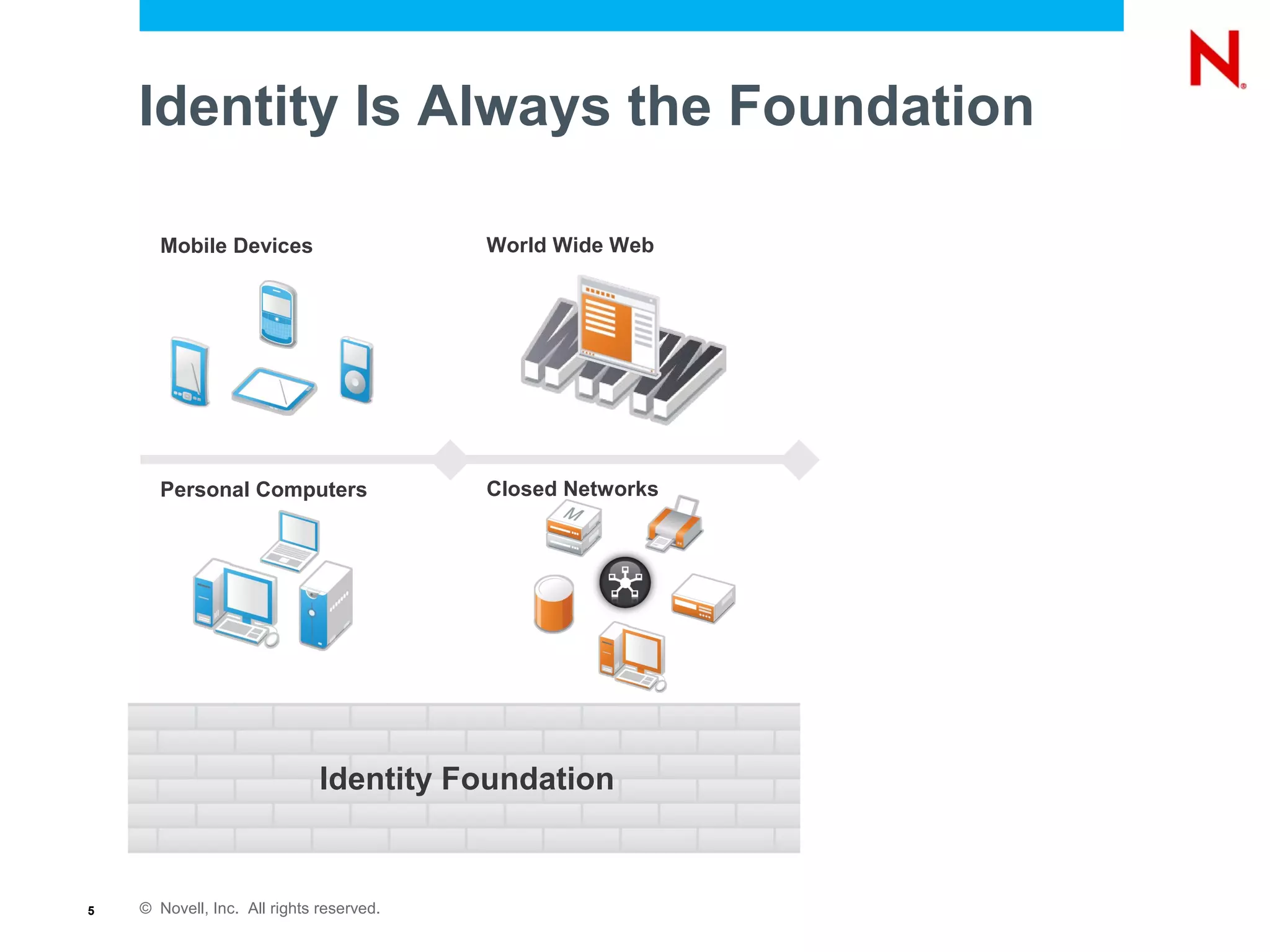
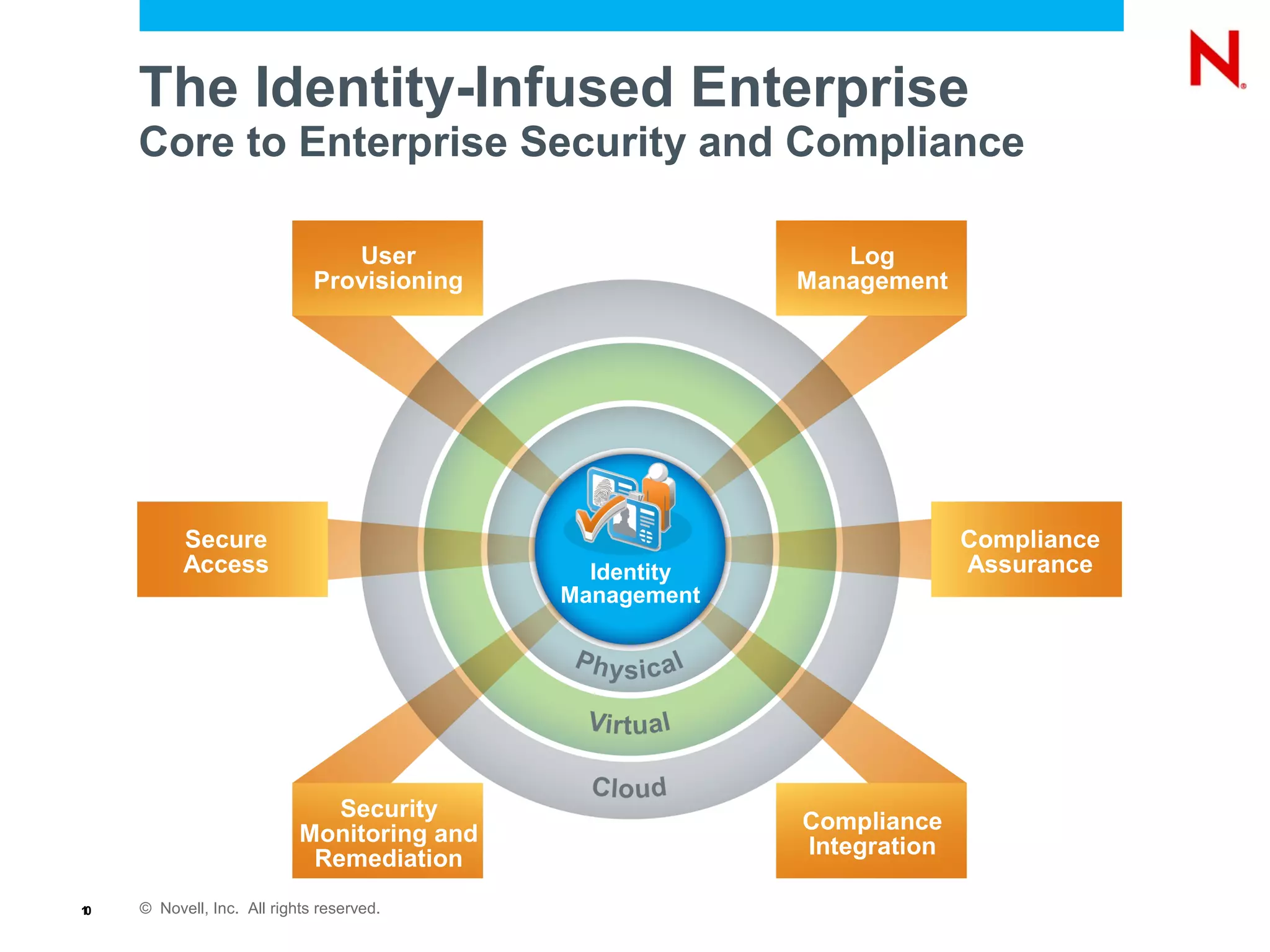
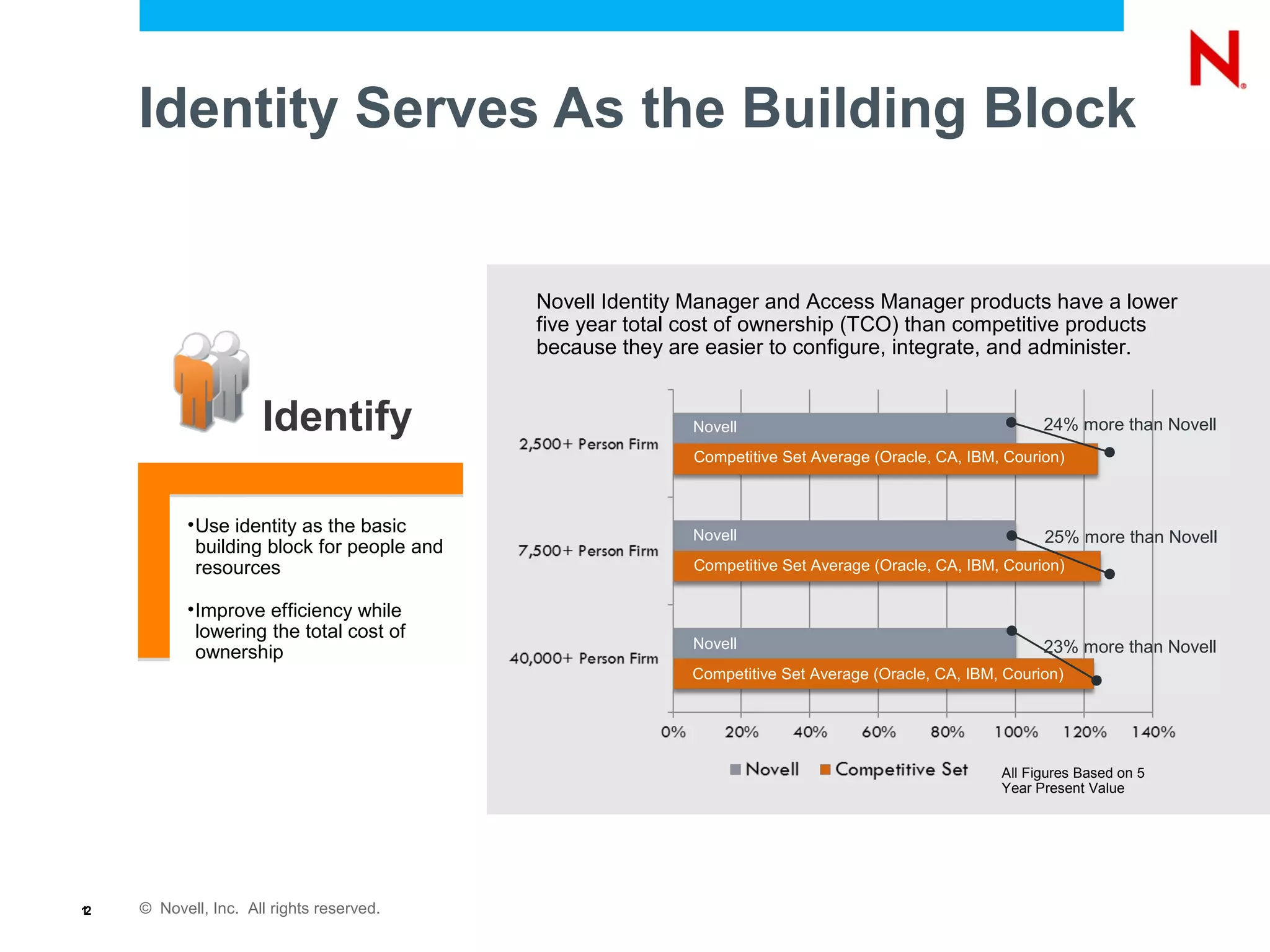
