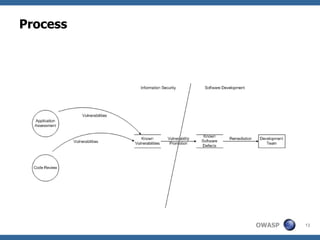
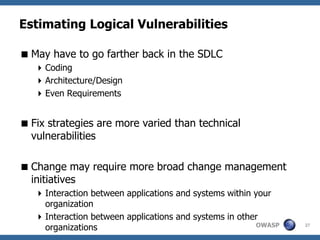
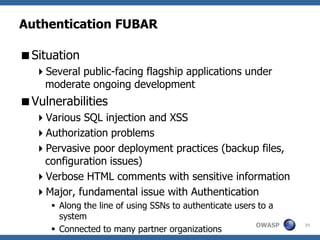
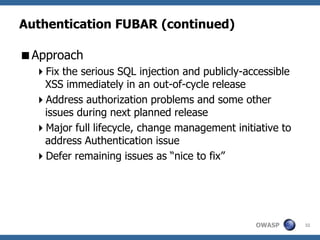
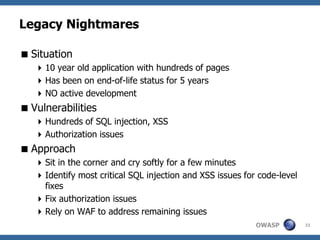
This document provides a summary of a presentation on vulnerability management in application security. It discusses how application vulnerabilities should be treated as software defects and tracked in a defect management system. It also covers how to prioritize vulnerabilities based on a risk calculation considering likelihood, impact, and remediation effort. The presentation provides examples of different vulnerability management challenges and recommendations for improving policies, baselines, prioritization, remediation, and ongoing maintenance of applications.