Verizon DBIR 2021
•
0 likes•500 views
An overview of Verizon’s 2021 Data Breach Investigation Report: An Overall Summary for Industries, Incident Classification Patterns and SMBs
Report
Share
Report
Share
Download to read offline
Recommended
Cost of Cybercrime Study in Financial Services: 2019 Report

Now in its 9th year, this new Accenture presentation explores the impact associated with cybercrime, quantifying the cost of cyberattacks and analyzing trends in malicious activities in the financial services industry. And this year for the first time, we look to the future so that financial services organizations can better target their funds and resources and open up new revenue opportunities to unlock economic value.
Chief Audit Execs speak out: Cybersecurity & risk management

Highlights from our fifth annual survey of chief audit executives. To read the full report, grantthornton.com/fs-cae-survey
Infographic: Symantec Healthcare IT Security Risk Management Study

Cybersecurity in Healthcare: While Cyberattacks and data breaches are rising across industries, healthcare is lagging behind in cybersecurity investment.
NME IT Security Survey 2016 

Mr. Mirza Asrar Baig featured in the Network Middle East Security Survey 2016
Proofpoint Understanding Email Fraud in 2018 

Email fraud, also known as business email compromise (BEC), is one of today's greatest cyber threats. These highly targeted attacks, sent in low volumes, target people rather than technologies. As a result, they are difficult for traditional security solutions to detect.
To better understand how email fraud is affecting companies like yours, Proofpoint commissioned a survey of more than 2,250 IT decision makers across the U.S., the U.K., Australia, France, and Germany. This infographic highlights our findings.
Recommended
Cost of Cybercrime Study in Financial Services: 2019 Report

Now in its 9th year, this new Accenture presentation explores the impact associated with cybercrime, quantifying the cost of cyberattacks and analyzing trends in malicious activities in the financial services industry. And this year for the first time, we look to the future so that financial services organizations can better target their funds and resources and open up new revenue opportunities to unlock economic value.
Chief Audit Execs speak out: Cybersecurity & risk management

Highlights from our fifth annual survey of chief audit executives. To read the full report, grantthornton.com/fs-cae-survey
Infographic: Symantec Healthcare IT Security Risk Management Study

Cybersecurity in Healthcare: While Cyberattacks and data breaches are rising across industries, healthcare is lagging behind in cybersecurity investment.
NME IT Security Survey 2016 

Mr. Mirza Asrar Baig featured in the Network Middle East Security Survey 2016
Proofpoint Understanding Email Fraud in 2018 

Email fraud, also known as business email compromise (BEC), is one of today's greatest cyber threats. These highly targeted attacks, sent in low volumes, target people rather than technologies. As a result, they are difficult for traditional security solutions to detect.
To better understand how email fraud is affecting companies like yours, Proofpoint commissioned a survey of more than 2,250 IT decision makers across the U.S., the U.K., Australia, France, and Germany. This infographic highlights our findings.
INFOGRAPHIC: The Evolution of Data Privacy

The EU’s new General Data Protection Regulation
has left many businesses wondering if they are
ready to comply.
INFOGRAPHIC: Here are the reasons why
Scalar security study2017_slideshare_rev[1]![Scalar security study2017_slideshare_rev[1]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Scalar security study2017_slideshare_rev[1]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Highlights of the 2017 Scalar Security Study, The Cyber Security Readiness of Canadian Organizations, published February 2017. The full report can be downloaded at scalar.ca/en/landing/2017-scalar-security-study/
Unisys Security Insights Infographic: Global

In light of seemingly constant news about the loss of personal data, Unisys Security Insights asks consumers in 12 countries: How likely do you think your personal information shared with organizations will be accessed by an unauthorized person either accidently or deliberately within the next 12 months? View global findings here: http://www.unisys.com/ms/unisys-security-insights/
2015 cost of data breach study global analysis

2015 Cost of Data Breach Study:
Global Analysis
By: Ponemon Institute
Benchmark research sponsored by IBM
Independently conducted by Ponemon Institute LLC
May 2015
SVB Cybersecurity Impact on Innovation Report - Overview

In a survey of U.S. technology and healthcare executives nationwide, Silicon Valley Bank found that companies believe cyber attacks are a serious threat to both their data and their business continuity.
Highlights
- 98% are maintaining or increasing resources devoted to cyber security
- 50% are increasing their cyber security resources, preparing for when, not if, cyber attacks occur
- Just 35% are completely or very confident in the security of their company information, and only 16% feel the same about their business partners
The Cyber Security Readiness of Canadian Organizations

