hashing, encryption, and authentication while highlighting the importance of secure storage and transport mechanisms. Additionally, it covers the supporting technologies, standards, and browser implementations needed for effective web cryptography.


![TodoMVC Uses localStorage
Chrome keeps localStorage in an SQLite file:
OS X: ~/Library/Application Support/Google/Chrome/Default/Local Storage
Windows: %HOMEPATH%AppDataLocalGoogleChromeUser DataDefaultLocal Storage
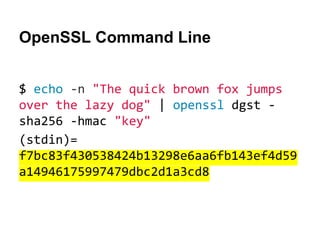
$ sqlite3 http_todomvc.com_0.localstorage
sqlite> select * from ItemTable;
todos-jquery|[{"id":"c8f7b7e1-88bf-451b-8aff-
04c9ac2544aa","title":"secure using Web
Cryptography API","completed":false}]](https://image.slidesharecdn.com/securingtodomvcusingthewebcryptographyapijqcon-140921130442-phpapp01/85/Securing-TodoMVC-Using-the-Web-Cryptography-API-8-320.jpg)











![Javascript Cryptography Considered
Harmful (circa 2010)
● Opinion on browser Javascript cryptography
○ "no reliable way for any piece of Javascript code to
verify its execution environment"
○ "can't outsource random number generation in a
cryptosystem"
○ "practically no value to doing crypto in Javascript
once you add SSL to the mix"
○ "store the key on that server [and] documents there"
http://www.matasano.com/articles/javascript-cryptography/
● Didn't consider the "offline" user experience](https://image.slidesharecdn.com/securingtodomvcusingthewebcryptographyapijqcon-140921130442-phpapp01/85/Securing-TodoMVC-Using-the-Web-Cryptography-API-26-320.jpg)






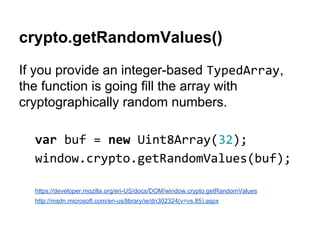
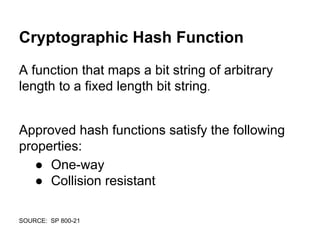

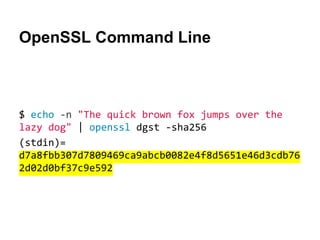
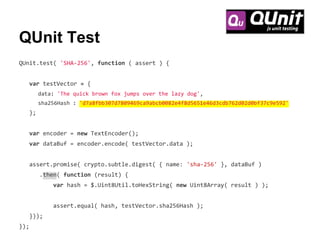







