Infographic–A Look Back at the First Year of GDPR
•
0 likes•56 views
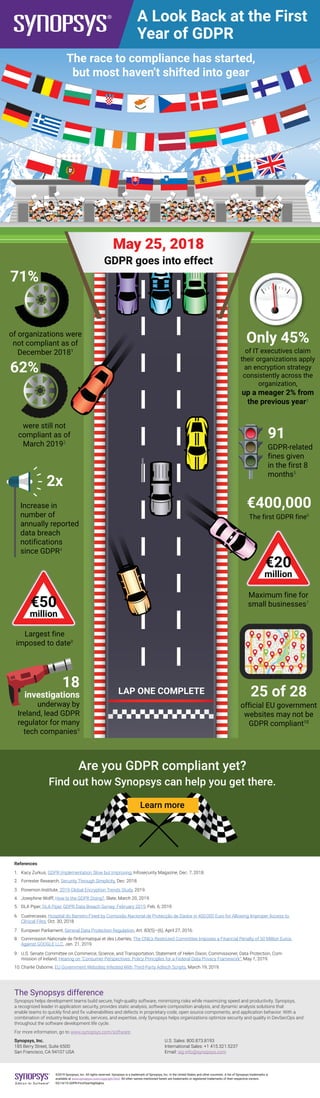
1) One year after the GDPR went into effect, most organizations were still not compliant. Only 45% of IT executives claimed their organizations consistently applied encryption strategies. 2) There has been a two-fold increase in the number of annually reported data breach notifications since GDPR and 91 GDPR-related fines have been given in the first 8 months. 3) The largest GDPR fine to date was €50 million imposed on Google and 18 investigations are underway by Ireland's data protection regulator for many tech companies.
Report
Share
Report
Share
Download to read offline
Recommended
Recommended
More Related Content
What's hot
What's hot (20)
GDPR: National Grid Case Study - Glen Truman (National Grid)

GDPR: National Grid Case Study - Glen Truman (National Grid)
Marketing data management | The new way to think about your data

Marketing data management | The new way to think about your data
Let’s rethink cloud application security in 2016 - Patrick Kerpan's Secure360...

Let’s rethink cloud application security in 2016 - Patrick Kerpan's Secure360...
ROI of Privacy: Building a Case for Investment [Webinar Slides]![ROI of Privacy: Building a Case for Investment [Webinar Slides]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![ROI of Privacy: Building a Case for Investment [Webinar Slides]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
ROI of Privacy: Building a Case for Investment [Webinar Slides]
The Evolution of Data Privacy - A Symantec Information Security Perspective o...

The Evolution of Data Privacy - A Symantec Information Security Perspective o...
Benchmarking Your GDPR Compliance: Will You Make the Grade? [TrustArc Webinar...

Benchmarking Your GDPR Compliance: Will You Make the Grade? [TrustArc Webinar...
A Data Privacy & Security Year in Review: Top 10 Trends and Predictions

A Data Privacy & Security Year in Review: Top 10 Trends and Predictions
Security Practices: The Generational Gap | Infographic

Security Practices: The Generational Gap | Infographic
The Third Wave of Enterprise Communications by Bryan Martin, 8x8

The Third Wave of Enterprise Communications by Bryan Martin, 8x8
Infographic: The crippled state of network security

Infographic: The crippled state of network security
Teleran Data Protection - Addressing 5 Critical GDPR Requirements

Teleran Data Protection - Addressing 5 Critical GDPR Requirements
Similar to Infographic–A Look Back at the First Year of GDPR
Similar to Infographic–A Look Back at the First Year of GDPR (20)
GDPR: A Threat or Opportunity? www.normanbroadbent.

GDPR: A Threat or Opportunity? www.normanbroadbent.
GDPR: A ticking time bomb is approaching - Another Millennium Bug or is this ...

GDPR: A ticking time bomb is approaching - Another Millennium Bug or is this ...
GDPR, what you need to know and how to prepare for it e book

GDPR, what you need to know and how to prepare for it e book
delphix-ebook-using-data-effectively-compliance-banking-1

delphix-ebook-using-data-effectively-compliance-banking-1
What does GDPR laws mean for Australian businesses

What does GDPR laws mean for Australian businesses
Security, GDRP, and IT outsourcing: How to get it right

Security, GDRP, and IT outsourcing: How to get it right
Running Head THE IMPACT OF GDPR ON GLOBAL IT POLICIES1THE IMPA.docx

Running Head THE IMPACT OF GDPR ON GLOBAL IT POLICIES1THE IMPA.docx
#FIRMday Manchester Autumn 2017 - The General Data Protection Regulation (GDP...