Highlights of the 2015 Scalar Security Study, The Cyber Security Readiness of Canadian Organizations, published February 2015. The full report can be downloaded at: http://hubs.ly/y0tFbr0
SVB Cybersecurity Impact on Innovation Report

In a survey of U.S. technology and healthcare executives nationwide, Silicon Valley Bank found that companies believe cyber attacks are a serious threat to both their data and their business continuity.
Highlights
- 98% are maintaining or increasing resources devoted to cyber security
- 50% are increasing their cyber security resources, preparing for when, not if, cyber attacks occur
- Just 35% are completely or very confident in the security of their company information, and only 16% feel the same about their business partners
Networkers cyber security market intelligence report

In this report we share our insight on the recruitment of cyber security professionals including information regarding the key drivers in the cyber security market, permanent and contract recruitment trends, transferable skills, the top job titles, salaries and qualifications analysis, a heat map of skills demands/talent pools across the UK, concluding with recommendations on attracting and retaining cyber security talent.
Sharing the blame: How companies are collaborating on data security breaches

Sharing the blame: How companies are collaborating on data security breachesThe Economist Media Businesses
Sharing the blame: How companies are collaborating on data security breaches, is an Economist Intelligence Unit research project, sponsored by Akamai Technologies, exploring the ways in which organisations are collaborating to deal with the disclosure of data security breaches. How are they co-operating with governments, other companies and third parties in areas such as requirements for the public disclosure of such breaches? Do they have consistent cyber security policies? To what extent are they sharing best practices?IMC 618 - Public Relations Campaign

Public Relations Campaign for SecureWorks for IMC 618: PR Concepts & Strategy. Campaign is focused on increasing brand awareness among both big and small businesses as well as potential investors.
Cybersecurity in the Boardroom

A Briefing Guide for C-Level Executives to Threats,
Tactics, and Strategies.
Cyber security investments 2021

We found that while cyber security was named as the topmost future tech adoption for organizations in 2019, cyber security is now the second tech priority for 2021 but with a higher budget than previously allocated. We also discovered that cloud security currently holds more importance with CISOs, CTOs and CIOs than data security and privacy.
Perception Gaps in Cyber Resilience: What Are Your Blind Spots?

Protecting enterprise systems against cyber threats is a strategic priority, yet only 42% of executives are confident they could recover without impacting their business from a cyber event. Find out the hidden risks of shadow IT, cloud and cyber insurance.
Norton Mobile Apps Survey Report

Symantec surveyed consumers around the globe to gauge perceptions toward mobile privacy against the realities of today’s connected world.
Data Integrity Trends

This presentation explores the goals of today's data-driven organizations, the challenges imposed by external macro forces, and the imperative for data integrity to enable innovation and drive business success. Learn about the key insights and findings from the latest global survey of over 400 global data professionals, the 2023 Data Integrity Trends and Insights report.
Protected Harbor Data Breach Trend Report

The Protected Harbor Data Breach Trend Report is a comprehensive analysis of current trends and insights in the cybersecurity landscape. Delve into this in-depth report to better understand emerging threats, vulnerabilities, and strategies for safeguarding your organization's data. Stay one step ahead in the ever-evolving world of data security with valuable insights from our experts.
CSO Pandemic Impact Survey, 2020

To get a better understanding of how organizations were prepared from a security perspective and the impact that security leaders expect to be long lasting due to COVID-19.
More Related Content
What's hot
INFOGRAPHIC: The Evolution of Data Privacy

The EU’s new General Data Protection Regulation
has left many businesses wondering if they are
ready to comply.
INFOGRAPHIC: Here are the reasons why
Scalar security study2017_slideshare_rev[1]![Scalar security study2017_slideshare_rev[1]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Scalar security study2017_slideshare_rev[1]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Highlights of the 2017 Scalar Security Study, The Cyber Security Readiness of Canadian Organizations, published February 2017. The full report can be downloaded at scalar.ca/en/landing/2017-scalar-security-study/
Unisys Security Insights Infographic: Global

In light of seemingly constant news about the loss of personal data, Unisys Security Insights asks consumers in 12 countries: How likely do you think your personal information shared with organizations will be accessed by an unauthorized person either accidently or deliberately within the next 12 months? View global findings here: http://www.unisys.com/ms/unisys-security-insights/
2015 cost of data breach study global analysis

