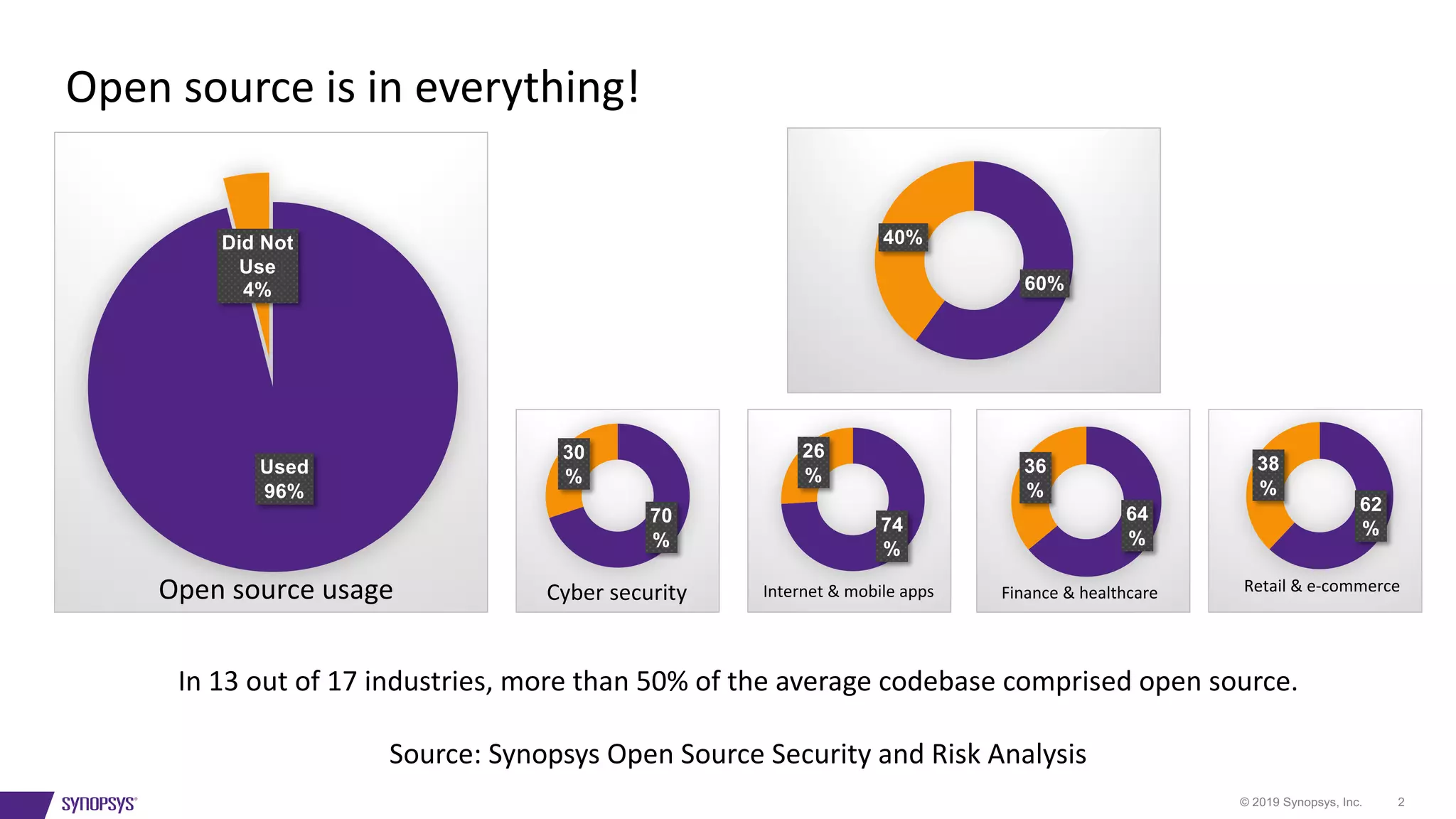
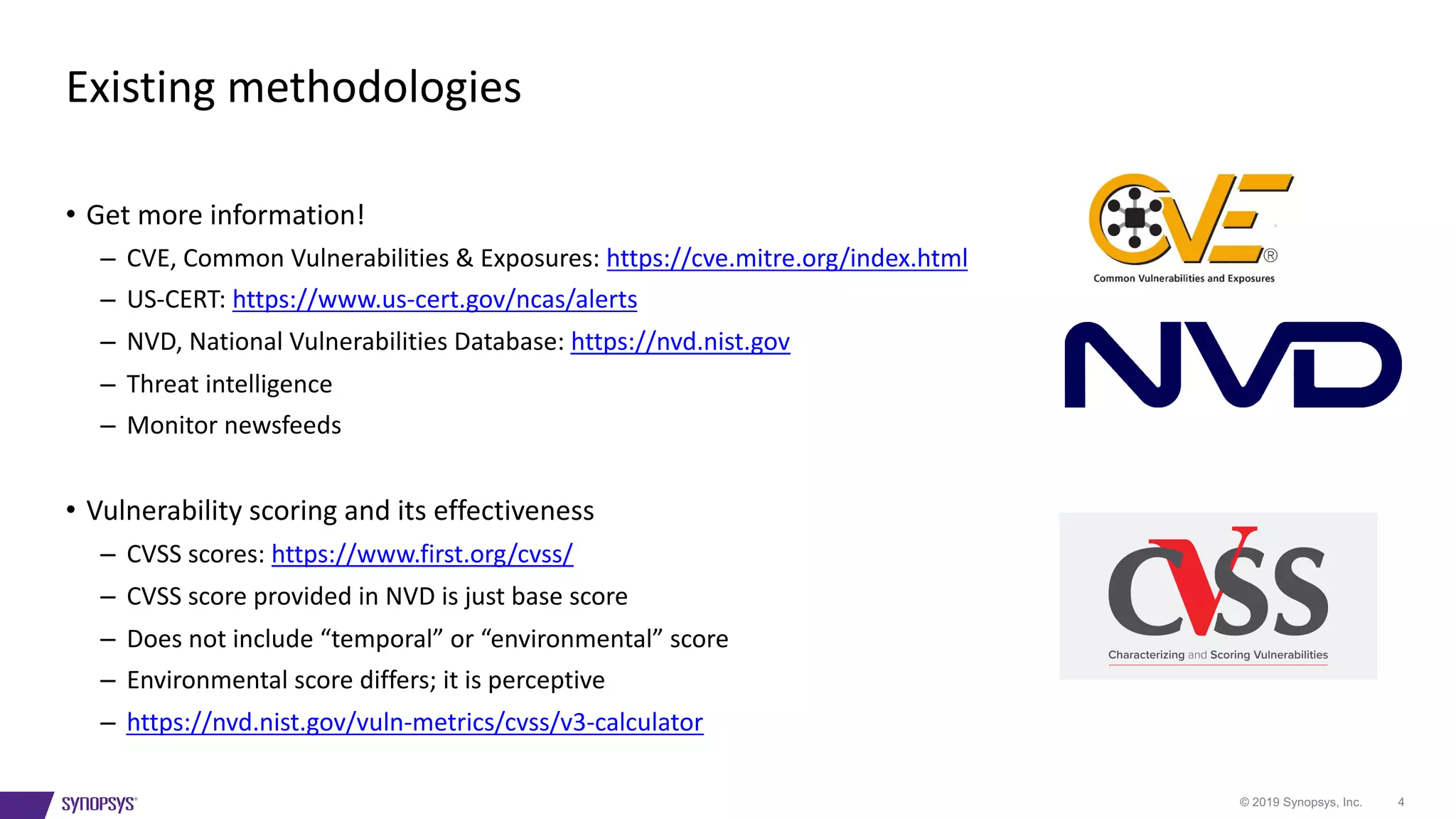
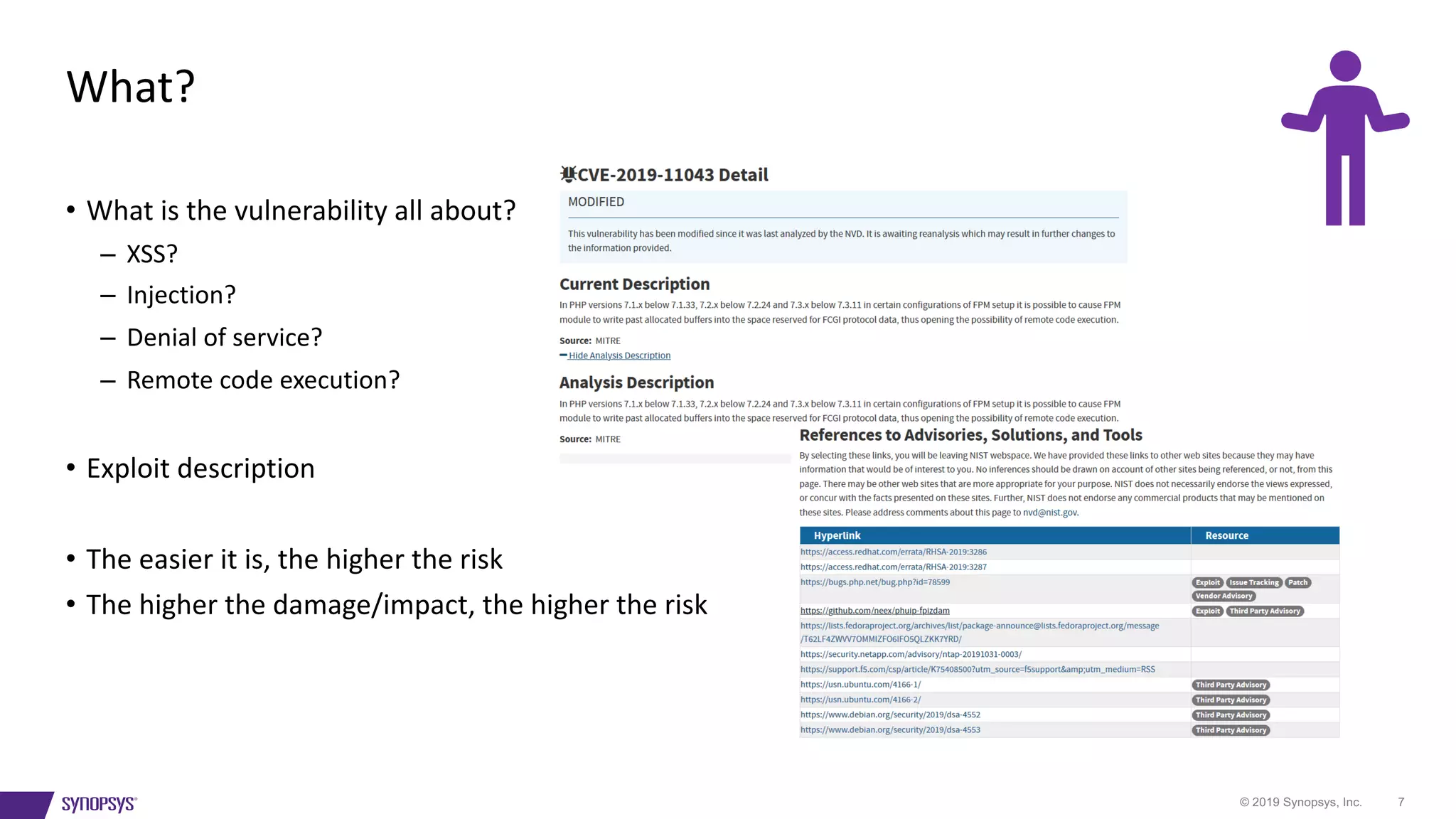
