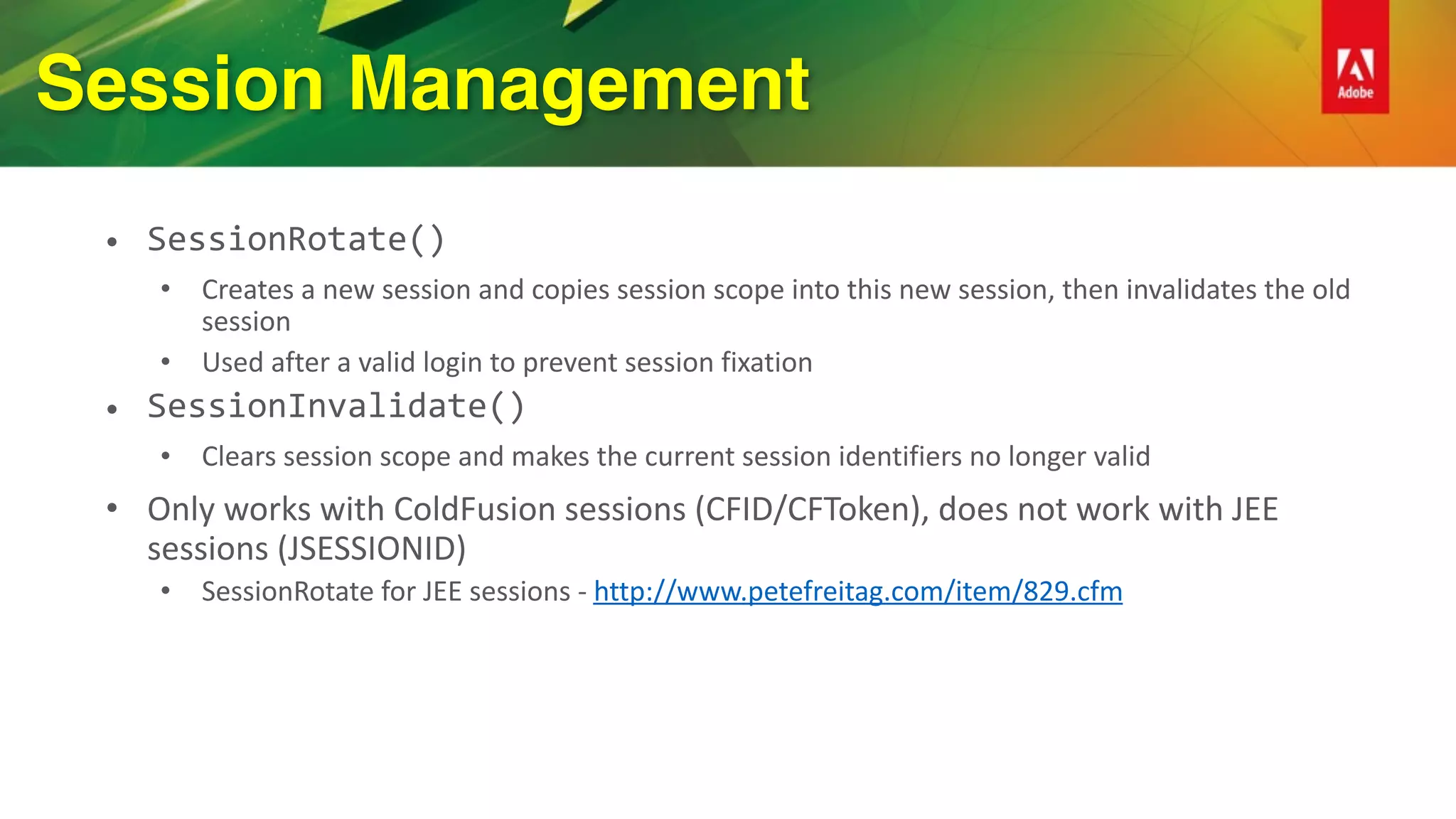
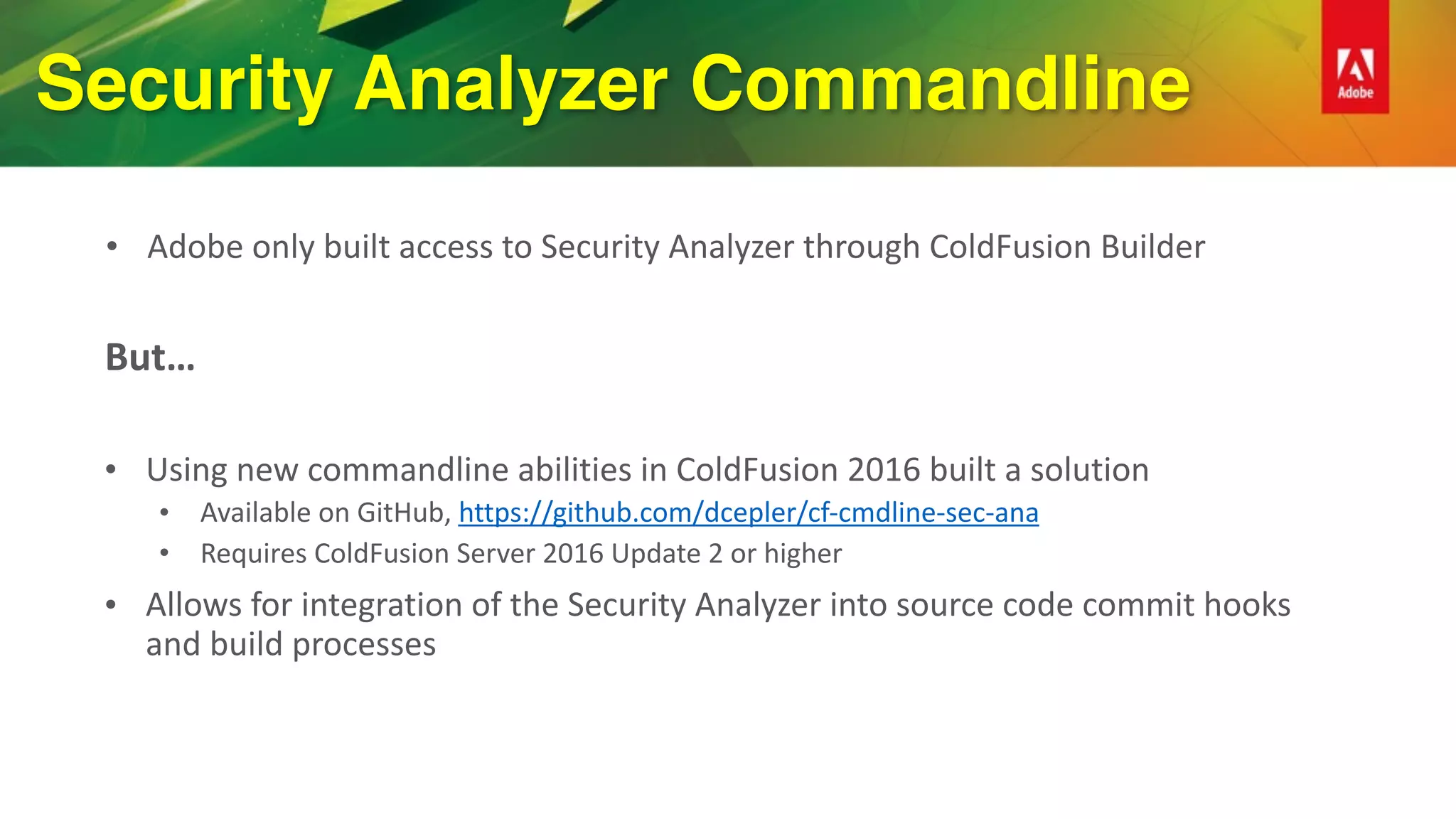
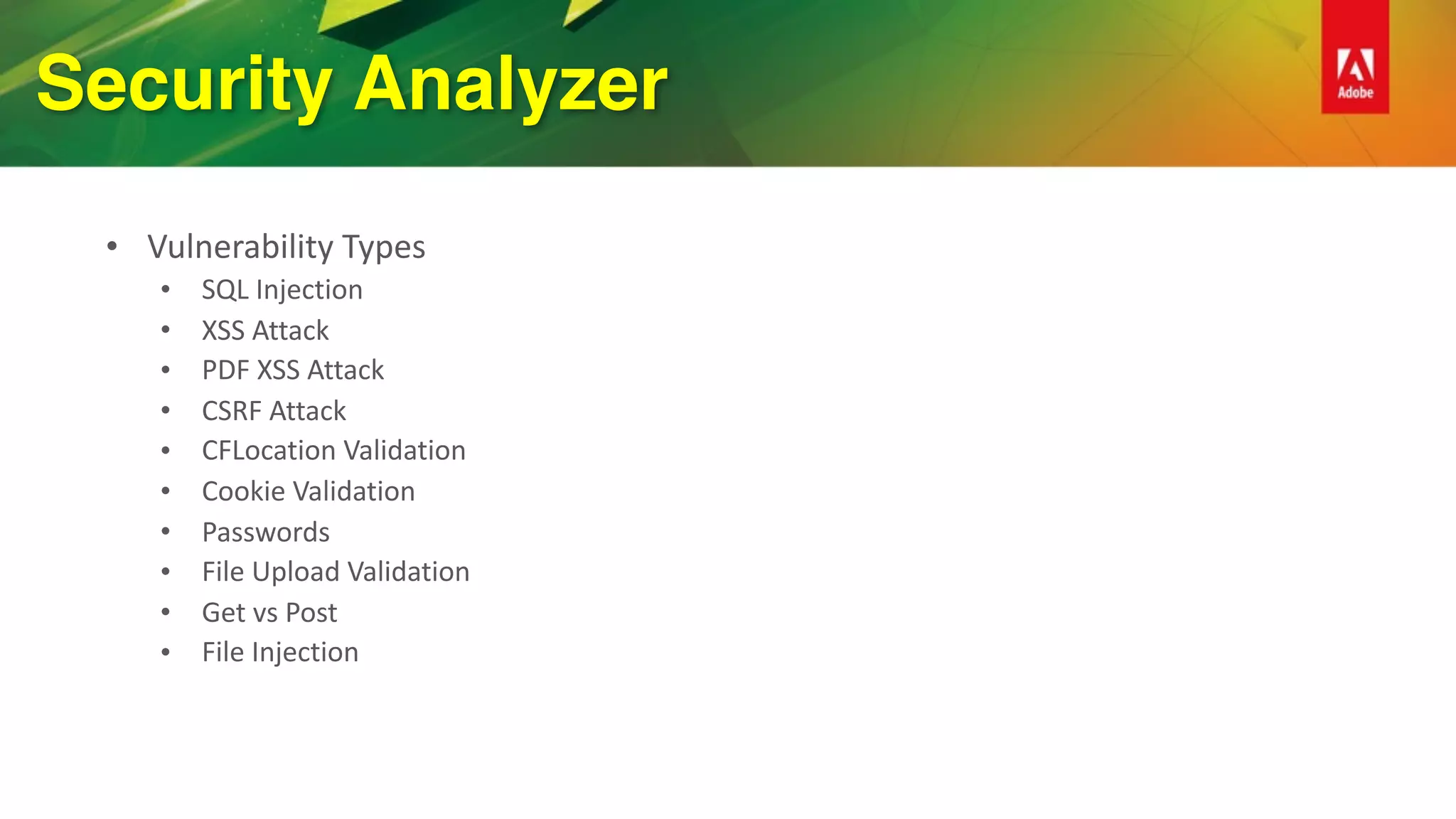