2015 Cost of Data Breach Study:
Global Analysis
By: Ponemon Institute
Benchmark research sponsored by IBM
Independently conducted by Ponemon Institute LLC
May 2015
SVB Cybersecurity Impact on Innovation Report - Overview

In a survey of U.S. technology and healthcare executives nationwide, Silicon Valley Bank found that companies believe cyber attacks are a serious threat to both their data and their business continuity.
Highlights
- 98% are maintaining or increasing resources devoted to cyber security
- 50% are increasing their cyber security resources, preparing for when, not if, cyber attacks occur
- Just 35% are completely or very confident in the security of their company information, and only 16% feel the same about their business partners
The Cyber Security Readiness of Canadian Organizations

Highlights of the 2015 Scalar Security Study, The Cyber Security Readiness of Canadian Organizations, published February 2015. The full report can be downloaded at: http://hubs.ly/y0tFbr0
SVB Cybersecurity Impact on Innovation Report

In a survey of U.S. technology and healthcare executives nationwide, Silicon Valley Bank found that companies believe cyber attacks are a serious threat to both their data and their business continuity.
Highlights
- 98% are maintaining or increasing resources devoted to cyber security
- 50% are increasing their cyber security resources, preparing for when, not if, cyber attacks occur
- Just 35% are completely or very confident in the security of their company information, and only 16% feel the same about their business partners
Networkers cyber security market intelligence report

In this report we share our insight on the recruitment of cyber security professionals including information regarding the key drivers in the cyber security market, permanent and contract recruitment trends, transferable skills, the top job titles, salaries and qualifications analysis, a heat map of skills demands/talent pools across the UK, concluding with recommendations on attracting and retaining cyber security talent.
Sharing the blame: How companies are collaborating on data security breaches

Sharing the blame: How companies are collaborating on data security breachesThe Economist Media Businesses
Sharing the blame: How companies are collaborating on data security breaches, is an Economist Intelligence Unit research project, sponsored by Akamai Technologies, exploring the ways in which organisations are collaborating to deal with the disclosure of data security breaches. How are they co-operating with governments, other companies and third parties in areas such as requirements for the public disclosure of such breaches? Do they have consistent cyber security policies? To what extent are they sharing best practices?IMC 618 - Public Relations Campaign

Public Relations Campaign for SecureWorks for IMC 618: PR Concepts & Strategy. Campaign is focused on increasing brand awareness among both big and small businesses as well as potential investors.
Cybersecurity in the Boardroom

A Briefing Guide for C-Level Executives to Threats,
Tactics, and Strategies.
Cyber security investments 2021

We found that while cyber security was named as the topmost future tech adoption for organizations in 2019, cyber security is now the second tech priority for 2021 but with a higher budget than previously allocated. We also discovered that cloud security currently holds more importance with CISOs, CTOs and CIOs than data security and privacy.
Perception Gaps in Cyber Resilience: What Are Your Blind Spots?

Protecting enterprise systems against cyber threats is a strategic priority, yet only 42% of executives are confident they could recover without impacting their business from a cyber event. Find out the hidden risks of shadow IT, cloud and cyber insurance.
Norton Mobile Apps Survey Report

Symantec surveyed consumers around the globe to gauge perceptions toward mobile privacy against the realities of today’s connected world.
What's hot (18)
SVB Cybersecurity Impact on Innovation Report - Overview

SVB Cybersecurity Impact on Innovation Report - Overview
The Cyber Security Readiness of Canadian Organizations

The Cyber Security Readiness of Canadian Organizations
Networkers cyber security market intelligence report

Networkers cyber security market intelligence report
Sharing the blame: How companies are collaborating on data security breaches

Sharing the blame: How companies are collaborating on data security breaches
Perception Gaps in Cyber Resilience: What Are Your Blind Spots?

Perception Gaps in Cyber Resilience: What Are Your Blind Spots?
Similar to Verizon DBIR 2021
Data Integrity Trends

This presentation explores the goals of today's data-driven organizations, the challenges imposed by external macro forces, and the imperative for data integrity to enable innovation and drive business success. Learn about the key insights and findings from the latest global survey of over 400 global data professionals, the 2023 Data Integrity Trends and Insights report.
Protected Harbor Data Breach Trend Report

The Protected Harbor Data Breach Trend Report is a comprehensive analysis of current trends and insights in the cybersecurity landscape. Delve into this in-depth report to better understand emerging threats, vulnerabilities, and strategies for safeguarding your organization's data. Stay one step ahead in the ever-evolving world of data security with valuable insights from our experts.
CSO Pandemic Impact Survey, 2020

To get a better understanding of how organizations were prepared from a security perspective and the impact that security leaders expect to be long lasting due to COVID-19.
Government and Education Webinar: Public Sector Cybersecurity Survey - What I...