#FIRMday Manchester Autumn 2017 - The General Data Protection Regulation (GDP...
More from Synopsys Software Integrity Group
Webinar–Mobile Application Hardening Protecting Business Critical Apps

Webinar–Mobile Application Hardening Protecting Business Critical AppsSynopsys Software Integrity Group
Do Design Quality and Code Quality Matter in Merger and Acquisition Tech Due ...

Do Design Quality and Code Quality Matter in Merger and Acquisition Tech Due ...Synopsys Software Integrity Group
Webinar–Financial Services Study Shows Why Investing in AppSec Matters

Webinar–Financial Services Study Shows Why Investing in AppSec MattersSynopsys Software Integrity Group
Webinar–Improving Fuzz Testing of Infotainment Systems and Telematics Units U...

Webinar–Improving Fuzz Testing of Infotainment Systems and Telematics Units U...Synopsys Software Integrity Group
Webinar–Is Your Software Security Supply Chain a Security Blind Spot?

Webinar–Is Your Software Security Supply Chain a Security Blind Spot?Synopsys Software Integrity Group
Webinar–Creating a Modern AppSec Toolchain to Quantify Service Risks

Webinar–Creating a Modern AppSec Toolchain to Quantify Service RisksSynopsys Software Integrity Group
Webinar – Streamling Your Tech Due Diligence Process for Software Assets

Webinar – Streamling Your Tech Due Diligence Process for Software AssetsSynopsys Software Integrity Group
More from Synopsys Software Integrity Group (20)
Webinar–Mobile Application Hardening Protecting Business Critical Apps

Webinar–Mobile Application Hardening Protecting Business Critical Apps
Webinar–You've Got Your Open Source Audit Report–Now What? 

Webinar–You've Got Your Open Source Audit Report–Now What?
Webinar–OWASP Top 10 for JavaScript for Developers

Webinar–OWASP Top 10 for JavaScript for Developers
Webinar–The State of Open Source in M&A Transactions 

Webinar–The State of Open Source in M&A Transactions
Do Design Quality and Code Quality Matter in Merger and Acquisition Tech Due ...

Do Design Quality and Code Quality Matter in Merger and Acquisition Tech Due ...
Webinar–Delivering a Next Generation Vulnerability Feed

Webinar–Delivering a Next Generation Vulnerability Feed
Webinar–Financial Services Study Shows Why Investing in AppSec Matters

Webinar–Financial Services Study Shows Why Investing in AppSec Matters
Webinar–What You Need To Know About Open Source Licensing

Webinar–What You Need To Know About Open Source Licensing
Webinar–Improving Fuzz Testing of Infotainment Systems and Telematics Units U...

Webinar–Improving Fuzz Testing of Infotainment Systems and Telematics Units U...
Webinar–Why All Open Source Scans Aren't Created Equal

Webinar–Why All Open Source Scans Aren't Created Equal
Webinar–Is Your Software Security Supply Chain a Security Blind Spot?

Webinar–Is Your Software Security Supply Chain a Security Blind Spot?
Webinar–Sécurité Applicative et DevSecOps dans un monde Agile

Webinar–Sécurité Applicative et DevSecOps dans un monde Agile
Webinar–Creating a Modern AppSec Toolchain to Quantify Service Risks

Webinar–Creating a Modern AppSec Toolchain to Quantify Service Risks
Webinar – Streamling Your Tech Due Diligence Process for Software Assets

Webinar – Streamling Your Tech Due Diligence Process for Software Assets
Recently uploaded
Try MyIntelliAccount Cloud Accounting Software As A Service Solution Risk Fre...

Try MyIntelliAccount Cloud Accounting Software As A Service Solution Risk Fre...MyIntelliSource, Inc.
Steps To Getting Up And Running Quickly With MyTimeClock Employee Scheduling ...

Steps To Getting Up And Running Quickly With MyTimeClock Employee Scheduling ...MyIntelliSource, Inc.
Recently uploaded (20)
Professional Resume Template for Software Developers

Professional Resume Template for Software Developers
The Essentials of Digital Experience Monitoring_ A Comprehensive Guide.pdf

The Essentials of Digital Experience Monitoring_ A Comprehensive Guide.pdf
Advancing Engineering with AI through the Next Generation of Strategic Projec...

Advancing Engineering with AI through the Next Generation of Strategic Projec...
Building Real-Time Data Pipelines: Stream & Batch Processing workshop Slide

Building Real-Time Data Pipelines: Stream & Batch Processing workshop Slide
Try MyIntelliAccount Cloud Accounting Software As A Service Solution Risk Fre...

