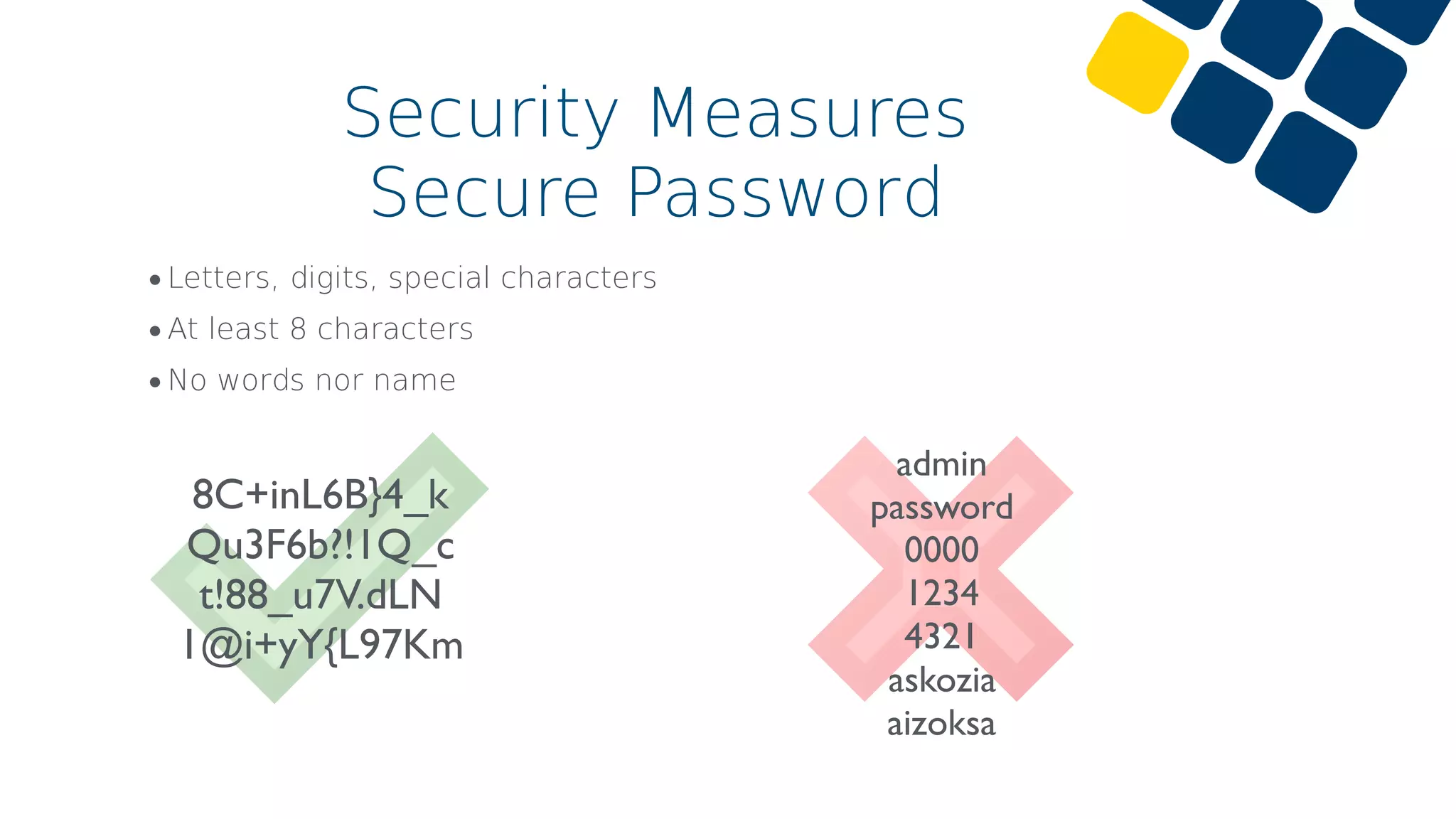
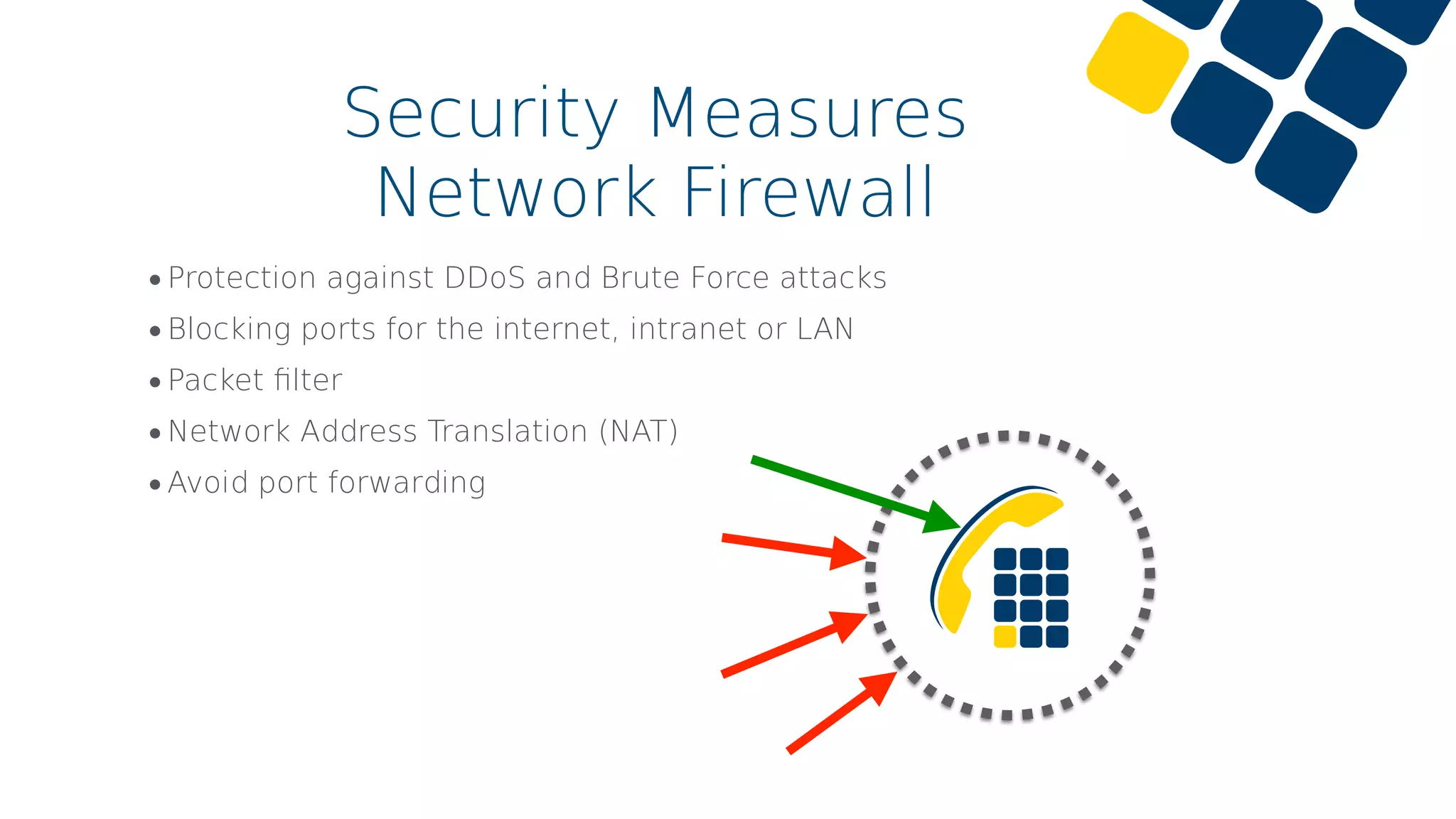
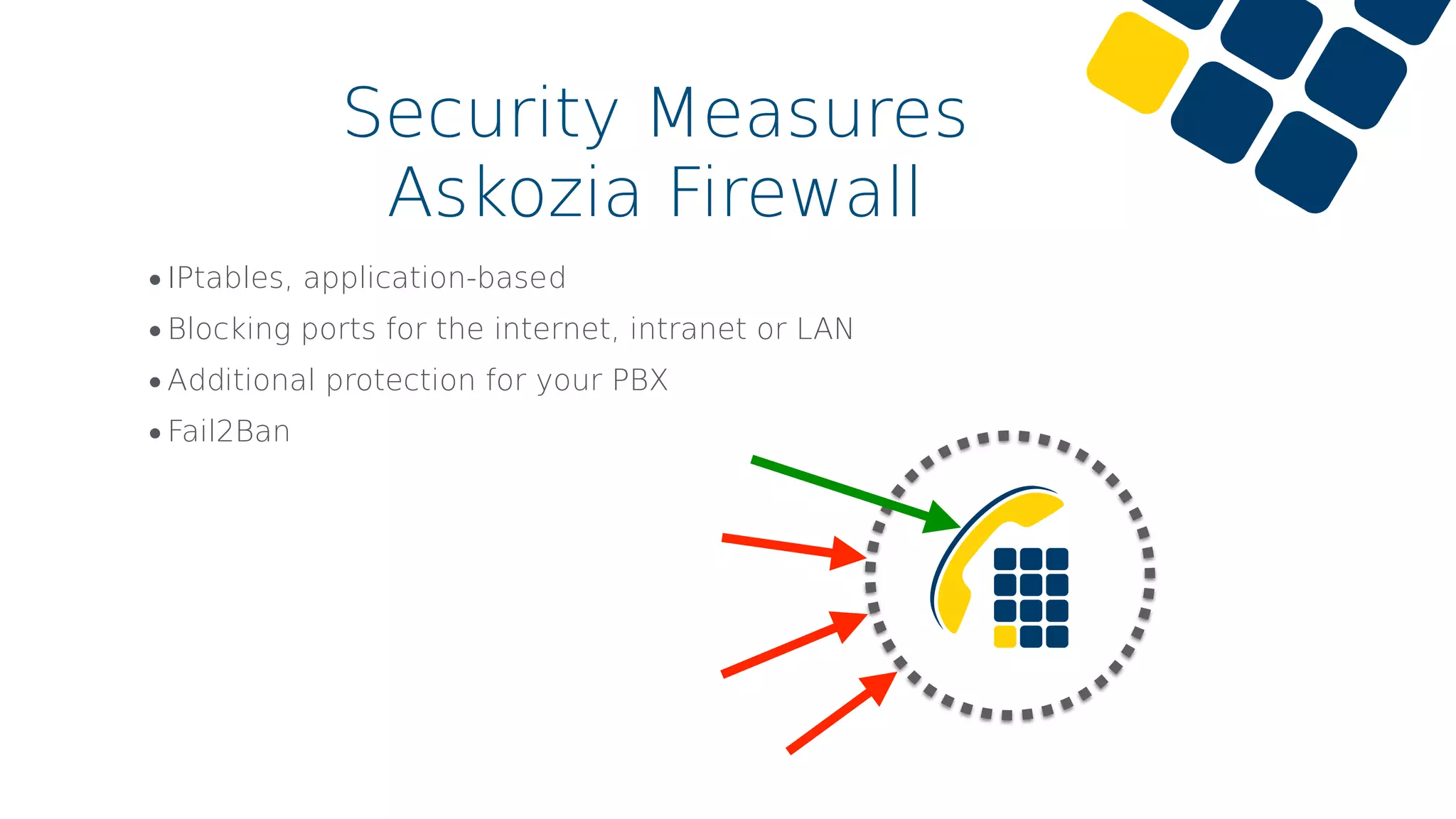
