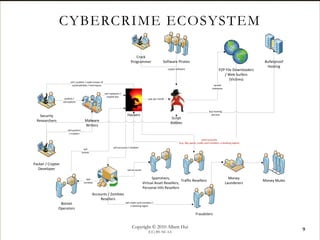
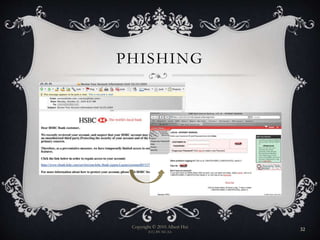
The document discusses the cybercrime ecosystem and specialization within it. It describes how cybercriminals specialize in specific criminal business functions like developing malware, exploit kits, crypting software, and spamming. This specialization allows criminals to scale up their operations and legitimize most business activities. The document also examines how cybercriminals realize financial gains through activities like spamming, renting botnets, selling accounts and personal information, money laundering through methods such as using money mules and stored value cards, and using online casinos and auction sites.