Try MyIntelliAccount Cloud Accounting Software As A Service Solution Risk Fre...
Alluxio Monthly Webinar | Cloud-Native Model Training on Distributed Data

Alluxio Monthly Webinar | Cloud-Native Model Training on Distributed Data
The Real-World Challenges of Medical Device Cybersecurity- Mitigating Vulnera...

The Real-World Challenges of Medical Device Cybersecurity- Mitigating Vulnera...
Steps To Getting Up And Running Quickly With MyTimeClock Employee Scheduling ...

Steps To Getting Up And Running Quickly With MyTimeClock Employee Scheduling ...
why an Opensea Clone Script might be your perfect match.pdf

why an Opensea Clone Script might be your perfect match.pdf
Learn the Fundamentals of XCUITest Framework_ A Beginner's Guide.pdf

Learn the Fundamentals of XCUITest Framework_ A Beginner's Guide.pdf
Building a General PDE Solving Framework with Symbolic-Numeric Scientific Mac...

Building a General PDE Solving Framework with Symbolic-Numeric Scientific Mac...
Project Based Learning (A.I).pptx detail explanation

Project Based Learning (A.I).pptx detail explanation
Short Story: Unveiling the Reasoning Abilities of Large Language Models by Ke...

Short Story: Unveiling the Reasoning Abilities of Large Language Models by Ke...
Infographic–A Look Back at the First Year of GDPR
- 1. A Look Back at the First Year of GDPR The race to compliance has started, but most haven’t shifted into gear May 25, 2018 GDPR goes into effect of organizations were not compliant as of December 20181 were still not compliant as of March 20192 Only 45% of IT executives claim their organizations apply an encryption strategy consistently across the organization, up a meager 2% from the previous year3 71% 62% 2x Increase in number of annually reported data breach notifications since GDPR4 91 GDPR-related fines given in the first 8 months5 €400,000 The first GDPR fine6 €20 million Maximum fine for small businesses7 €50 million Largest fine imposed to date8 18 investigations underway by Ireland, lead GDPR regulator for many tech companies9 25 of 28 official EU government websites may not be GDPR compliant10 Are you GDPR compliant yet? Find out how Synopsys can help you get there. Learn more ©2019 Synopsys, Inc. All rights reserved. Synopsys is a trademark of Synopsys, Inc. in the United States and other countries. A list of Synopsys trademarks is available at www.synopsys.com/copyright.html . All other names mentioned herein are trademarks or registered trademarks of their respective owners. 05/14/19.GDPR-FirstYearHighlights. The Synopsys difference Synopsys helps development teams build secure, high-quality software, minimizing risks while maximizing speed and productivity. Synopsys, a recognized leader in application security, provides static analysis, software composition analysis, and dynamic analysis solutions that enable teams to quickly find and fix vulnerabilities and defects in proprietary code, open source components, and application behavior. With a combination of industry-leading tools, services, and expertise, only Synopsys helps organizations optimize security and quality in DevSecOps and throughout the software development life cycle. For more information, go to www.synopsys.com/software. Synopsys, Inc. 185 Berry Street, Suite 6500 San Francisco, CA 94107 USA U.S. Sales: 800.873.8193 International Sales: +1 415.321.5237 Email: sig-info@synopsys.com LAP ONE COMPLETE References 1. Kacy Zurkus, GDPR Implementation Slow but Improving, Infosecurity Magazine, Dec. 7, 2018. 2. Forrester Research, Security Through Simplicity, Dec. 2018. 3. Ponemon Institute, 2019 Global Encryption Trends Study, 2019. 4. Josephine Wolff, How Is the GDPR Doing?, Slate, March 20, 2019. 5. DLA Piper, DLA Piper GDPR Data Breach Survey: February 2019, Feb. 6, 2019. 6. Cuatrecasas, Hospital do Barreiro Fined by Comissão Nacional de Protecção de Dados in 400,000 Euro for Allowing Improper Access to Clinical Files, Oct. 30, 2018. 7. European Parliament, General Data Protection Regulation, Art. 83(5)–(6), April 27, 2016. 8. Commission Nationale de l’Informatique et des Libertés, The CNIL’s Restricted Committee Imposes a Financial Penalty of 50 Million Euros Against GOOGLE LLC, Jan. 21, 2019. 9. U.S. Senate Committee on Commerce, Science, and Transportation, Statement of Helen Dixon, Commissioner, Data Protection, Com- mission of Ireland, Hearing on “Consumer Perspectives: Policy Principles for a Federal Data Privacy Framework”, May 1, 2019. 10. Charlie Osborne, EU Government Websites Infested With Third-Party Adtech Scripts, March 19, 2019.