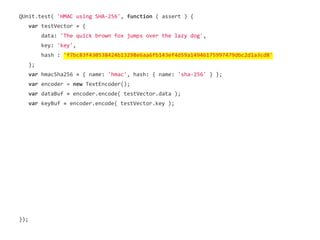
![QUnit.test( 'HMAC using SHA-256', function ( assert ) {
var testVector = {
data: 'The quick brown fox jumps over the lazy dog',
key: 'key',
hash : 'f7bc83f430538424b13298e6aa6fb143ef4d59a14946175997479dbc2d1a3cd8'
};
var hmacSha256 = { name: 'hmac', hash: { name: 'sha-256' } };
var encoder = new TextEncoder();
var dataBuf = encoder.encode( testVector.data );
var keyBuf = encoder.encode( testVector.key );
assert.promise( crypto.subtle.importKey( 'raw', keyBuf, hmacSha256,
true, ['sign', 'verify'] )
.then( function ( keyResult ) {
}));
});](https://image.slidesharecdn.com/securingtodomvcusingthewebcryptographyapijqcon-140921130442-phpapp01/85/Securing-TodoMVC-Using-the-Web-Cryptography-API-50-320.jpg)
![QUnit.test( 'HMAC using SHA-256', function ( assert ) {
var testVector = {
data: 'The quick brown fox jumps over the lazy dog',
key: 'key',
hash : 'f7bc83f430538424b13298e6aa6fb143ef4d59a14946175997479dbc2d1a3cd8'
};
var hmacSha256 = { name: 'hmac', hash: { name: 'sha-256' } };
var encoder = new TextEncoder();
var dataBuf = encoder.encode( testVector.data );
var keyBuf = encoder.encode( testVector.key );
assert.promise( crypto.subtle.importKey( 'raw', keyBuf, hmacSha256,
true, ['sign', 'verify'] )
.then( function ( keyResult ) {
return crypto.subtle.sign( hmacSha256, keyResult, dataBuf )
.then( function ( signResult ) {
var hash = $.Uint8Util.toHexString( new Uint8Array( signResult ) );
assert.equal( hash, testVector.hash );
})
}));
});](https://image.slidesharecdn.com/securingtodomvcusingthewebcryptographyapijqcon-140921130442-phpapp01/85/Securing-TodoMVC-Using-the-Web-Cryptography-API-51-320.jpg)
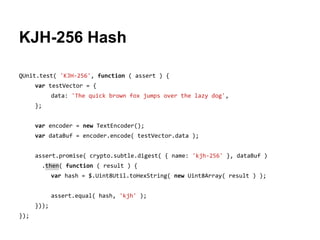
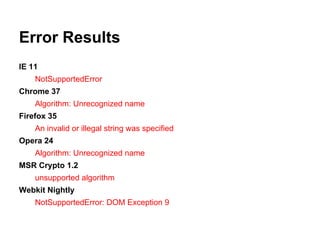
![QUnit.test( 'HMAC using KJH-256', function ( assert ) {
var testVector = {
data: 'The quick brown fox jumps over the lazy dog',
key: 'key'
};
var encoder = new TextEncoder();
var dataBuf = encoder.encode( testVector.data );
var keyBuf = encoder.encode( testVector.key );
var hmacKjh256 = { name: 'hmac', hash: { name: 'kjh-256' } };
assert.promise( crypto.subtle.importKey( 'raw', keyBuf, hmacKjh256,
true, ['sign', 'verify'] )
.then( function ( keyResult ) {
return crypto.subtle.sign( hmacKjh256, keyResult, dataBuf )
.then( function ( signResult ) {
var hash = $.Uint8Util.toHexString( new Uint8Array( signResult ) );
assert.equal( hash, 'kjh' );
})
}));
});](https://image.slidesharecdn.com/securingtodomvcusingthewebcryptographyapijqcon-140921130442-phpapp01/85/Securing-TodoMVC-Using-the-Web-Cryptography-API-54-320.jpg)




