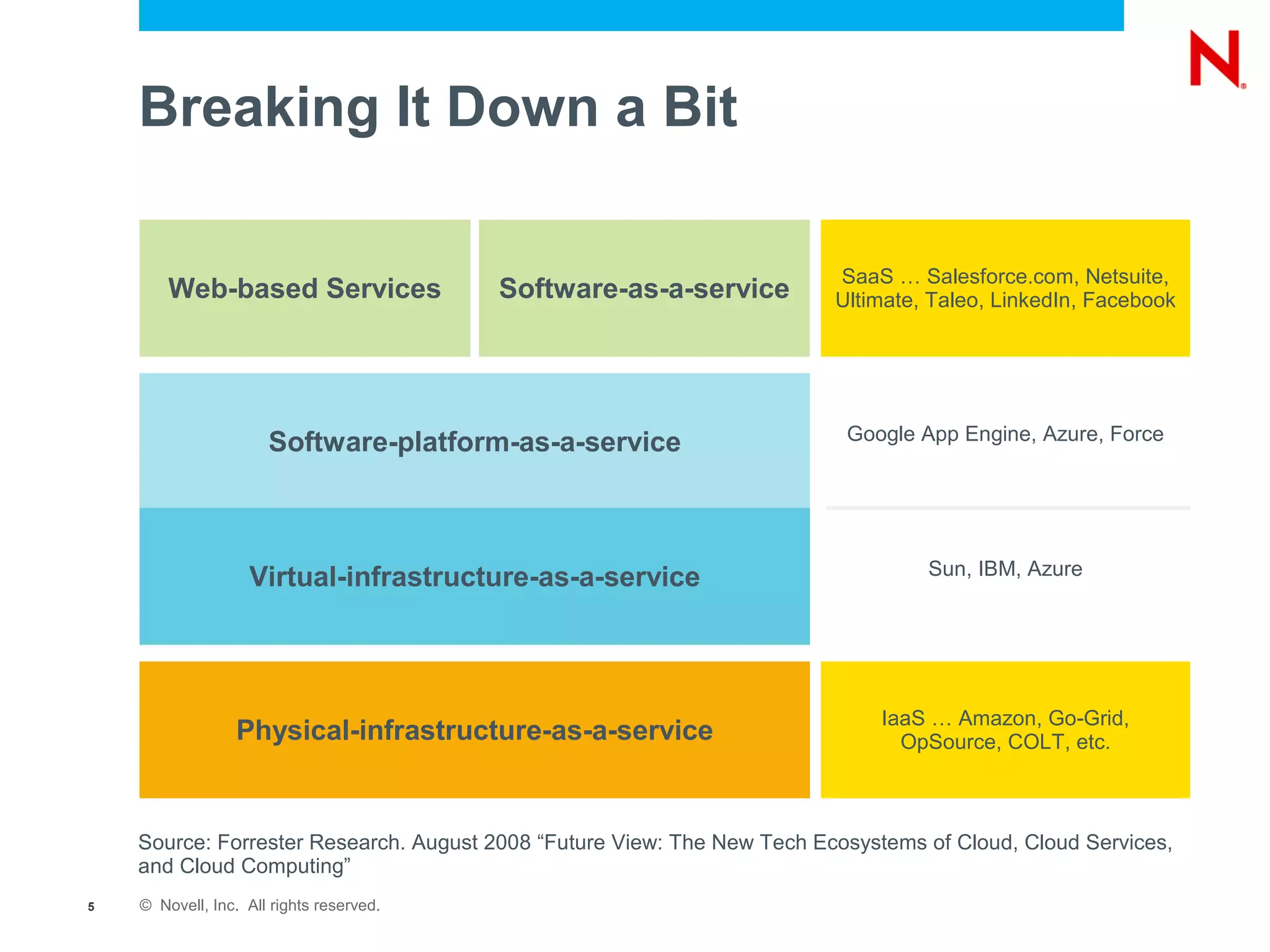
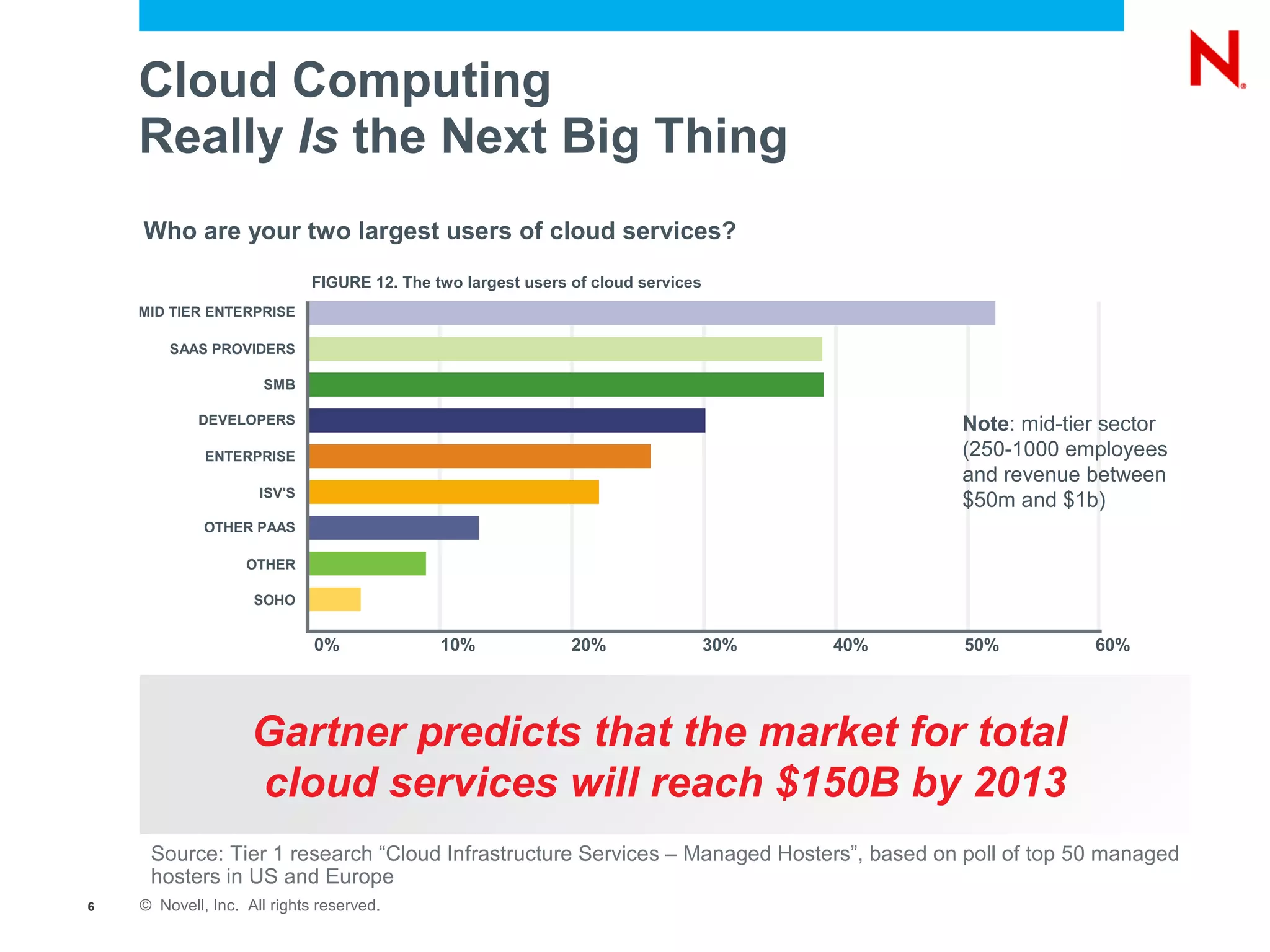
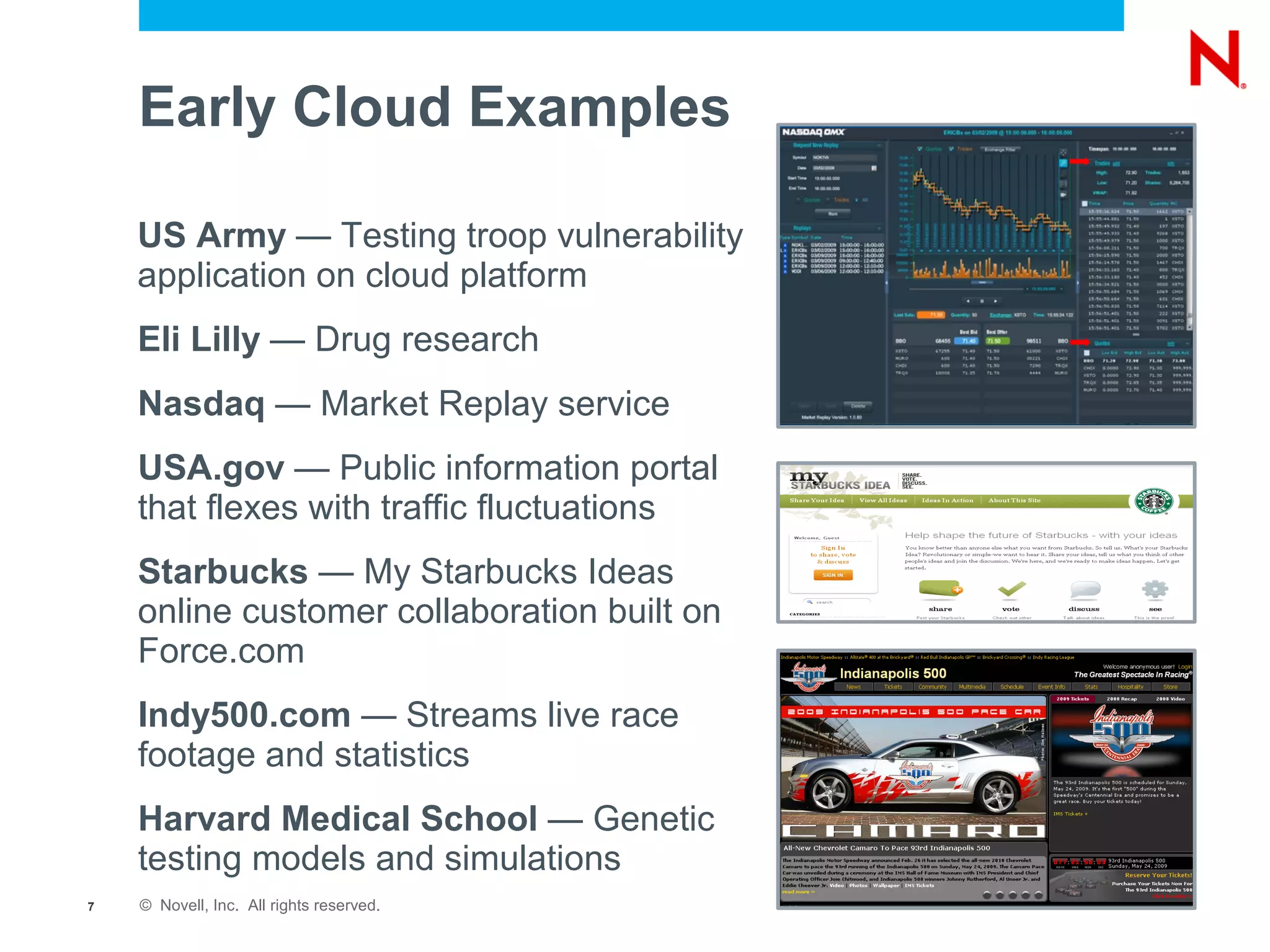
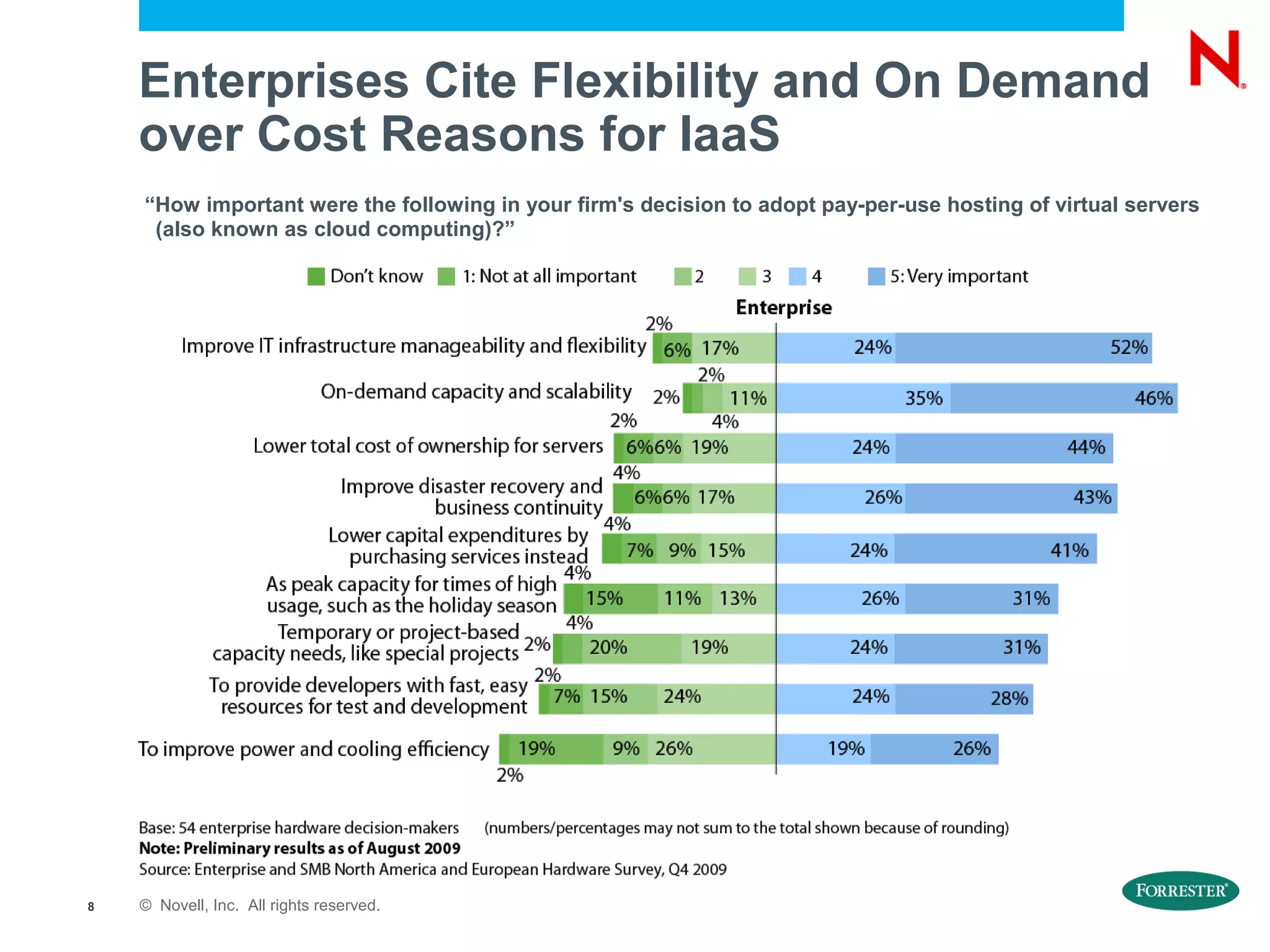
