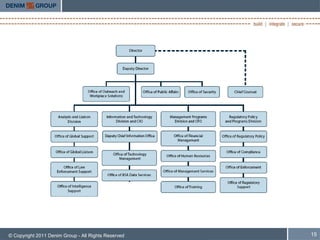
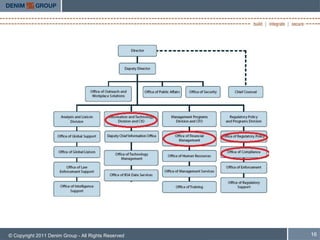
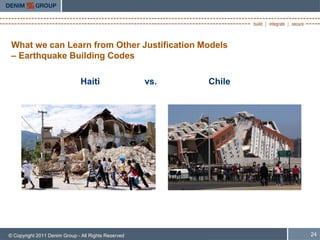
The document discusses whether "OK" is good enough for software security. It covers the current state of software security testing, including limitations of automated scanners. It analyzes justification models from other industries like earthquake building codes. Finally, it proposes some potential models for improving software security justifications, such as tailoring responses based on limited resources and prioritizing elimination of common vulnerabilities.