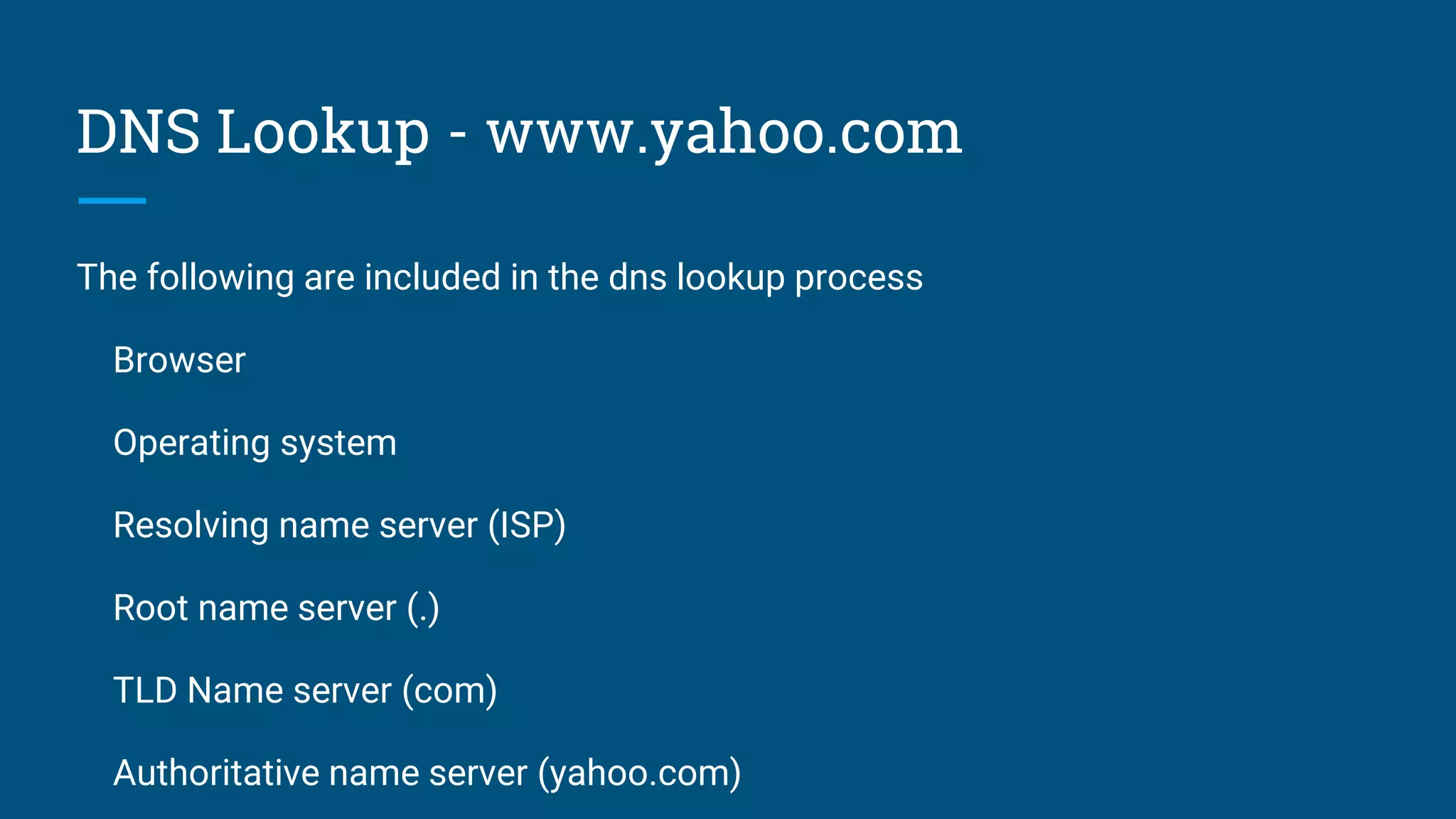
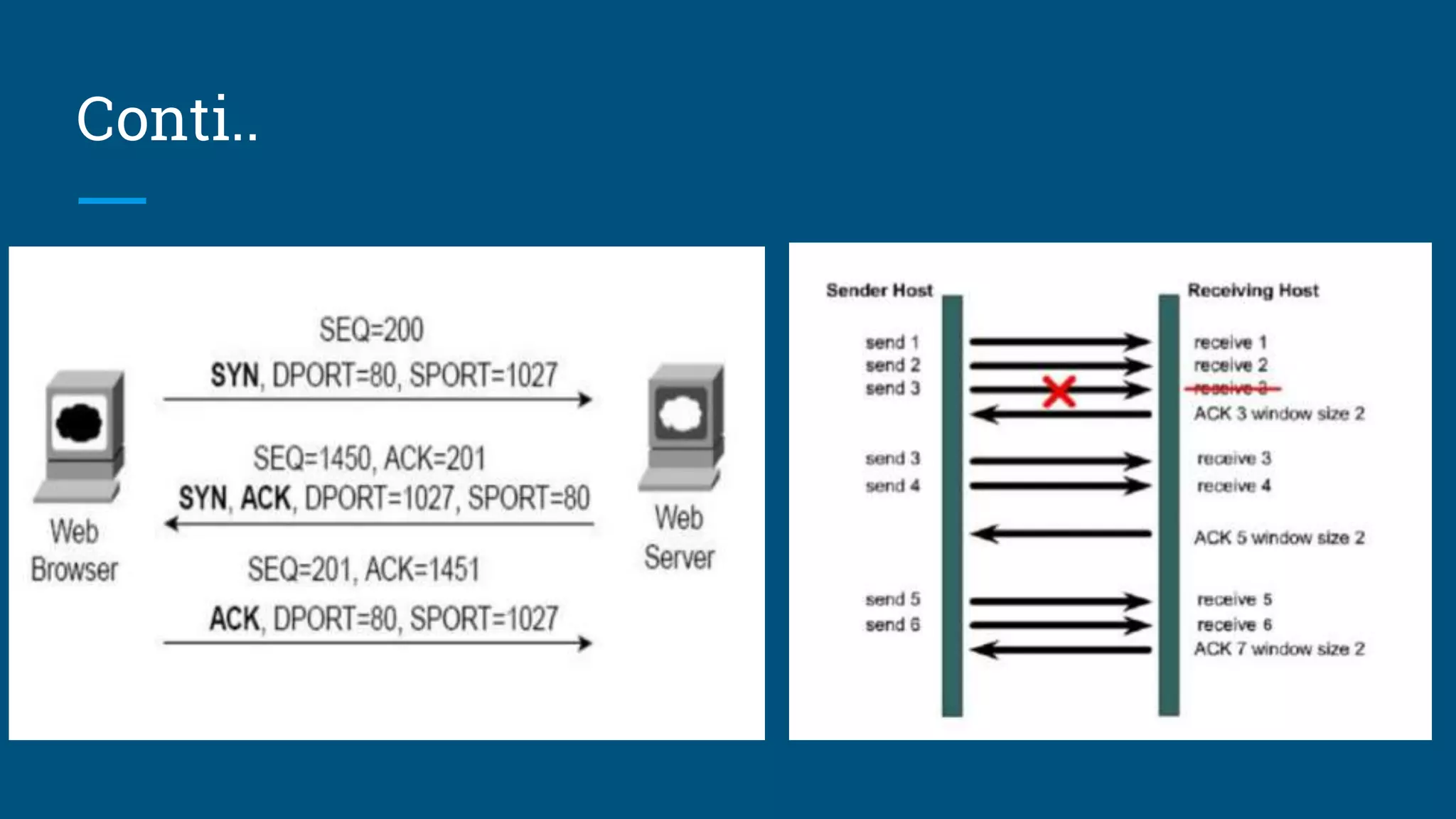
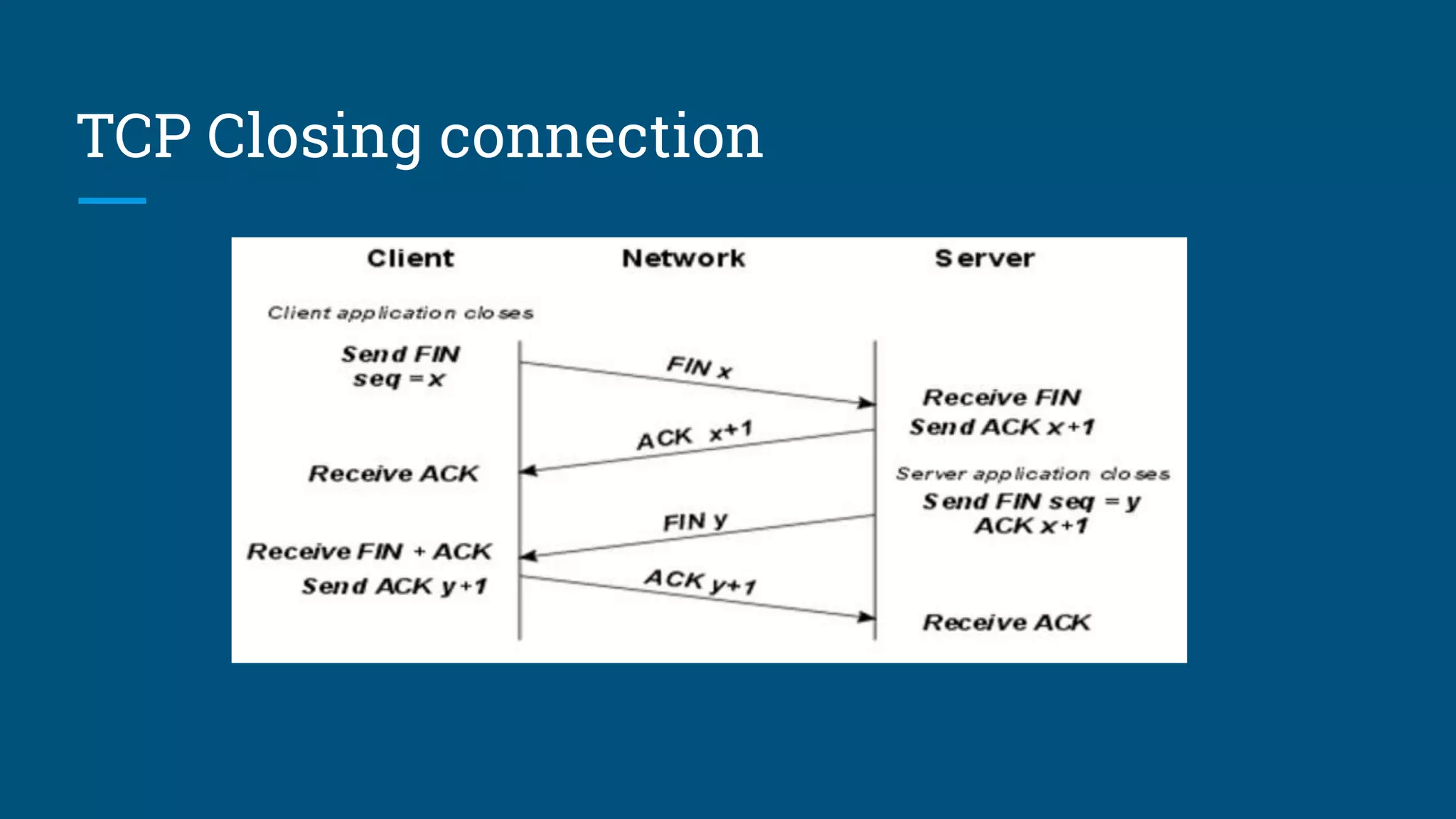
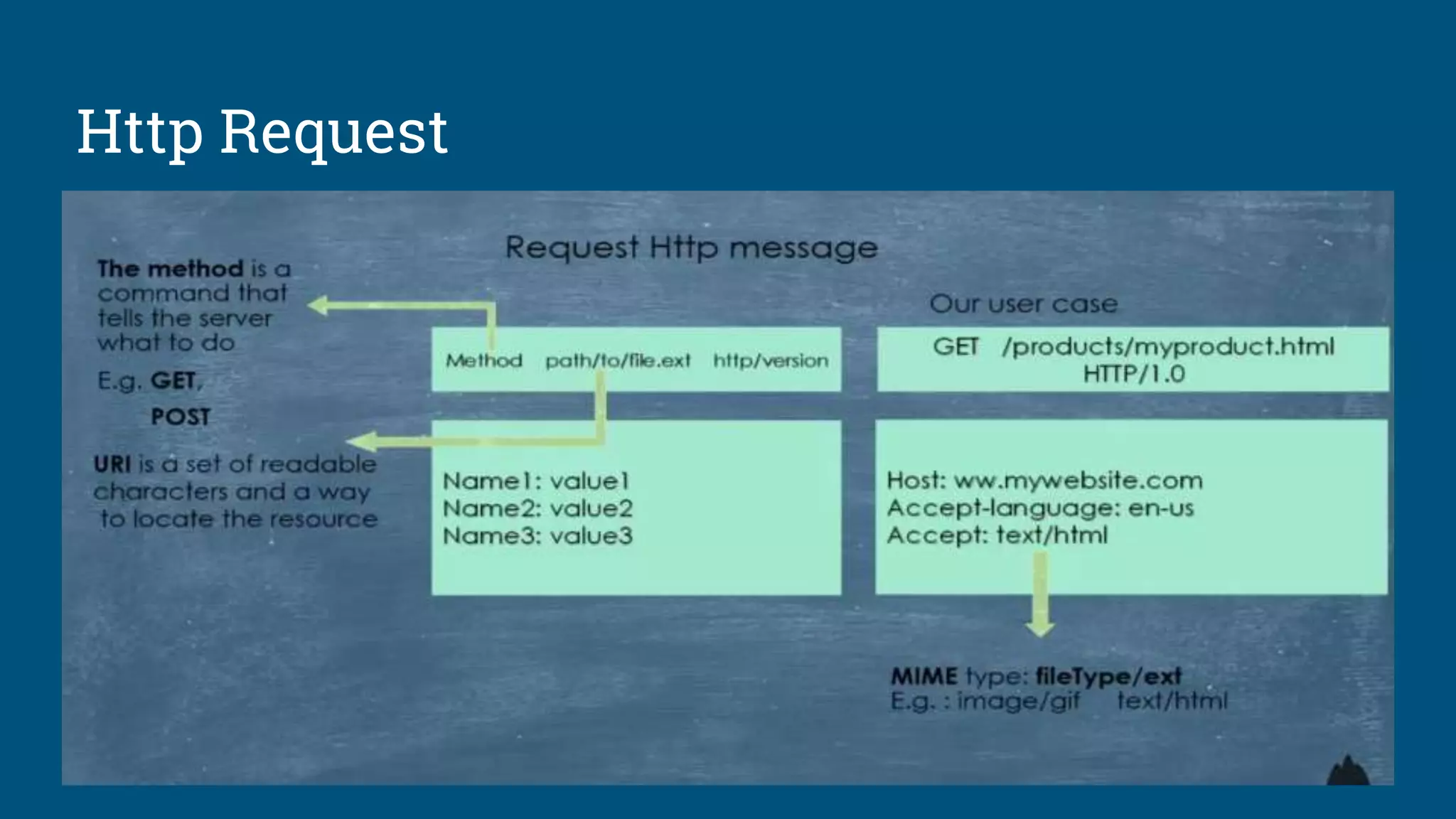