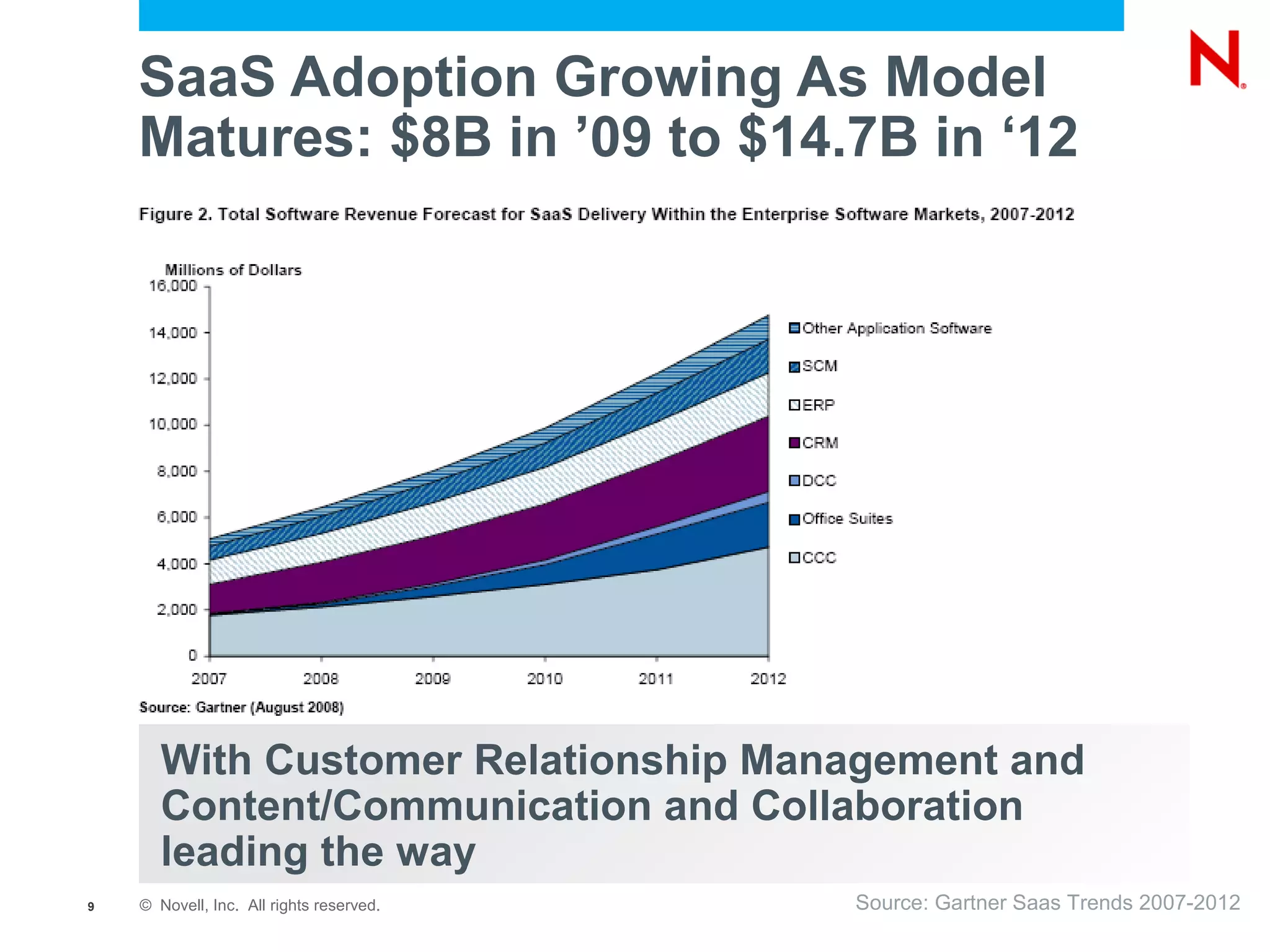
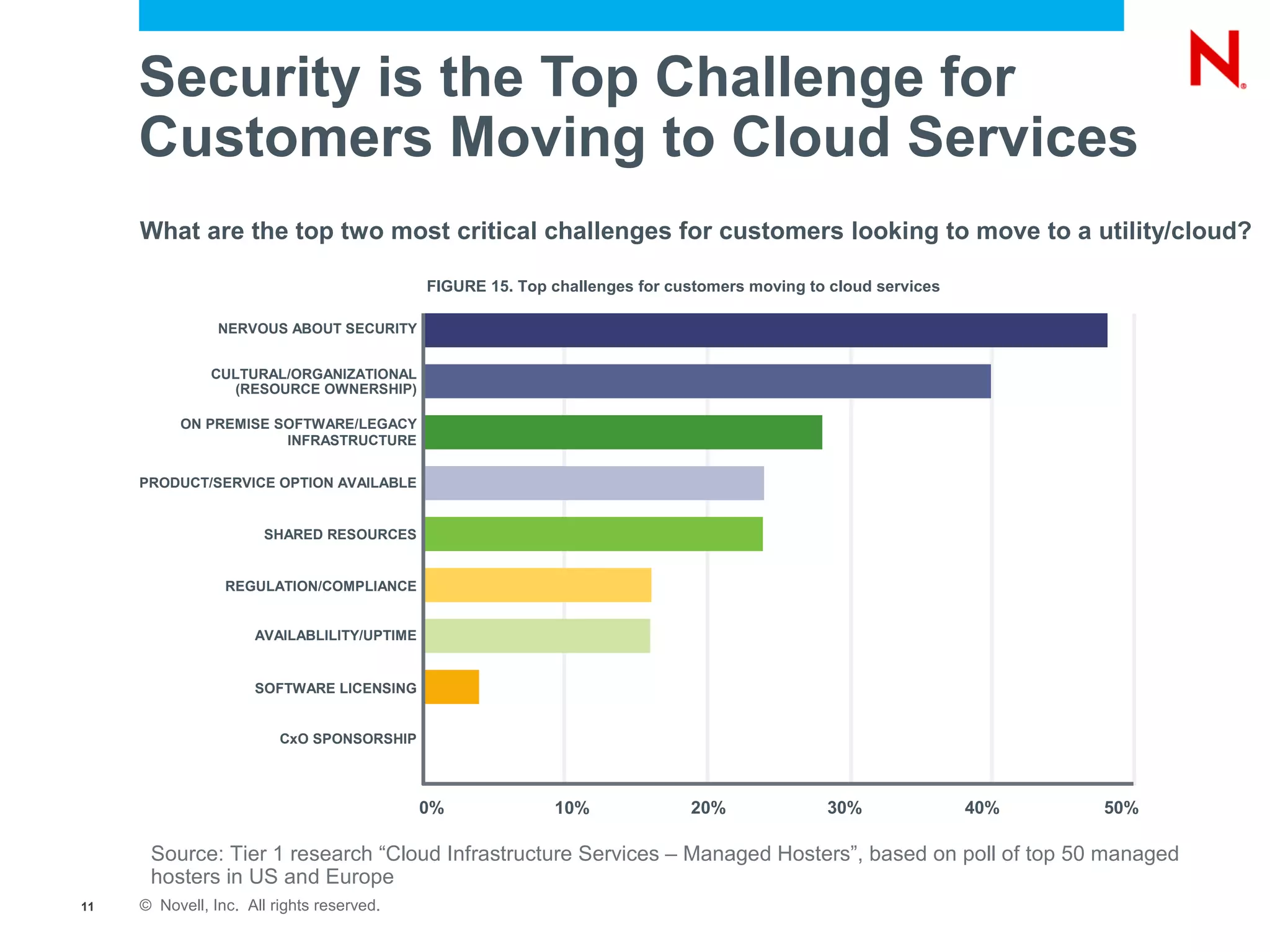
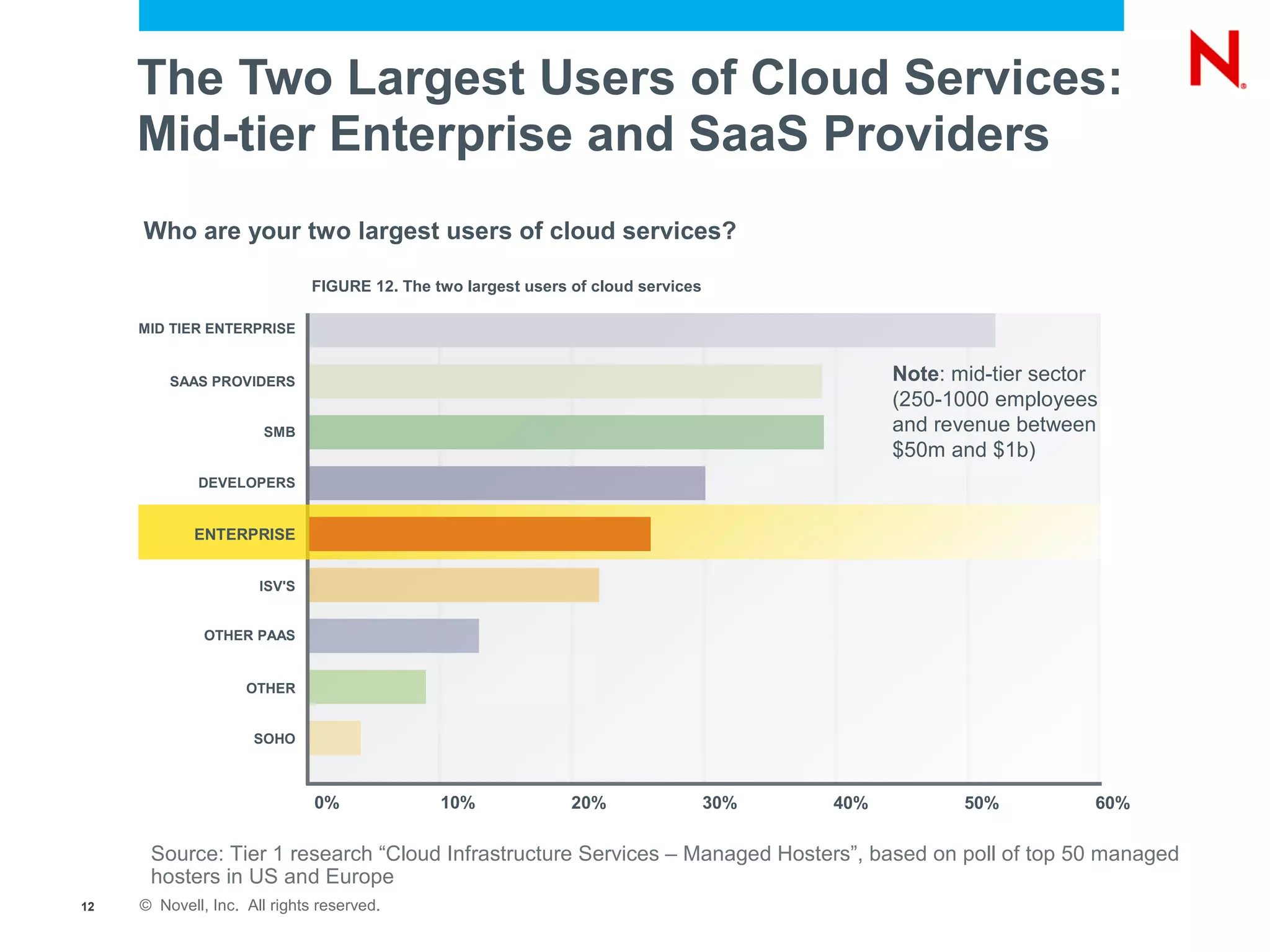