Join SolarWinds® CISO, Tim Brown, and Group Vice President, Brandon Shopp for a webinar to review and discuss our most recent Public Sector Cybersecurity Survey results, including significant differences across public sector market segments and how confident the respondents were in their teams’ ability to keep up with evolving threats.
The Internet Is a Dog-Eat-Dog World, and Your App Is Clad in Milk-Bone Underwear

Presentation at the 2016 Big Sky Developers' Conference.
Overview of the dismal state of security on the Web, some suggestions for better app development processes to mitigate problems.
INFOGRAPHIC: IS YOUR PATIENT DATA PROTECTED?

According to OCR, there were 253 breaches affecting 500 individuals or more w/ a combined loss of over 112M records. Healthcare Failing to secure their data
48% encountered a data breach or failed a compliance audit in the last 12 months
26% are protecting data because of a past data breach
138% jump in number of breached healthcare records since 2012
The estimated cost for HIPAA breaches since 2009 has reached over 31 billion dollars.
Healthcare IT Challenges
42% of 2014 data breaches were in healthcare
90% of healthcare organizations have had at least 1 data breach in past 2 years
40% report that they have had more than 5 incidents of the entire U.S population was impacted by cybercrime in 9 months
Healthcare Cost of Breach
29% Reputation and brand damage
21% lost productivity
19% Lost Revenue
12% Forensics
10% Technical Support
8% Compliance Regulatory
With Data breaches expected to reach $2.1 trillion globally by 2019, which is four times the expected cost for cybercrime in 2015, It's apparent that a new approach to data security is needed if organizations are to stay ahead of the attackers and more effectively protect their intellectual property, data, customer information, employees, and their bottom lines against data breaches in the future
Contact us to learn how to safeguard against such breaches and implement it security strategy.
State of Security

All product and company names mentioned herein are for identification and educational purposes only and are the property of, and may be trademarks of, their respective owners.
HEALTHCARE IT SERVICES MARKET: THE OUTLOOK FOR 2017

Findings from our first annual survey : healthcare IT services demand environment and outlook for 2017
Cybersercurity Resource Allocation & Efficacy Index: 2020 - 2021 Trends

Hear how security pros are responding and adapting to increased attacks and breaches, including facilitating more comprehensive cyber threat management strategies and best practices and the increasing investments and resource utilization to mitigate these challenges. Listen to the webinar, based on the Cybersecurity Resource Allocation & Efficacy (CRAE) Index study for Q1 2021, from CyberRisk Alliance Business Intelligence to hear the panel of experts:
•Review survey results from CRAE Index’s Q1 global research study;
•Discuss the latest trends on proactive and reactive cybersecurity; and
•Hear insights on what lies ahead.
2018 LexisNexis Fraud Mitigation Study

LexisNexis® Risk Solutions commissioned the Fraud Mitigation Study to uncover fraud trends and patterns. 800 fraud mitigation professionals from insurance, financial services, retail, government, healthcare and communications took part in the survey.
Its 2018... Should Pharma Still be Scared of Digital?

One of Pharma's biggest fears when it comes to adopting digital and new technology, is fear of regulations and compliance. To see how much of an issue this really is, breaches of the ABPI code of practice were analyzed over 2017 & 2016, across all channels. The results are interesting...
CAPP Conference Survey

CynergisTek’s Survey Data Reveals Leading Cybersecurity Concerns for Healthcare Organization Executives.
Client-Conference Data Unveils That Risks Associated with Internet of Things, Medical Devices, Third-Party Vendors, and Program Management are Top of Mind for Security Executives, Yet Action is Lagging
Similar to Verizon DBIR 2021 (20)
Government and Education Webinar: Public Sector Cybersecurity Survey - What I...

Government and Education Webinar: Public Sector Cybersecurity Survey - What I...
The Internet Is a Dog-Eat-Dog World, and Your App Is Clad in Milk-Bone Underwear

The Internet Is a Dog-Eat-Dog World, and Your App Is Clad in Milk-Bone Underwear
HEALTHCARE IT SERVICES MARKET: THE OUTLOOK FOR 2017

HEALTHCARE IT SERVICES MARKET: THE OUTLOOK FOR 2017
Cybersercurity Resource Allocation & Efficacy Index: 2020 - 2021 Trends

Cybersercurity Resource Allocation & Efficacy Index: 2020 - 2021 Trends
Its 2018... Should Pharma Still be Scared of Digital?

