Embed presentation
Download as PDF, PPTX












The document discusses different nmap scanning techniques including SYN scans, FIN scans, ACK scans, and window scans. It provides pros and cons of each technique. It then details a mission to penetrate SCO's firewall and discern open ports on a target system using different scan types. Another mission works to locate webservers on the Playboy network offering free images, optimizing the scan by getting timing information and scanning faster without DNS lookups. Several IP addresses with port 80 open are identified.
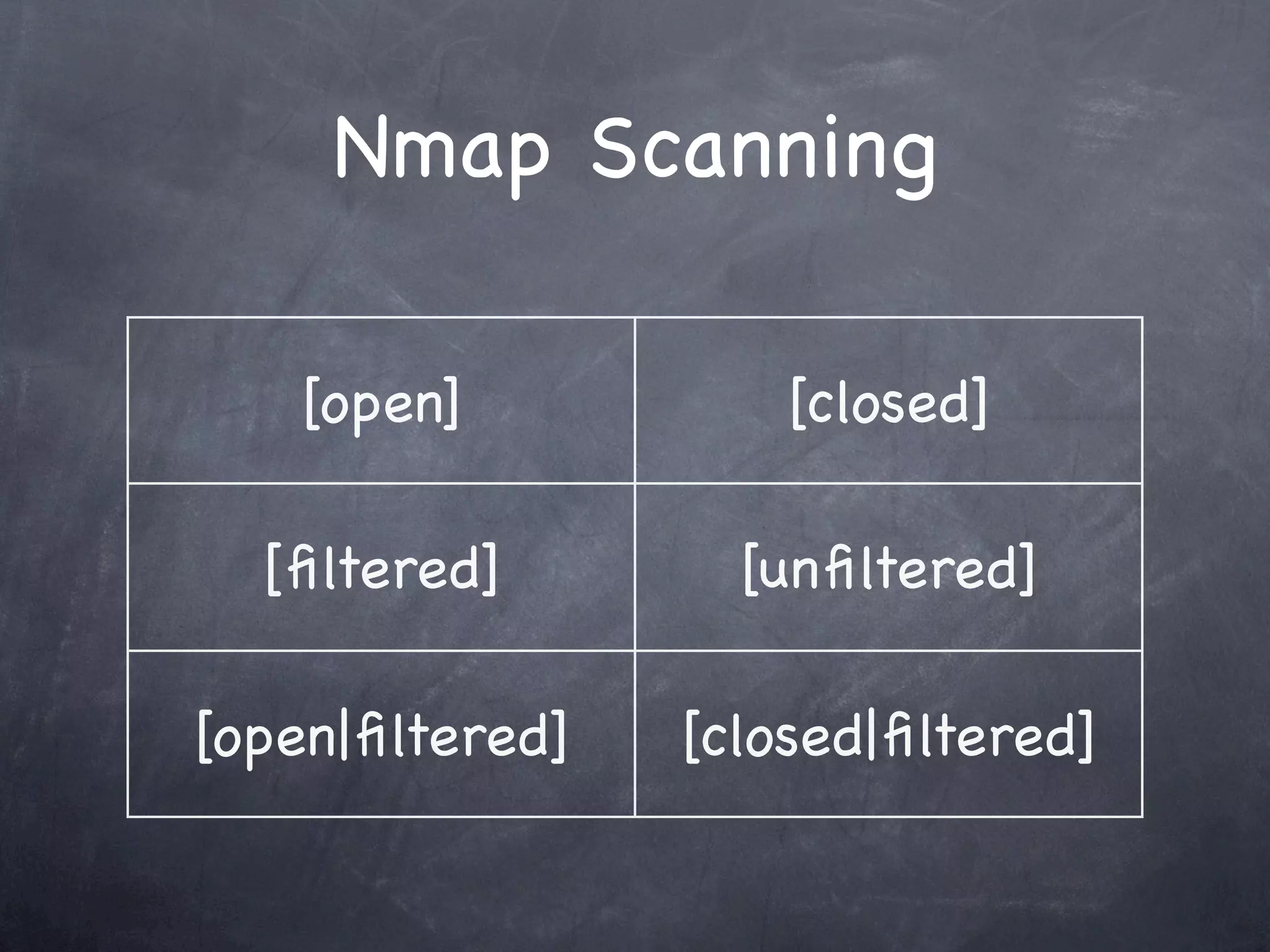
Introduces Nmap scanning techniques and types of port states including open, closed, filtered, and unfiltered.