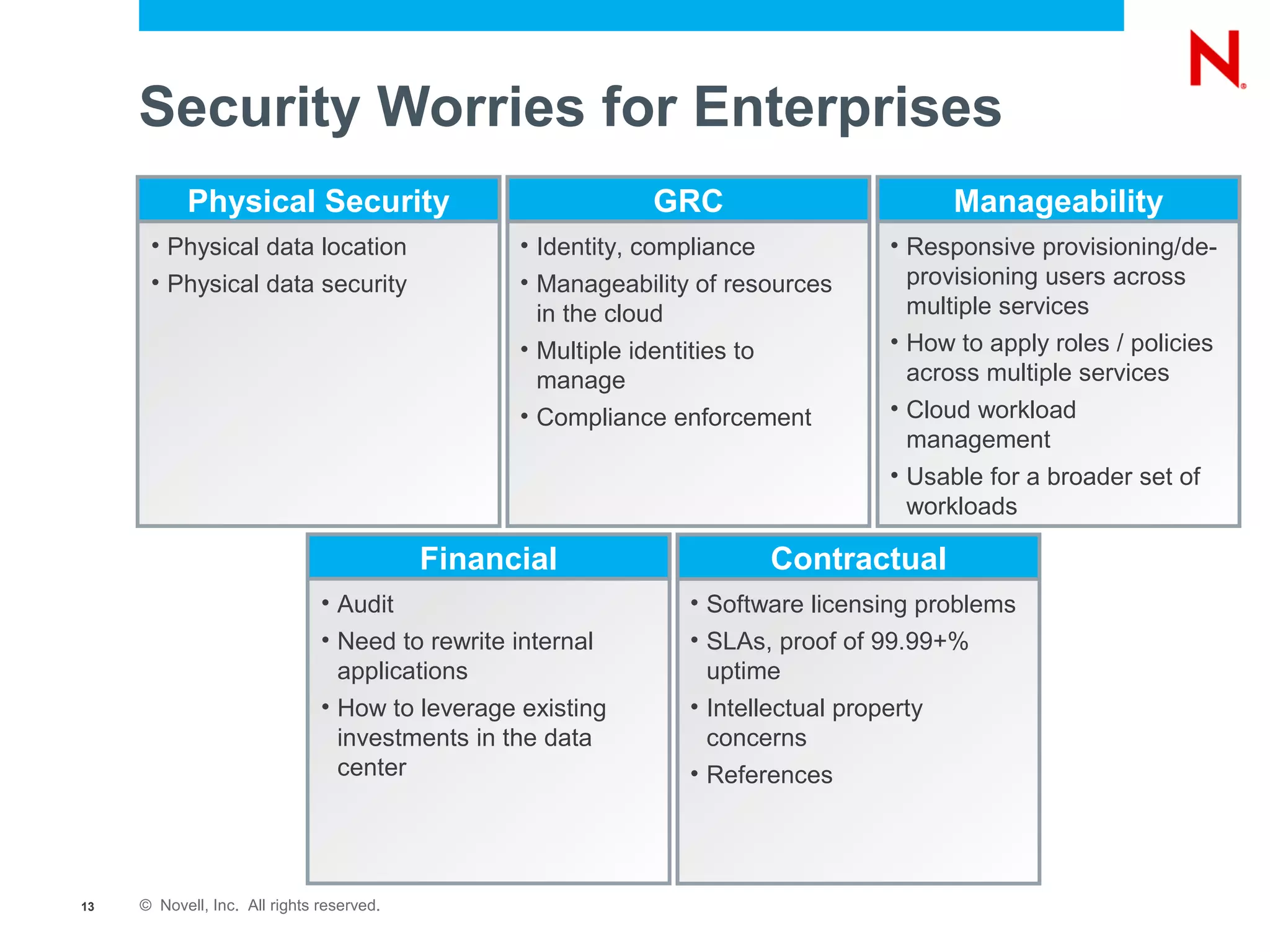
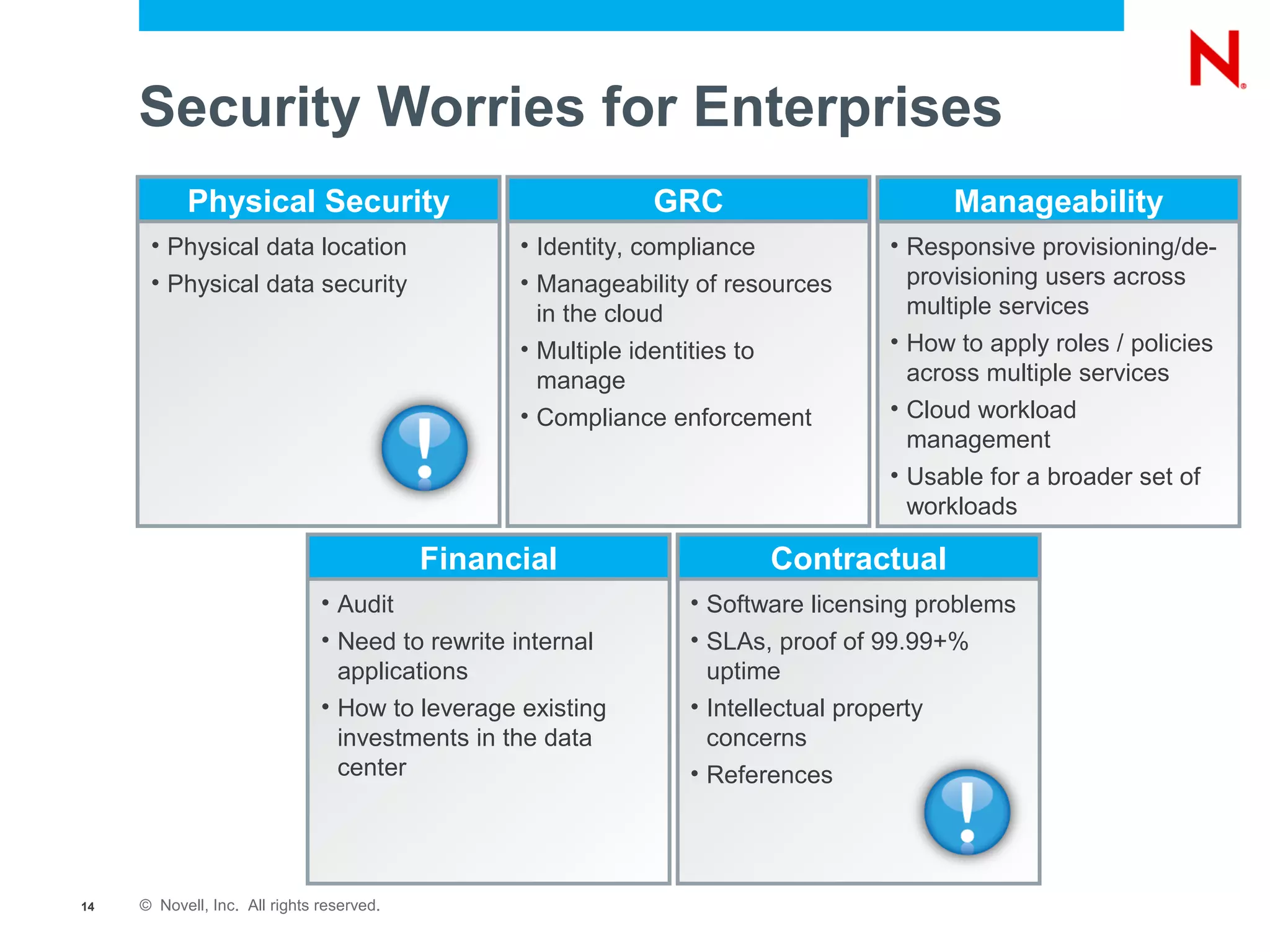
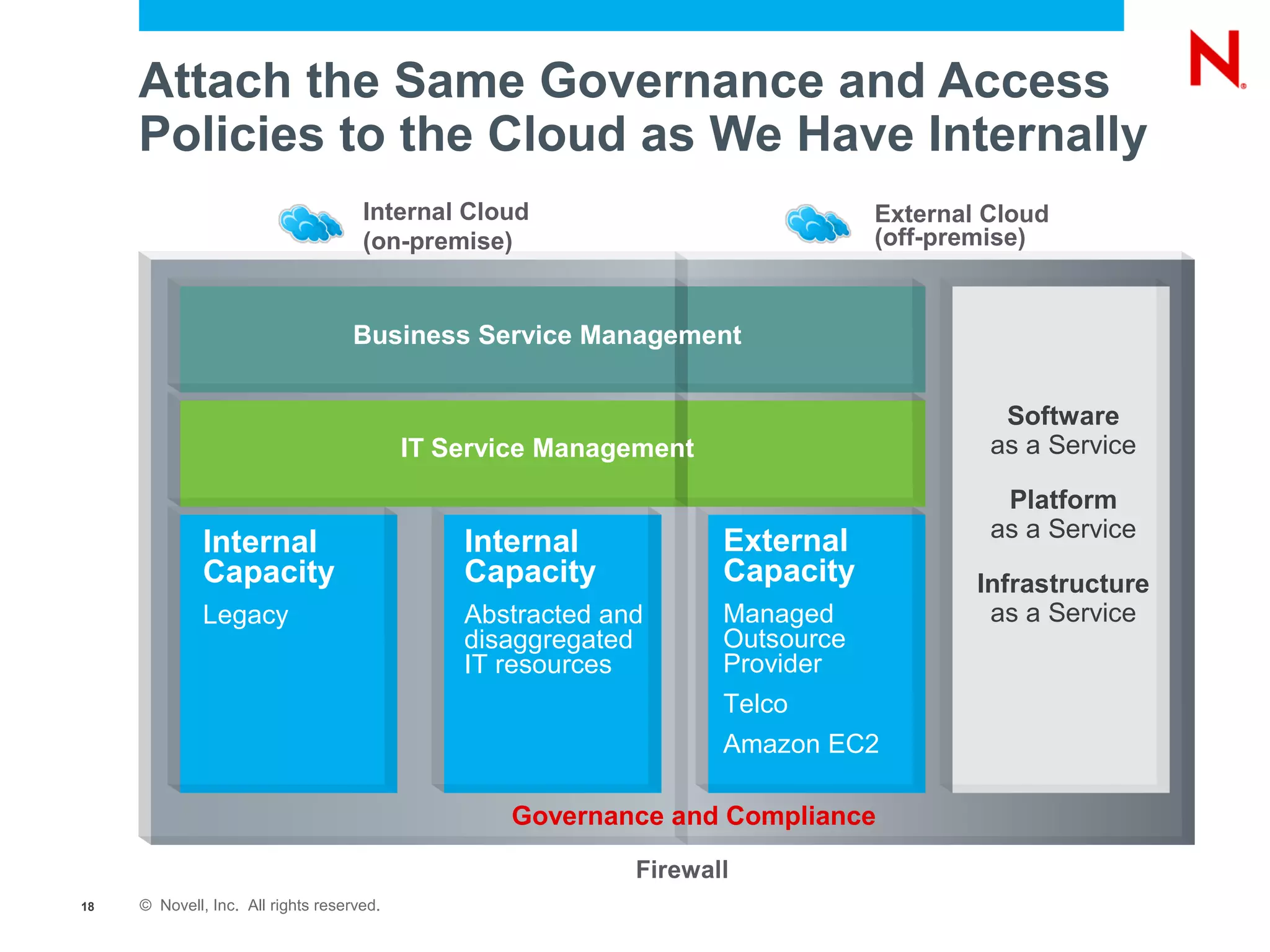
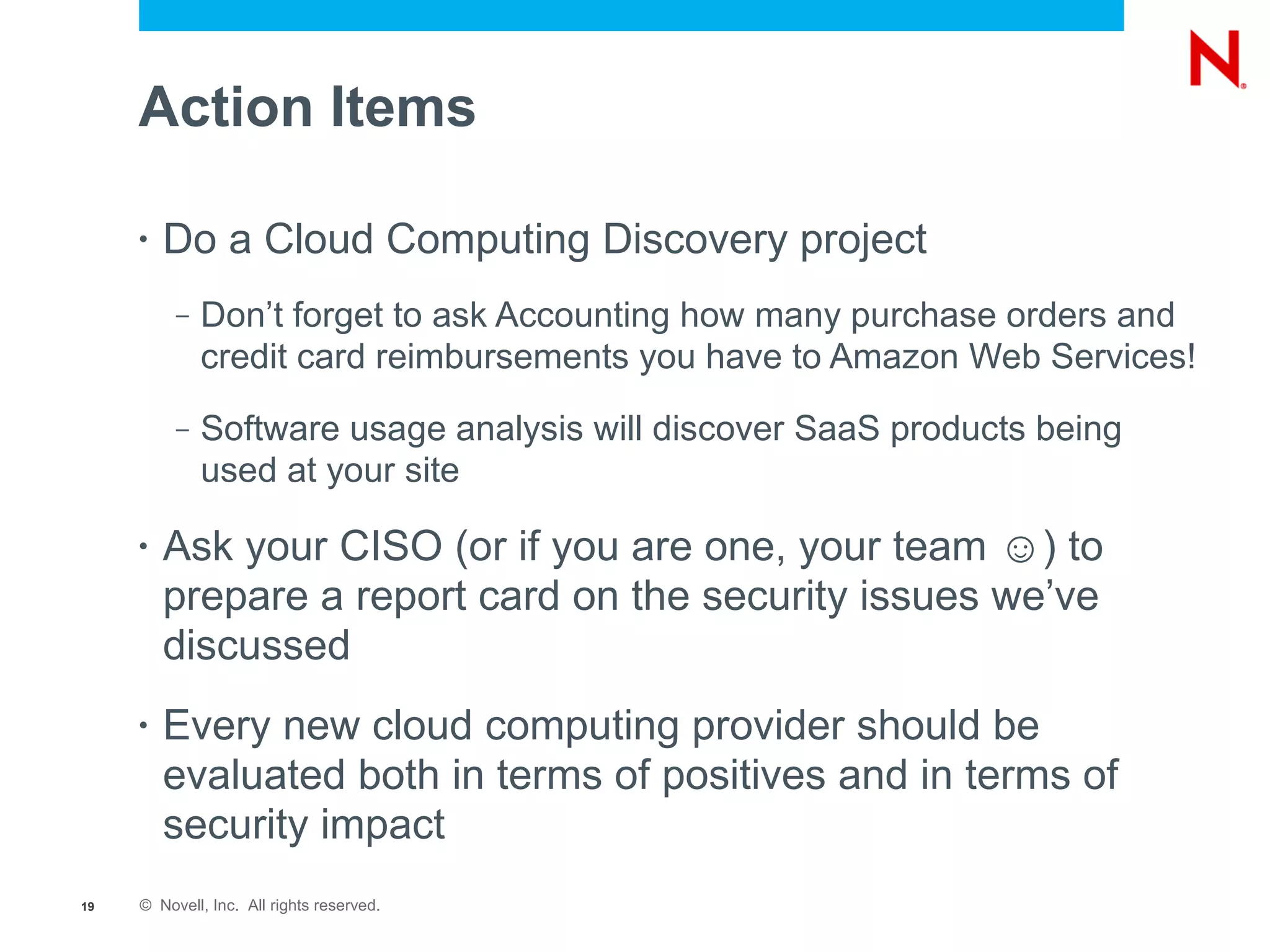