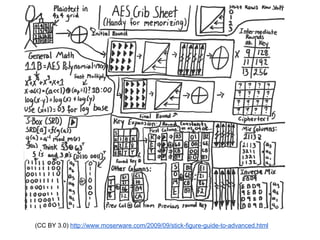

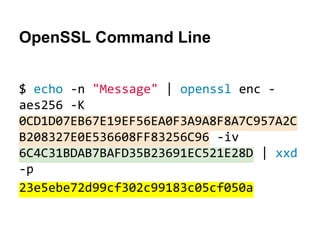
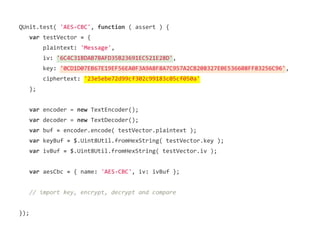
![assert.promise( crypto.subtle.importKey( 'raw', keyBuf, { name: 'AES-CBC' },
true, ['encrypt', 'decrypt'] )
.then( function ( encryptionKey ) {
}));](https://image.slidesharecdn.com/securingtodomvcusingthewebcryptographyapijqcon-140921130442-phpapp01/85/Securing-TodoMVC-Using-the-Web-Cryptography-API-63-320.jpg)
![assert.promise( crypto.subtle.importKey( 'raw', keyBuf, { name: 'AES-CBC' },
true, ['encrypt', 'decrypt'] )
.then( function ( encryptionKey ) {
return crypto.subtle.encrypt( aesCbc, encryptionKey, buf )
.then( function ( encryptResult ) {
var encryptBuf = new Uint8Array( encryptResult );
var ciphertext = $.Uint8Util.toHexString( encryptBuf );
assert.equal( ciphertext, testVector.ciphertext );
});
}));](https://image.slidesharecdn.com/securingtodomvcusingthewebcryptographyapijqcon-140921130442-phpapp01/85/Securing-TodoMVC-Using-the-Web-Cryptography-API-64-320.jpg)
![assert.promise( crypto.subtle.importKey( 'raw', keyBuf, { name: 'AES-CBC' },
true, ['encrypt', 'decrypt'] )
.then( function ( encryptionKey ) {
return crypto.subtle.encrypt( aesCbc, encryptionKey, buf )
.then( function ( encryptResult ) {
var encryptBuf = new Uint8Array( encryptResult );
var ciphertext = $.Uint8Util.toHexString( encryptBuf );
assert.equal( ciphertext, testVector.ciphertext );
return crypto.subtle.decrypt( aesCbc, encryptionKey, encryptBuf )
.then( function ( decryptResult ) {
var plaintext = decoder.decode( new Uint8Array( decryptResult ) );
assert.equal( plaintext, testVector.plaintext );
});
});
}));](https://image.slidesharecdn.com/securingtodomvcusingthewebcryptographyapijqcon-140921130442-phpapp01/85/Securing-TodoMVC-Using-the-Web-Cryptography-API-65-320.jpg)

![function importKey () {
return crypto.subtle.importKey( 'raw', keyBuf, { name: 'AES-CBC' },
true, ['encrypt', 'decrypt'] )
}
function encrypt ( importedKey ) {
encryptionKey = importedKey;
return crypto.subtle.encrypt( aesCbc, encryptionKey, buf );
}
function decrypt ( encryptResult ) {
var encryptBuf = new Uint8Array( encryptResult );
var ciphertext = $.Uint8Util.toHexString( encryptBuf );
assert.equal( ciphertext, testVector.ciphertext );
return crypto.subtle.decrypt( aesCbc, encryptionKey, encryptBuf );
}](https://image.slidesharecdn.com/securingtodomvcusingthewebcryptographyapijqcon-140921130442-phpapp01/85/Securing-TodoMVC-Using-the-Web-Cryptography-API-67-320.jpg)
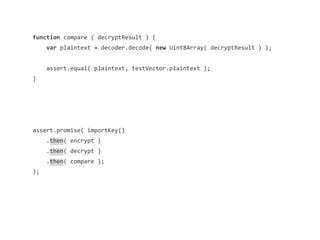





