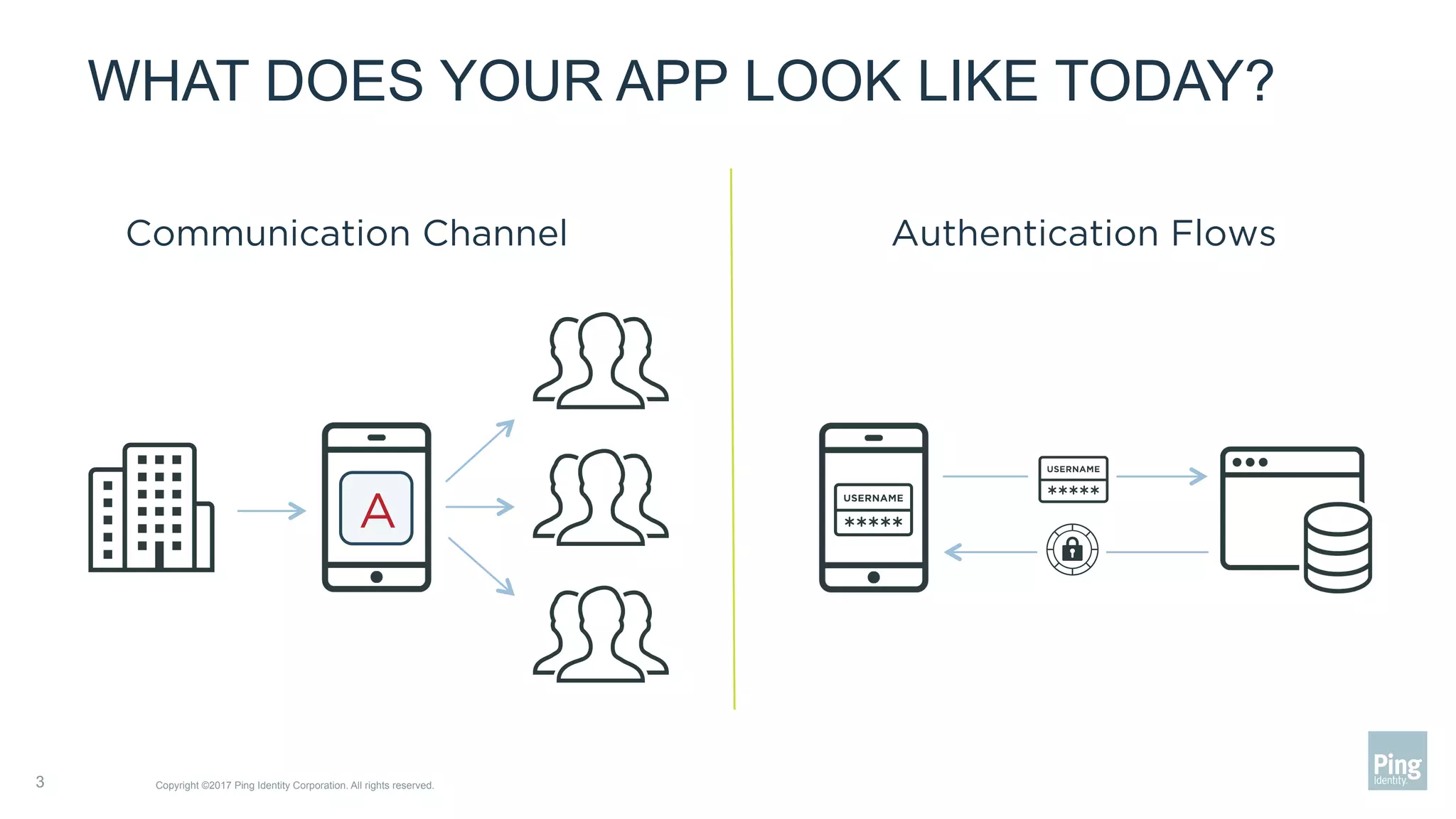
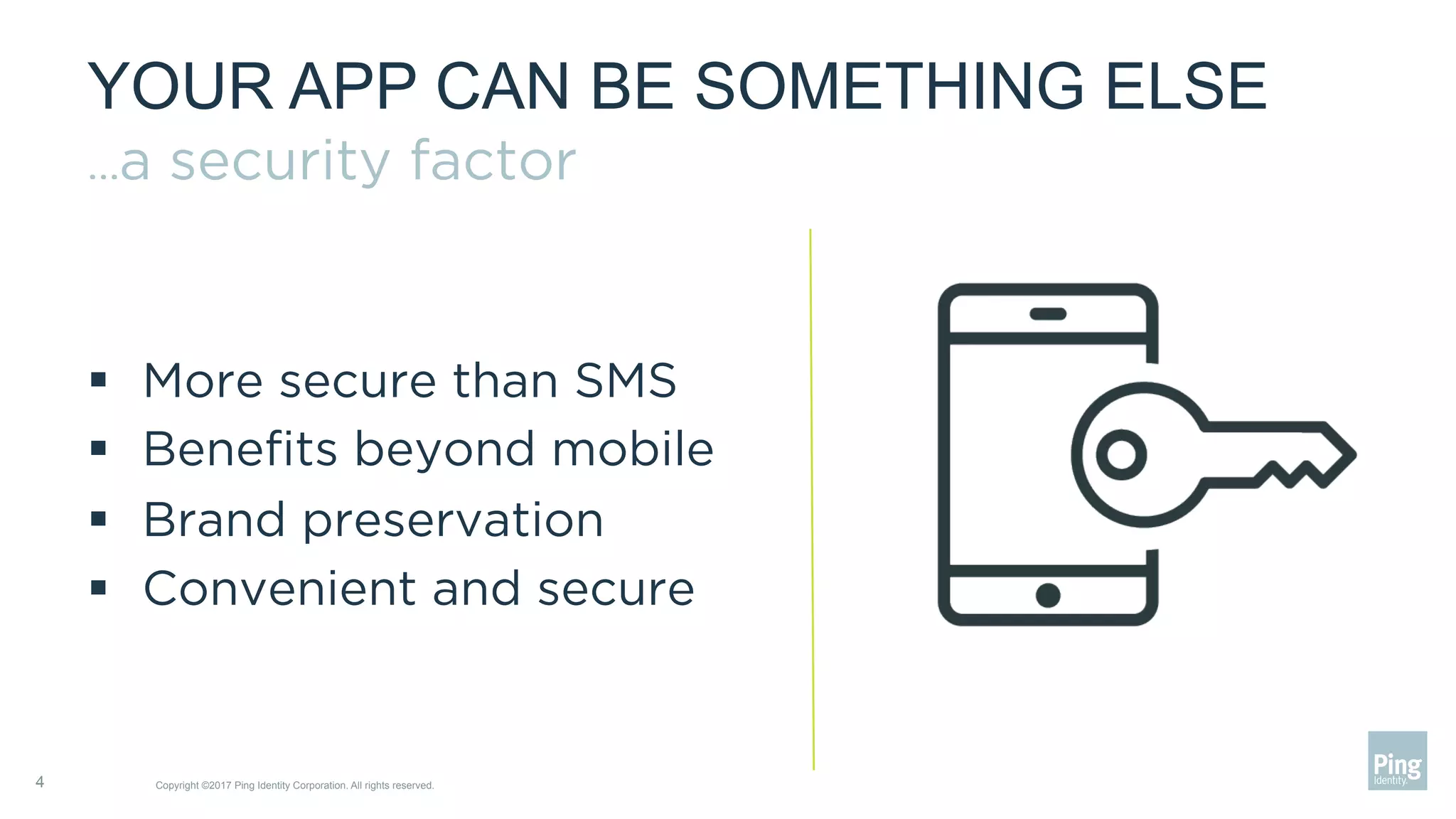
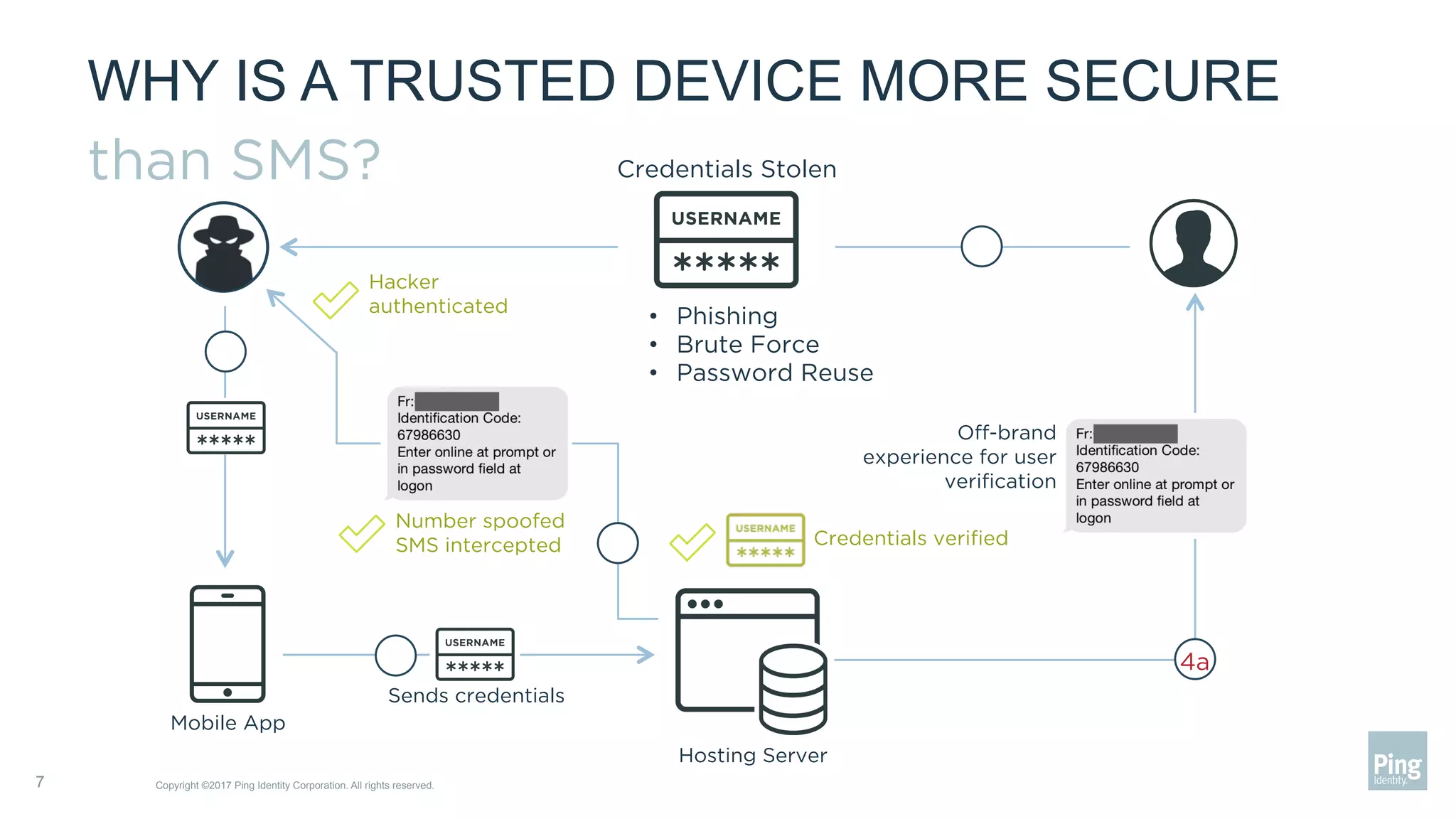
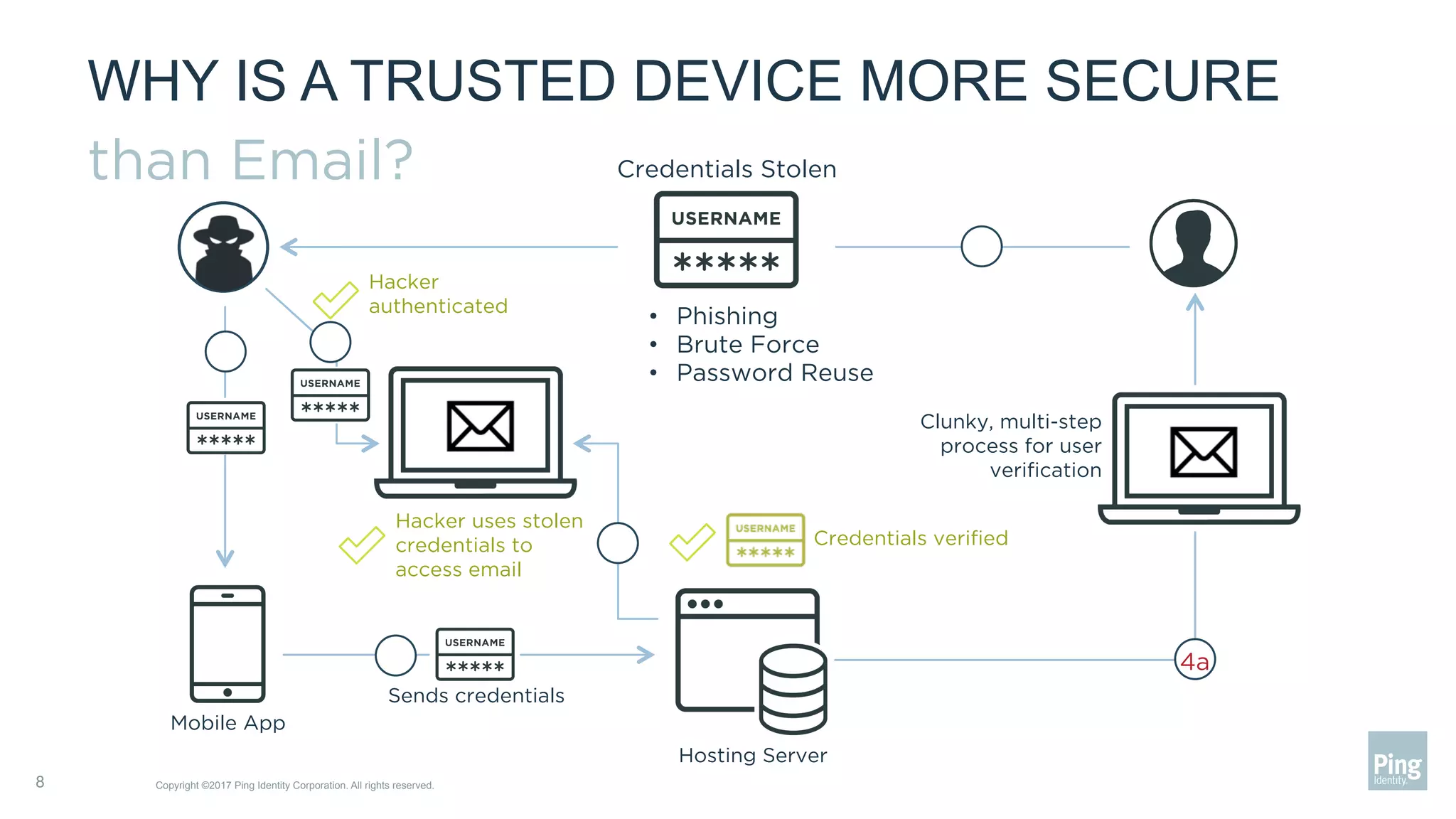
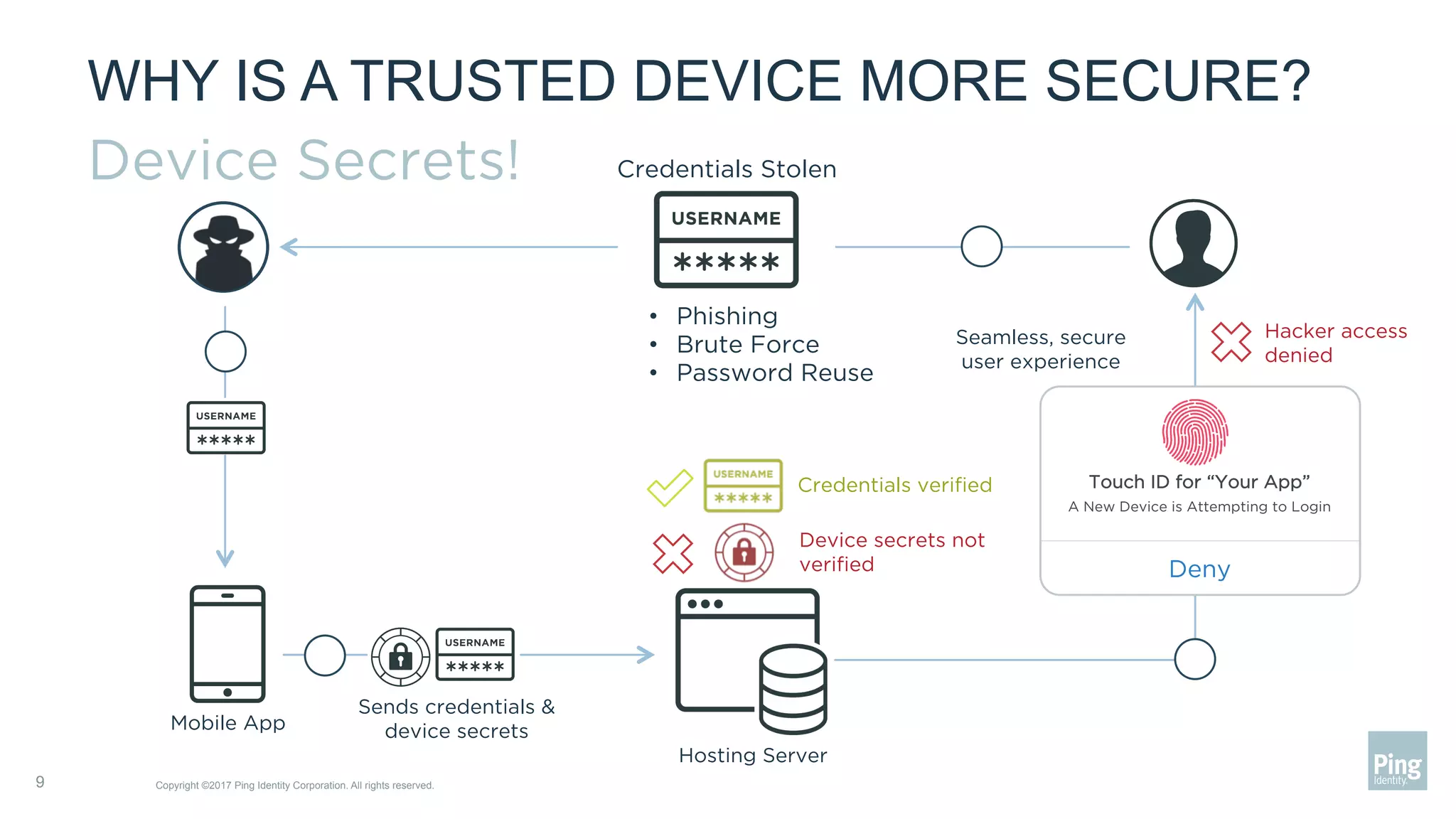
