Costs of Failed Certificate and Key Management Practices
•
2 likes•527 views
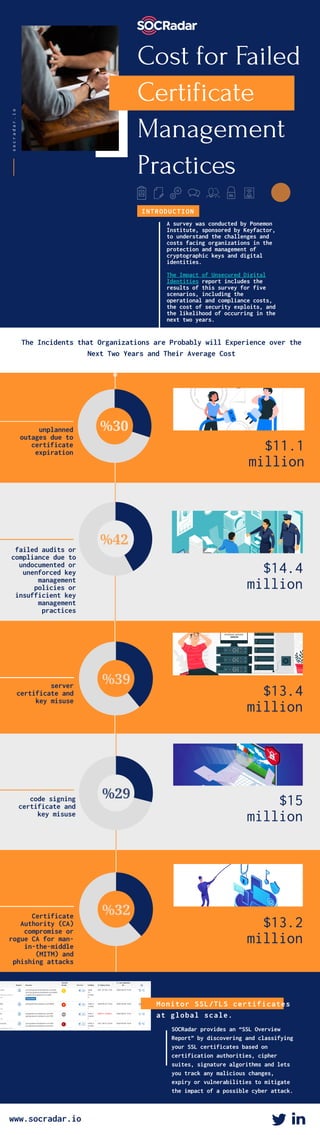
A survey was conducted by Ponemon Institute, sponsored by Keyfactor, to understand the challenges and costs of managing cryptographic keys and digital identities. The report analyzed five scenarios related to unsecured digital identities, including the operational and compliance costs of failures, the cost of security exploits, and the likelihood of these issues occurring in the next two years. On average, the report found that organizations will likely experience unplanned outages due to expired certificates costing $11.1 million, failed audits or compliance issues costing $14.4 million, server or code signing certificate misuse costing $13.4-15 million, and compromise by rogue certificate authorities costing $13.2 million.
Report
Share
Report
Share
Download to read offline
Recommended
Recommended
More Related Content
What's hot
What's hot (19)
Mobey Forum Oslo Aradiom Presentation - How to Choose 2FA Security Solution

Mobey Forum Oslo Aradiom Presentation - How to Choose 2FA Security Solution
Unintentional Insider Threat featuring Dr. Eric Cole

Unintentional Insider Threat featuring Dr. Eric Cole
Iasi code camp 12 october 2013 ana tudosa - challenges in implementing and ...

Iasi code camp 12 october 2013 ana tudosa - challenges in implementing and ...
New Developments in Cybersecurity and Technology for RDOs: Howland

New Developments in Cybersecurity and Technology for RDOs: Howland
VAPT - Vulnerability Assessment & Penetration Testing 

VAPT - Vulnerability Assessment & Penetration Testing
Winning the war on cybercrime keys to holistic fraud prevention 

Winning the war on cybercrime keys to holistic fraud prevention
Similar to Costs of Failed Certificate and Key Management Practices
Similar to Costs of Failed Certificate and Key Management Practices (20)
Ponemon Report: When Trust Online Breaks, Businesses Lose Customers

Ponemon Report: When Trust Online Breaks, Businesses Lose Customers
Feeding the Beast-How Fraud Tools Bring Context into Authentication (Gartner ...

Feeding the Beast-How Fraud Tools Bring Context into Authentication (Gartner ...
Reconsidering Public Key Infrastructure and its Place in Your Enterprise Stra...

Reconsidering Public Key Infrastructure and its Place in Your Enterprise Stra...
Joint Presentation - Part 1: The Future Evolution of E-Banking & Cyber Securi...

Joint Presentation - Part 1: The Future Evolution of E-Banking & Cyber Securi...
45 key vendors and thier online fraud prevention solutions

45 key vendors and thier online fraud prevention solutions
Digital Shadows and the NIST Cyber Security Framework

Digital Shadows and the NIST Cyber Security Framework
Multi Factor Authentication Whitepaper Arx - Intellect Design

Multi Factor Authentication Whitepaper Arx - Intellect Design
More from SOCRadar Inc
More from SOCRadar Inc (8)
Recently uploaded
Recently uploaded (20)
Transcript: #StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024

Transcript: #StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024
Boost PC performance: How more available memory can improve productivity

Boost PC performance: How more available memory can improve productivity
08448380779 Call Girls In Greater Kailash - I Women Seeking Men

08448380779 Call Girls In Greater Kailash - I Women Seeking Men
Breaking the Kubernetes Kill Chain: Host Path Mount

Breaking the Kubernetes Kill Chain: Host Path Mount
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...

Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...
Swan(sea) Song – personal research during my six years at Swansea ... and bey...

Swan(sea) Song – personal research during my six years at Swansea ... and bey...
Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...

Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...
WhatsApp 9892124323 ✓Call Girls In Kalyan ( Mumbai ) secure service

WhatsApp 9892124323 ✓Call Girls In Kalyan ( Mumbai ) secure service
FULL ENJOY 🔝 8264348440 🔝 Call Girls in Diplomatic Enclave | Delhi

FULL ENJOY 🔝 8264348440 🔝 Call Girls in Diplomatic Enclave | Delhi
IAC 2024 - IA Fast Track to Search Focused AI Solutions

IAC 2024 - IA Fast Track to Search Focused AI Solutions
#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024

#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024
08448380779 Call Girls In Civil Lines Women Seeking Men

08448380779 Call Girls In Civil Lines Women Seeking Men
Costs of Failed Certificate and Key Management Practices
- 1. A survey was conducted by Ponemon Institute, sponsored by Keyfactor, to understand the challenges and costs facing organizations in the protection and management of cryptographic keys and digital identities. The Impact of Unsecured Digital Identities report includes the results of this survey for five scenarios, including the operational and compliance costs, the cost of security exploits, and the likelihood of occurring in the next two years. Cost for Failed Certificate Management Practices socradar.io INTRODUCTION The Incidents that Organizations are Probably will Experience over the Next Two Years and Their Average Cost $11.1 million unplanned outages due to certificate expiration %30 %42 failed audits or compliance due to undocumented or unenforced key management policies or insufficient key management practices $14.4 million $13.4 million %39server certificate and key misuse $15 million %29code signing certificate and key misuse $13.2 million Certificate Authority (CA) compromise or rogue CA for man- in-the-middle (MITM) and phishing attacks %32 SOCRadar provides an “SSL Overview Report” by discovering and classifying your SSL certificates based on certification authorities, cipher suites, signature algorithms and lets you track any malicious changes, expiry or vulnerabilities to mitigate the impact of a possible cyber attack. Monitor SSL/TLS certificates at global scale. www.socradar.io