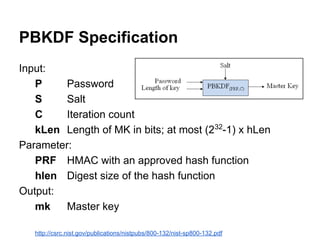
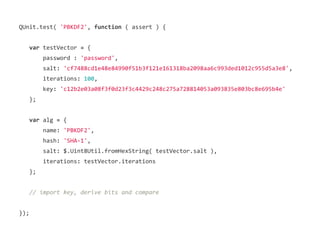
![var passwordBuf = decoder.decode( testVector.password );
assert.promise( crypto.subtle.importKey('raw', passwordBuf, 'PBKDF2',
false, ['deriveKey'])
.then(function ( keyResult ) {
}));](https://image.slidesharecdn.com/securingtodomvcusingthewebcryptographyapijqcon-140921130442-phpapp01/85/Securing-TodoMVC-Using-the-Web-Cryptography-API-76-320.jpg)
![var passwordBuf = decoder.decode( testVector.password );
assert.promise( crypto.subtle.importKey('raw', passwordBuf, 'PBKDF2',
false, ['deriveKey'])
.then(function ( keyResult ) {
return crypto.subtle.deriveBits( alg, keyResult, 256 )
.then(function ( deriveResult ) {
var deriveBuf = new Uint8Array( deriveResult );
var key = $.Uint8Util.toHexString( deriveBuf );
assert.equal( key, testVector.key );
});
}));](https://image.slidesharecdn.com/securingtodomvcusingthewebcryptographyapijqcon-140921130442-phpapp01/85/Securing-TodoMVC-Using-the-Web-Cryptography-API-77-320.jpg)
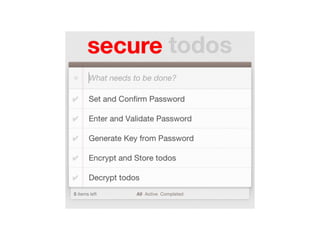
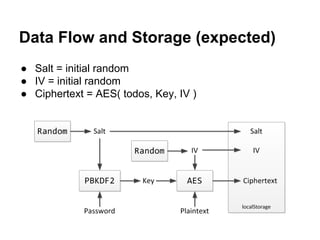
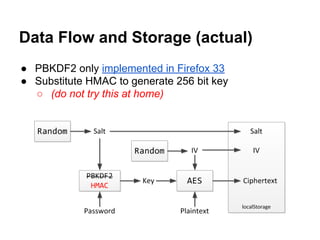
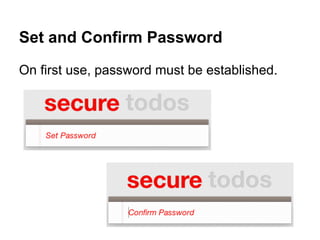




![Generate Key from Password
return $.WebCryptoAPI.subtle.importKey('raw', this.salt, hmacSha256,
true, ['sign', 'verify'])
.then(function (keyResult) {
});](https://image.slidesharecdn.com/securingtodomvcusingthewebcryptographyapijqcon-140921130442-phpapp01/85/Securing-TodoMVC-Using-the-Web-Cryptography-API-91-320.jpg)
![Generate Key from Password
return $.WebCryptoAPI.subtle.importKey('raw', this.salt, hmacSha256,
true, ['sign', 'verify'])
.then(function (keyResult) {
return $.WebCryptoAPI.subtle.sign(hmacSha256, keyResult, buf)
.then(function (signResult) {
});
});](https://image.slidesharecdn.com/securingtodomvcusingthewebcryptographyapijqcon-140921130442-phpapp01/85/Securing-TodoMVC-Using-the-Web-Cryptography-API-92-320.jpg)
![Generate Key from Password
return $.WebCryptoAPI.subtle.importKey('raw', this.salt, hmacSha256,
true, ['sign', 'verify'])
.then(function (keyResult) {
return $.WebCryptoAPI.subtle.sign(hmacSha256, keyResult, buf)
.then(function (signResult) {
var keyBuf = new Uint8Array(signResult);
// importKey for later AES encryption
return $.WebCryptoAPI.subtle.importKey('raw', keyBuf, {name: 'AES-CBC'},
true, ['encrypt', 'decrypt'])
.then(function (result) {
});
});
});](https://image.slidesharecdn.com/securingtodomvcusingthewebcryptographyapijqcon-140921130442-phpapp01/85/Securing-TodoMVC-Using-the-Web-Cryptography-API-93-320.jpg)
![Generate Key from Password
return $.WebCryptoAPI.subtle.importKey('raw', this.salt, hmacSha256,
true, ['sign', 'verify'])
.then(function (keyResult) {
return $.WebCryptoAPI.subtle.sign(hmacSha256, keyResult, buf)
.then(function (signResult) {
var keyBuf = new Uint8Array(signResult);
// importKey for later AES encryption
return $.WebCryptoAPI.subtle.importKey('raw', keyBuf, {name: 'AES-CBC'},
true, ['encrypt', 'decrypt'])
.then(function (result) {
that.encryptionKey = result;
if (!that.hasTodos) {
return that.setItem([]);
}
});
});
});](https://image.slidesharecdn.com/securingtodomvcusingthewebcryptographyapijqcon-140921130442-phpapp01/85/Securing-TodoMVC-Using-the-Web-Cryptography-API-94-320.jpg)