Its 2018... Should Pharma Still be Scared of Digital?
More from SOCRadar Inc
Dark Web Slangs-2

Escrow is related to financial transactions. When there are two parties in process of a transaction, there is a third party (neutral) that holds the 'escrow money'. This action is done to ensure that a transaction payment will be made to a seller on completion of items sent to a buyer. Until the buyer declares the seller has met the terms of purchase, the money will be held 'in escrow'.
Cost for Failed Certificate Management Practices

The Impact of Unsecured Digital Identities report includes the results of this survey for five scenarios, including the operational and compliance costs, the cost of security exploits, and the likelihood of occurring in the next two years.
Types of impersonating

Using social engineering skills and of course other hacking skills, threat actors send legitimate-looking emails, impersonated domains or create completely cloned websites to create traps for organizations. In able to thwart these actions, you should know what the difference between these types of cybercrimes is.
Type of Malware

Malware is any software intentionally designed to cause damage to a computer, server, client, or computer network.
Type of Threat Actor

Threat Actor: cyber terrorist, hactivist, insider threat, organized hacker, state sponsored hacker
Threat Intelligence Keys

Type of Data
Type of Data Collection Methods
Type of Threat Intelligence Feeds
More from SOCRadar Inc (7)
Recently uploaded
GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...

Effective Application Security in Software Delivery lifecycle using Deployment Firewall and DBOM
The modern software delivery process (or the CI/CD process) includes many tools, distributed teams, open-source code, and cloud platforms. Constant focus on speed to release software to market, along with the traditional slow and manual security checks has caused gaps in continuous security as an important piece in the software supply chain. Today organizations feel more susceptible to external and internal cyber threats due to the vast attack surface in their applications supply chain and the lack of end-to-end governance and risk management.
The software team must secure its software delivery process to avoid vulnerability and security breaches. This needs to be achieved with existing tool chains and without extensive rework of the delivery processes. This talk will present strategies and techniques for providing visibility into the true risk of the existing vulnerabilities, preventing the introduction of security issues in the software, resolving vulnerabilities in production environments quickly, and capturing the deployment bill of materials (DBOM).
Speakers:
Bob Boule
Robert Boule is a technology enthusiast with PASSION for technology and making things work along with a knack for helping others understand how things work. He comes with around 20 years of solution engineering experience in application security, software continuous delivery, and SaaS platforms. He is known for his dynamic presentations in CI/CD and application security integrated in software delivery lifecycle.
Gopinath Rebala
Gopinath Rebala is the CTO of OpsMx, where he has overall responsibility for the machine learning and data processing architectures for Secure Software Delivery. Gopi also has a strong connection with our customers, leading design and architecture for strategic implementations. Gopi is a frequent speaker and well-known leader in continuous delivery and integrating security into software delivery.
GraphRAG is All You need? LLM & Knowledge Graph

Guy Korland, CEO and Co-founder of FalkorDB, will review two articles on the integration of language models with knowledge graphs.
1. Unifying Large Language Models and Knowledge Graphs: A Roadmap.
https://arxiv.org/abs/2306.08302
2. Microsoft Research's GraphRAG paper and a review paper on various uses of knowledge graphs:
https://www.microsoft.com/en-us/research/blog/graphrag-unlocking-llm-discovery-on-narrative-private-data/
Elizabeth Buie - Older adults: Are we really designing for our future selves?

Elizabeth Buie - Older adults: Are we really designing for our future selves?
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar
Smart TV Buyer Insights Survey 2024 by 91mobiles.pdf

91mobiles recently conducted a Smart TV Buyer Insights Survey in which we asked over 3,000 respondents about the TV they own, aspects they look at on a new TV, and their TV buying preferences.
A tale of scale & speed: How the US Navy is enabling software delivery from l...