Discusses four common scanning techniques: SYN, FIN, ACK, and Window scans with pros and cons for each.
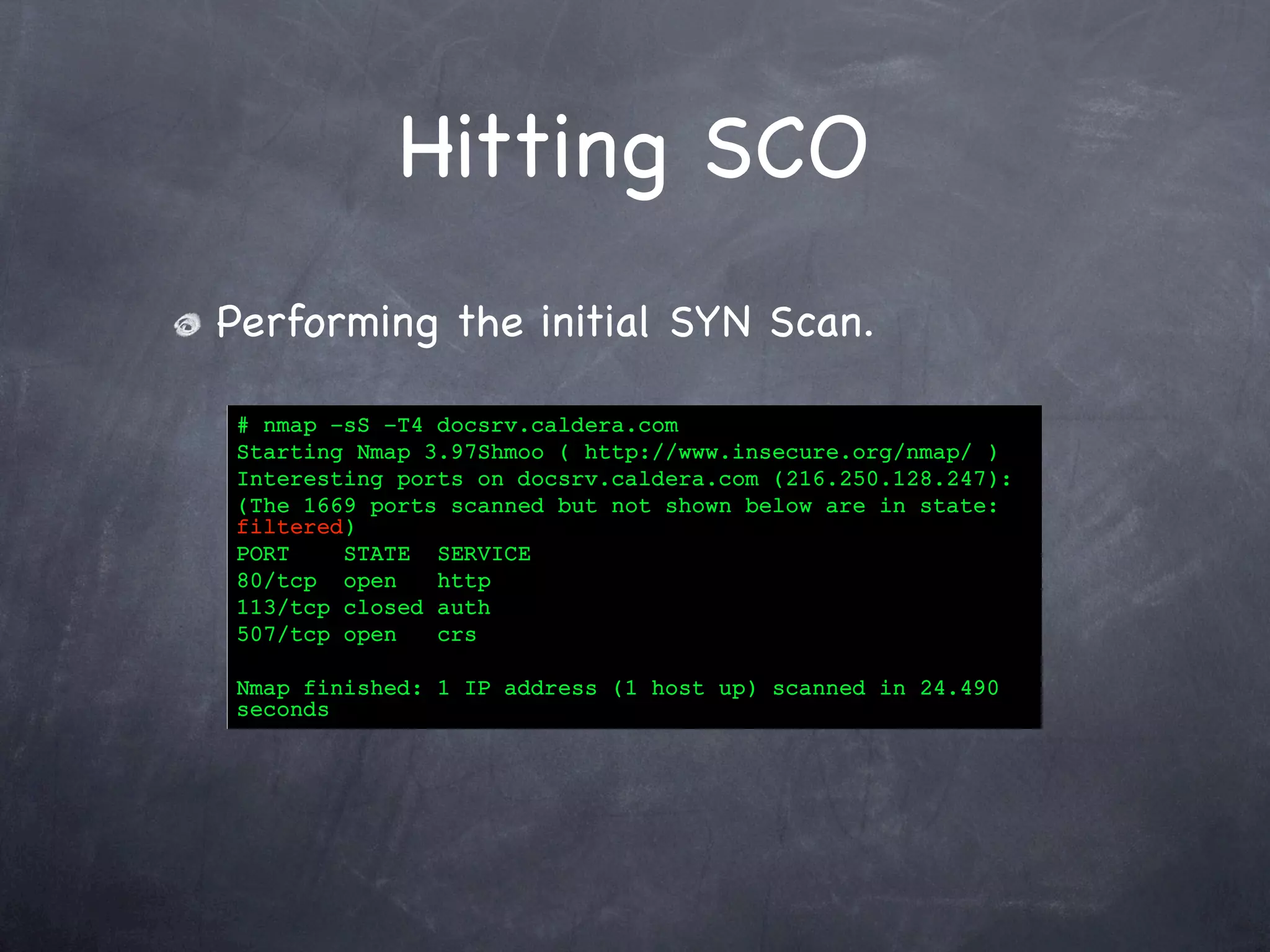
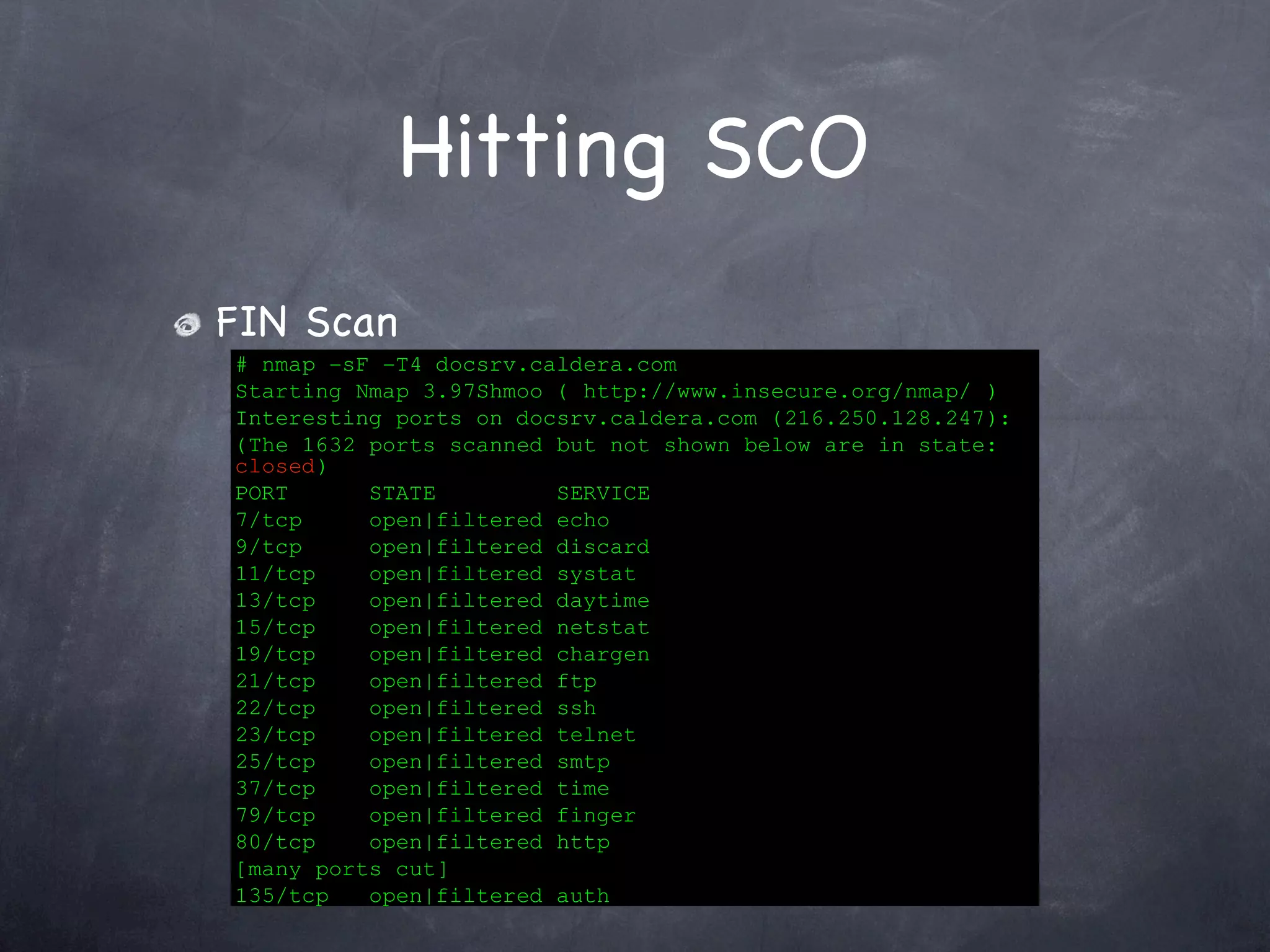
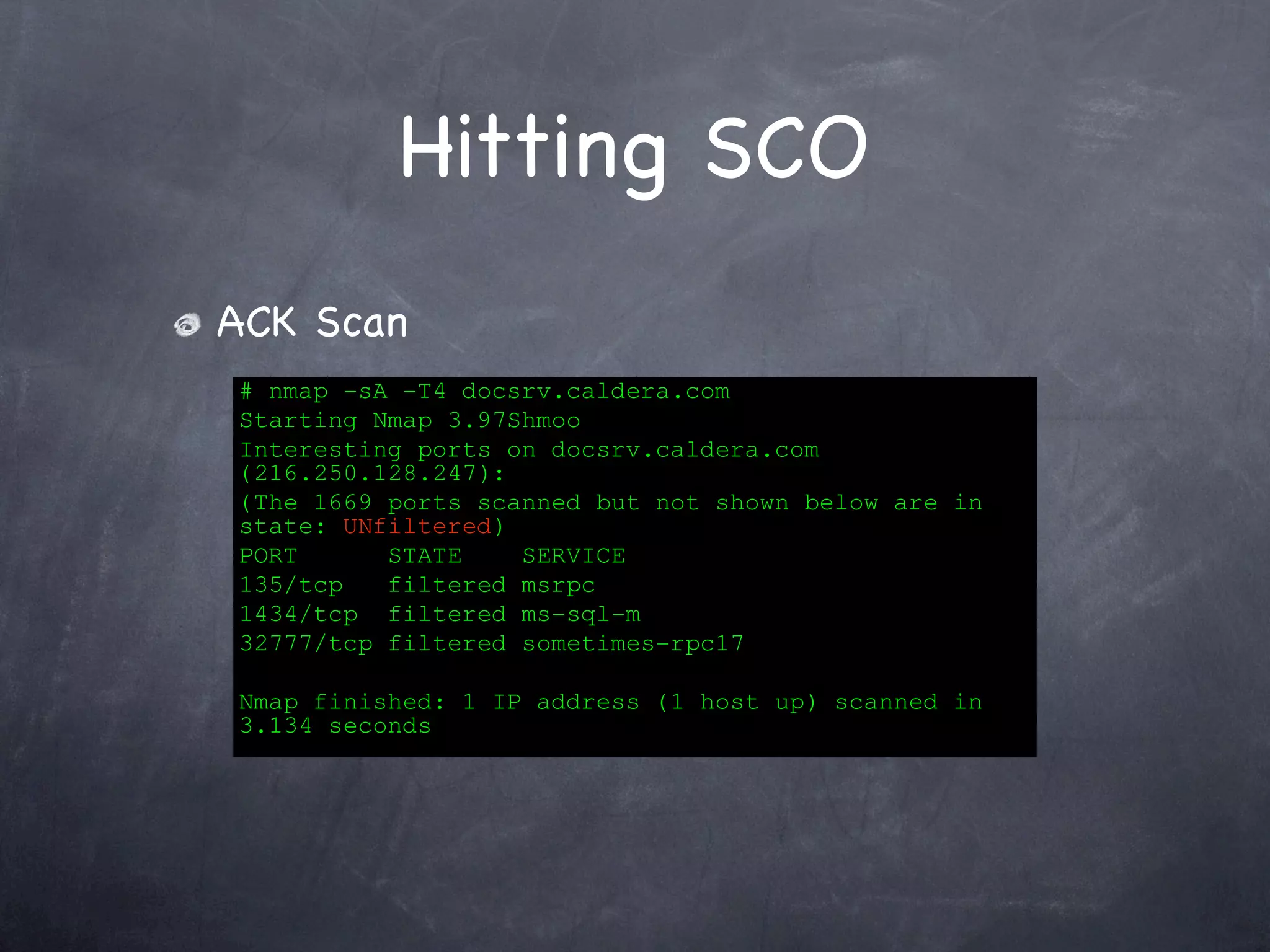
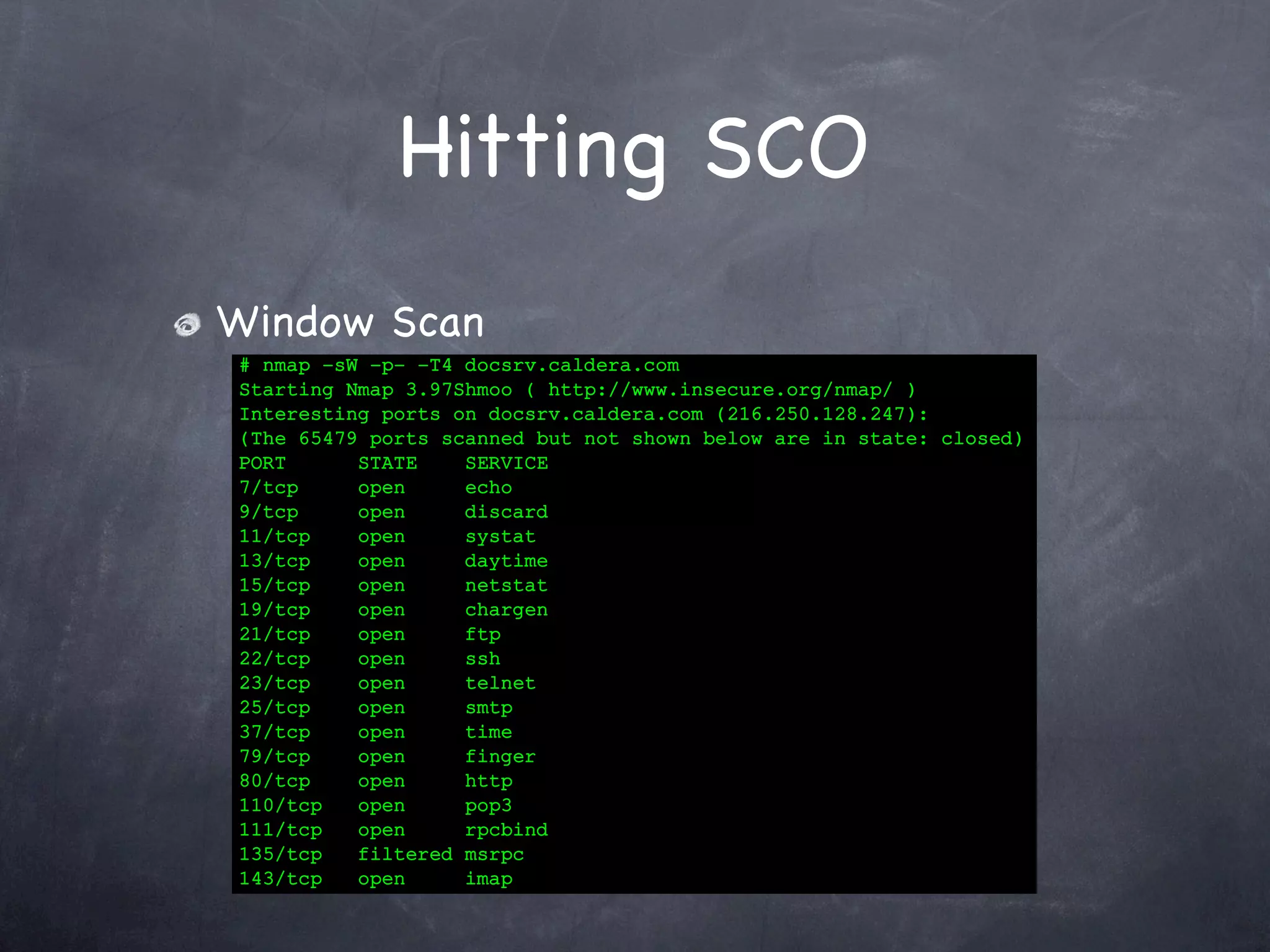
Details the execution of SYN, FIN, ACK, and Window scans on SCO's server with port states and results.