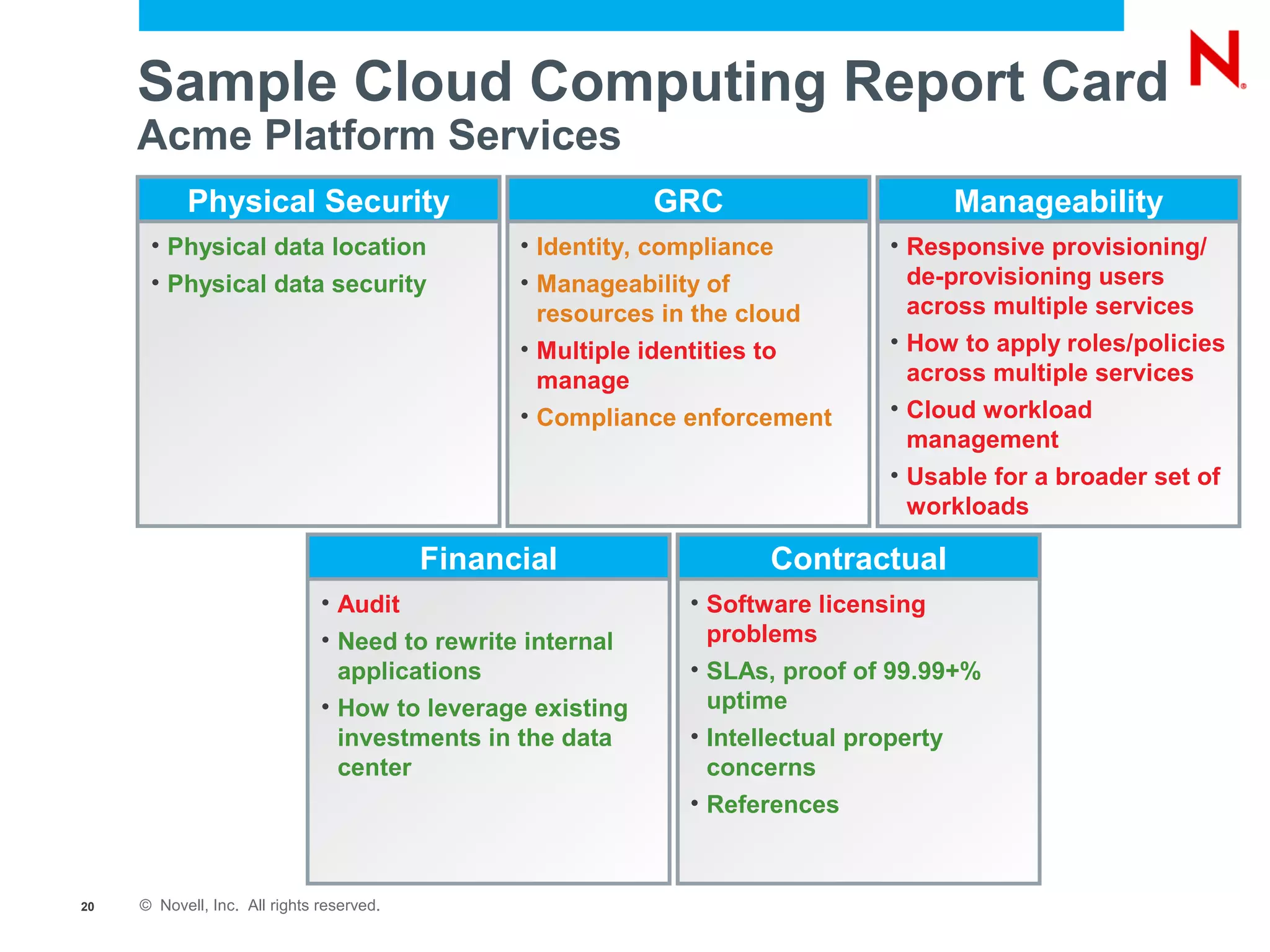
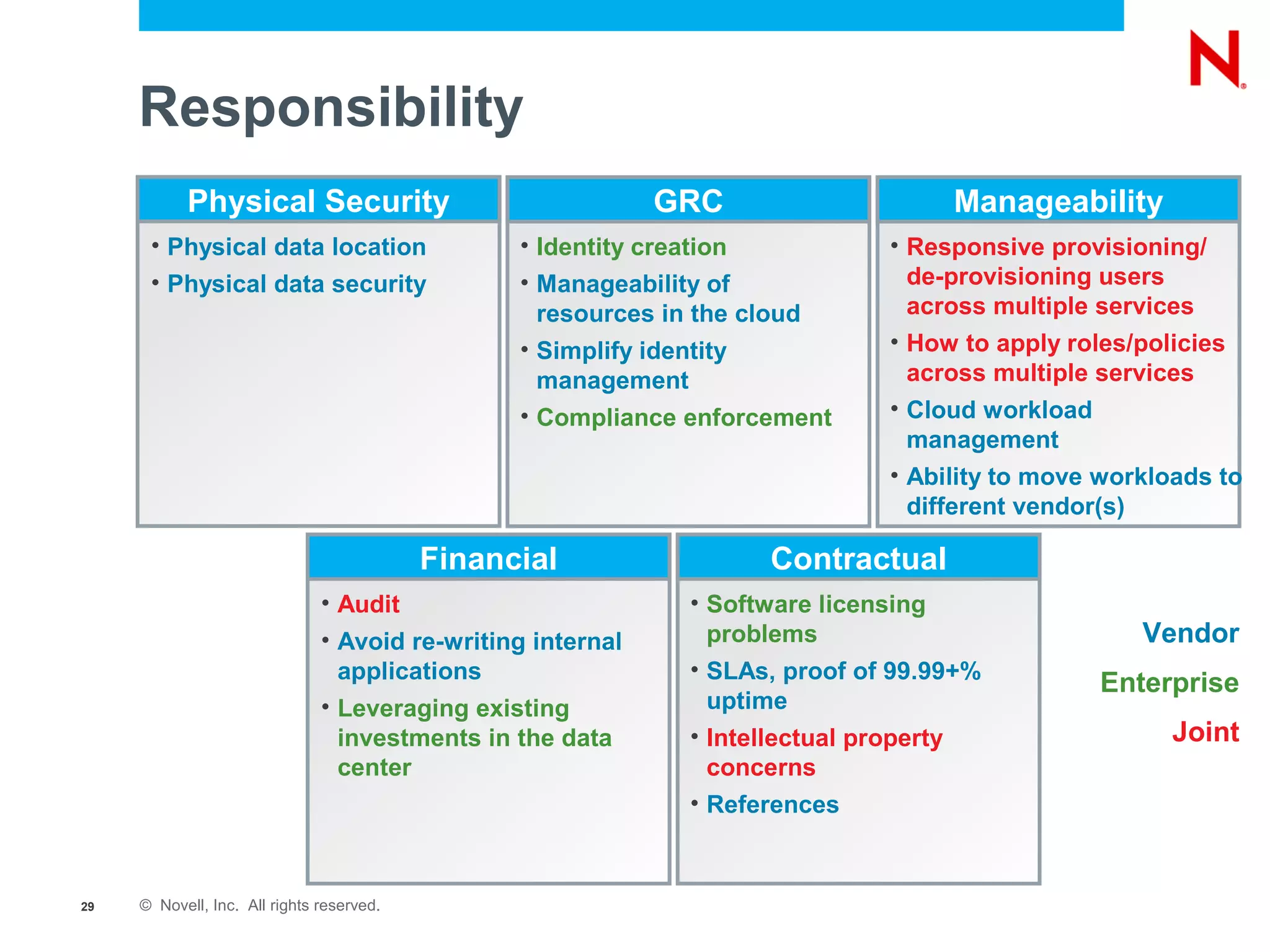
The document discusses the significance of cloud computing for enterprises, highlighting its potential for cost savings and increased flexibility amidst widespread skepticism regarding security and trust in cloud solutions. It identifies major user sectors, emphasizes the necessity for security governance, and outlines key risks and challenges associated with cloud adoption, particularly in handling sensitive data and regulatory compliance. Recommendations for evaluating cloud providers and addressing security concerns are also provided to ensure businesses effectively manage their cloud computing strategies.