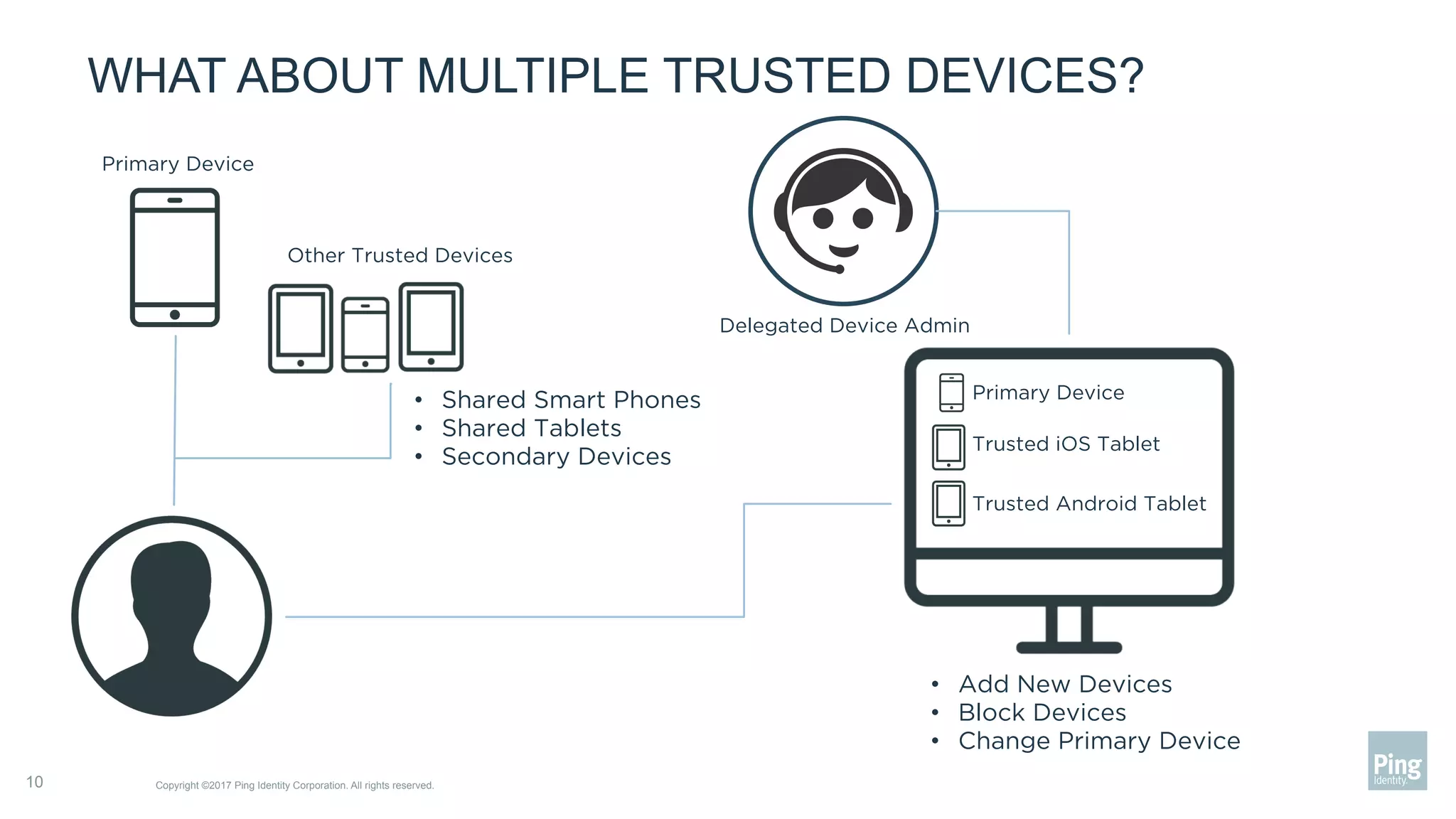
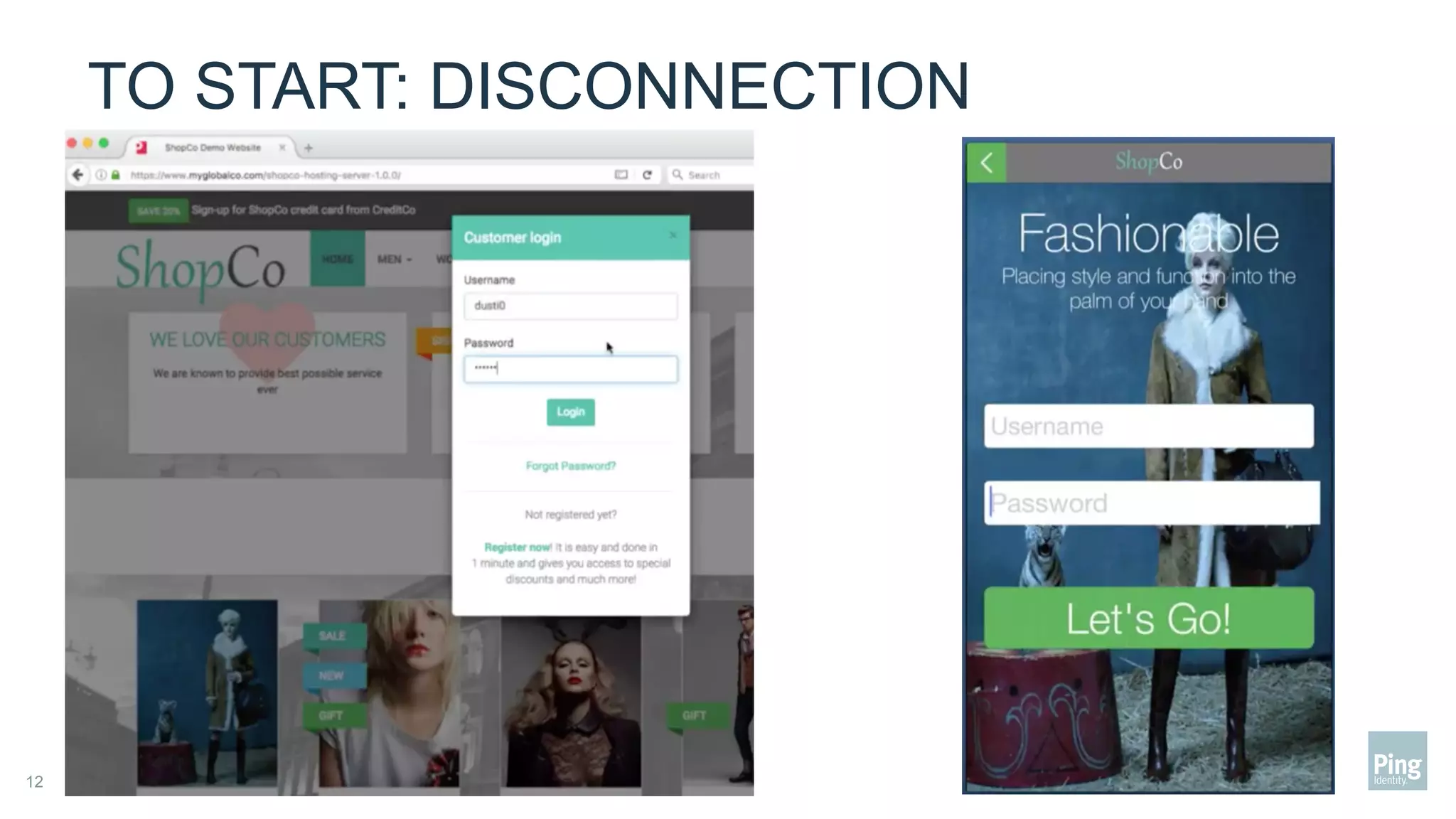
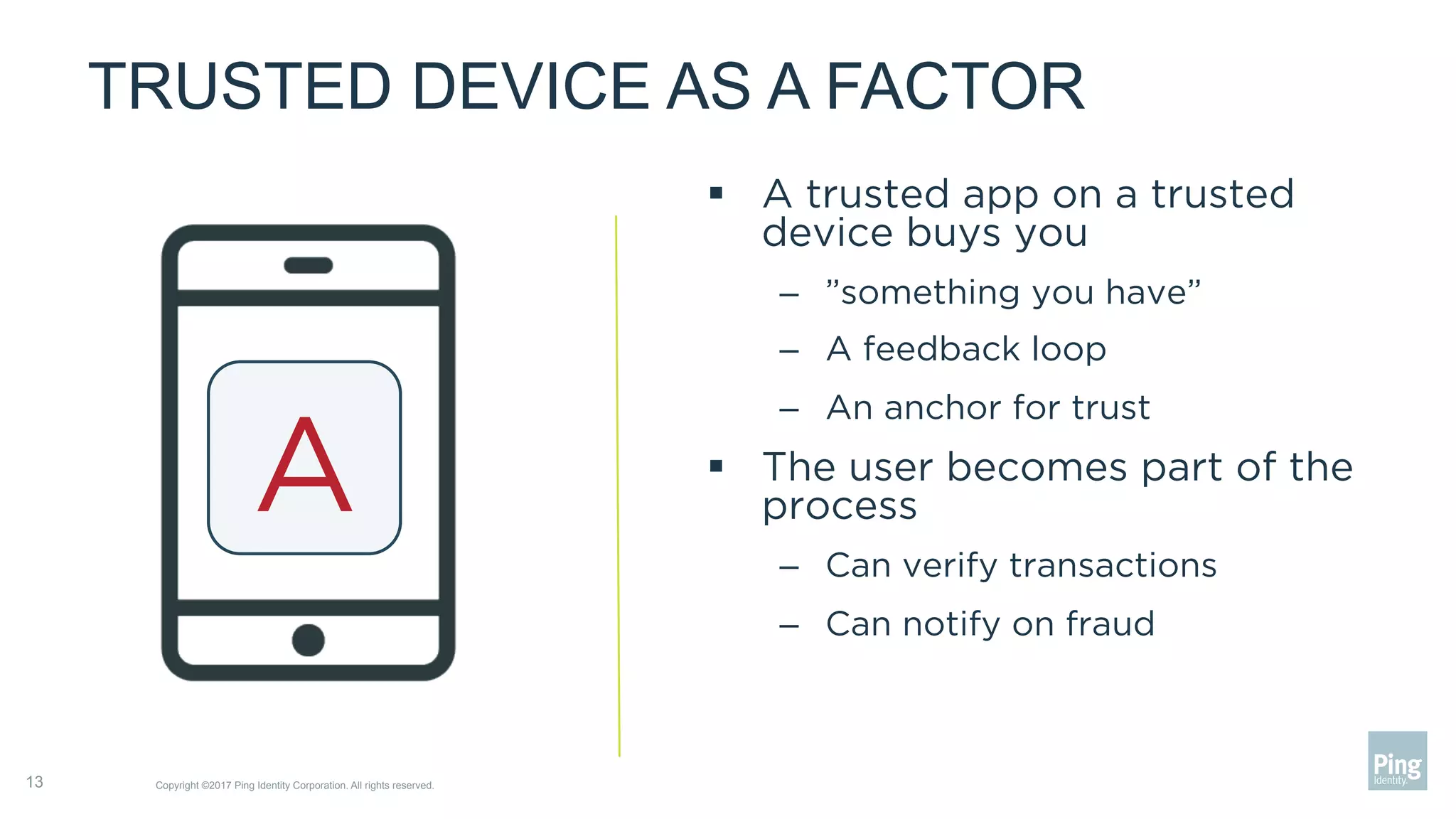
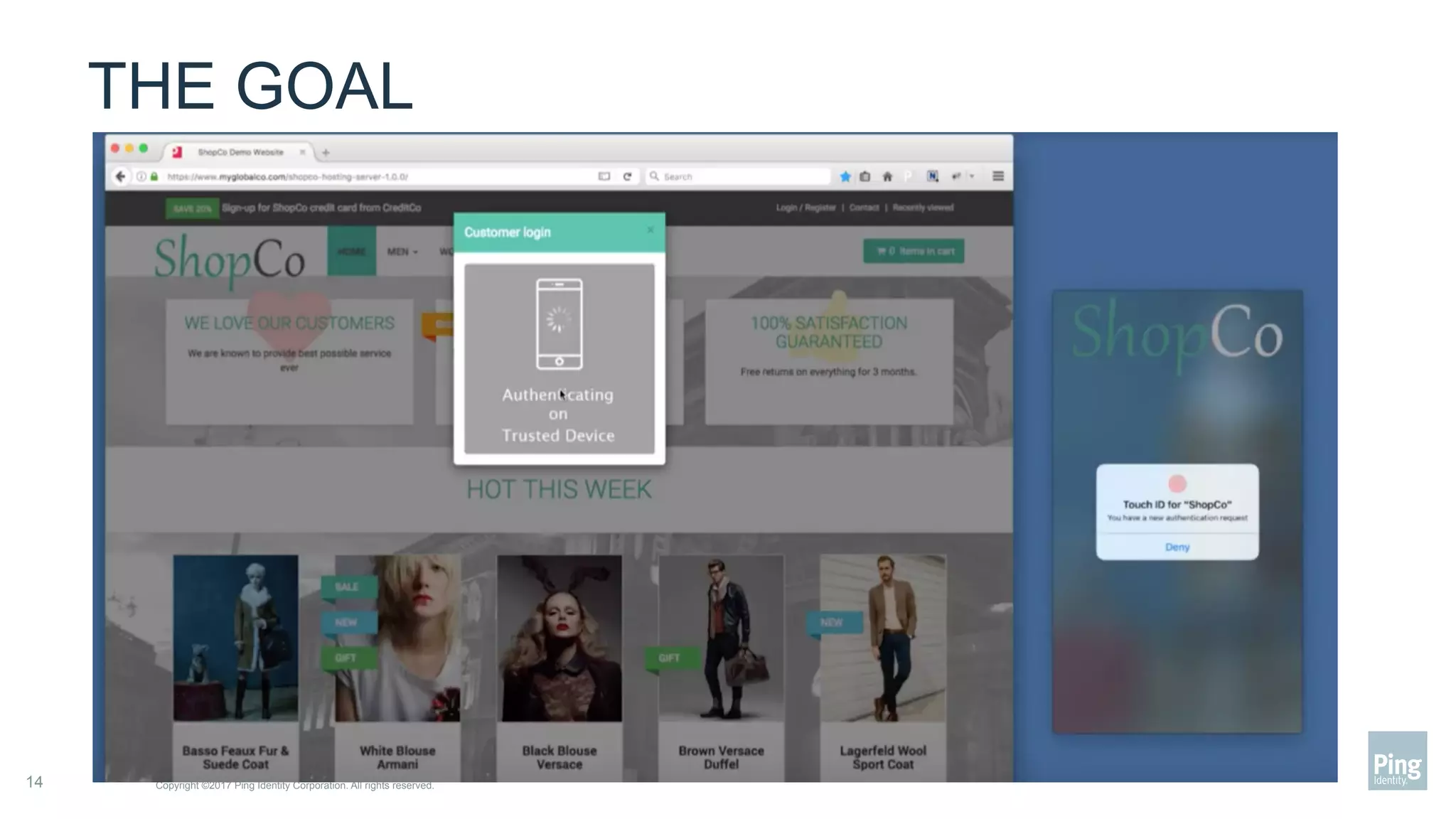
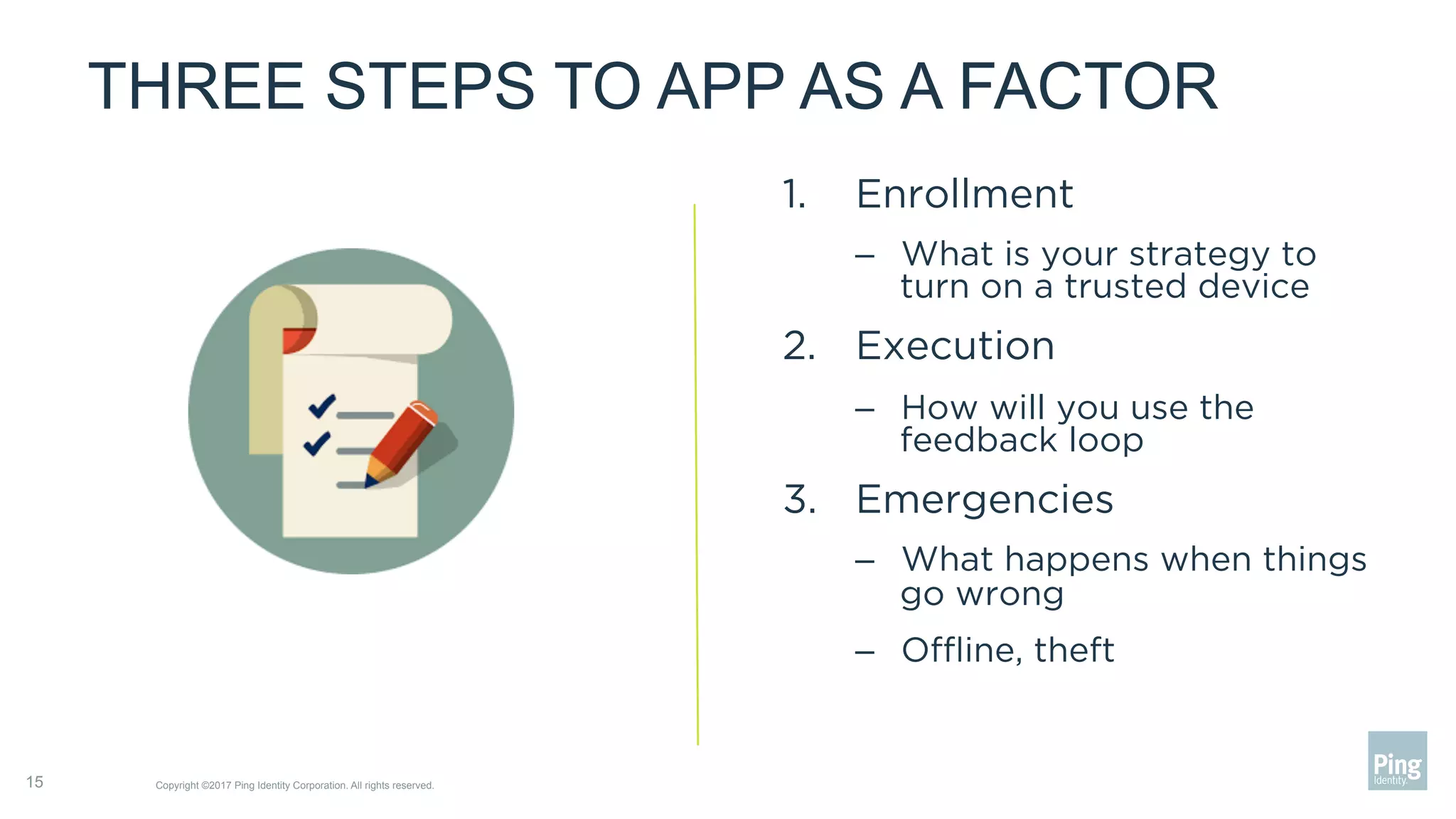