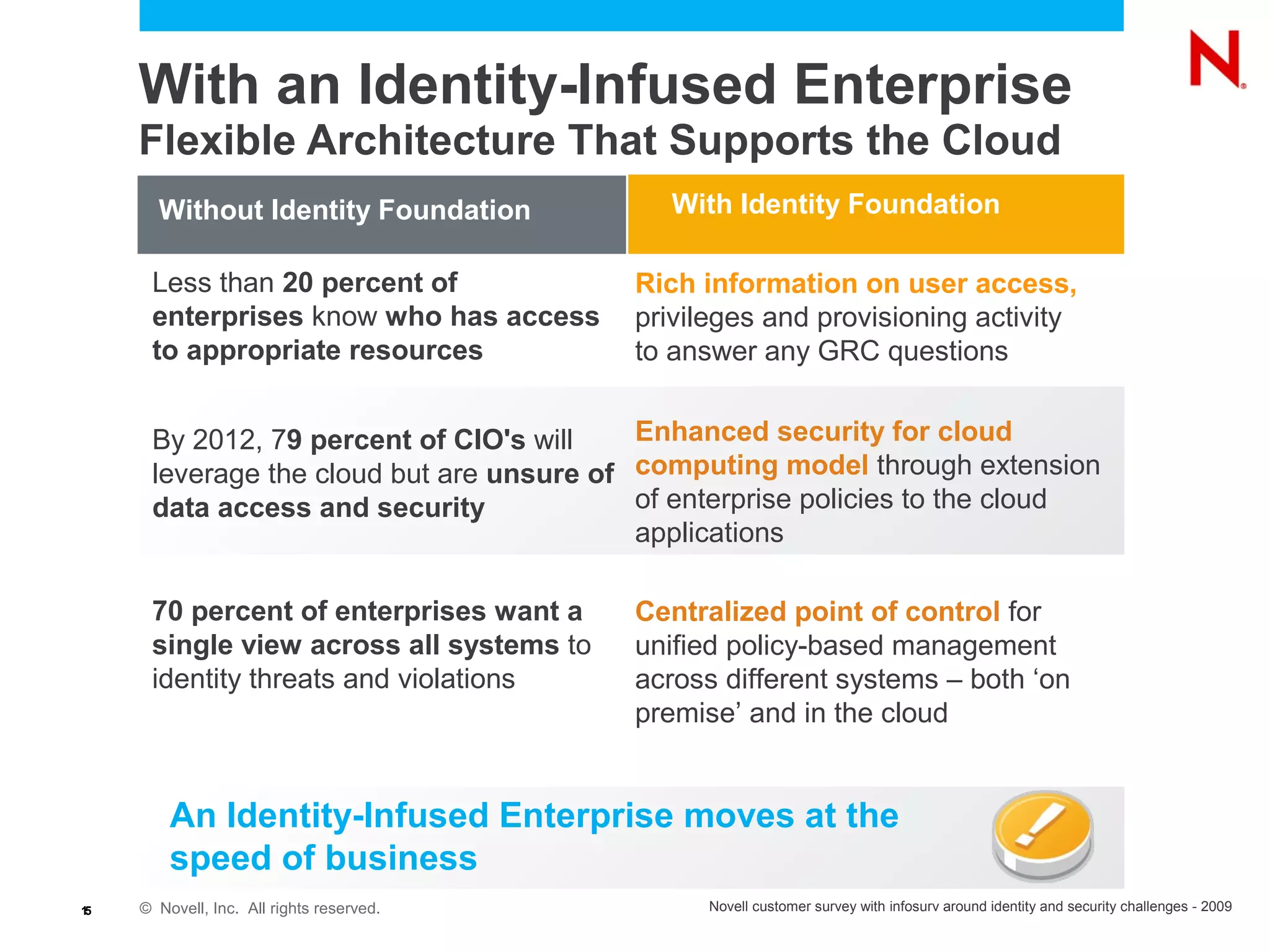
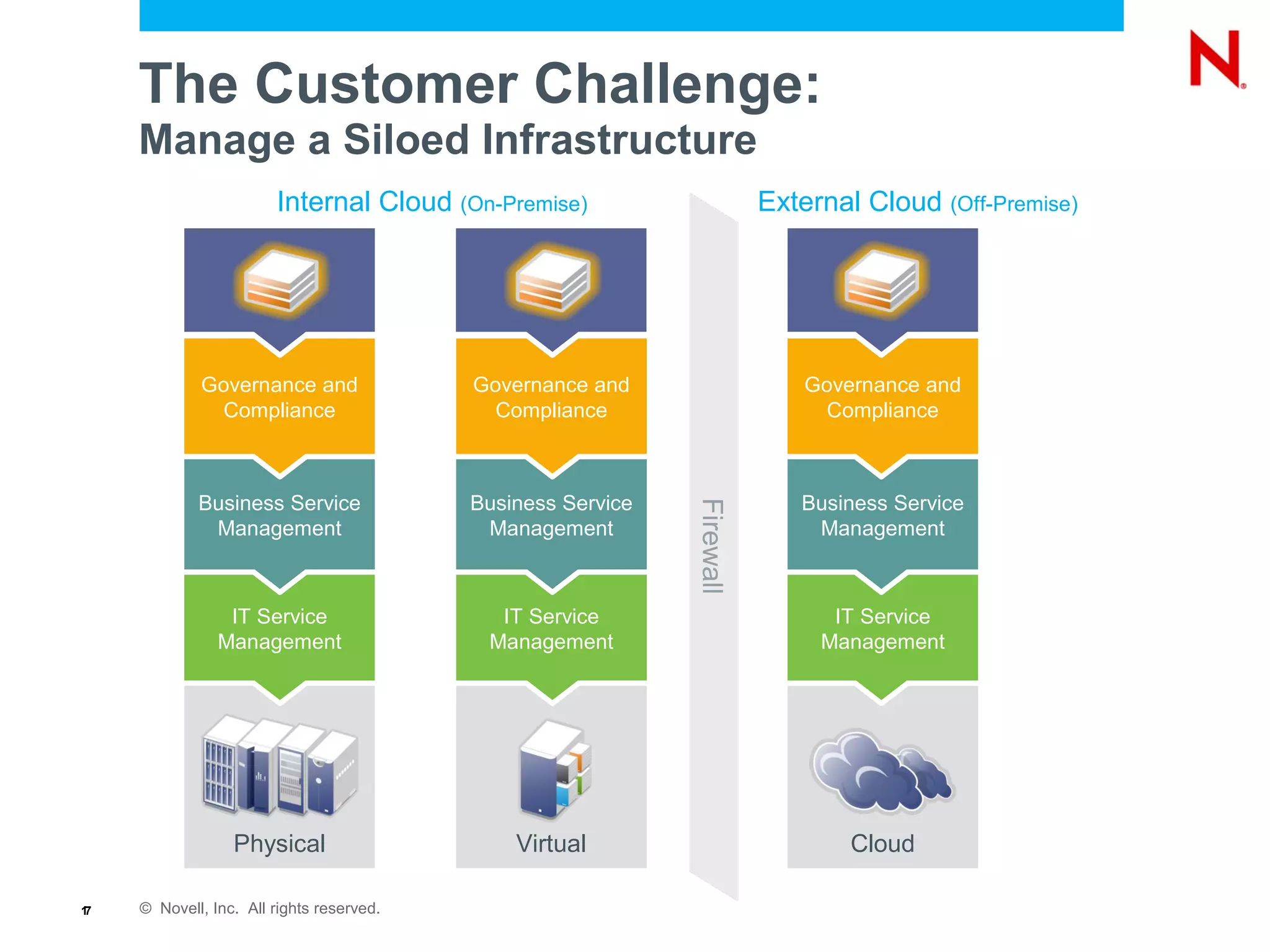
