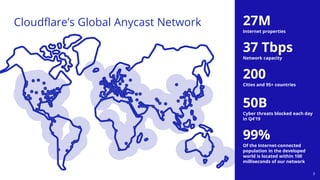
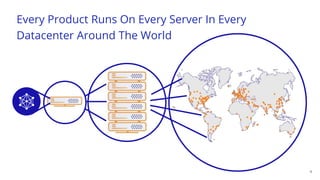
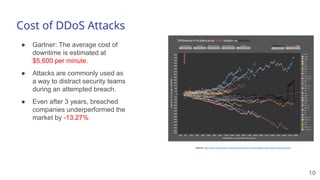
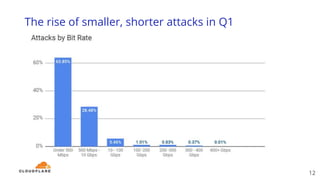
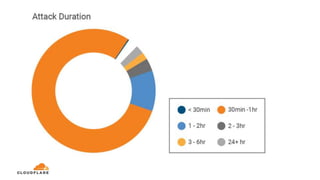
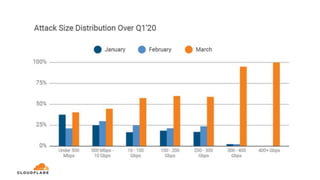
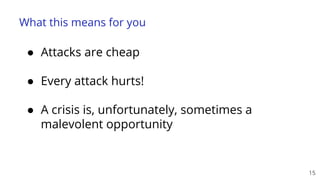
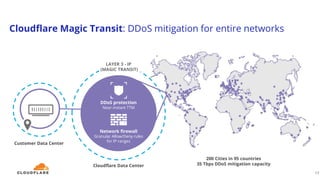
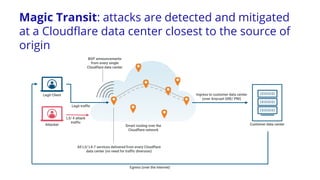
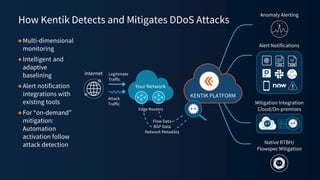
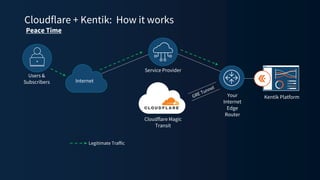
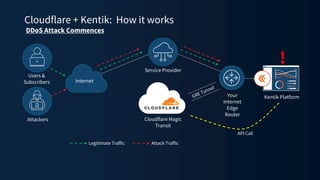
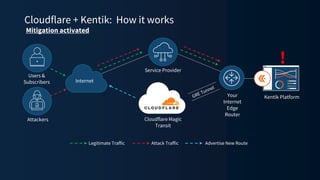
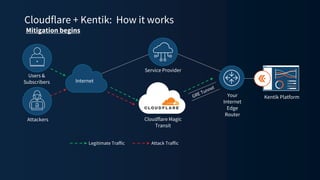
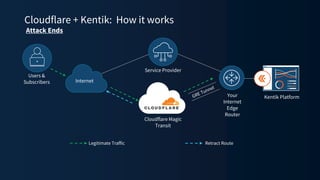
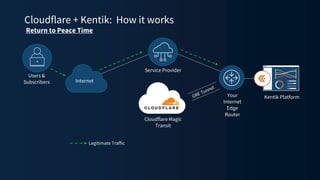
The document discusses a webinar on monitoring and mitigating DDoS attacks using Cloudflare and Kentik's technologies, highlighting their global network capabilities and the critical nature of DDoS protection. It outlines the costs associated with DDoS attacks, current trends, and the integration of Cloudflare's Magic Transit service for automated defense against such threats. Furthermore, the document promotes a special offer for businesses looking to transition from their current service providers to Cloudflare's solutions.