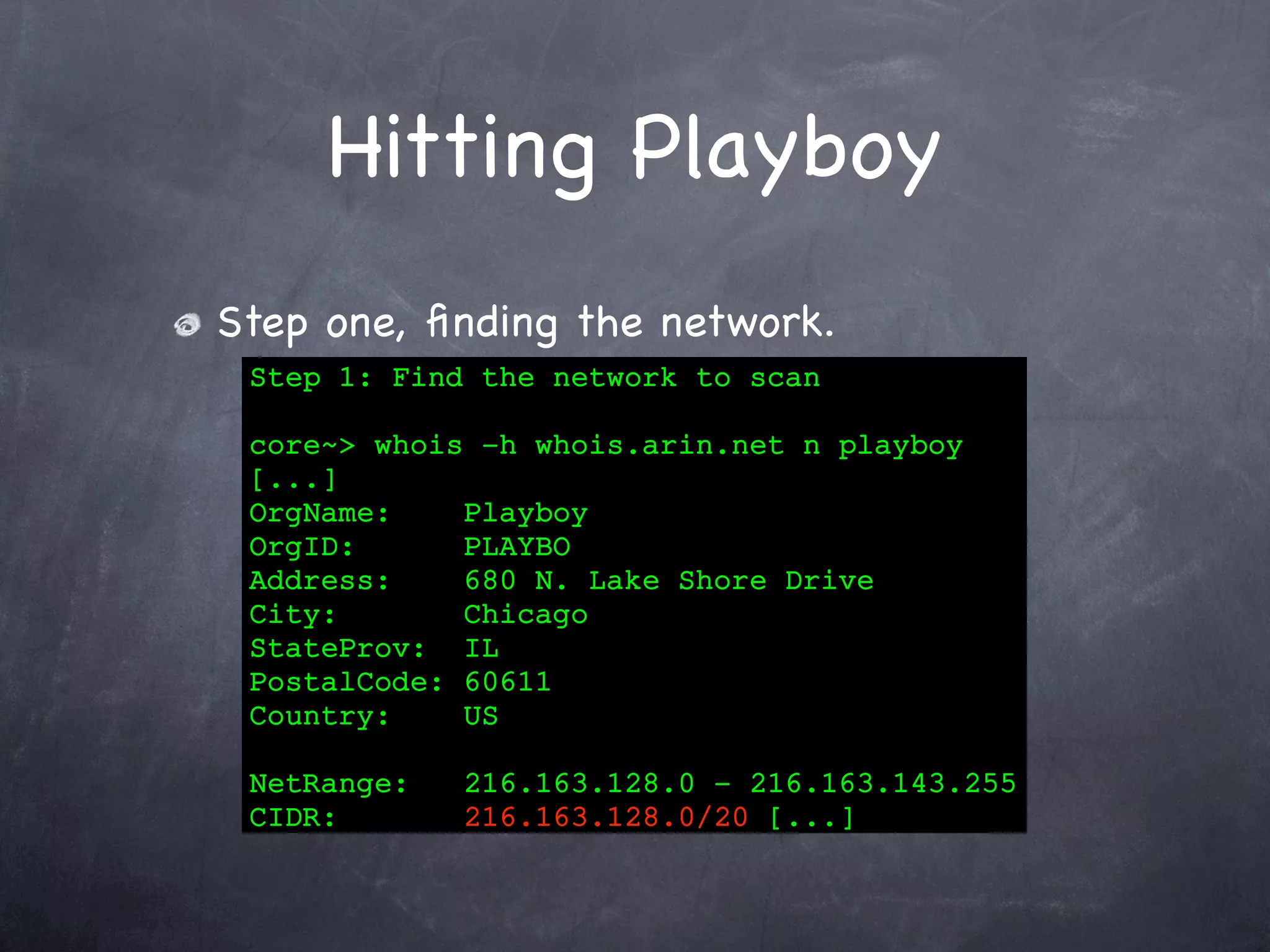
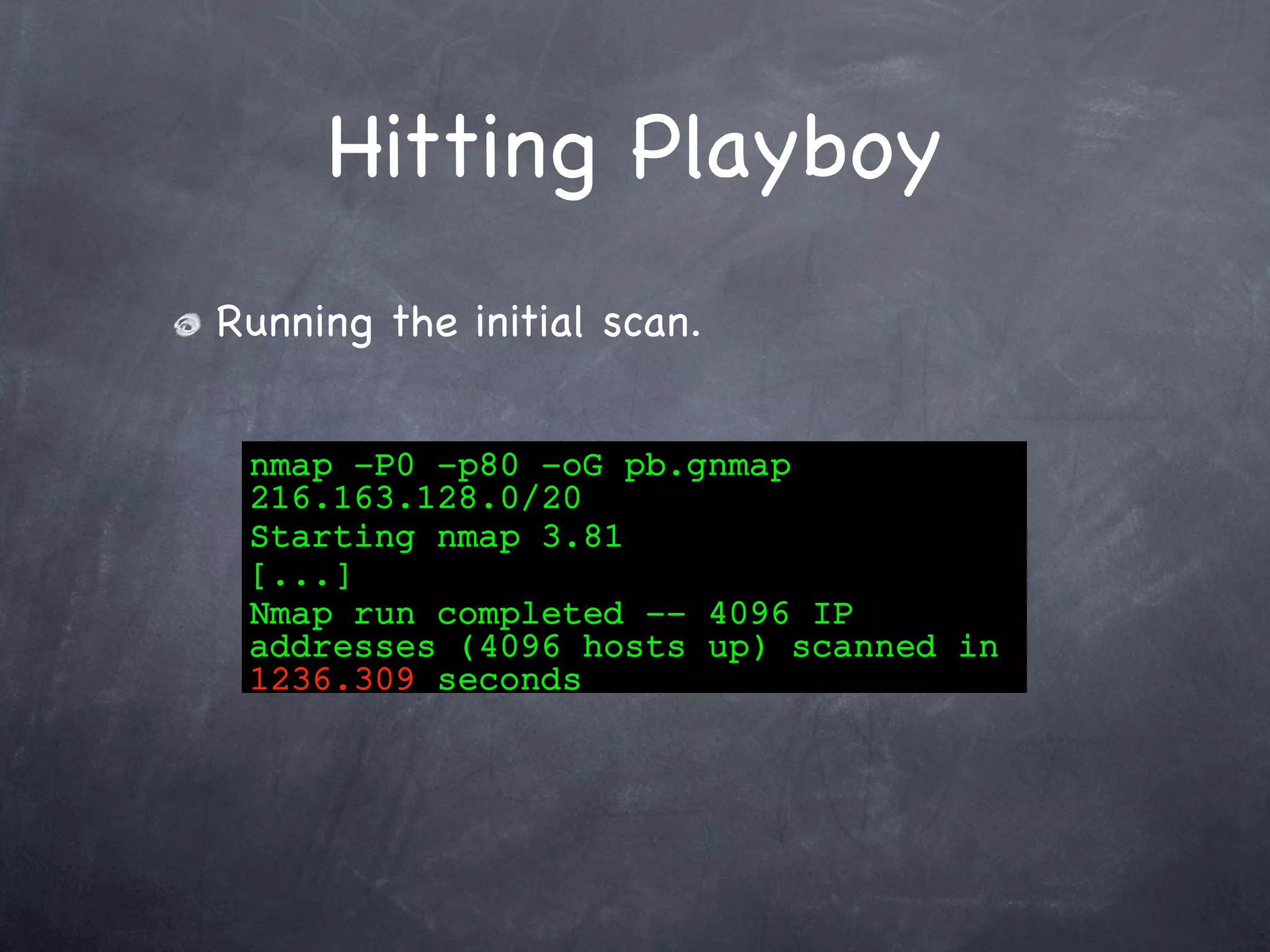
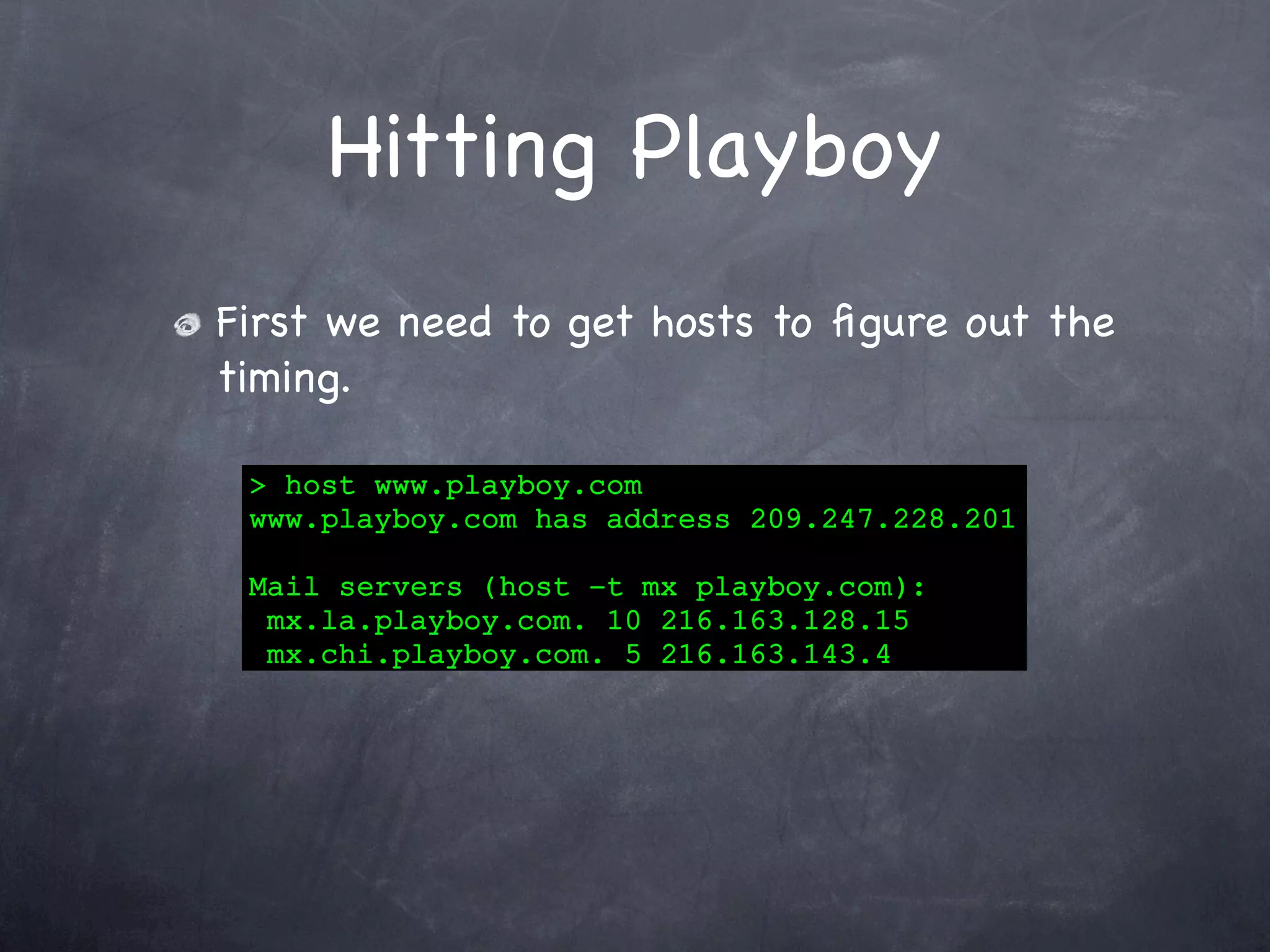
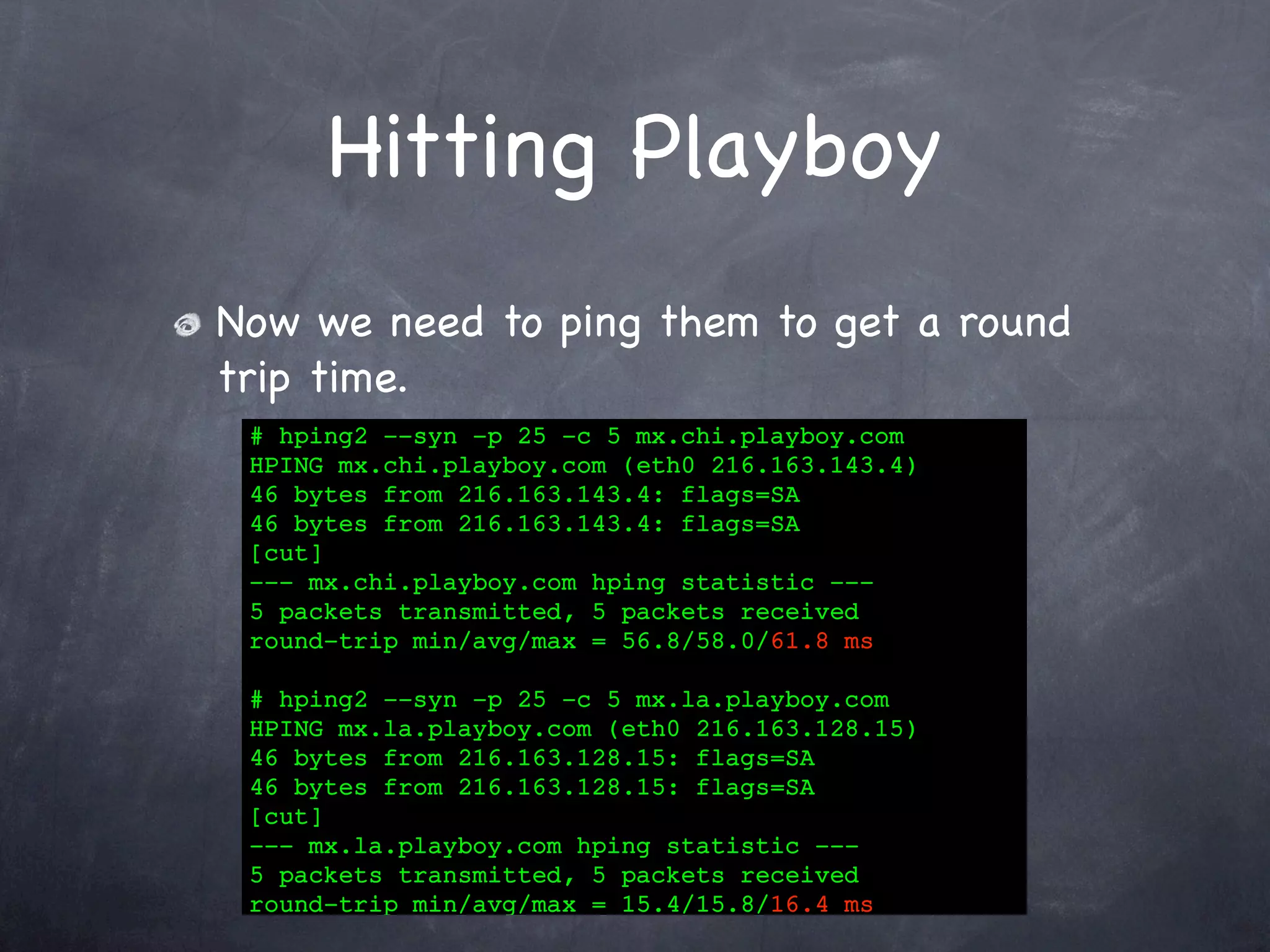
