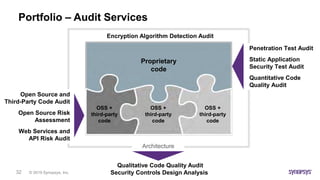
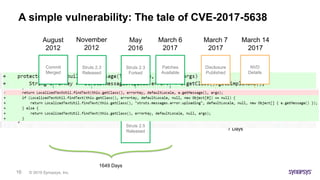
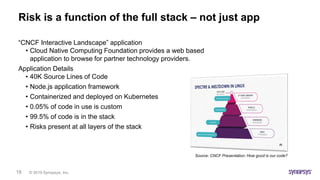
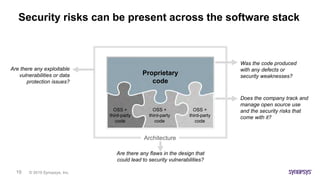
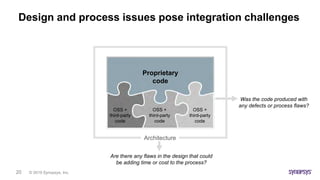
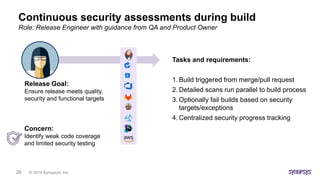
This document discusses the intricacies of technology due diligence in software acquisitions, particularly focusing on open-source software's risks and compliance challenges. It highlights the growing concerns over security vulnerabilities, the complexities of managing open-source components, and the importance of thorough auditing processes. Key factors include understanding software architecture, governance, and continuous security assessments during development to mitigate risks associated with open-source usage.

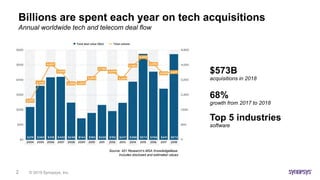

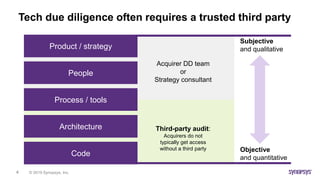




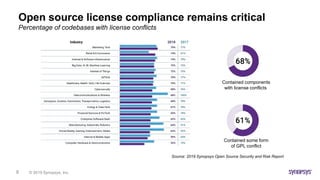





![© 2019 Synopsys, Inc.28
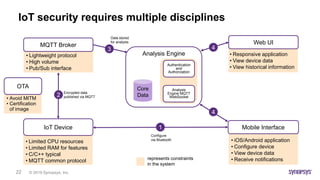
Web services APIs also impact risk profiles
API Lifecycle
• Twitter API shutdown August 2018
• Google+ shutdown April 2019
• Salesforce API versioning
Data usage and control
• GDPR data processor vs data controller
• Data sovereignty and jurisdiction
• Data mashups and inference scenarios
Data and privacy breaches
• Facebook API tokens
• [24]7.io and Delta, Kmart, Sears
• Third-party data bleeds
• Phone home tracking
• CVE-2018-1002105 in Kubernetes API](https://image.slidesharecdn.com/streamlingtechdue-190702144955/85/Webinar-Streamling-Your-Tech-Due-Diligence-Process-for-Software-Assets-28-320.jpg)