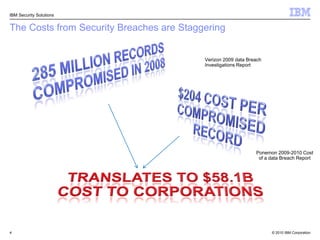
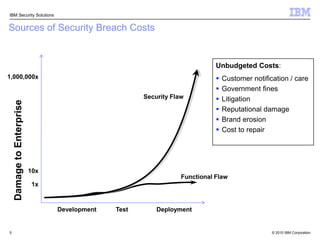
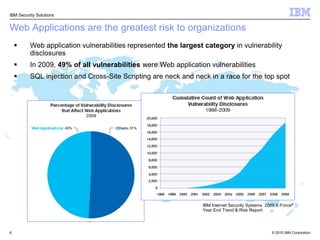
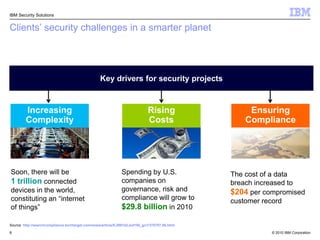
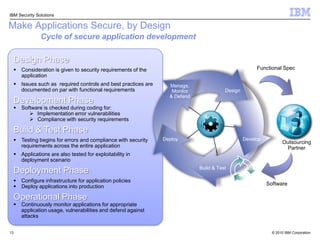
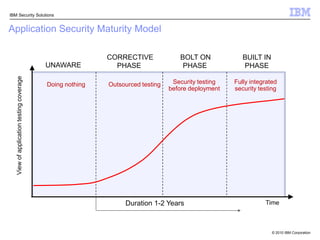
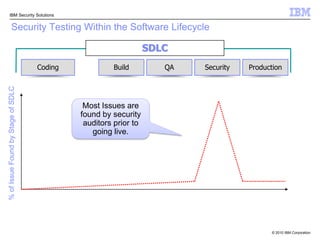
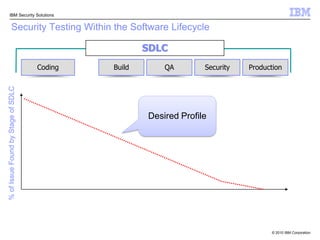
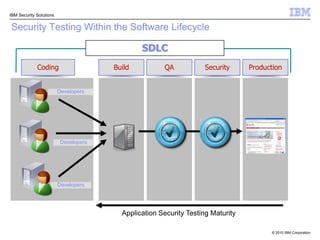
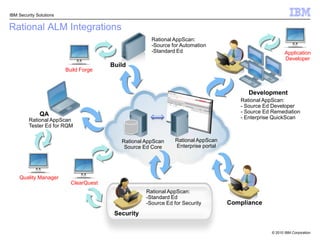
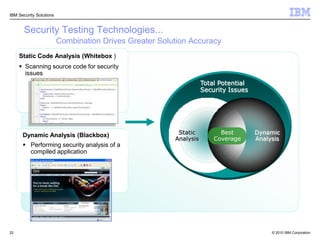
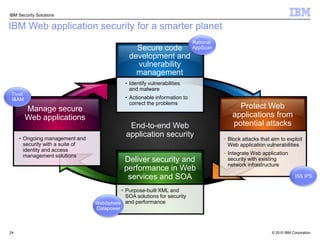
This document discusses IBM's Rational Application Security solution. It begins with current trends in application security, noting that web applications are the greatest risk and source of vulnerabilities. It then introduces Rational AppScan Suite for comprehensive application vulnerability management. The document discusses strategies for customer success, including integrating application security into the development lifecycle. It provides an overview of the Rational AppScan Suite and how IBM offers full application security coverage through additional products that complement Rational AppScan.