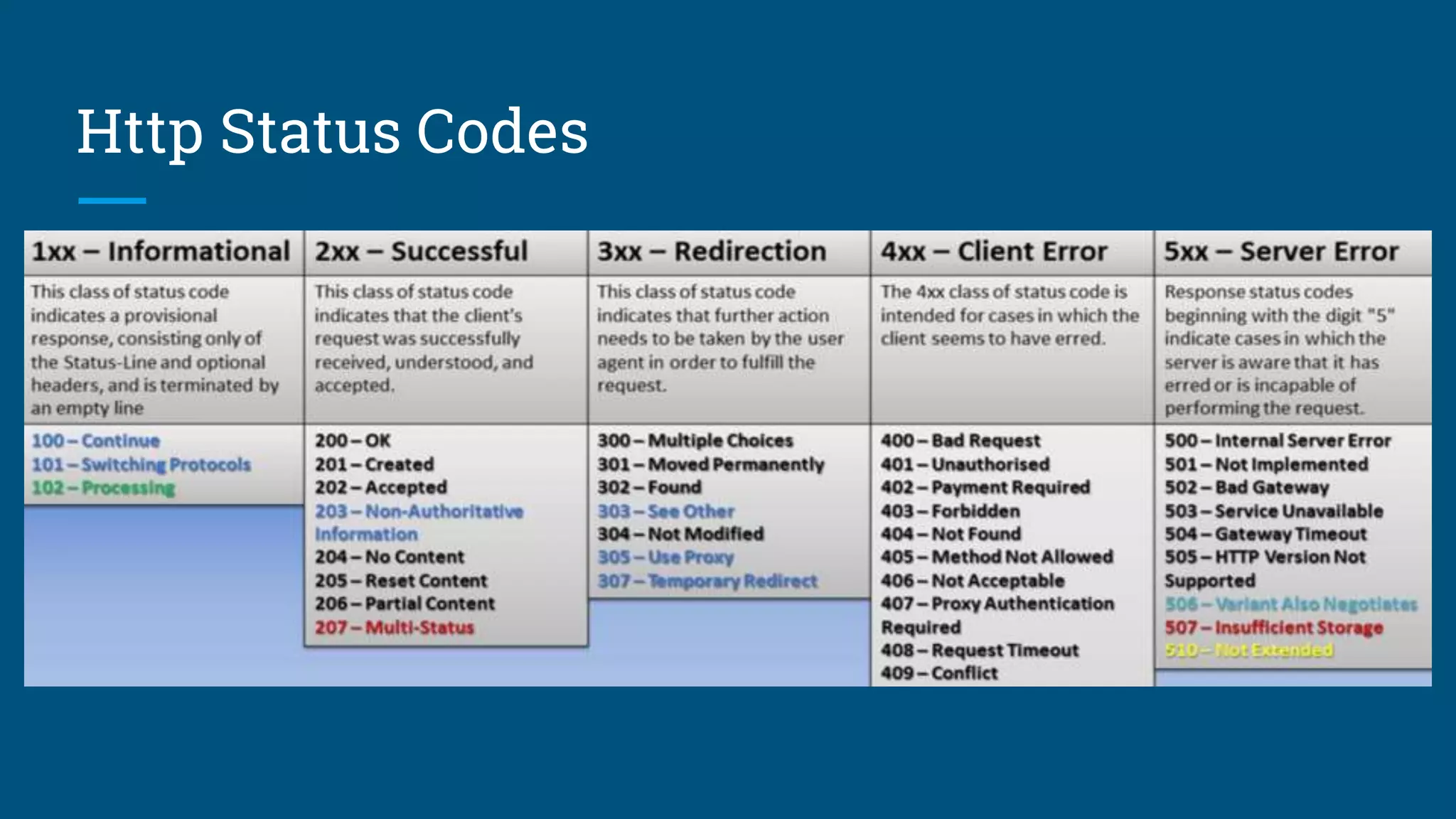
The document discusses the web request and response lifecycle from DNS lookup through HTTP methods and status codes. It describes the process of DNS lookup involving the browser, operating system, resolving name server, root name server, top-level domain name server and authoritative name server to resolve a domain name like www.yahoo.com to an IP address. It then explains the stateless HTTP protocol and how it can deliver different types of data, as well as the TCP three-way handshake process for establishing a connection and transmitting data using windows and acknowledgements. The document also briefly mentions HTTP requests, responses, methods including safe and idempotent methods, and status codes.