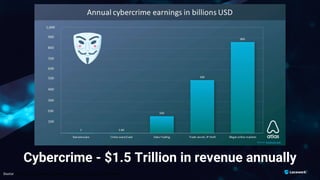
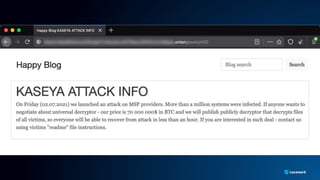
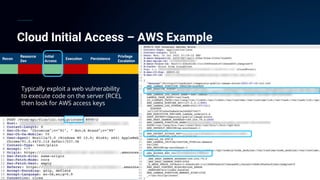
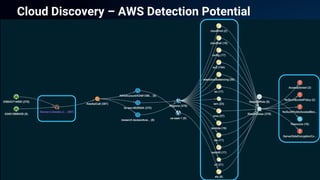
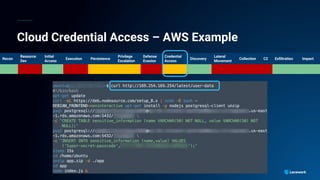
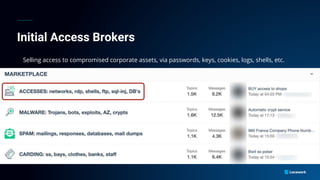
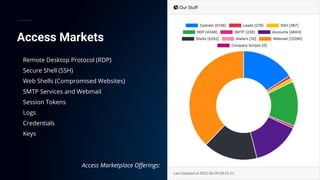
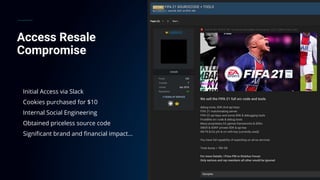
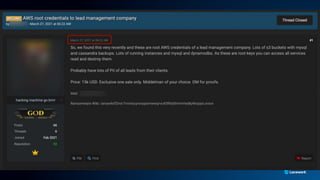
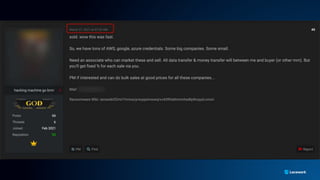
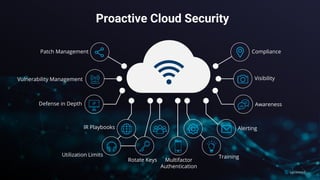
The document presents a detailed analysis of the rising threat of cybercrime, particularly in the context of cloud computing, which is generating $1.5 trillion annually. It explores various tactics and techniques used in ransomware attacks, especially within AWS environments, outlining the importance of early detection and comprehensive security measures. Additionally, it discusses the underground economy and cryptocurrency-related attack vectors that further complicate the cybersecurity landscape.