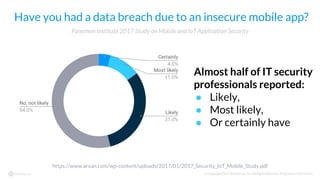
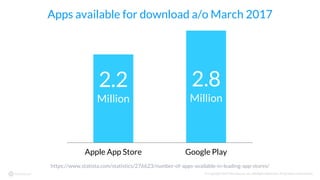
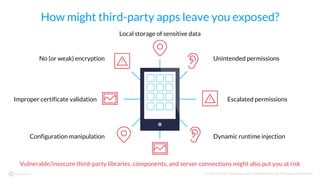
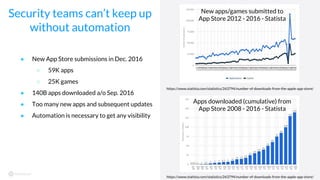
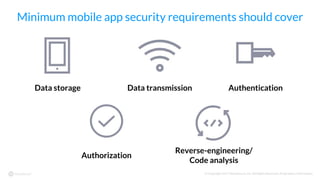
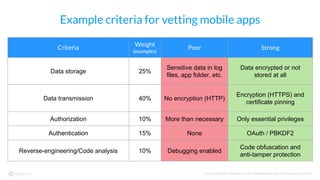
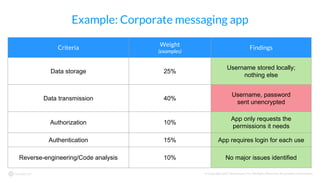
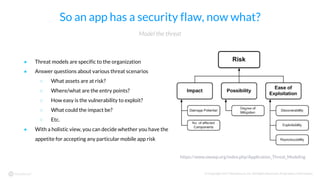
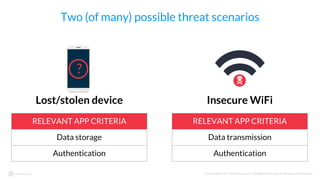
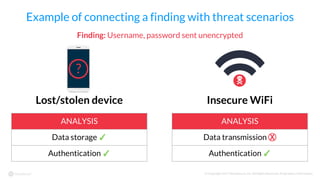
The document discusses the importance of vetting mobile apps for corporate use due to security risks, indicating that a significant percentage of mobile apps harbor vulnerabilities. It outlines a process for mobile app vetting, which includes establishing security requirements, assessing apps, and automating the review process to keep up with the influx of new applications. Key takeaways emphasize that organizations should not rely solely on app store vetting and should actively assess apps against their security standards.