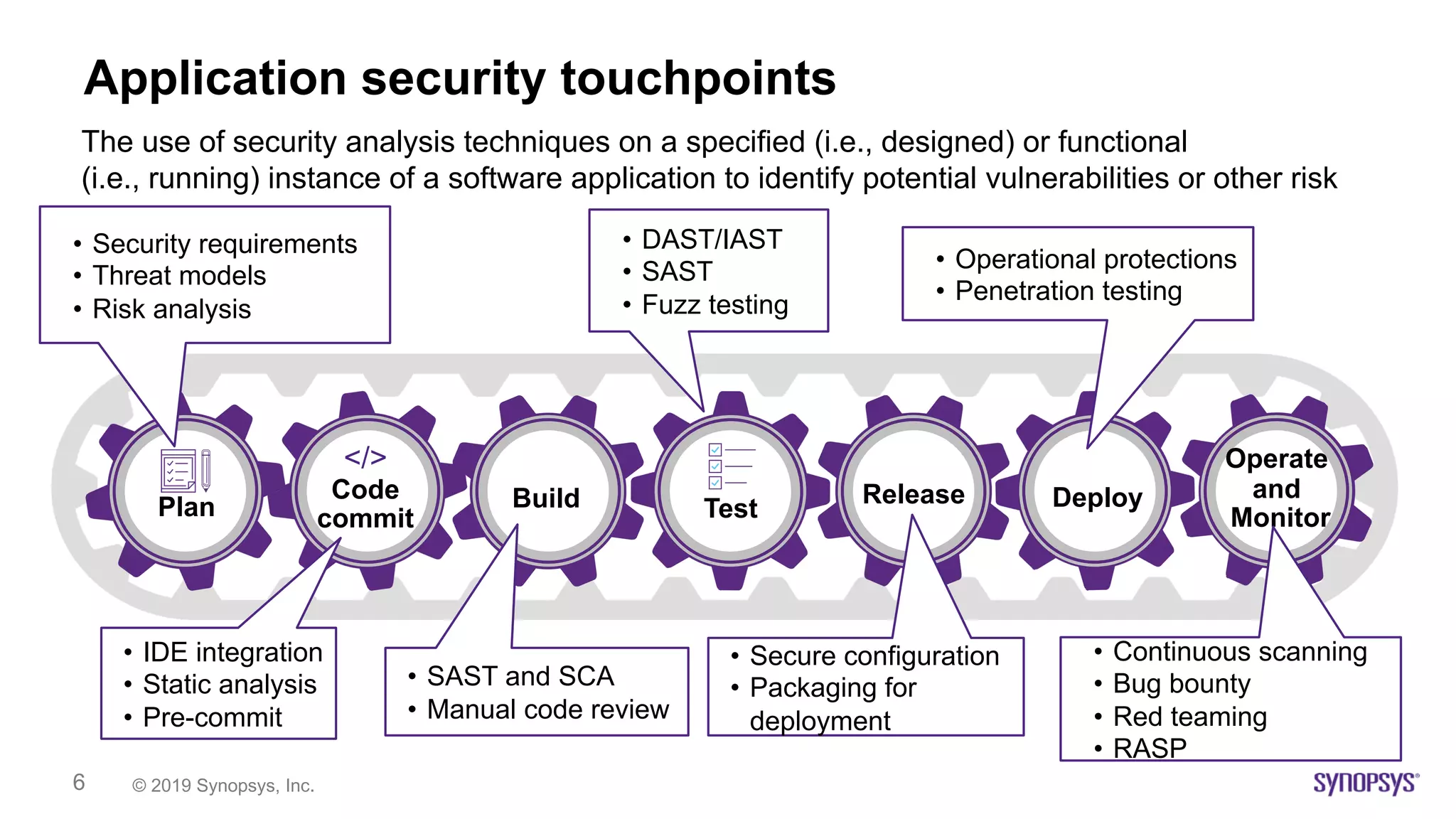
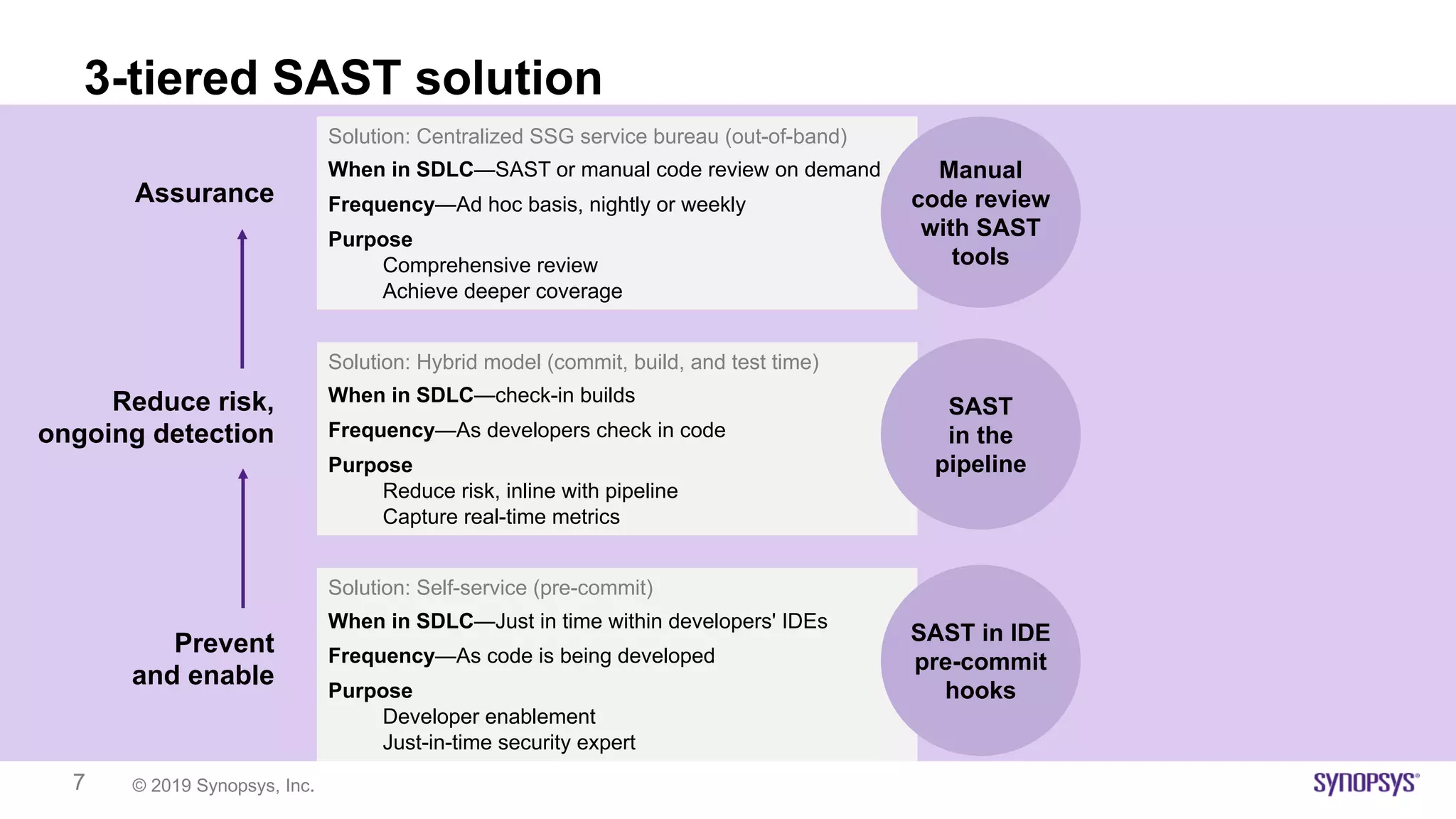
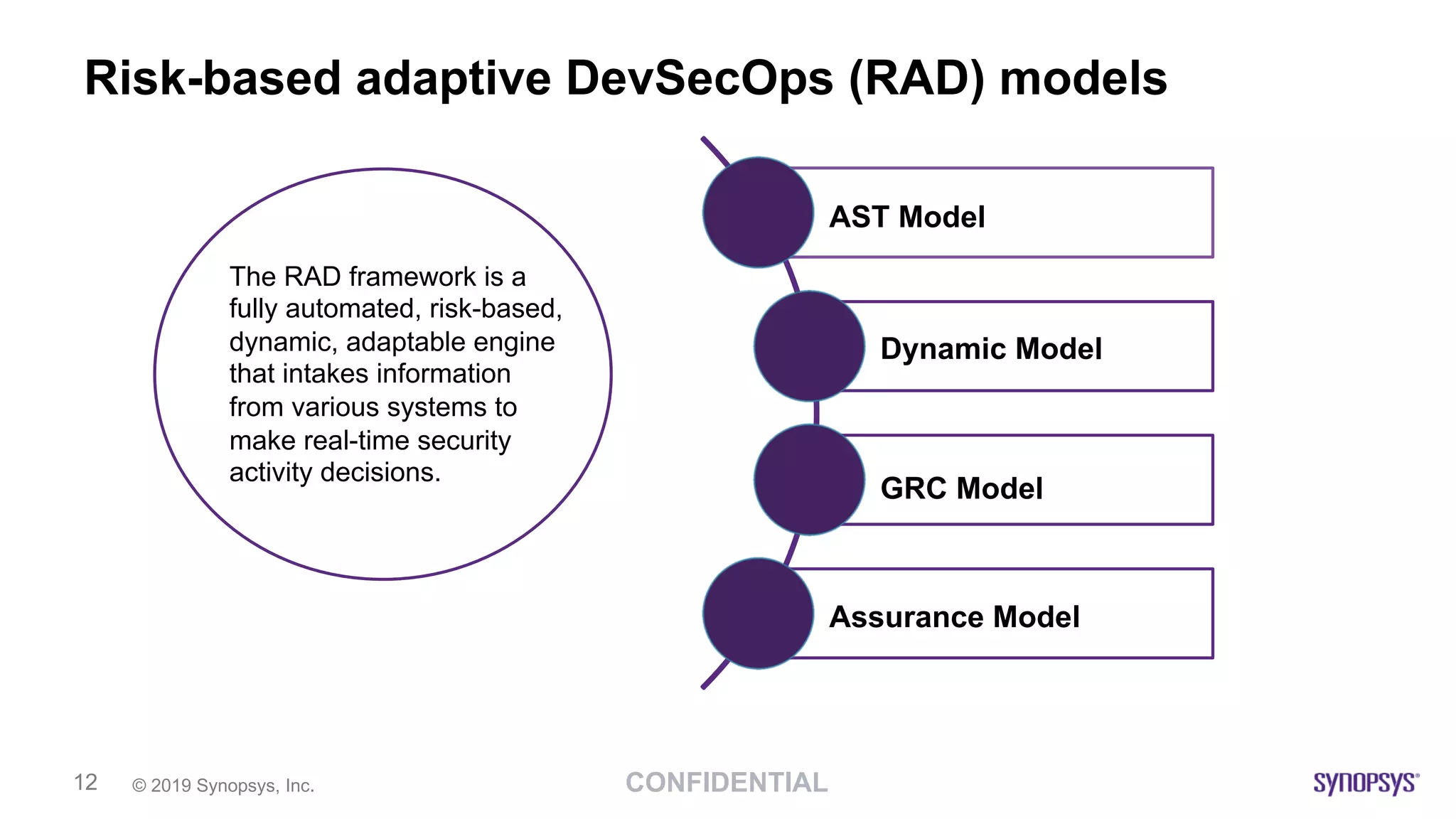
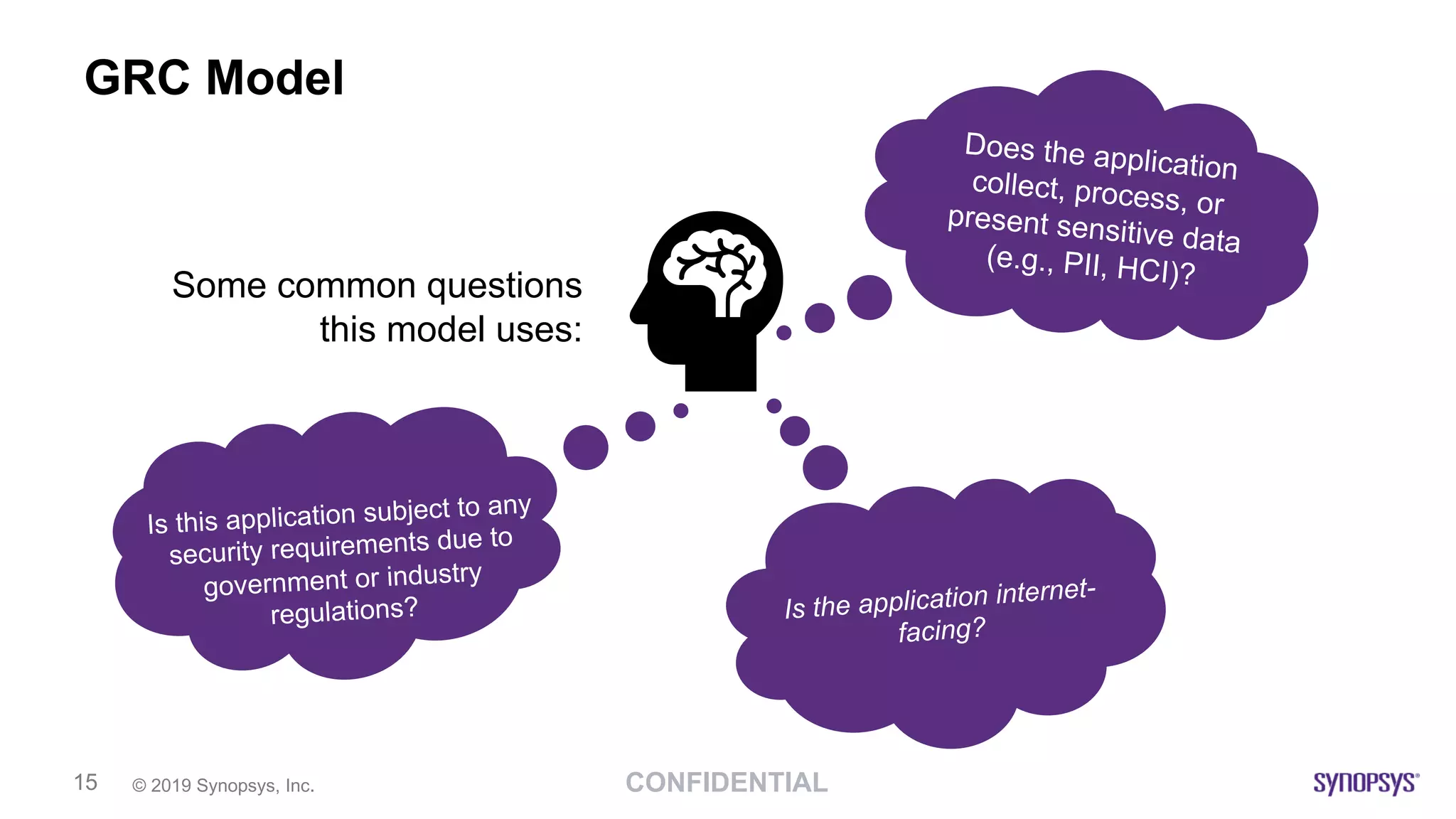