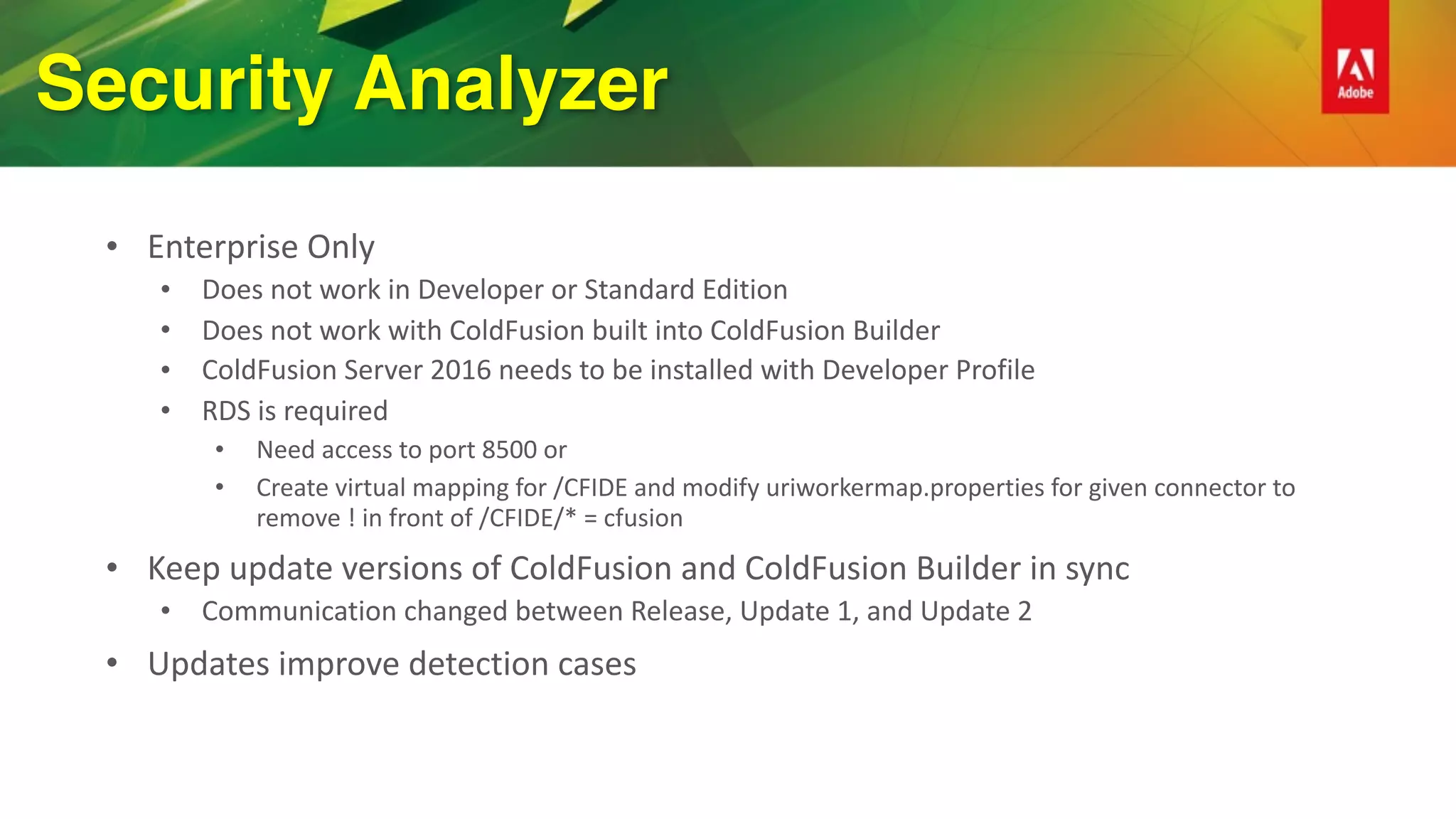
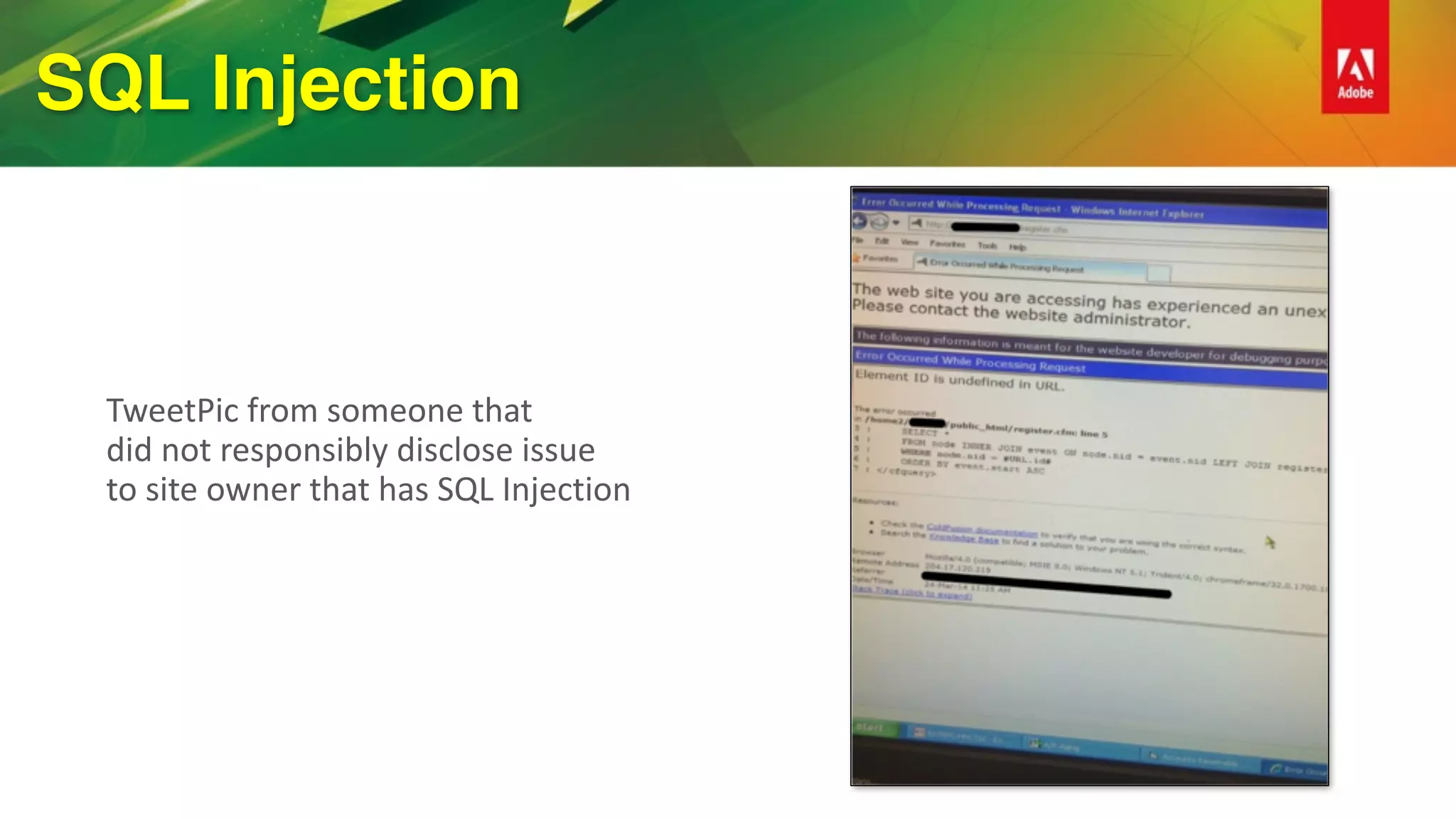
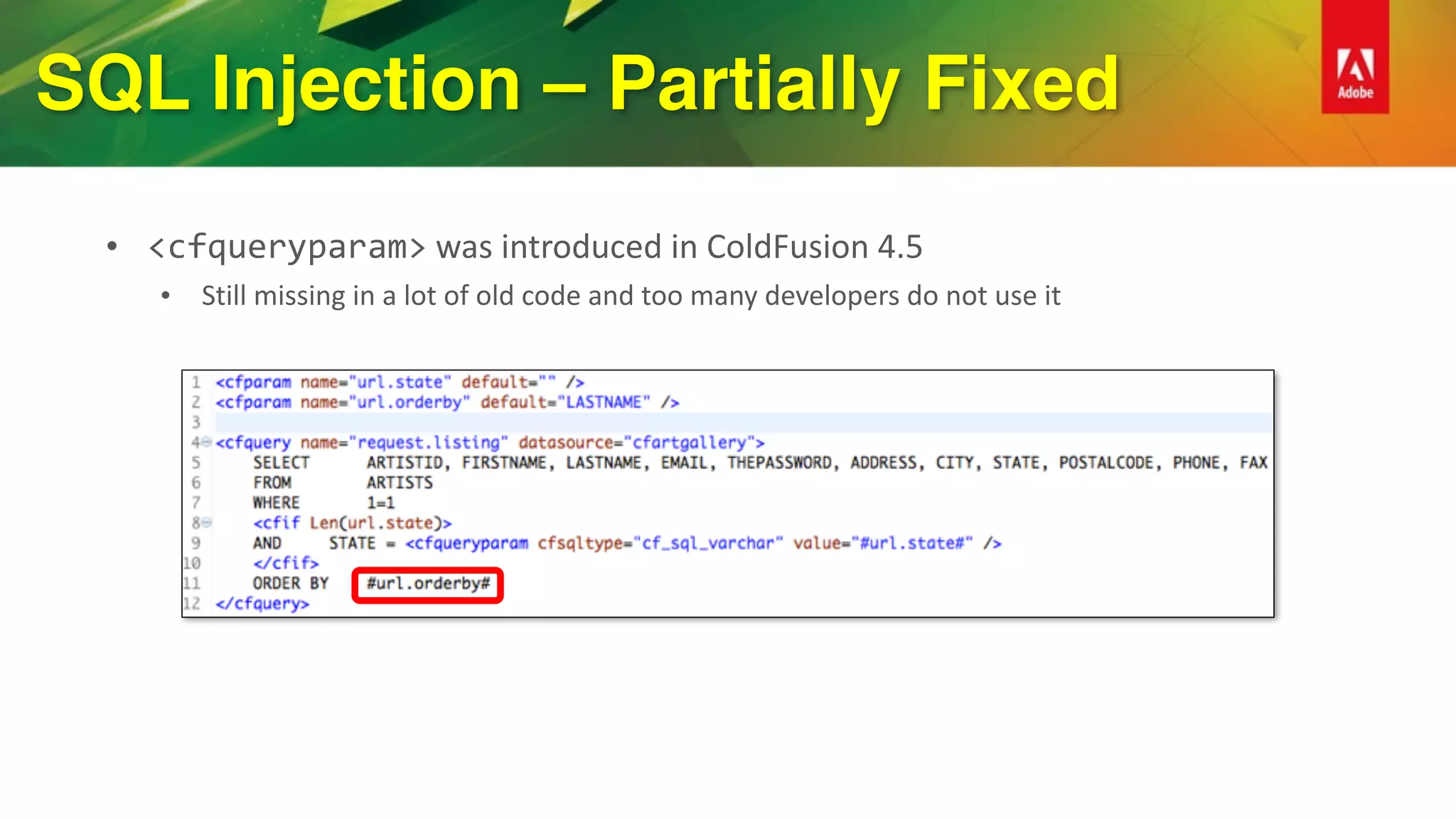
This document provides an overview of how to improve security when using ColdFusion 2016. It discusses installing ColdFusion with the secure profile, following the lockdown guide, applying updates, and using the new Security Analyzer tool. The Security Analyzer checks code for vulnerabilities like SQL injection, XSS, and CSRF. The document also recommends coding practices to avoid vulnerabilities, such as using ESAPI encoders and <cfqueryparam>. Proper session management and preventing attacks like XSS, SQL injection, and CSRF are also discussed.



















