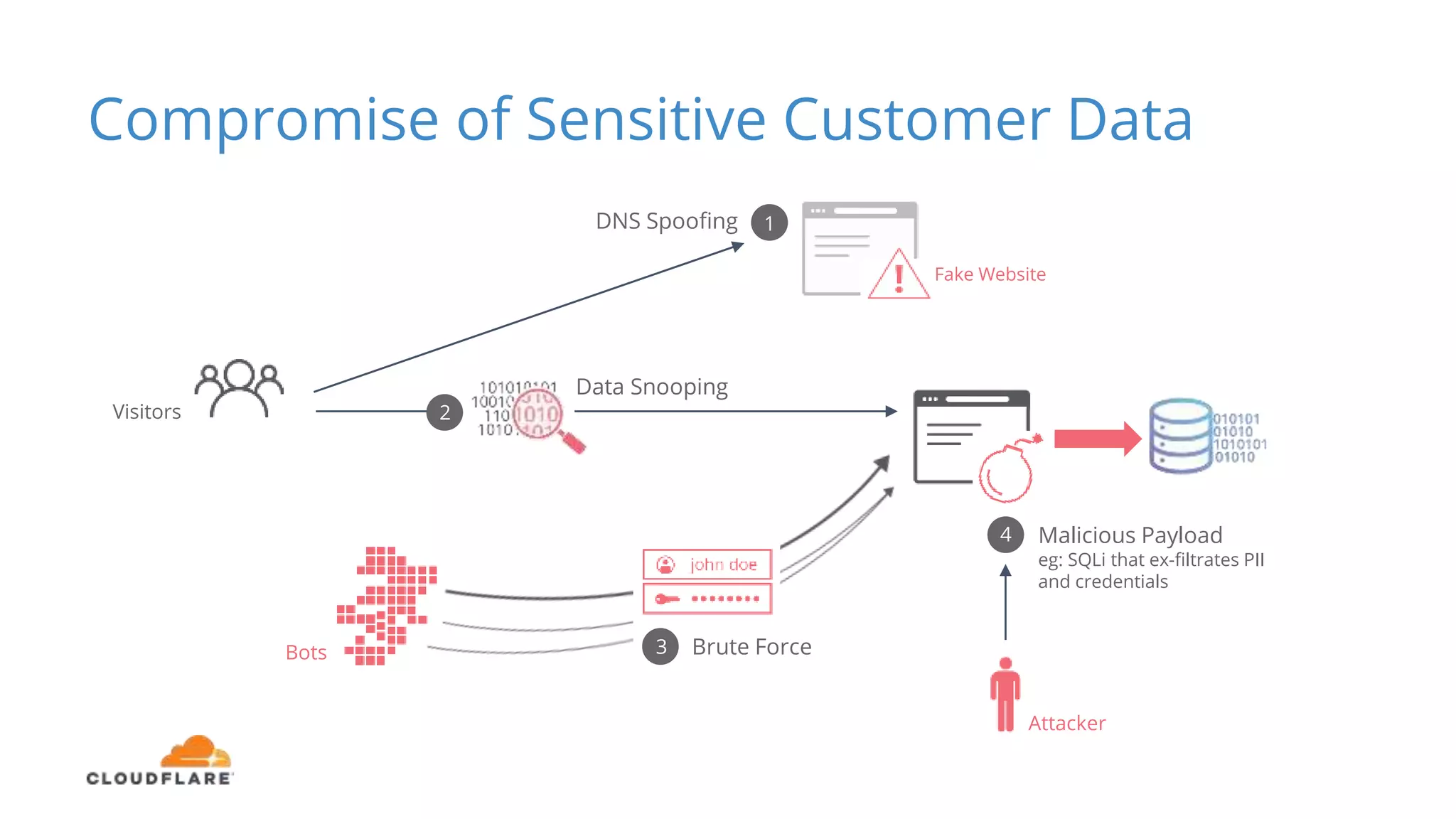
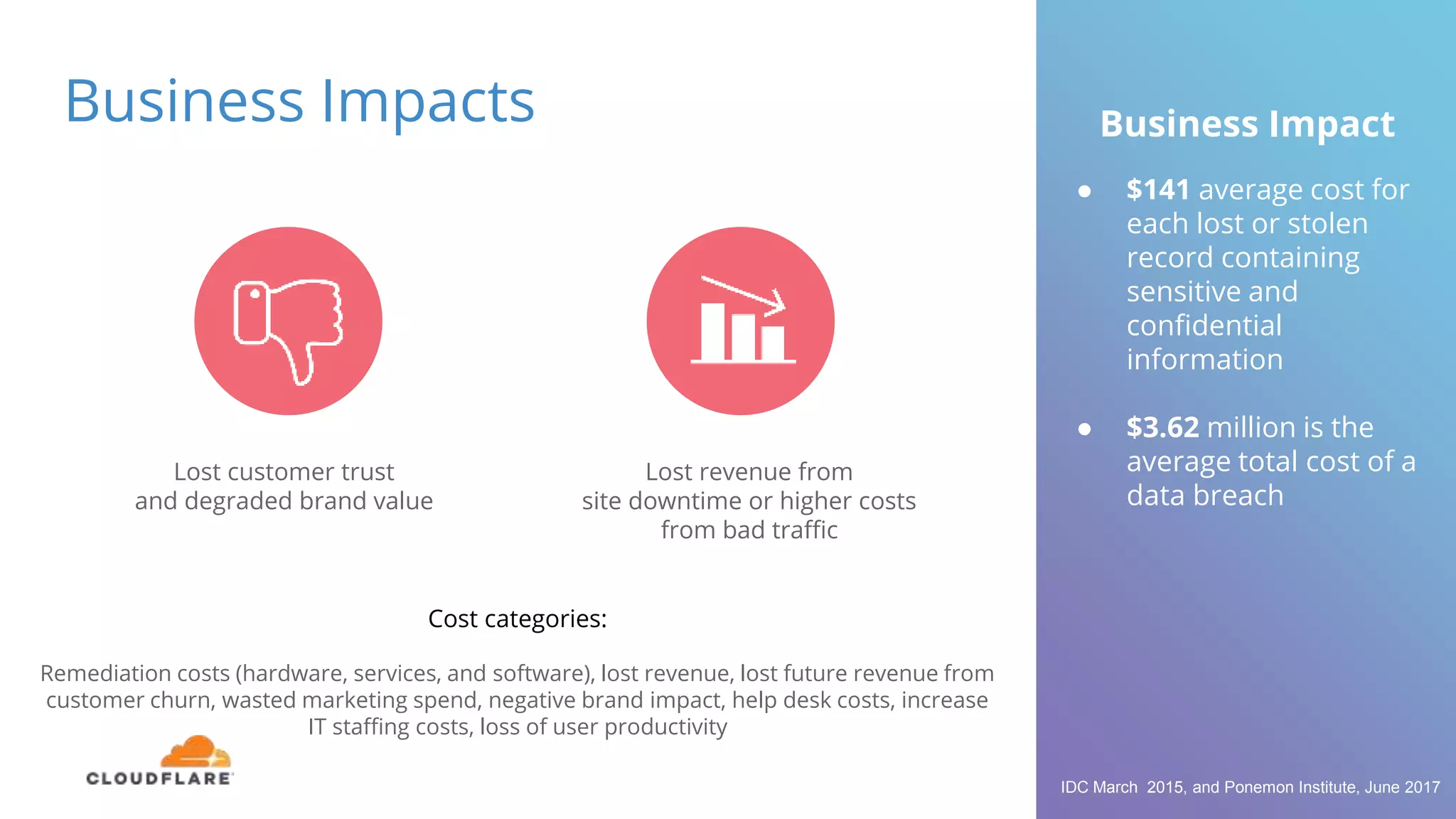
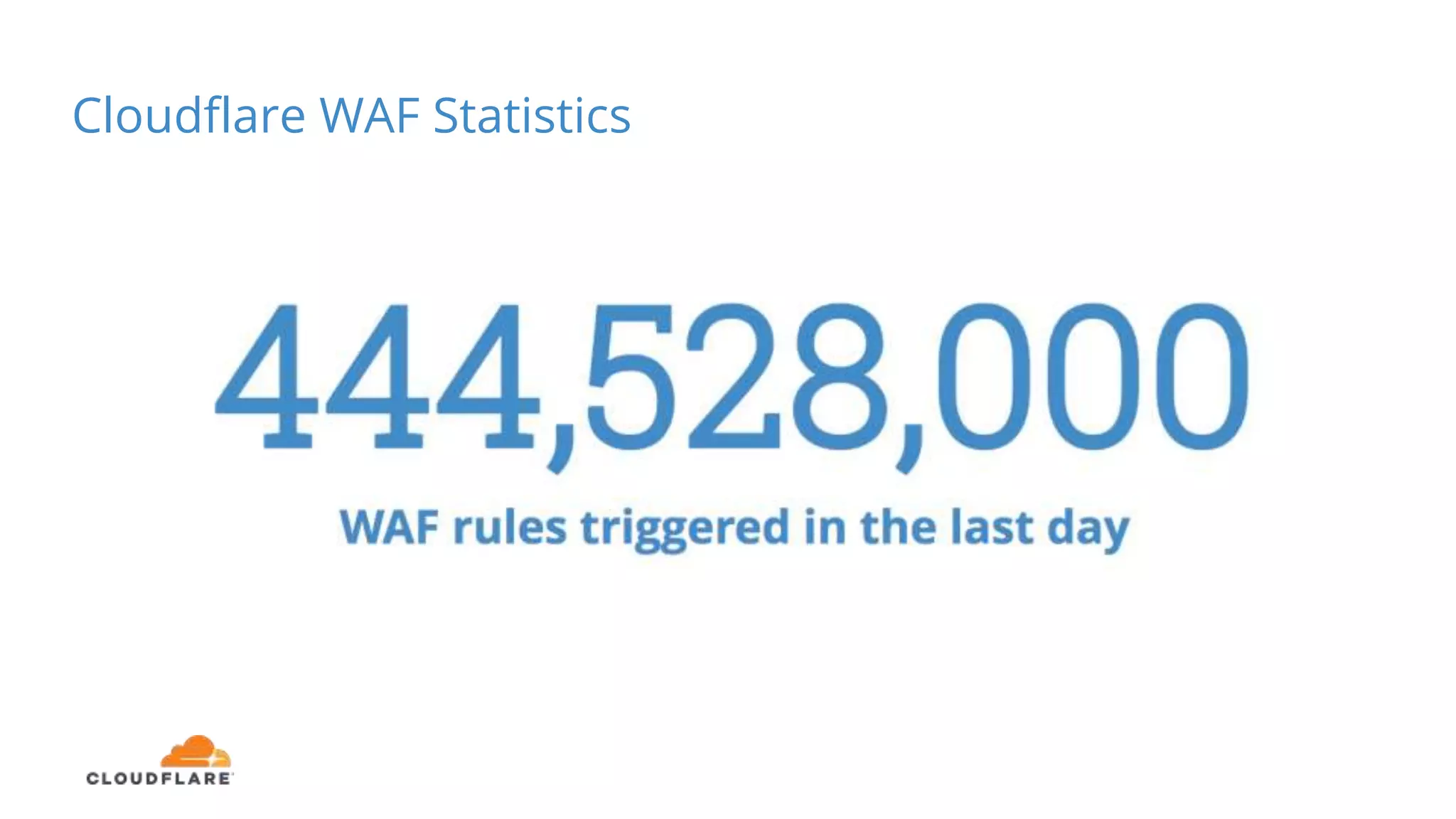
The document discusses the limitations of traditional web application firewalls (WAFs) and highlights current security challenges, such as DDoS attacks and data breaches, that impact businesses. It emphasizes the importance of choosing an intelligent WAF, like Cloudflare, which offers comprehensive protection through advanced security measures, global infrastructure, and real-time intelligence. The content also outlines potential business impacts from security incidents, including financial losses and damage to brand value.