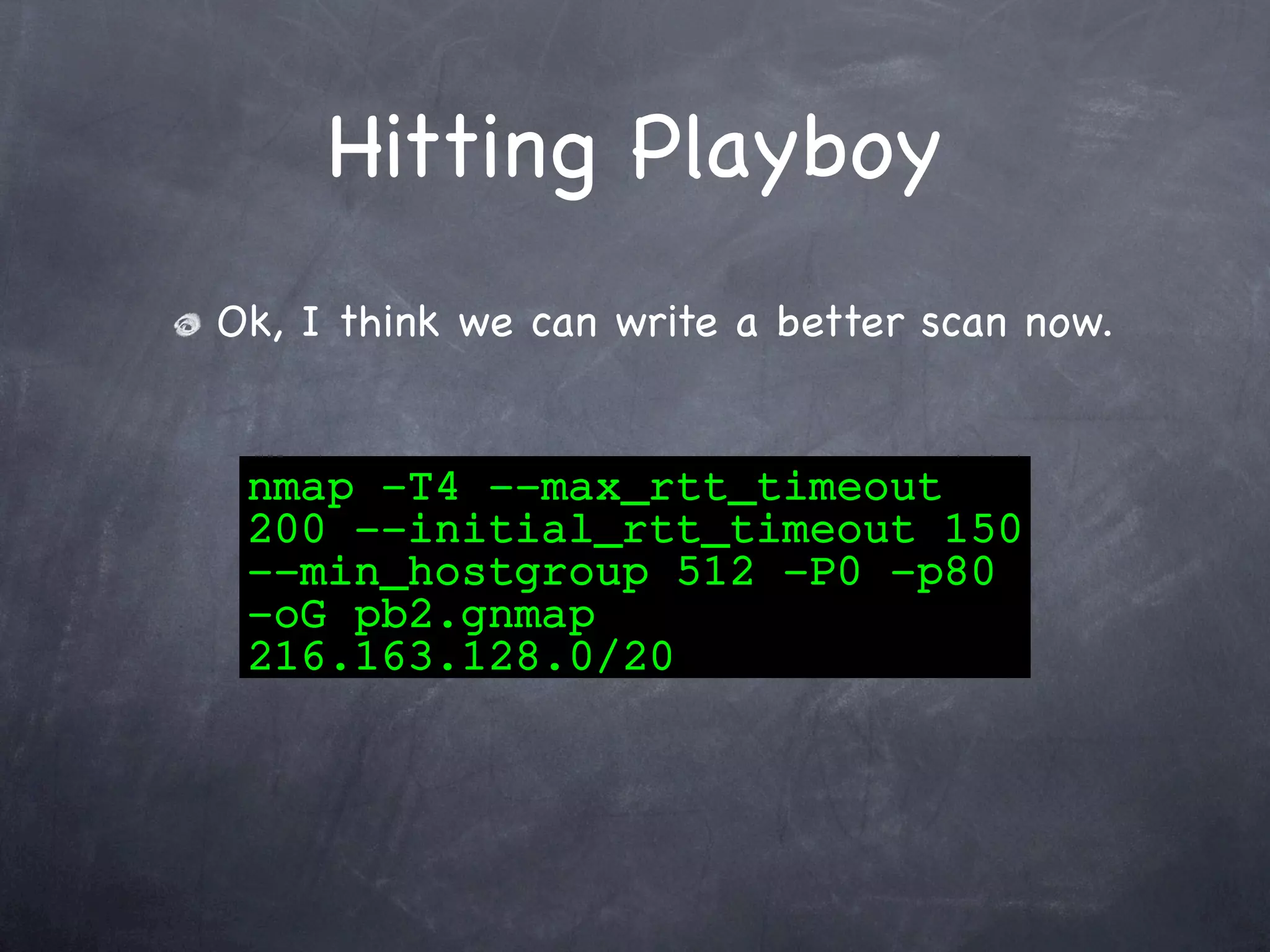
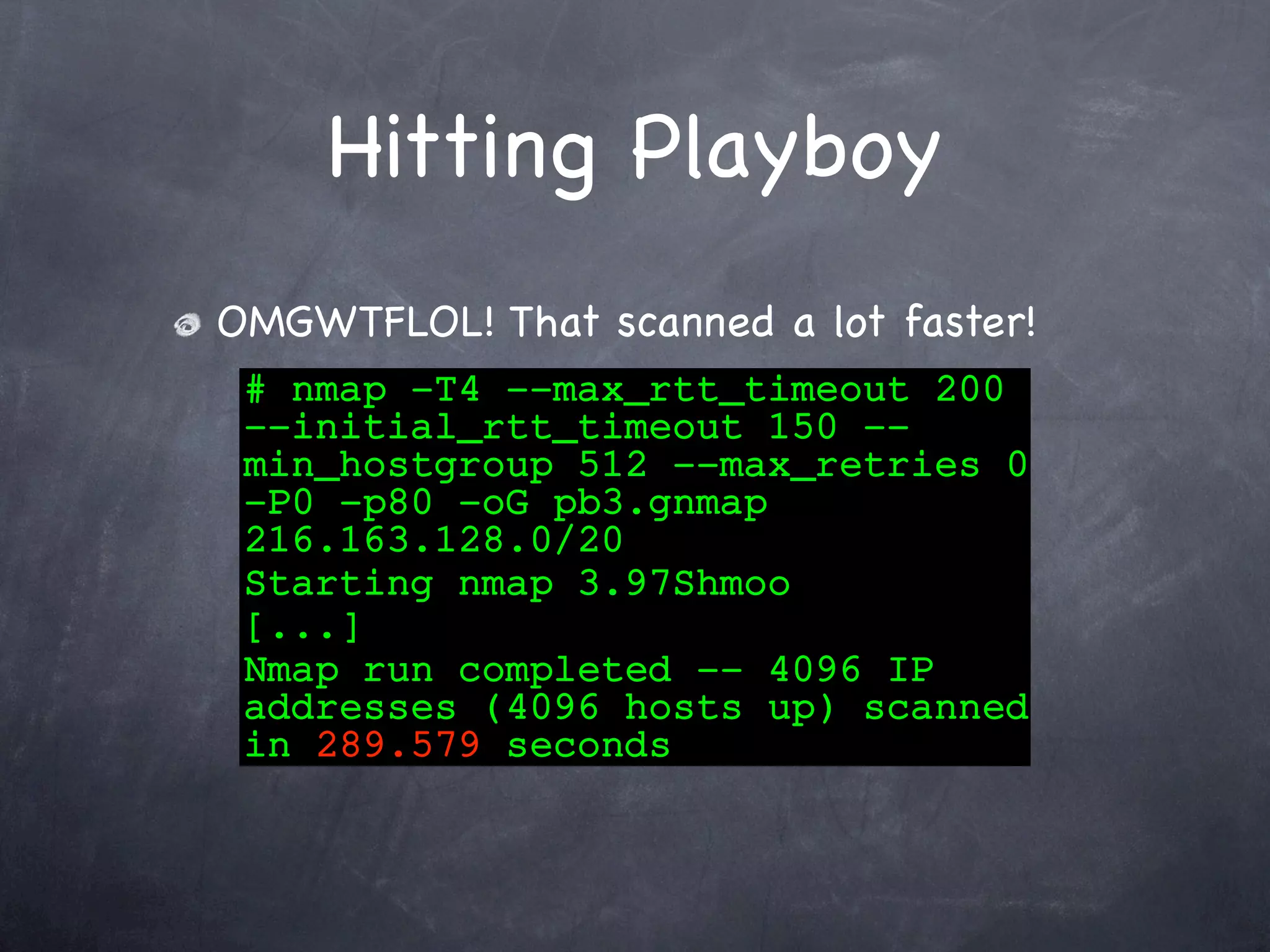
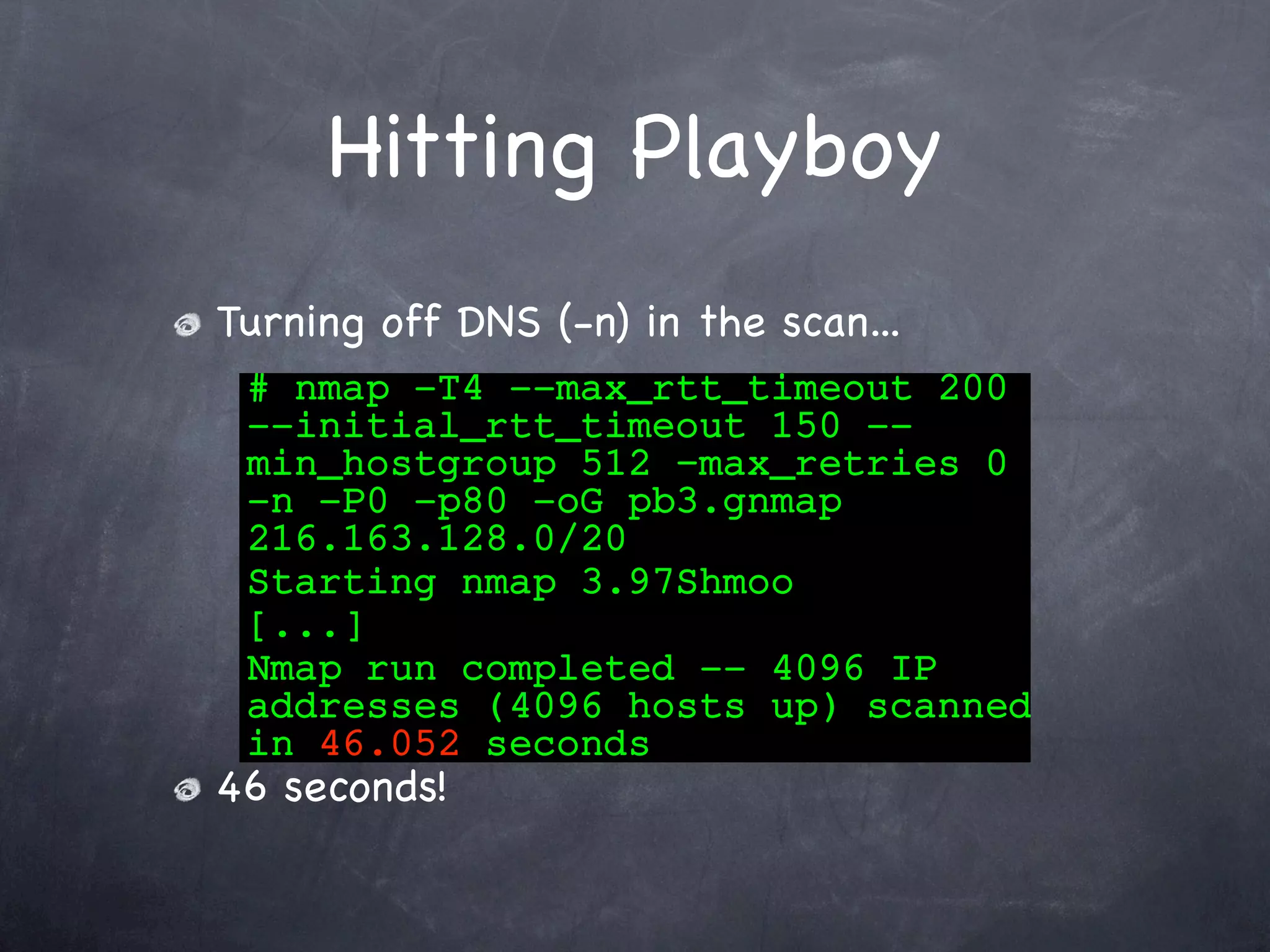
