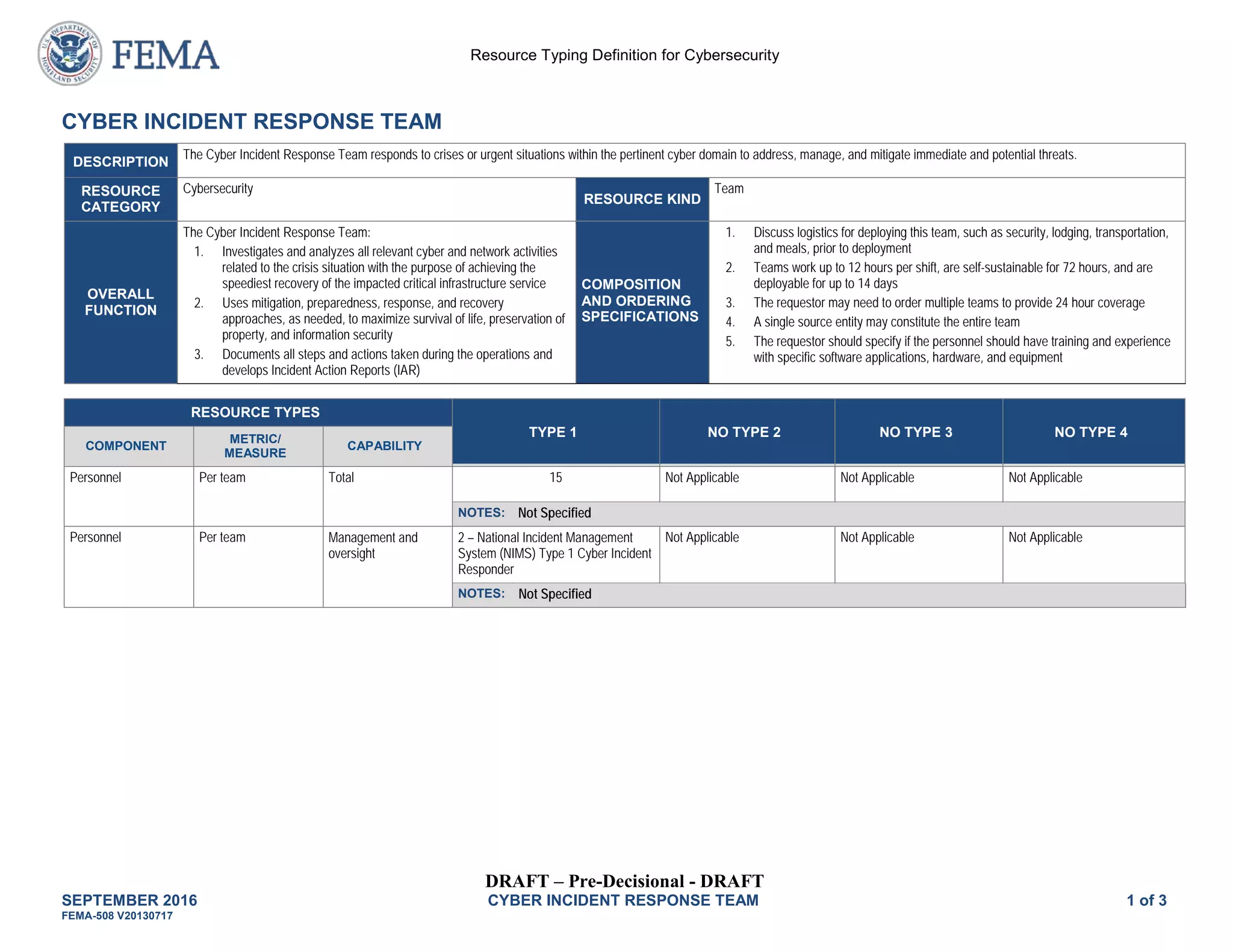
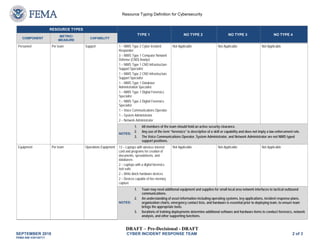
The Cyber Incident Response Team responds to cyber crises and threats. It is composed of 15 personnel including managers, analysts, specialists in areas like forensics and infrastructure. The team investigates incidents, uses mitigation approaches, and documents actions. It requires equipment like laptops, forensics tools, and communications devices and is deployable for up to 14 days.