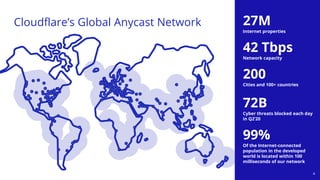
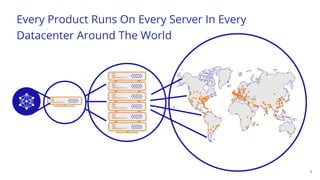
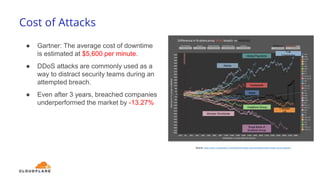
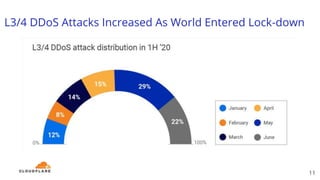
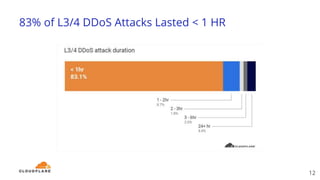
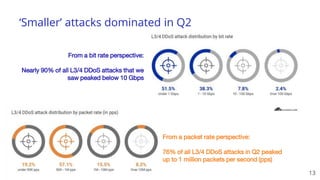
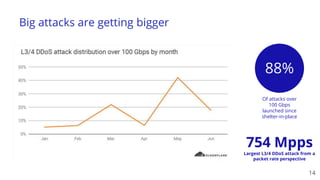
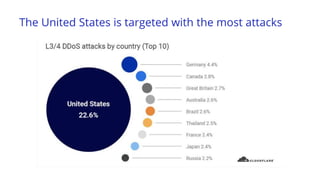
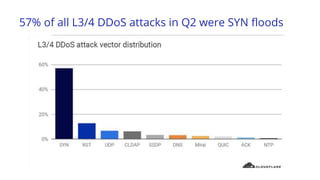
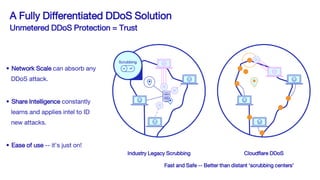
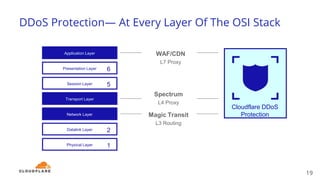
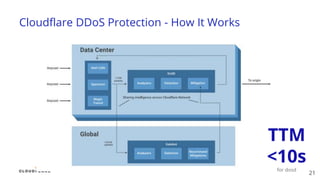
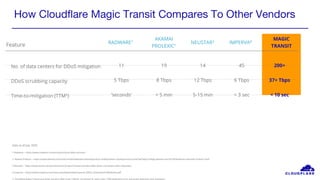
The document discusses recent DDoS attack trends and Cloudflare's protective measures against them, highlighting the increase in attacks during the COVID-19 lockdown. It explains various types of DDoS attacks, their costs, and the effectiveness of Cloudflare's solutions, including the 'Magic Transit' service for enhanced network protection. Additionally, it features a case study on how Cloudflare helped restore service for Wikipedia following a massive DDoS attack.