Rapid and secure feature delivery is a goal across every application team and every branch of the DoD. The Navy’s DevSecOps platform, Party Barge, has achieved:
- Reduction in onboarding time from 5 weeks to 1 day
- Improved developer experience and productivity through actionable findings and reduction of false positives
- Maintenance of superior security standards and inherent policy enforcement with Authorization to Operate (ATO)
Development teams can ship efficiently and ensure applications are cyber ready for Navy Authorizing Officials (AOs). In this webinar, Sigma Defense and Anchore will give attendees a look behind the scenes and demo secure pipeline automation and security artifacts that speed up application ATO and time to production.
We will cover:
- How to remove silos in DevSecOps
- How to build efficient development pipeline roles and component templates
- How to deliver security artifacts that matter for ATO’s (SBOMs, vulnerability reports, and policy evidence)
- How to streamline operations with automated policy checks on container images
Leading Change strategies and insights for effective change management pdf 1.pdf

Leading Change strategies and insights for effective change management pdf 1.pdf
Welocme to ViralQR, your best QR code generator.

Welcome to ViralQR, your best QR code generator available on the market!
At ViralQR, we design static and dynamic QR codes. Our mission is to make business operations easier and customer engagement more powerful through the use of QR technology. Be it a small-scale business or a huge enterprise, our easy-to-use platform provides multiple choices that can be tailored according to your company's branding and marketing strategies.
Our Vision
We are here to make the process of creating QR codes easy and smooth, thus enhancing customer interaction and making business more fluid. We very strongly believe in the ability of QR codes to change the world for businesses in their interaction with customers and are set on making that technology accessible and usable far and wide.
Our Achievements
Ever since its inception, we have successfully served many clients by offering QR codes in their marketing, service delivery, and collection of feedback across various industries. Our platform has been recognized for its ease of use and amazing features, which helped a business to make QR codes.
Our Services
At ViralQR, here is a comprehensive suite of services that caters to your very needs:
Static QR Codes: Create free static QR codes. These QR codes are able to store significant information such as URLs, vCards, plain text, emails and SMS, Wi-Fi credentials, and Bitcoin addresses.
Dynamic QR codes: These also have all the advanced features but are subscription-based. They can directly link to PDF files, images, micro-landing pages, social accounts, review forms, business pages, and applications. In addition, they can be branded with CTAs, frames, patterns, colors, and logos to enhance your branding.
Pricing and Packages
Additionally, there is a 14-day free offer to ViralQR, which is an exceptional opportunity for new users to take a feel of this platform. One can easily subscribe from there and experience the full dynamic of using QR codes. The subscription plans are not only meant for business; they are priced very flexibly so that literally every business could afford to benefit from our service.
Why choose us?
ViralQR will provide services for marketing, advertising, catering, retail, and the like. The QR codes can be posted on fliers, packaging, merchandise, and banners, as well as to substitute for cash and cards in a restaurant or coffee shop. With QR codes integrated into your business, improve customer engagement and streamline operations.
Comprehensive Analytics
Subscribers of ViralQR receive detailed analytics and tracking tools in light of having a view of the core values of QR code performance. Our analytics dashboard shows aggregate views and unique views, as well as detailed information about each impression, including time, device, browser, and estimated location by city and country.
So, thank you for choosing ViralQR; we have an offer of nothing but the best in terms of QR code services to meet business diversity!
The Art of the Pitch: WordPress Relationships and Sales

Clients don’t know what they don’t know. What web solutions are right for them? How does WordPress come into the picture? How do you make sure you understand scope and timeline? What do you do if sometime changes?
All these questions and more will be explored as we talk about matching clients’ needs with what your agency offers without pulling teeth or pulling your hair out. Practical tips, and strategies for successful relationship building that leads to closing the deal.
LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...

Do you want to learn how to model and simulate an electrical network from scratch in under an hour?
Then welcome to this PowSyBl workshop, hosted by Rte, the French Transmission System Operator (TSO)!
During the webinar, you will discover the PowSyBl ecosystem as well as handle and study an electrical network through an interactive Python notebook.
PowSyBl is an open source project hosted by LF Energy, which offers a comprehensive set of features for electrical grid modelling and simulation. Among other advanced features, PowSyBl provides:
- A fully editable and extendable library for grid component modelling;
- Visualization tools to display your network;
- Grid simulation tools, such as power flows, security analyses (with or without remedial actions) and sensitivity analyses;
The framework is mostly written in Java, with a Python binding so that Python developers can access PowSyBl functionalities as well.
What you will learn during the webinar:
- For beginners: discover PowSyBl's functionalities through a quick general presentation and the notebook, without needing any expert coding skills;
- For advanced developers: master the skills to efficiently apply PowSyBl functionalities to your real-world scenarios.
PHP Frameworks: I want to break free (IPC Berlin 2024)