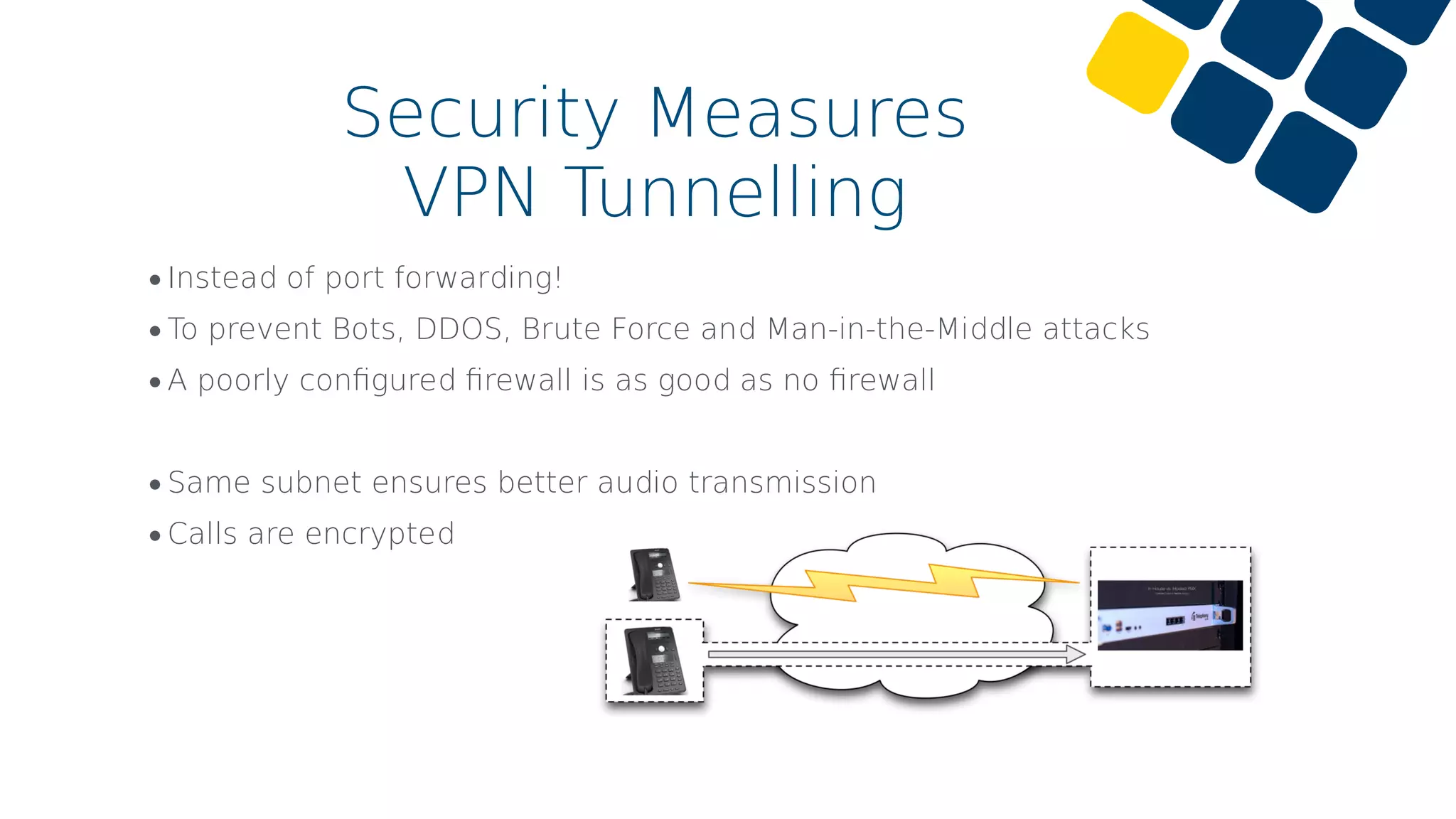
The document discusses common cybersecurity mistakes and attacks, emphasizing vulnerabilities related to VoIP systems such as eavesdropping, DoS attacks, and identity spoofing. Security measures like strong password policies, proper firewall configuration, and VPN usage are recommended to mitigate risks. The importance of regular updates, limited access rights, and having a backup plan is also highlighted.