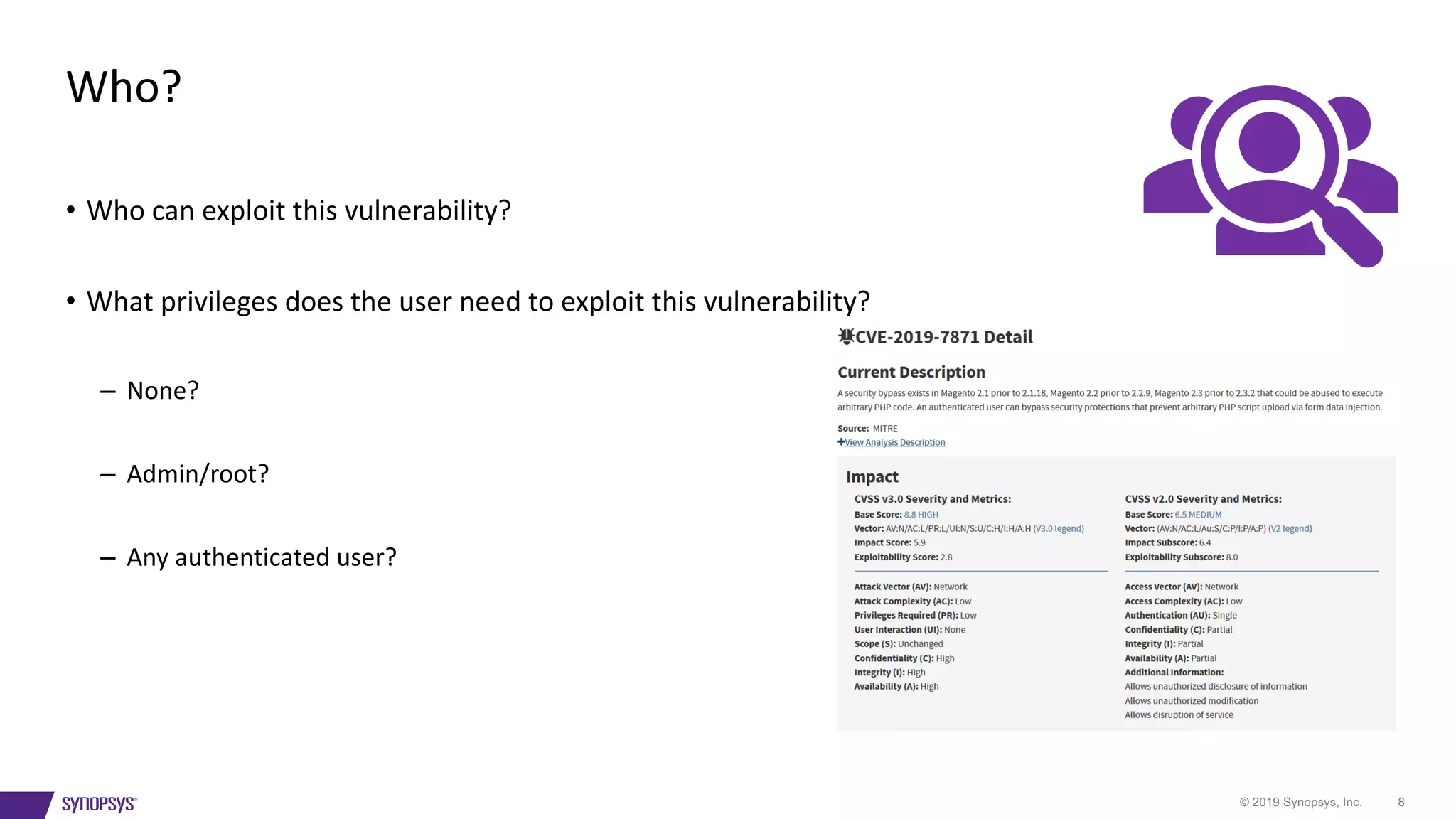
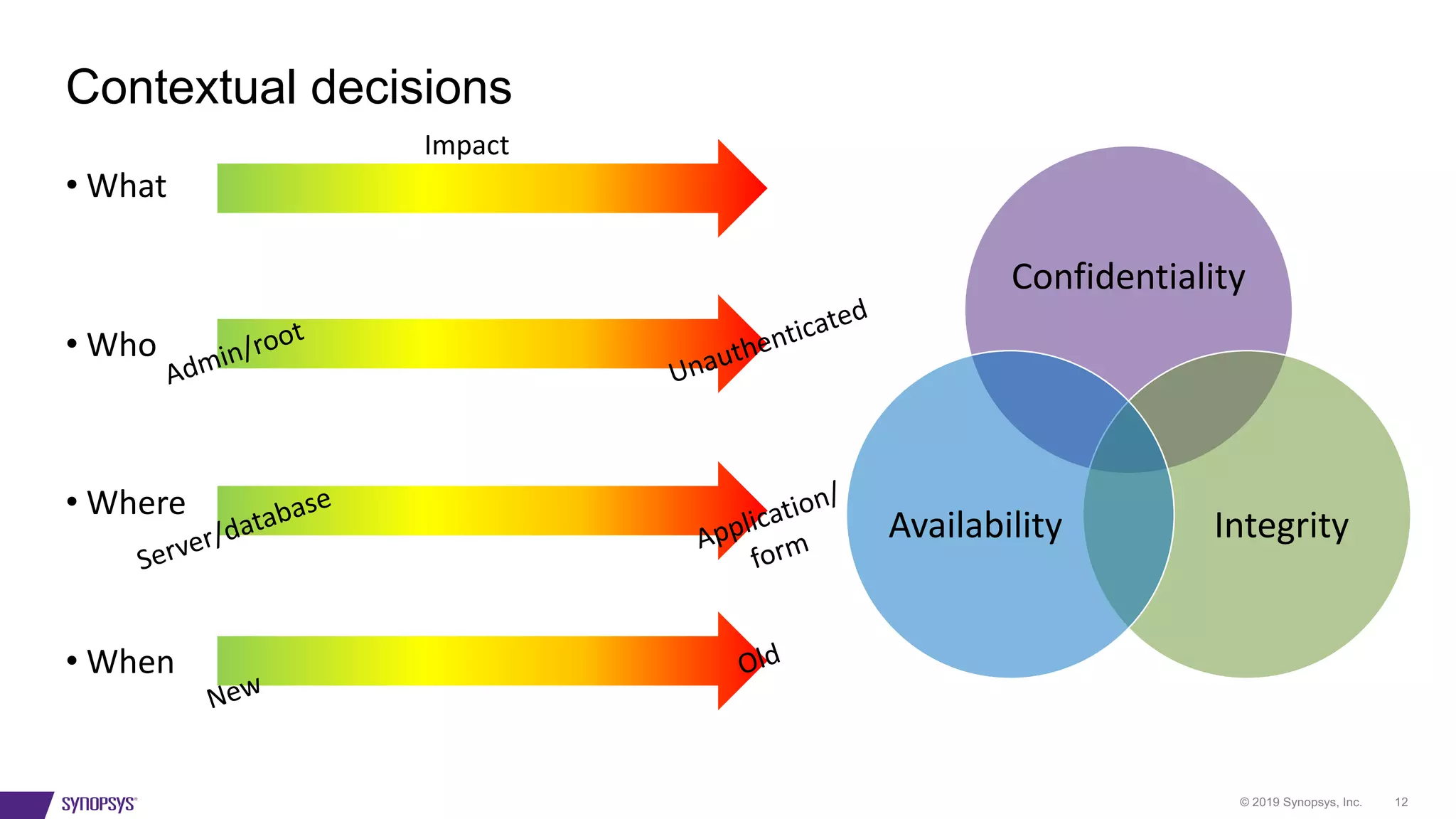
The document outlines a framework for risk-ranking vulnerabilities, emphasizing the importance of understanding the nature of vulnerabilities, their potential exploiters, their locations, and their age. It highlights that over 50% of code in many industries comprises open source, which has significant implications for security. The document also provides resources for further information on vulnerabilities and recommends assessing various factors that contribute to risk levels.