In this presentation, we examine the challenges and limitations of relying too heavily on PHP frameworks in web development. We discuss the history of PHP and its frameworks to understand how this dependence has evolved. The focus will be on providing concrete tips and strategies to reduce reliance on these frameworks, based on real-world examples and practical considerations. The goal is to equip developers with the skills and knowledge to create more flexible and future-proof web applications. We'll explore the importance of maintaining autonomy in a rapidly changing tech landscape and how to make informed decisions in PHP development.
This talk is aimed at encouraging a more independent approach to using PHP frameworks, moving towards a more flexible and future-proof approach to PHP development.
Assuring Contact Center Experiences for Your Customers With ThousandEyes

Presented by Suzanne Phillips and Alex Marcotte
GenAISummit 2024 May 28 Sri Ambati Keynote: AGI Belongs to The Community in O...

“AGI should be open source and in the public domain at the service of humanity and the planet.”
Dev Dives: Train smarter, not harder – active learning and UiPath LLMs for do...

💥 Speed, accuracy, and scaling – discover the superpowers of GenAI in action with UiPath Document Understanding and Communications Mining™:
See how to accelerate model training and optimize model performance with active learning
Learn about the latest enhancements to out-of-the-box document processing – with little to no training required
Get an exclusive demo of the new family of UiPath LLMs – GenAI models specialized for processing different types of documents and messages
This is a hands-on session specifically designed for automation developers and AI enthusiasts seeking to enhance their knowledge in leveraging the latest intelligent document processing capabilities offered by UiPath.
Speakers:
👨🏫 Andras Palfi, Senior Product Manager, UiPath
👩🏫 Lenka Dulovicova, Product Program Manager, UiPath
Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...

Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI)
SAP Sapphire 2024 - ASUG301 building better apps with SAP Fiori.pdf

Building better applications for business users with SAP Fiori.
• What is SAP Fiori and why it matters to you
• How a better user experience drives measurable business benefits
• How to get started with SAP Fiori today
• How SAP Fiori elements accelerates application development
• How SAP Build Code includes SAP Fiori tools and other generative artificial intelligence capabilities
• How SAP Fiori paves the way for using AI in SAP apps
Recently uploaded (20)
GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...

GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...
Assure Contact Center Experiences for Your Customers With ThousandEyes

Assure Contact Center Experiences for Your Customers With ThousandEyes
Elizabeth Buie - Older adults: Are we really designing for our future selves?

Elizabeth Buie - Older adults: Are we really designing for our future selves?
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf
Smart TV Buyer Insights Survey 2024 by 91mobiles.pdf

Smart TV Buyer Insights Survey 2024 by 91mobiles.pdf
A tale of scale & speed: How the US Navy is enabling software delivery from l...

A tale of scale & speed: How the US Navy is enabling software delivery from l...
Leading Change strategies and insights for effective change management pdf 1.pdf

Leading Change strategies and insights for effective change management pdf 1.pdf
The Art of the Pitch: WordPress Relationships and Sales

The Art of the Pitch: WordPress Relationships and Sales
LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...

LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...
PHP Frameworks: I want to break free (IPC Berlin 2024)

PHP Frameworks: I want to break free (IPC Berlin 2024)
FIDO Alliance Osaka Seminar: FIDO Security Aspects.pdf

FIDO Alliance Osaka Seminar: FIDO Security Aspects.pdf
Assuring Contact Center Experiences for Your Customers With ThousandEyes

Assuring Contact Center Experiences for Your Customers With ThousandEyes
GenAISummit 2024 May 28 Sri Ambati Keynote: AGI Belongs to The Community in O...

GenAISummit 2024 May 28 Sri Ambati Keynote: AGI Belongs to The Community in O...
Dev Dives: Train smarter, not harder – active learning and UiPath LLMs for do...

Dev Dives: Train smarter, not harder – active learning and UiPath LLMs for do...
Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...

Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...
FIDO Alliance Osaka Seminar: Passkeys at Amazon.pdf

FIDO Alliance Osaka Seminar: Passkeys at Amazon.pdf
SAP Sapphire 2024 - ASUG301 building better apps with SAP Fiori.pdf

SAP Sapphire 2024 - ASUG301 building better apps with SAP Fiori.pdf
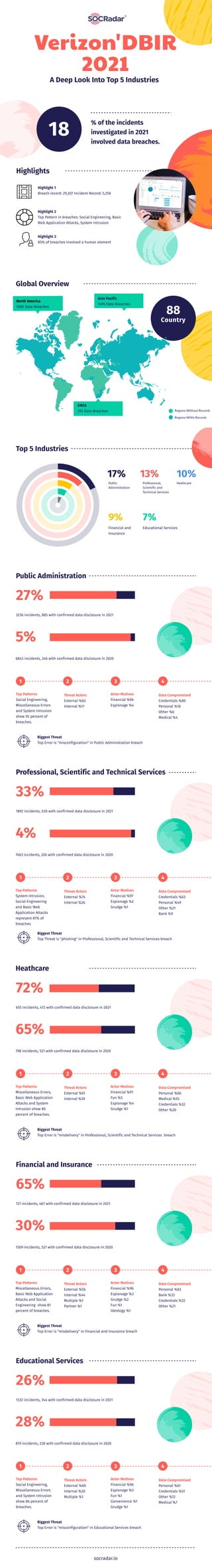
Verizon DBIR 2021
- 1. Highlight 1 Breach record: 29,207 Incident Record: 5,258 Highlight 2 Top Pattern in breaches: Social Engineering, Basic Web Application Attacks, System Intrusion % of the incidents investigated in 2021 involved data breaches. Highlights 18 Highlight 3 85% of breaches involved a human element Verizon'DBIR 2021 A Deep Look Into Top 5 Industries Global Overview North America 1080 Data Breaches Asia Pasific 1495 Data Breaches Country 88 EMEA 293 Data Breaches Regions Without Records Regions Witht Records Top 5 Industries 17% Public Administration 13% 9% 7% Professional, Scientific and Technical Services Financial and Insurance Educational Services 10% Heathcare Public Administration 27% 5% 3236 incidents, 885 with confirmed data disclosure in 2021 Top Patterns Social Engineering, Miscellaneous Errors and System Intrusion show 92 percent of breaches. 1 2 3 4 Actor Motives Financial %96 Espionage %4 Threat Actors External %83 Internal %17 Data Compromised Credentials %80 Personal %18 Other %6 Medical %4 6843 incidents, 346 with confirmed data disclosure in 2020 Biggest Threat Top Error is "misconfiguration" in Public Administration breach Professional, Scientific and Technical Services 33% 4% 1892 incidents, 630 with confirmed data disclosure in 2021 Top Patterns System Intrusion, Social Engineering and Basic Web Application Attacks represent 81% of breaches 1 2 3 4 Actor Motives Financial %97 Espionage %2 Grudge %1 Threat Actors External %74 Internal %26 Data Compromised Credentials %63 Personal %49 Other %21 Bank %9 7463 incidents, 326 with confirmed data disclosure in 2020 Biggest Threat Top Threat is "phishing" in Professional, Scientific and Technical Services breach Heathcare 72% 65% 655 incidents, 472 with confirmed data disclosure in 2021 Top Patterns Miscellaneous Errors, Basic Web Application Attacks and System Intrusion show 86 percent of breaches. 1 2 3 4 Actor Motives Financial %91 Fun %5 Espionage %4 Grudge %1 Threat Actors External %61 Internal %39 Data Compromised Personal %66 Medical %55 Credentials %32 Other %20 798 incidents, 521 with confirmed data disclosure in 2020 Biggest Threat Top Error is "misdelivery" in Professional, Scientific and Technical Services breach Financial and Insurance 65% 30% 721 incidents, 467 with confirmed data disclosure in 2021 Top Patterns Miscellaneous Errors, Basic Web Application Attacks and Social Engineering show 81 percent of breaches. 1 2 3 4 Actor Motives Financial %96 Espionage %3 Grudge %2 Fun %1 Ideology %1 Threat Actors External %56 Internal %44 Multiple %1 Partner %1 Data Compromised Personal %83 Bank %33 Credentials %32 Other %21 1509 incidents, 521 with confirmed data disclosure in 2020 Biggest Threat Top Error is "misdelivery" in Financial and Insurance breach Educational Services 26% 28% 1332 incidents, 344 with confirmed data disclosure in 2021 Top Patterns Social Engineering, Miscellaneous Errors and System Intrusion show 86 percent of breaches. 1 2 3 4 Actor Motives Financial %96 Espionage %3 Fun %1 Convenience %1 Grudge %1 Threat Actors External %80 Internal %20 Multiple %1 Data Compromised Personal %61 Credentials %51 Other %12 Medical %7 819 incidents, 228 with confirmed data disclosure in 2020 Biggest Threat Top Error is "misconfiguration" in Educational Services breach socradar.io