Details the process of scanning the Playboy network, including finding the network, host discovery, timing improvements, and faster scan designs.
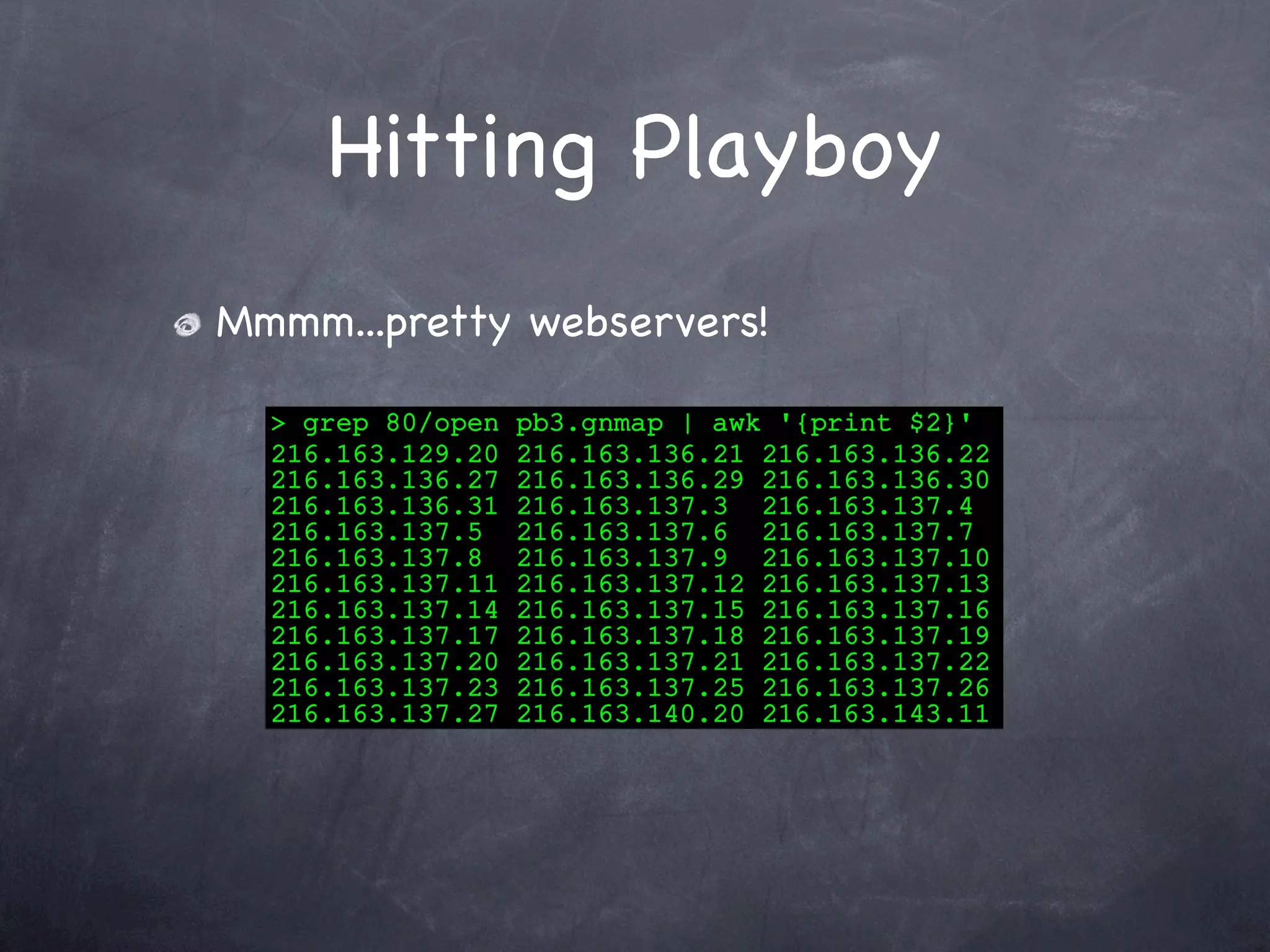