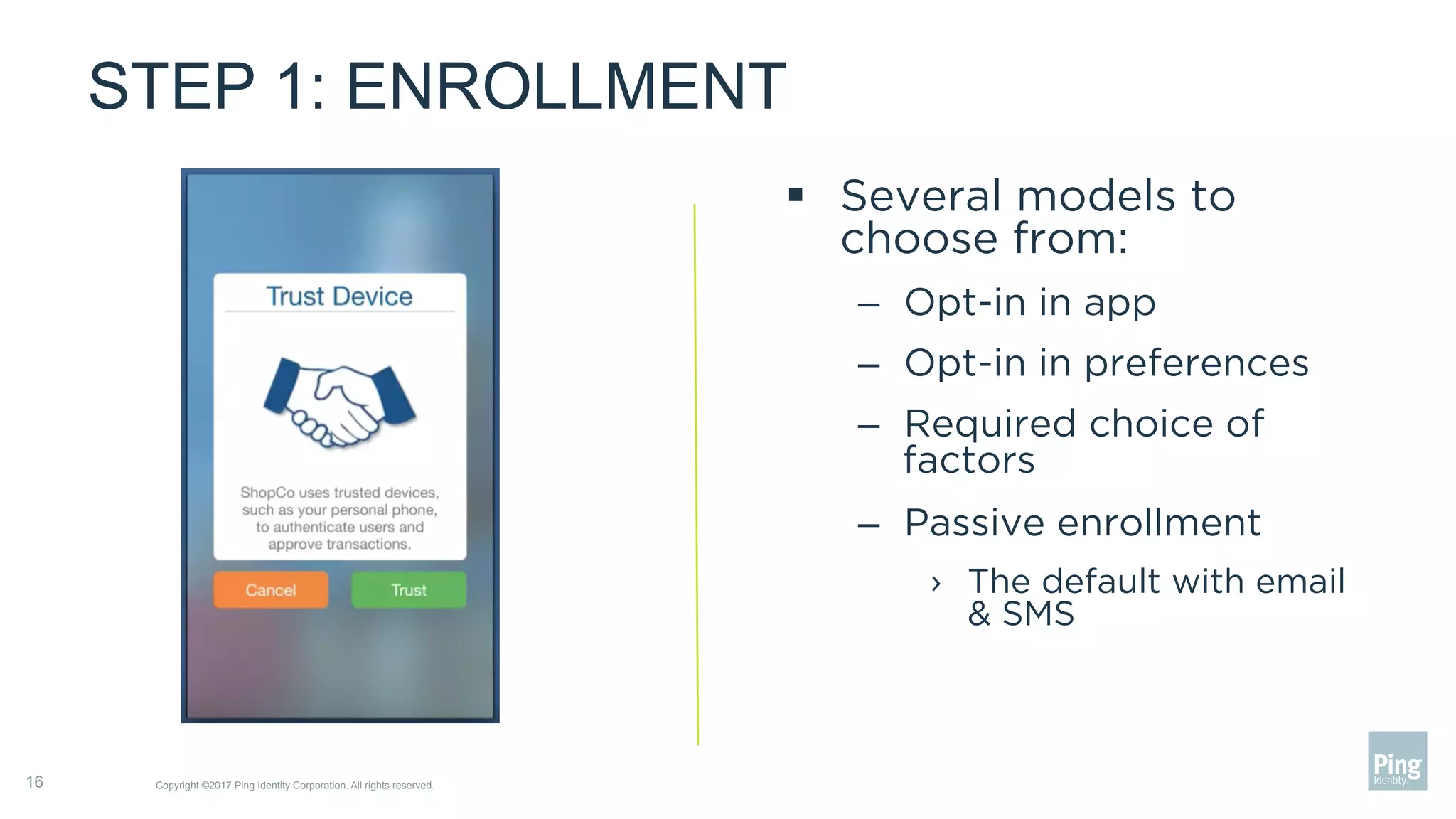
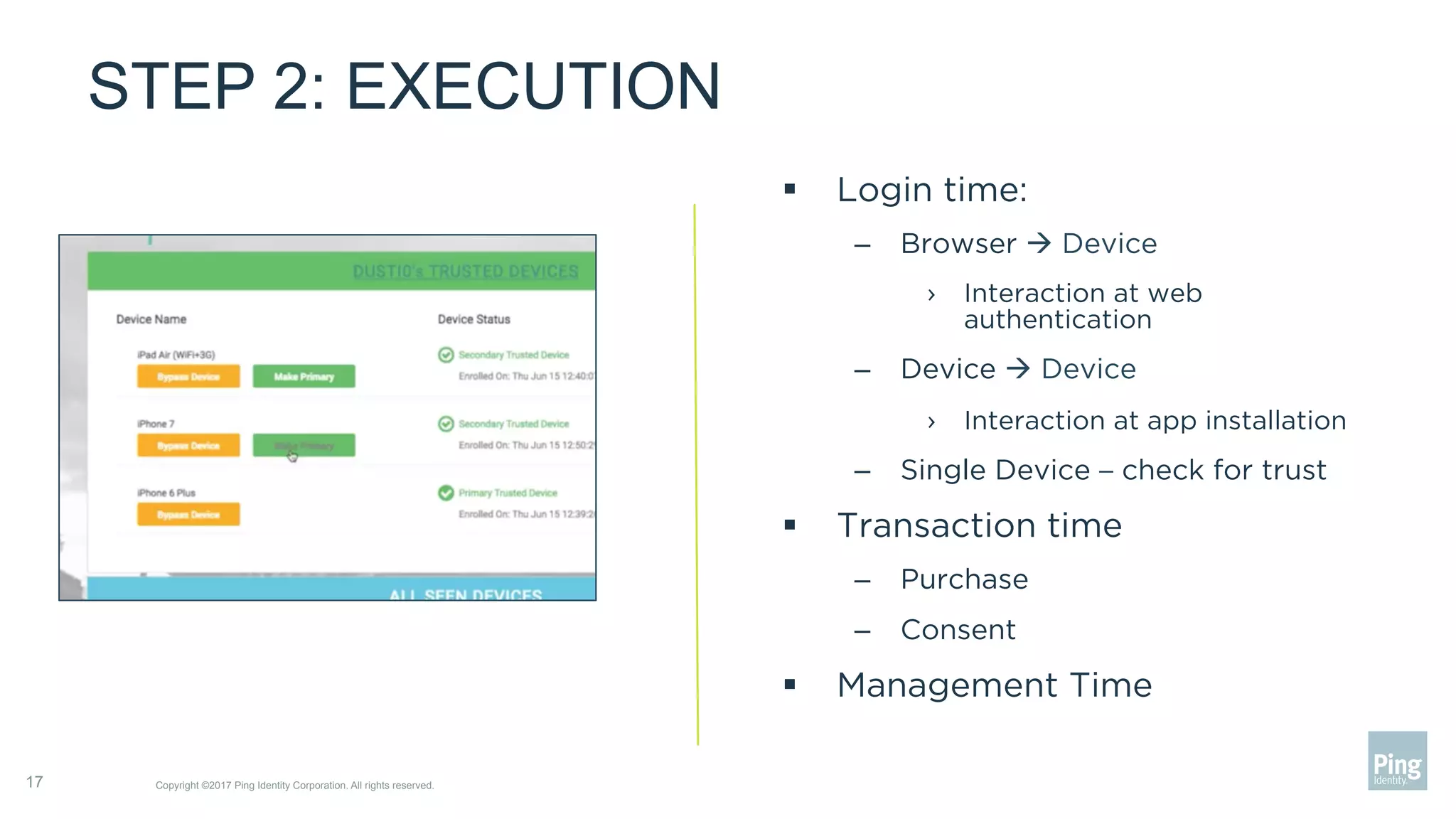
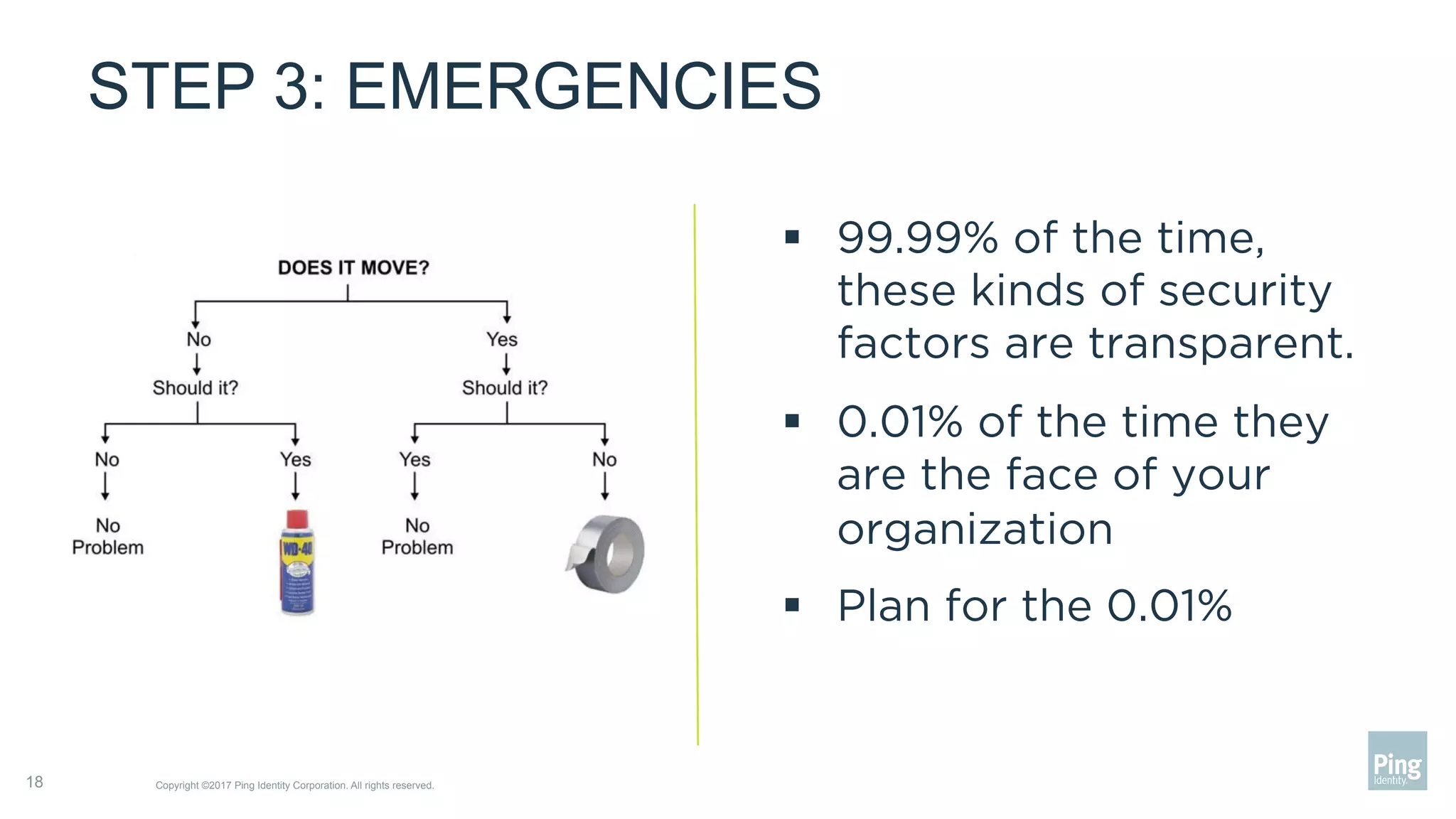
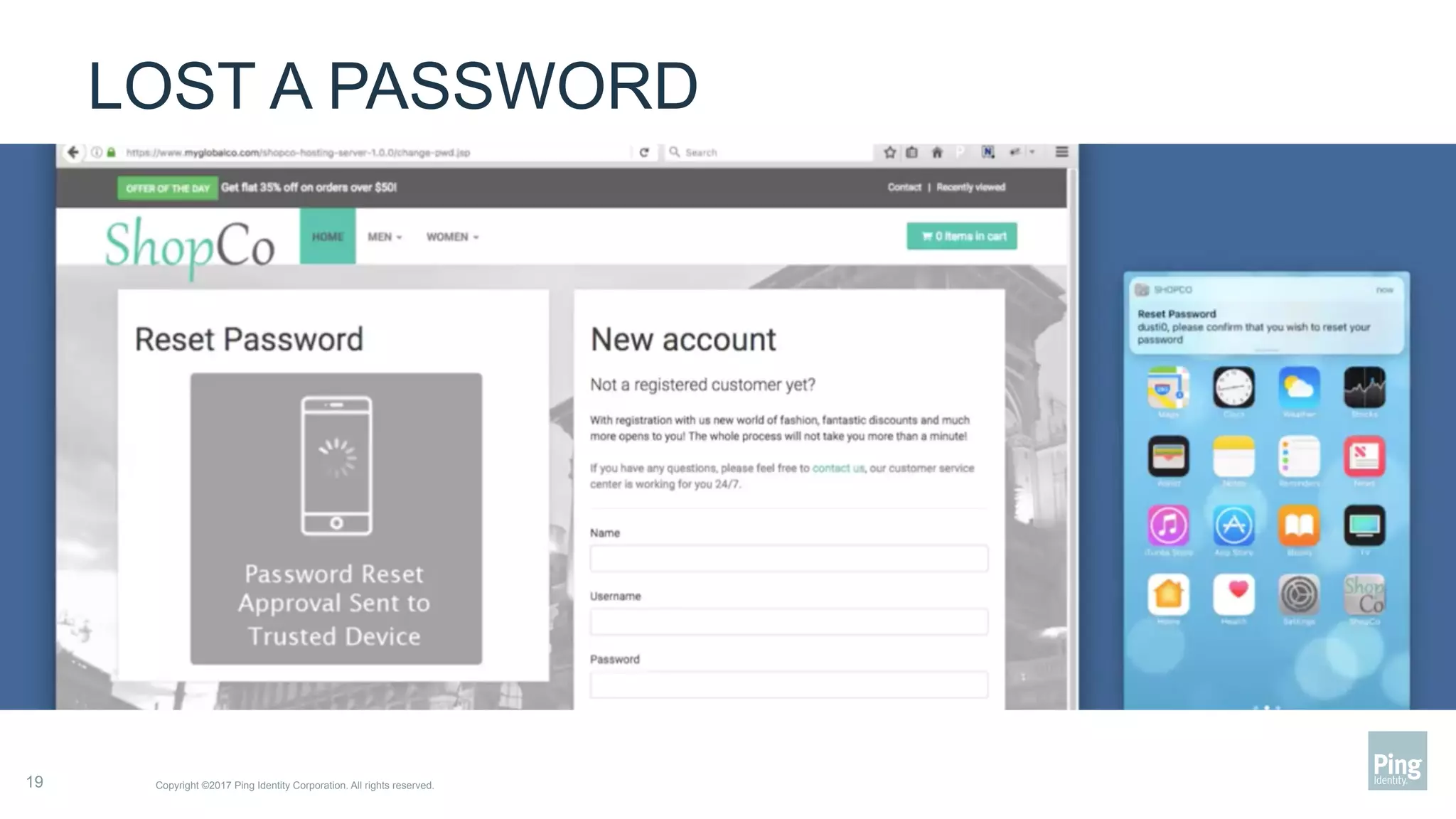
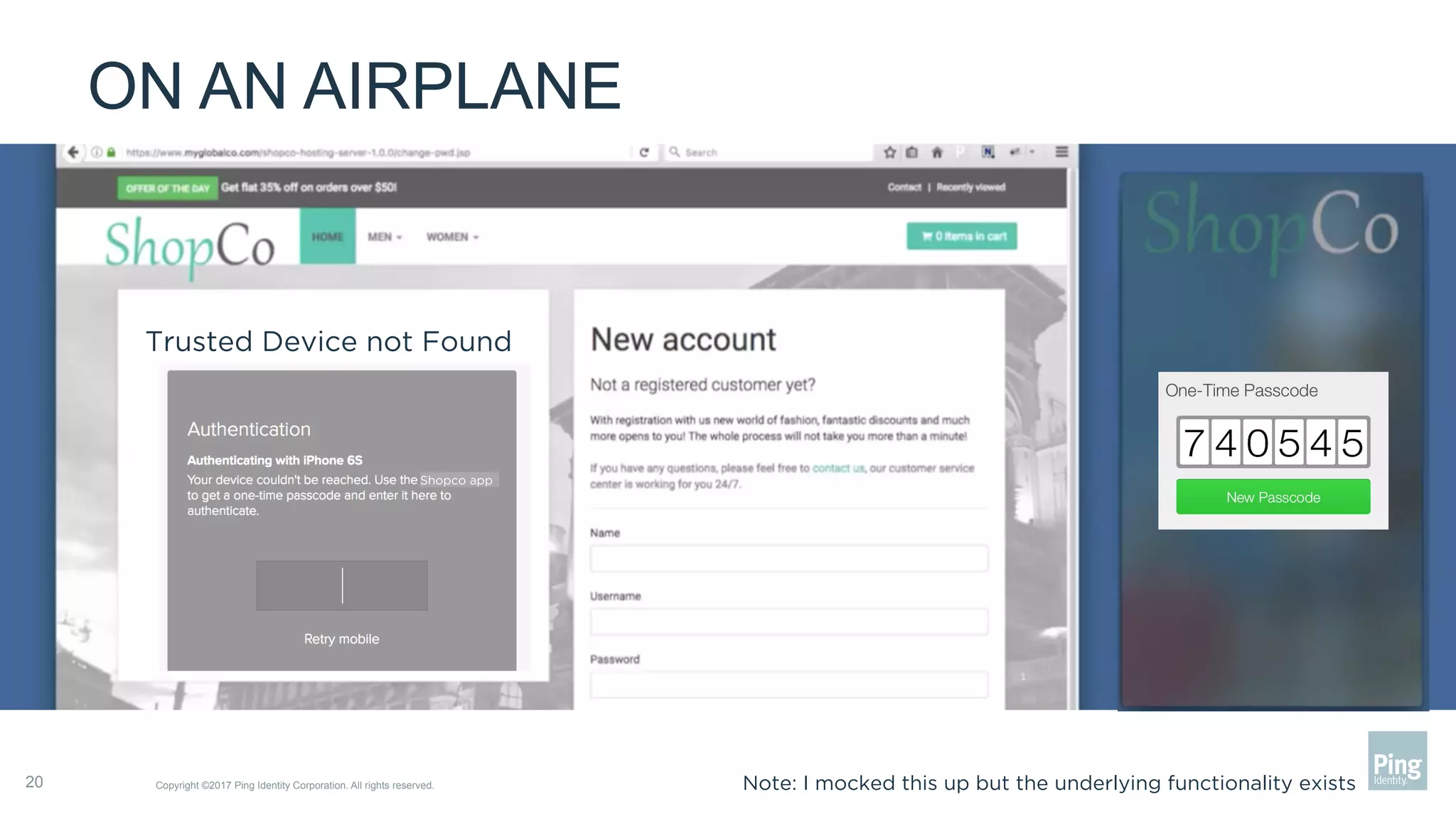
