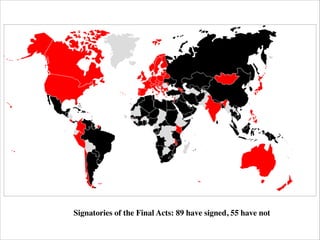
This document discusses the World Conference on International Telecommunications (WCIT-12) that took place in December 2012 in Dubai. It provides background information on the International Telecommunication Union (ITU), its sectors and conferences. It summarizes the key outcomes of WCIT-12, including amendments made to the International Telecommunication Regulations (ITRs) for the first time since 1988 relating to issues like network security, unsolicited communications, and access to telecommunication services.