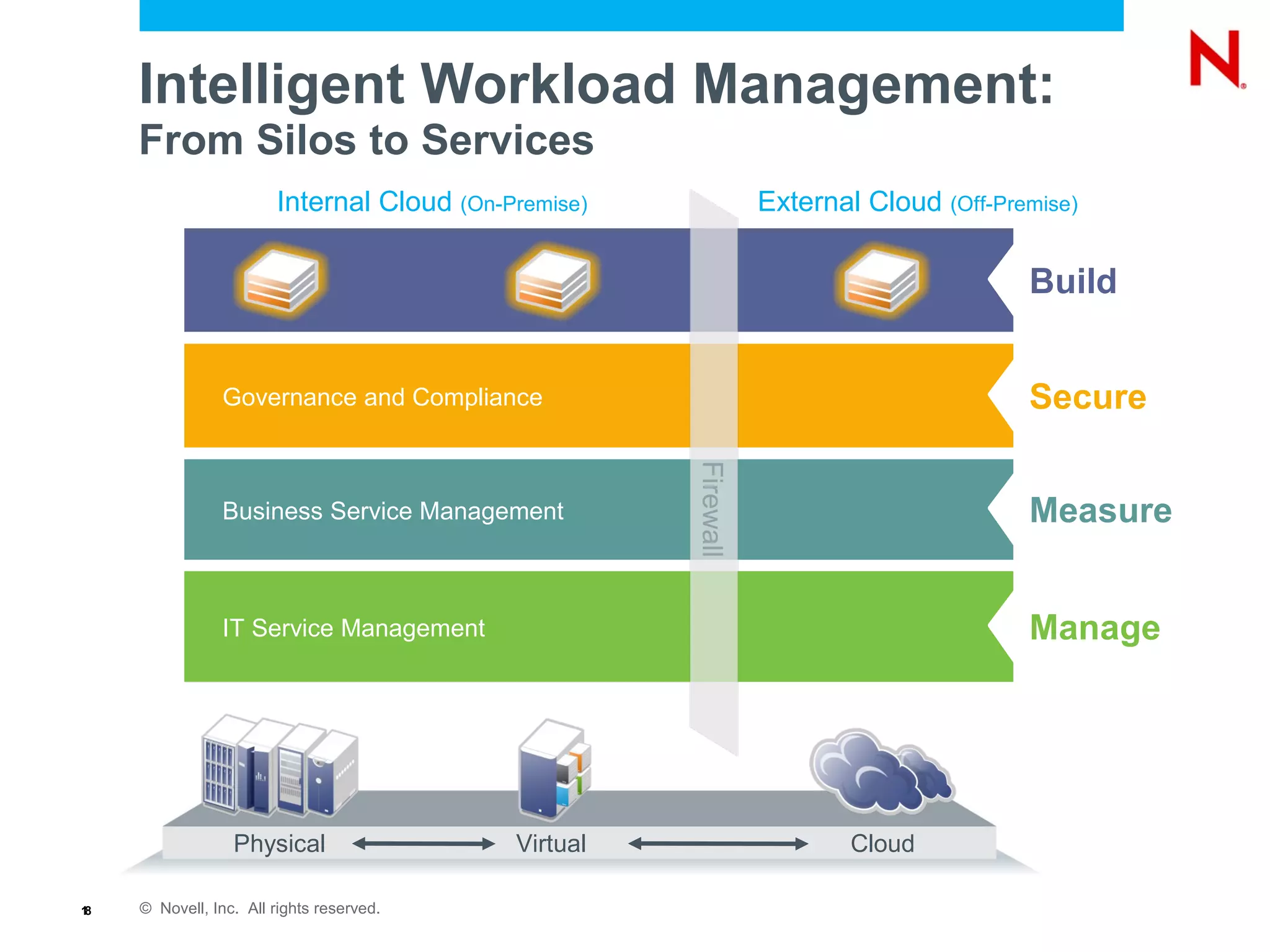
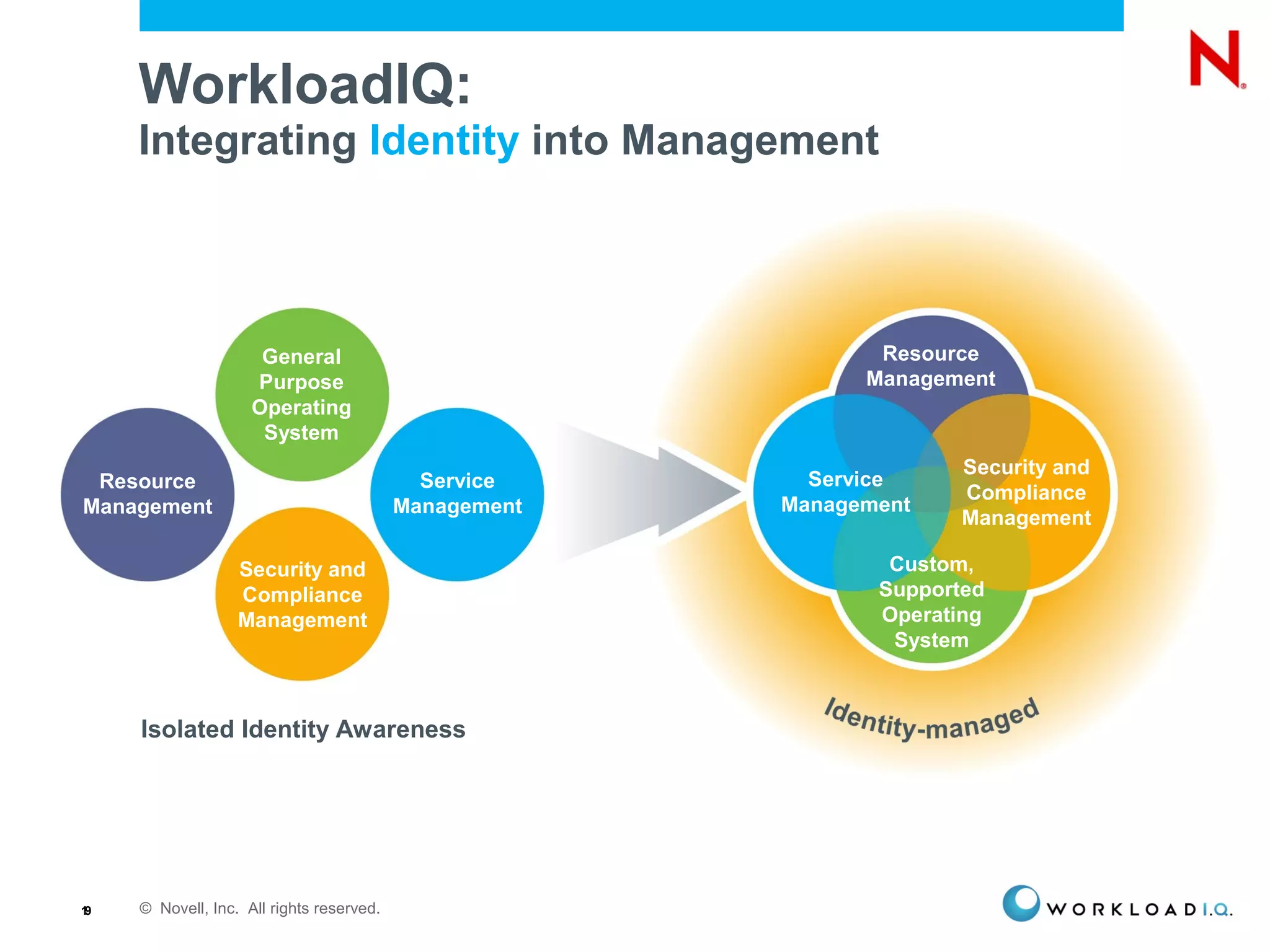
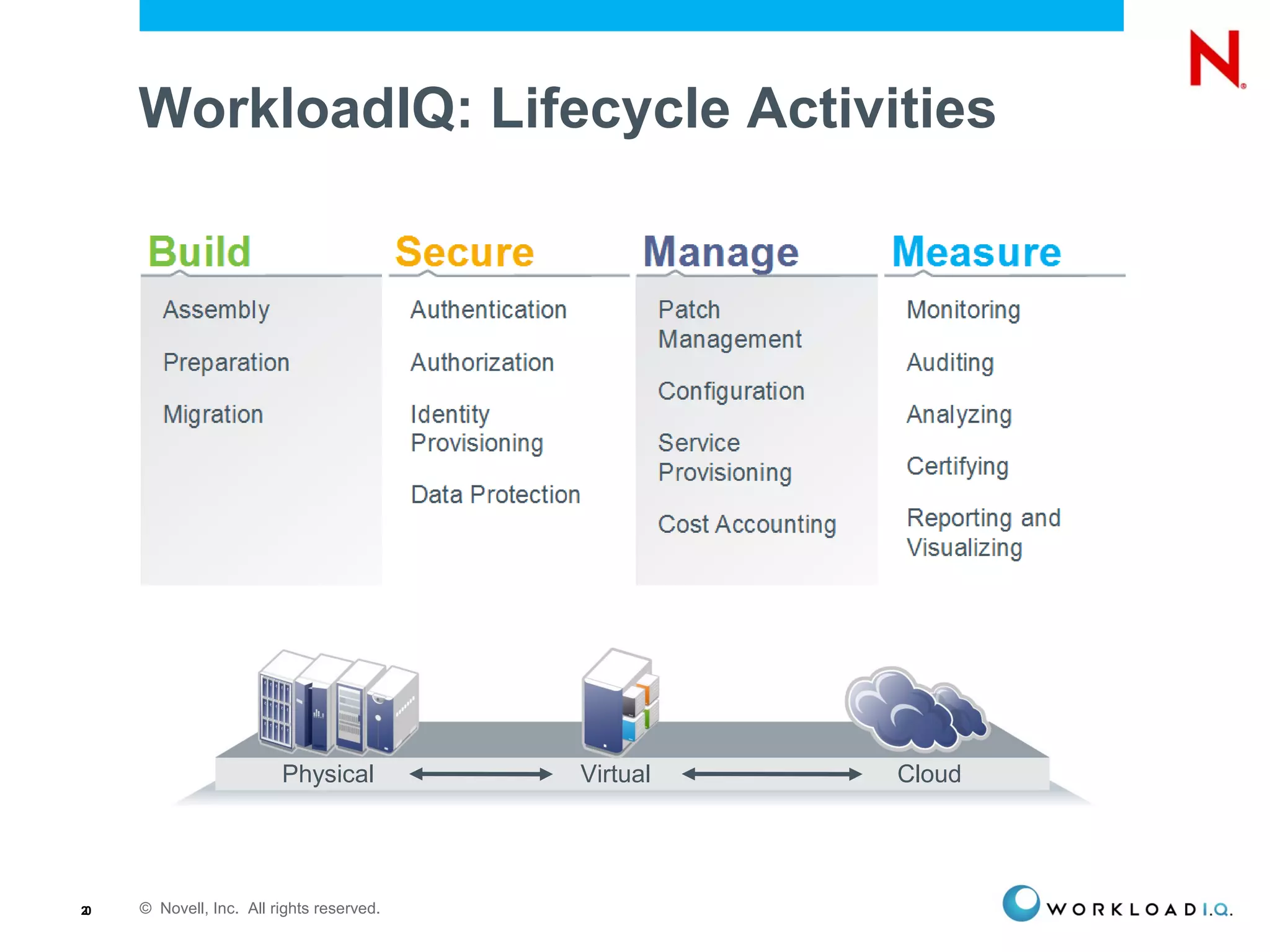
The document discusses the importance of identity management in modern computing environments. It argues that identity should serve as the foundation for securing access across devices, applications, and cloud-based services. With identity as the core, enterprises can better balance flexibility, compliance, and security when resources are distributed across different systems. The identity-infused enterprise model allows organizations to leverage existing identity investments to enhance control, visibility, and compliance across hybrid computing environments.