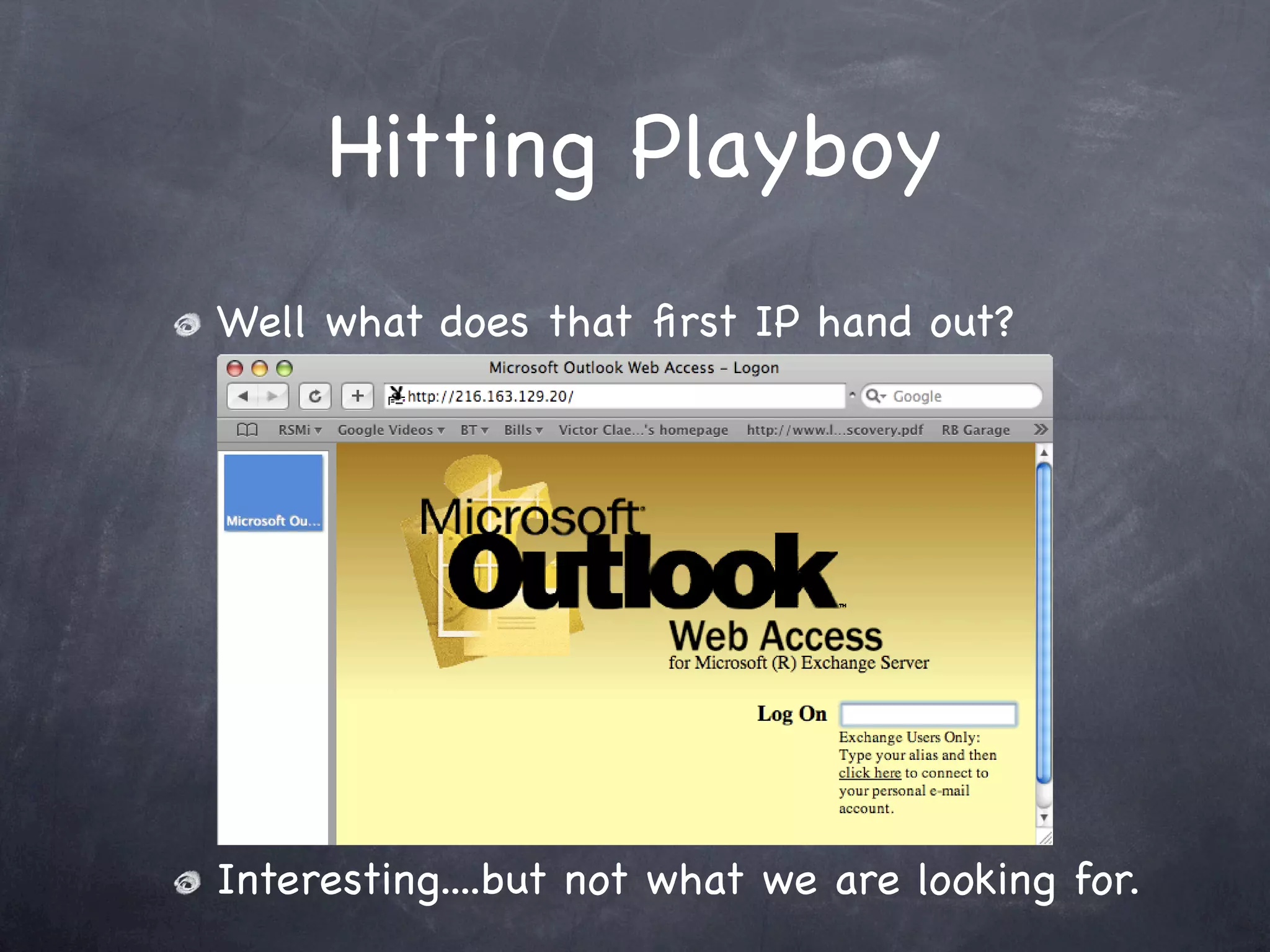
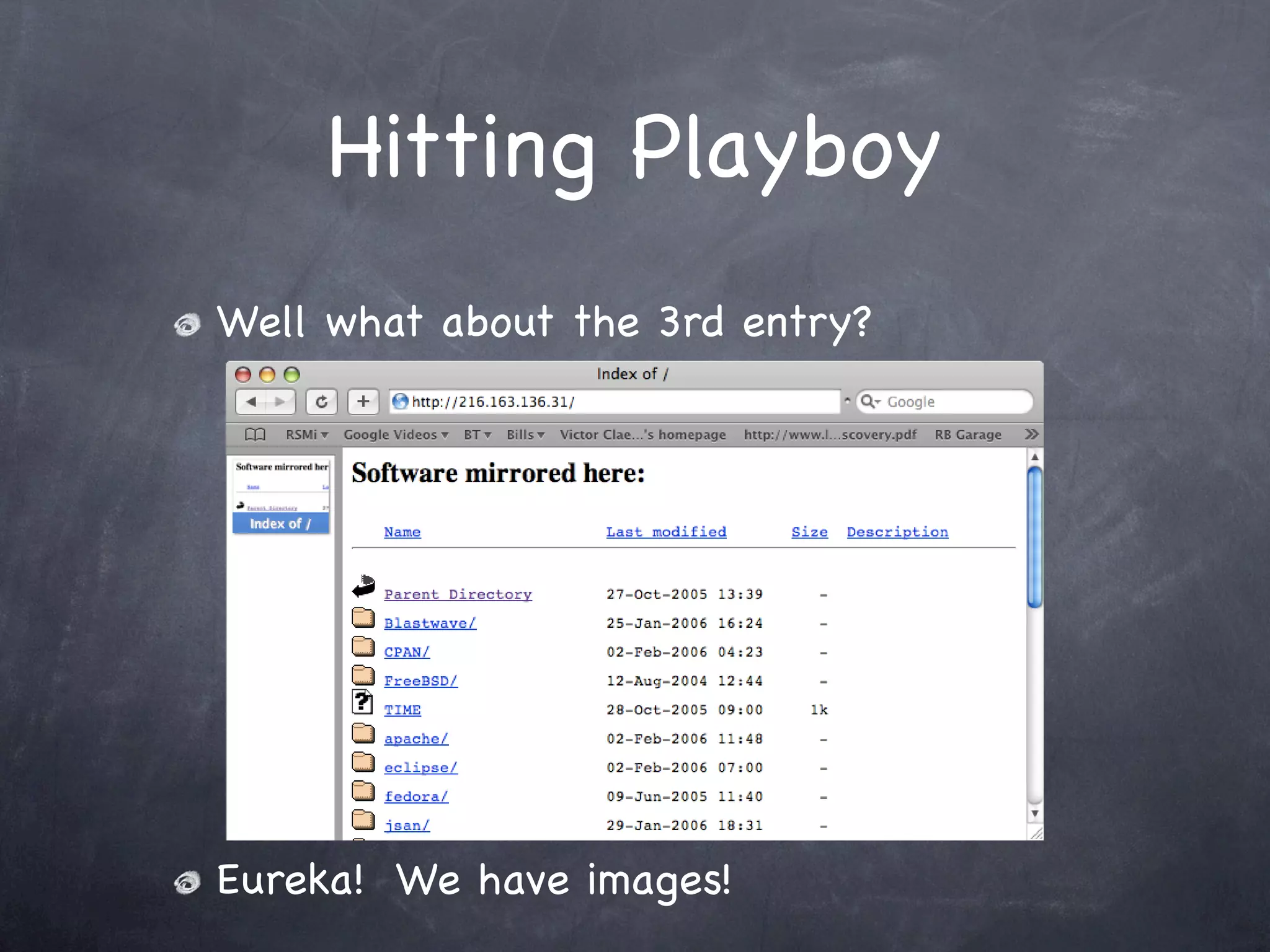
Presents the results of scanning the Playboy network, identifying open web servers and locating free images.
Summarizes the presentation and acknowledges contributions by Fyodor.



