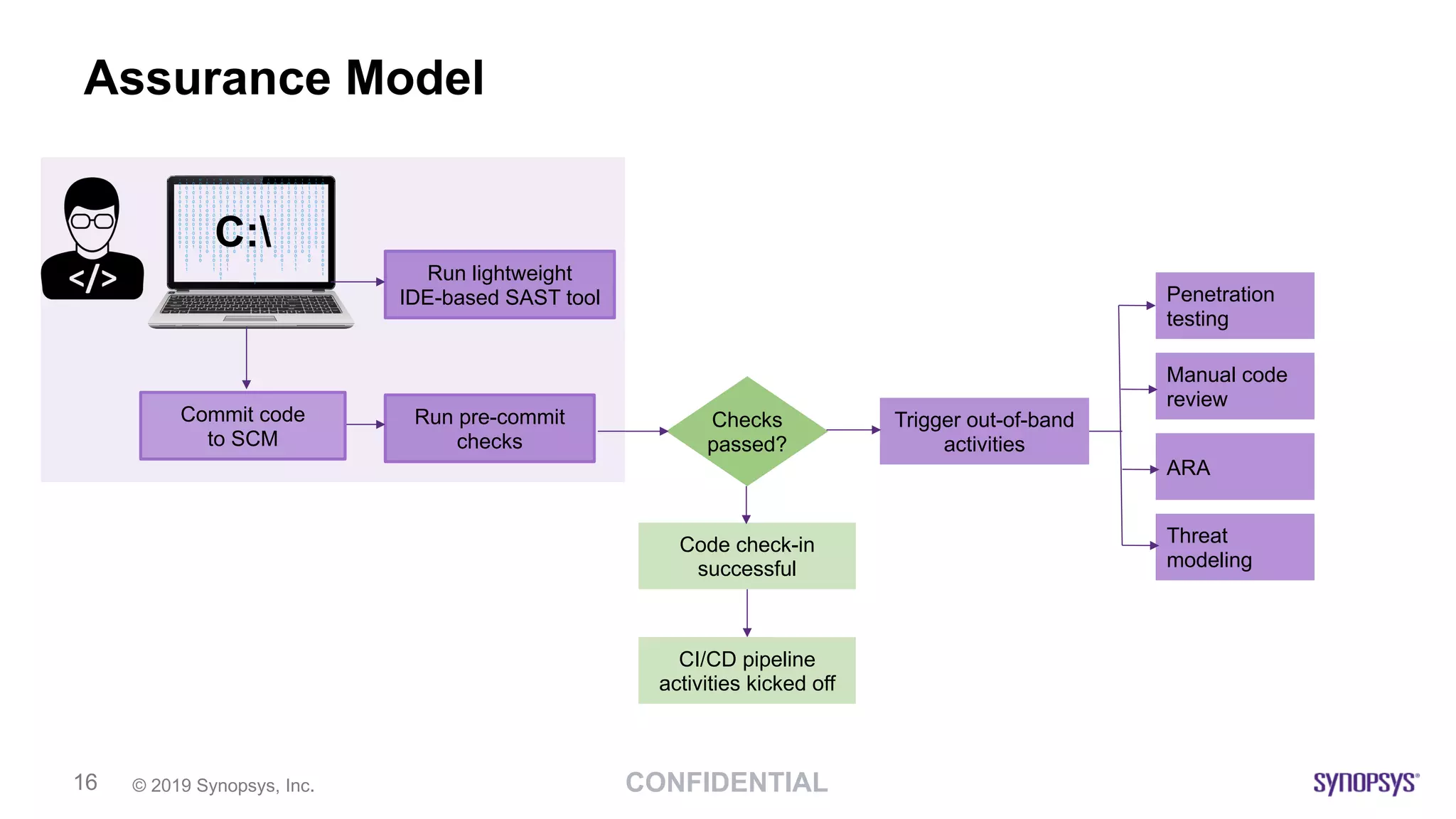
The document outlines the challenges of implementing DevSecOps in software development, highlighting the need for a risk-based adaptive DevSecOps (RAD) framework to enhance security without sacrificing speed and innovation. It presents various models and tools within the RAD framework aimed at automating security activities and ensuring continuous feedback across the software development lifecycle. The document emphasizes the importance of aligning security with development processes and adapting security measures based on risk assessments and compliance requirements.