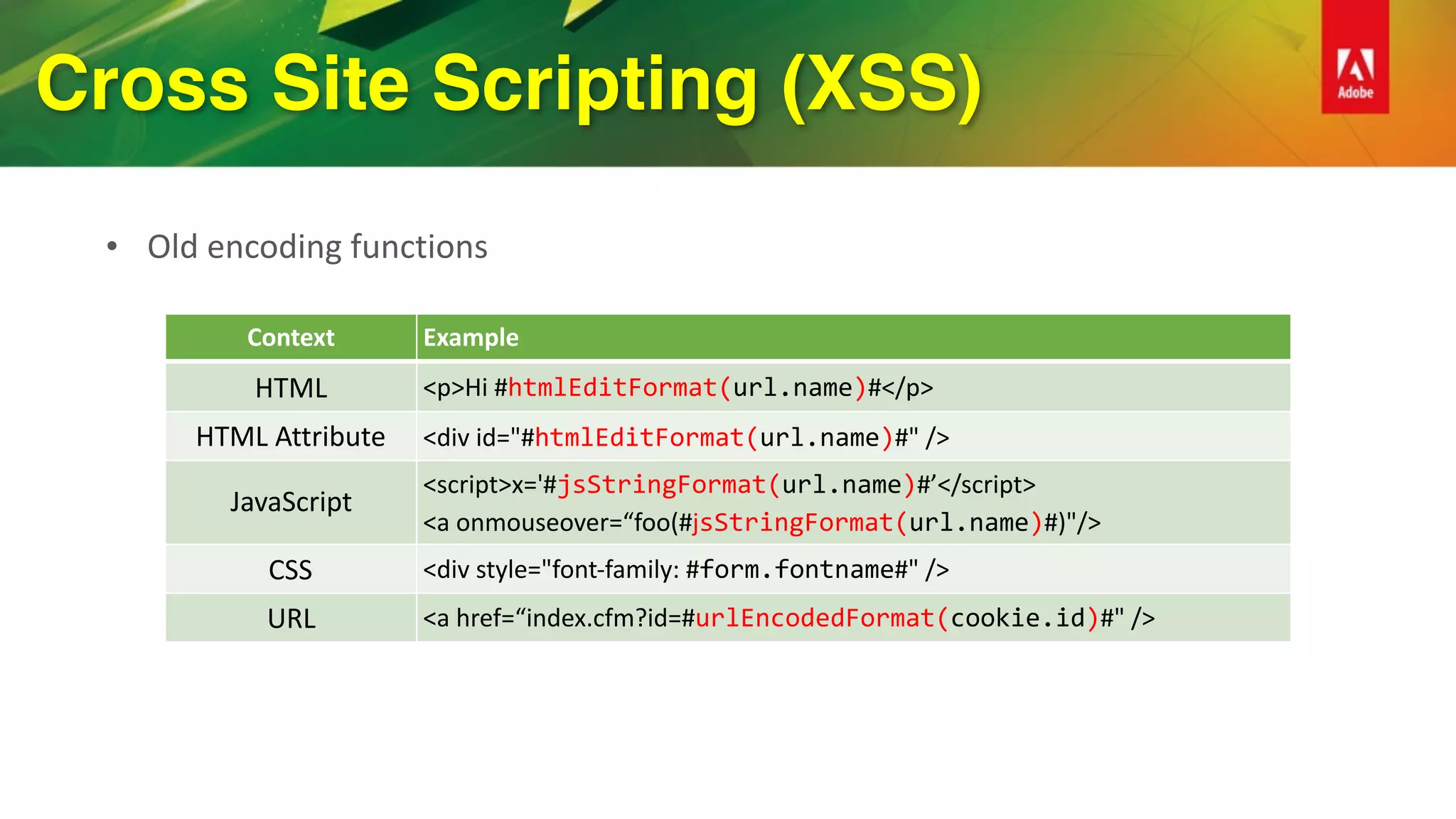

![Cross Site Scripting (XSS)
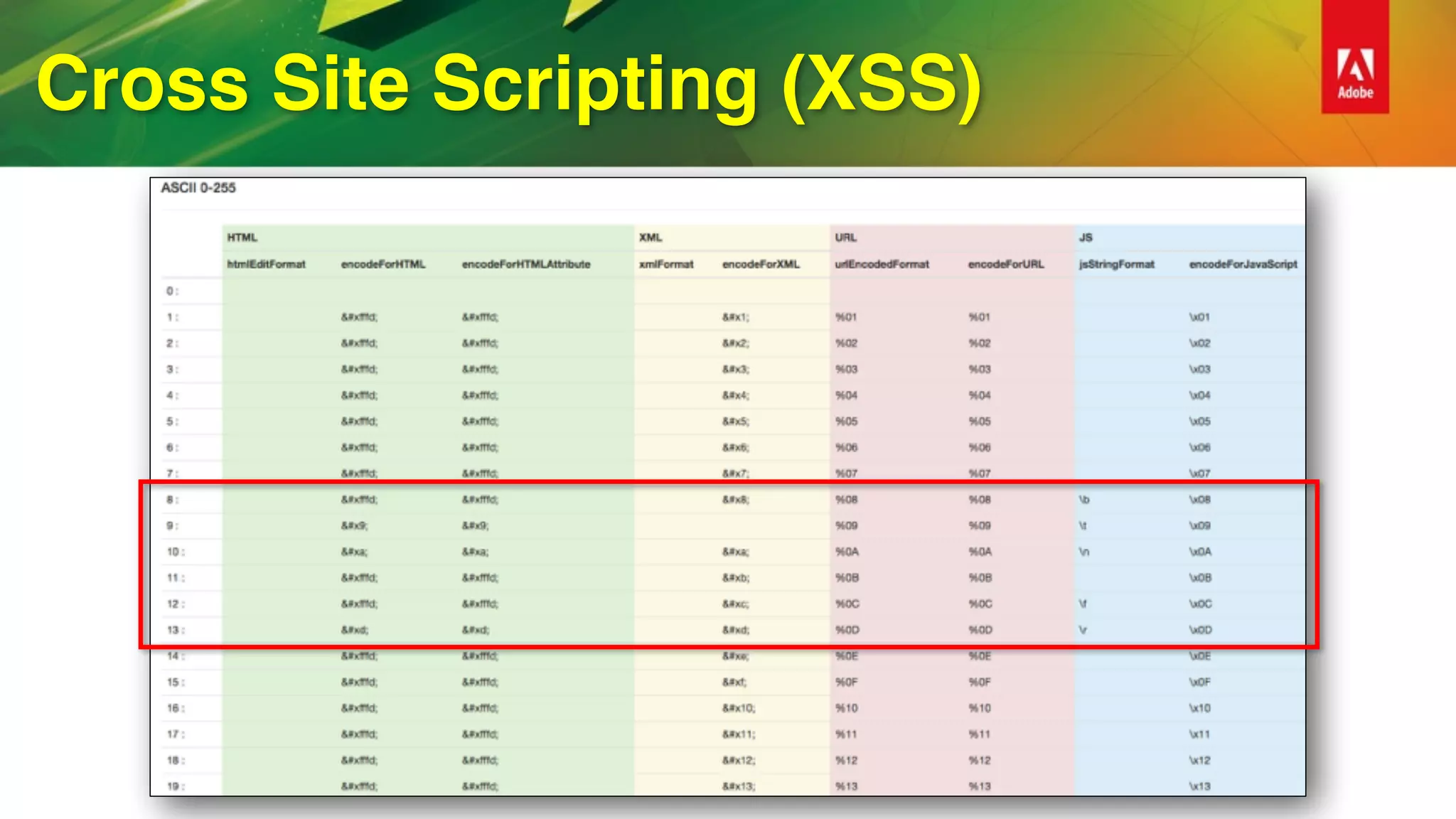
• WYSIWYG HTML editors
• ColdFusion 11 added support HTML Sanitization using OWASP AntiSamy
• isSafeHTML(inputString, [policyFile], [throwOnError])
• getSafeHTML(inputString, [policyFile], [throwOnError])
• ColdFusion’s default policy based on Slashdot policy from project
https://code.google.com/archive/p/owaspantisamy/downloads](https://image.slidesharecdn.com/cf-security-rockstar-161114161235/75/Become-a-Security-Rockstar-with-ColdFusion-2016-27-2048.jpg)




![Cross-site Request Forgery
• Random Token
• CSRFGenerateToken([key], [forceNew])
• Generates a random token and stores it in the session
• CSRFVerifyToken(token, [key])
• Validates the passed in token against the token stored in the session
• Must have session variables enabled](https://image.slidesharecdn.com/cf-security-rockstar-161114161235/75/Become-a-Security-Rockstar-with-ColdFusion-2016-35-2048.jpg)