Report
Share
Download to read offline
Recommended
10 Types Of Cyber Attacks And How They Can Affect You- Detox technologies.pdf

10 Types Of Cyber Attacks And How They Can Affect You- Detox technologies.pdfCyber security professional services- Detox techno
Recommended
10 Types Of Cyber Attacks And How They Can Affect You- Detox technologies.pdf

10 Types Of Cyber Attacks And How They Can Affect You- Detox technologies.pdfCyber security professional services- Detox techno
More Related Content
What's hot (20)
Similar to Type of Cyber Attacks
Similar to Type of Cyber Attacks (20)
Understanding the emerging threats of cyber security

Understanding the emerging threats of cyber security
Types of Cyber Security Attacks- Active & Passive Attak

Types of Cyber Security Attacks- Active & Passive Attak
8 Different Types of Cybersecurity and Threats Involved

8 Different Types of Cybersecurity and Threats Involved
More from SOCRadar Inc
More from SOCRadar Inc (8)
Recently uploaded
Recently uploaded (20)
Your enemies use GenAI too - staying ahead of fraud with Neo4j

Your enemies use GenAI too - staying ahead of fraud with Neo4j
Long journey of Ruby Standard library at RubyKaigi 2024

Long journey of Ruby Standard library at RubyKaigi 2024
The Value of Certifying Products for FDO _ Paul at FIDO Alliance.pdf

The Value of Certifying Products for FDO _ Paul at FIDO Alliance.pdf
Choosing the Right FDO Deployment Model for Your Application _ Geoffrey at In...

Choosing the Right FDO Deployment Model for Your Application _ Geoffrey at In...
BT & Neo4j _ How Knowledge Graphs help BT deliver Digital Transformation.pptx

BT & Neo4j _ How Knowledge Graphs help BT deliver Digital Transformation.pptx
Extensible Python: Robustness through Addition - PyCon 2024

Extensible Python: Robustness through Addition - PyCon 2024
ASRock Industrial FDO Solutions in Action for Industrial Edge AI _ Kenny at A...

ASRock Industrial FDO Solutions in Action for Industrial Edge AI _ Kenny at A...
Where to Learn More About FDO _ Richard at FIDO Alliance.pdf

Where to Learn More About FDO _ Richard at FIDO Alliance.pdf
PLAI - Acceleration Program for Generative A.I. Startups

PLAI - Acceleration Program for Generative A.I. Startups
Continuing Bonds Through AI: A Hermeneutic Reflection on Thanabots

Continuing Bonds Through AI: A Hermeneutic Reflection on Thanabots
A Business-Centric Approach to Design System Strategy

A Business-Centric Approach to Design System Strategy
What's New in Teams Calling, Meetings and Devices April 2024

What's New in Teams Calling, Meetings and Devices April 2024
Type of Cyber Attacks
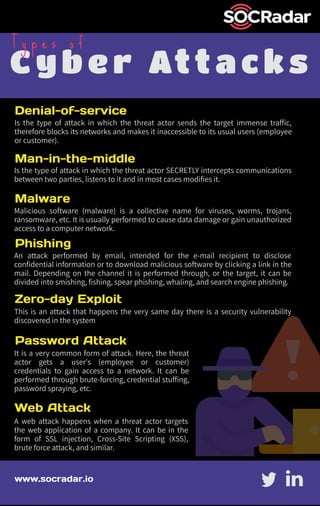
- 1. Cyber Attacks T y p e s o f Denial-of-service Phishing Malware Man-in-the-middle Zero-day Exploit Password Attack Web Attack Is the type of attack in which the threat actor sends the target immense traffic, therefore blocks its networks and makes it inaccessible to its usual users (employee or customer). A web attack happens when a threat actor targets the web application of a company. It can be in the form of SSL injection, Cross-Site Scripting (XSS), brute force attack, and similar. Is the type of attack in which the threat actor SECRETLY intercepts communications between two parties, listens to it and in most cases modifies it. Malicious software (malware) is a collective name for viruses, worms, trojans, ransomware, etc. It is usually performed to cause data damage or gain unauthorized access to a computer network. An attack performed by email, intended for the e-mail recipient to disclose confidential information or to download malicious software by clicking a link in the mail. Depending on the channel it is performed through, or the target, it can be divided into smishing, fishing, spear phishing, whaling, and search engine phishing. This is an attack that happens the very same day there is a security vulnerability discovered in the system It is a very common form of attack. Here, the threat actor gets a user's (employee or customer) credentials to gain access to a network. It can be performed through brute-forcing, credential stuffing, password spraying, etc. www.socradar.io