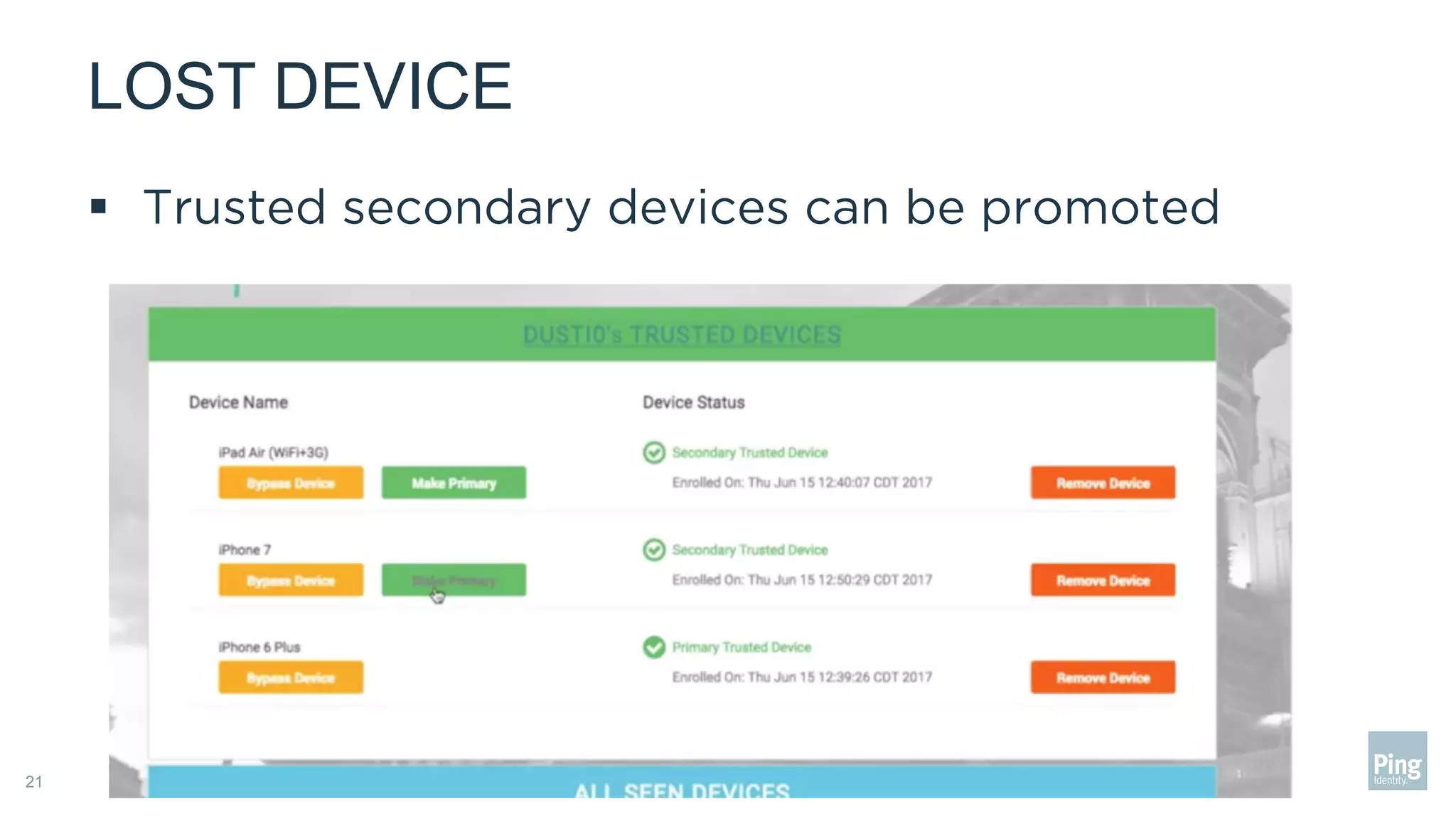
The document outlines three steps to transform a mobile app into a security factor, emphasizing the importance of creating a trusted device through device secrets rather than relying on SMS or email for two-factor authentication. It details enrollment strategies, execution methods for user interactions, and planning for emergencies to ensure user experience and security. Overall, the transformation requires careful planning but offers significant benefits, including increased control and user participation.

![SECURE & CONVENIENT INTERACTIONS
Customer Security
Two-factor authentication is
increasingly important [for CIAM]
Copyright ©2017 Ping Identity Corporation. All rights reserved.2
“
“
Customer Experience
Customers have a low tolerance
for poor user experience
“
“
Security
Customer
Experience](https://image.slidesharecdn.com/threestepsmfawebinarv7final-170831160636/75/Webinar-Three-Steps-to-Transform-Your-Mobile-App-into-a-Security-Factor-2-2048.jpg)