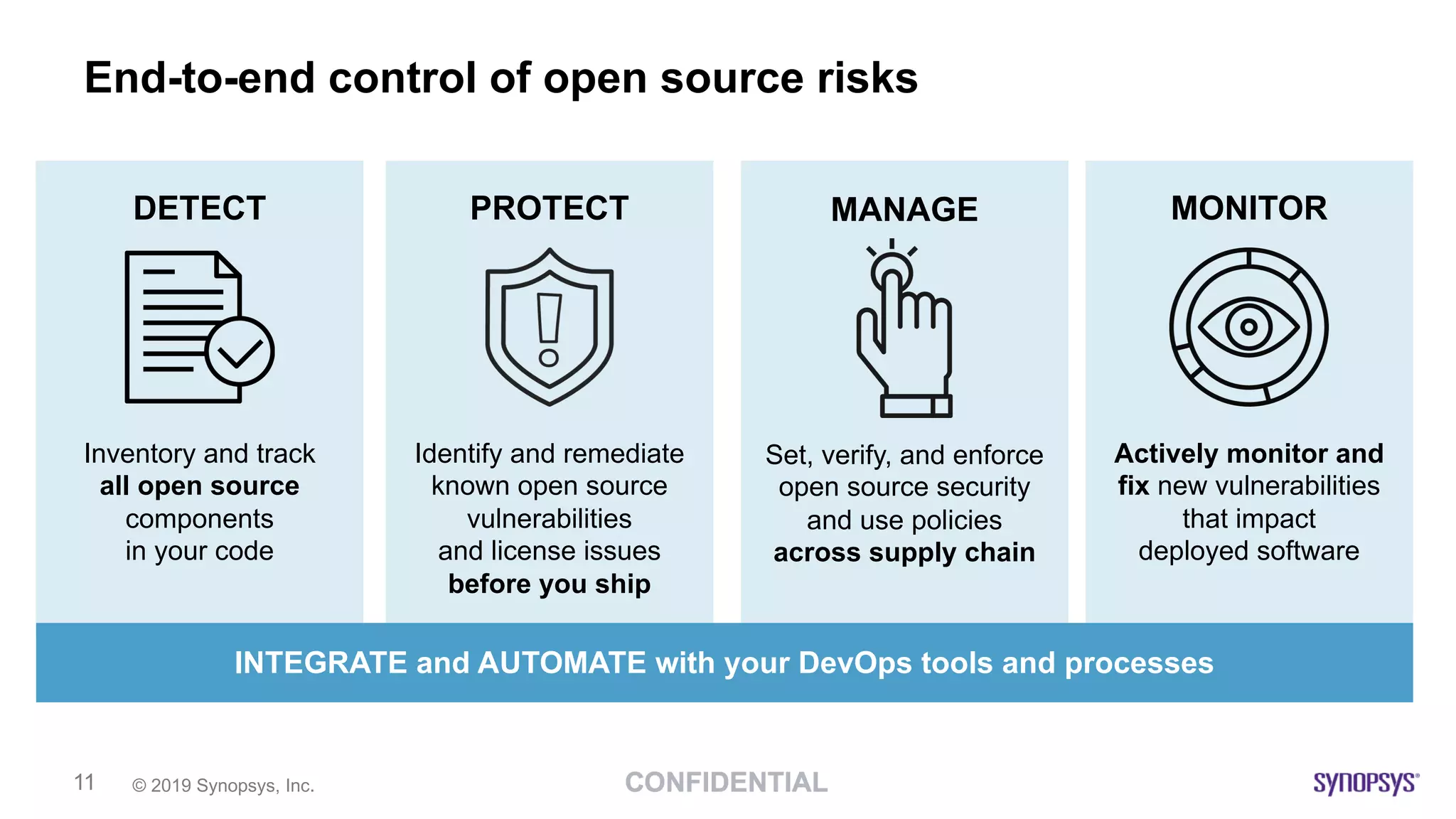
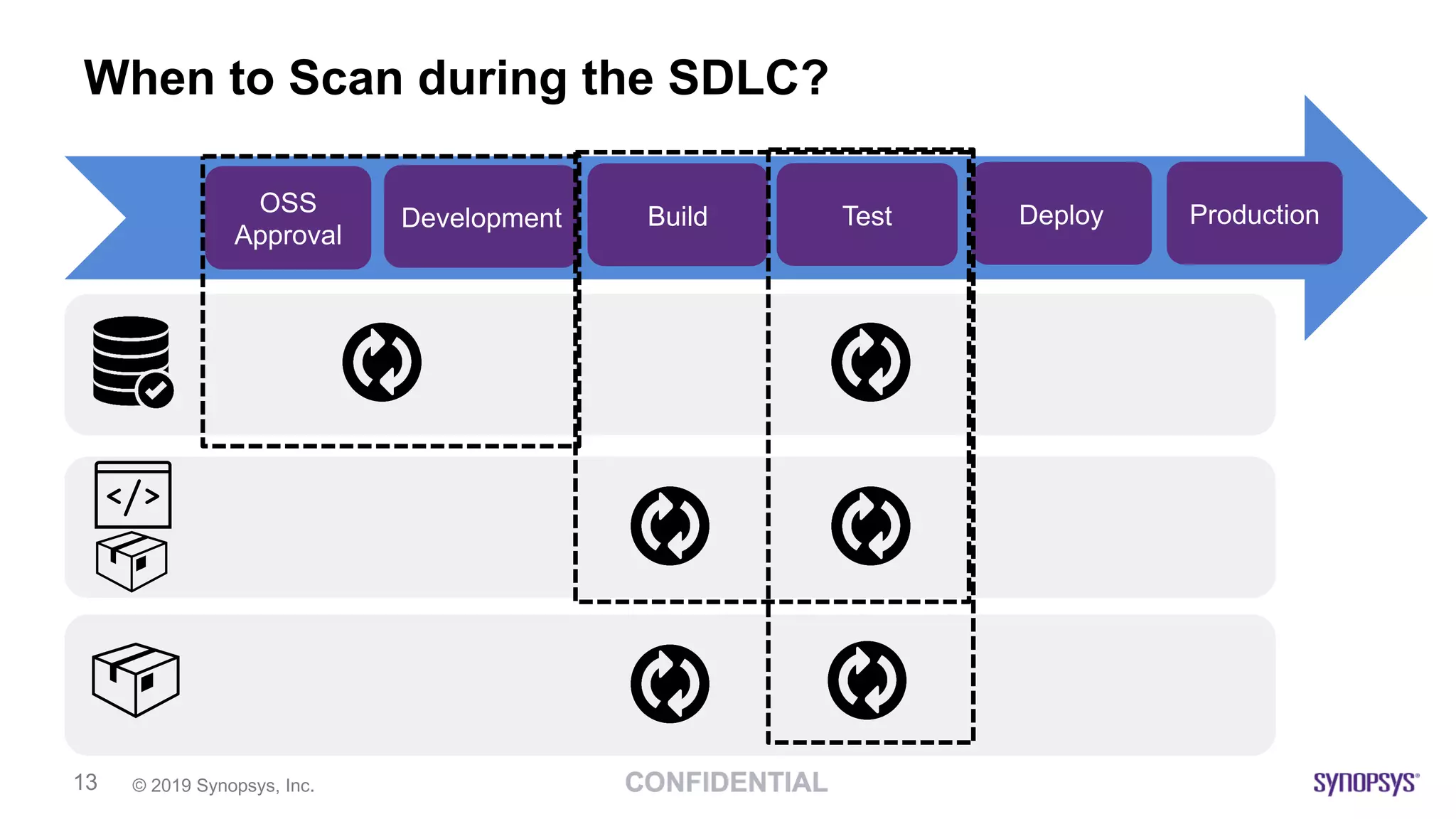
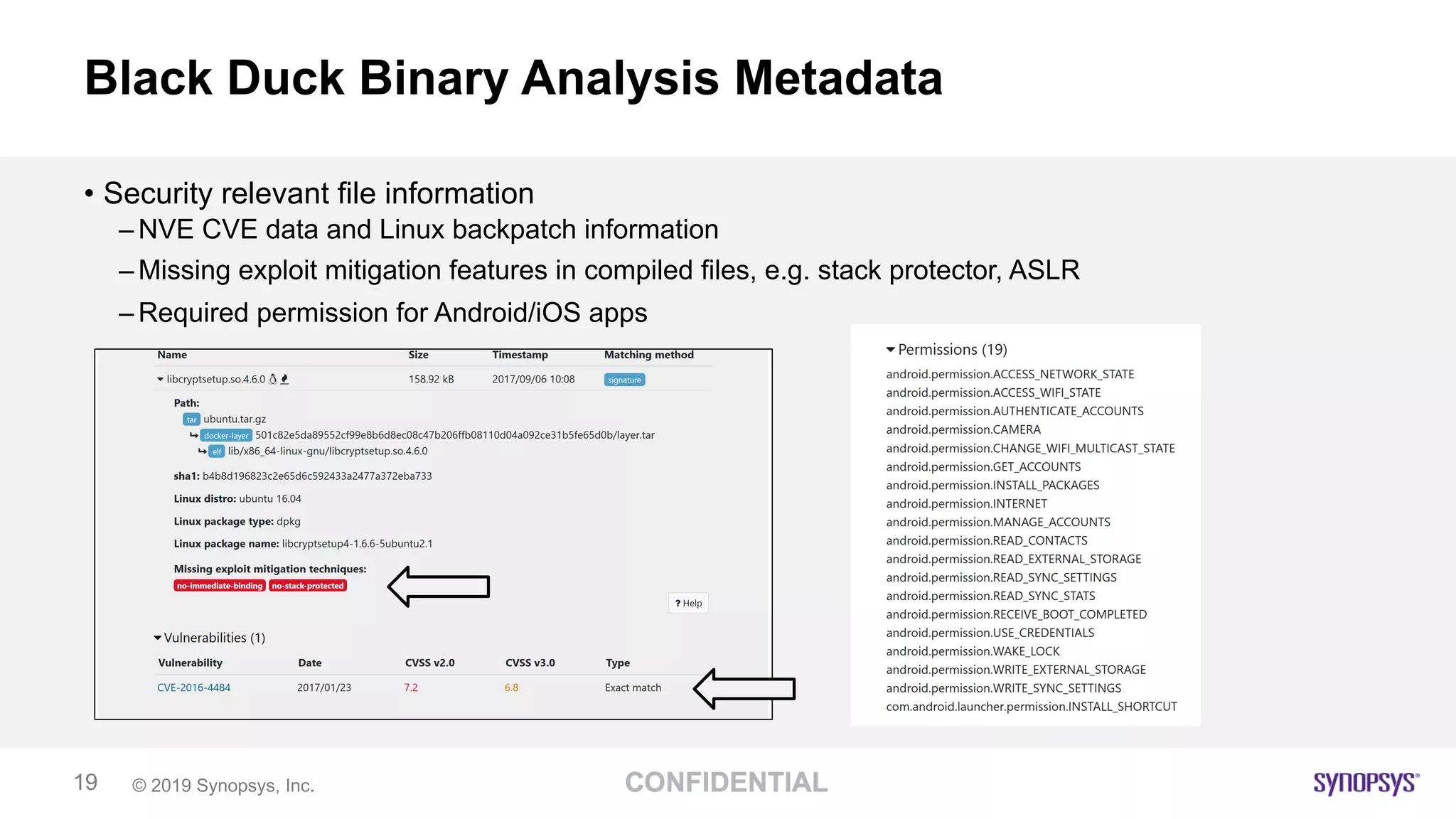
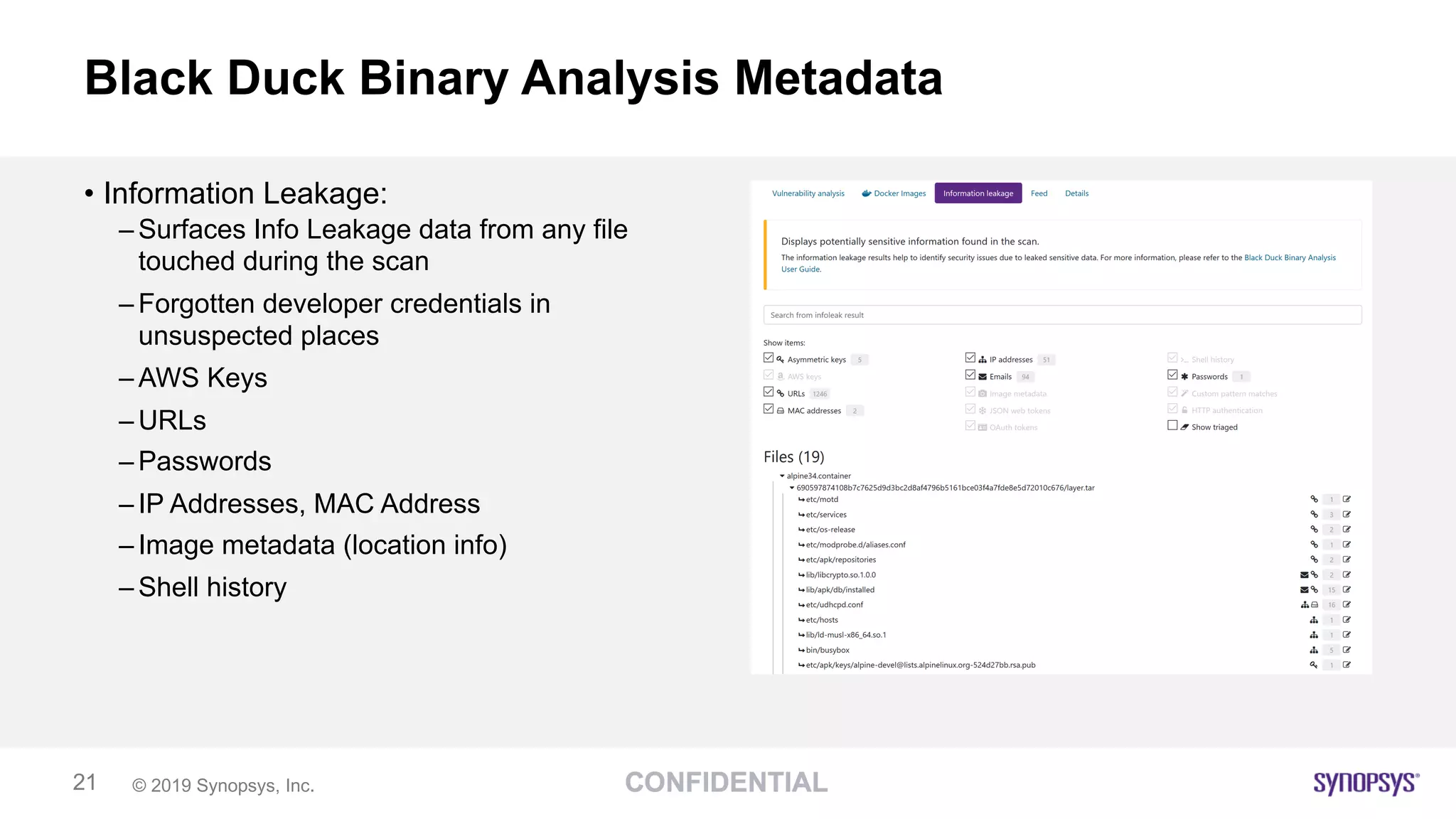
The document discusses the importance of scanning binaries for open source components, emphasizing that cybersecurity risks in supply chains are a major concern for leaders. It recommends using tools like Black Duck Binary Analysis to identify security vulnerabilities and manage risks associated with binaries, particularly since many components are delivered as binaries rather than source code. Key practices outlined include understanding risk tolerance, implementing end-to-end control of open source risks, and ensuring compliance through effective monitoring and scanning during the software development lifecycle.