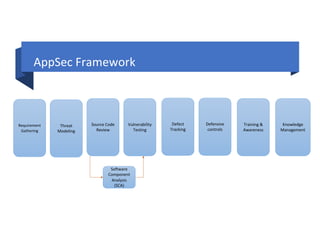
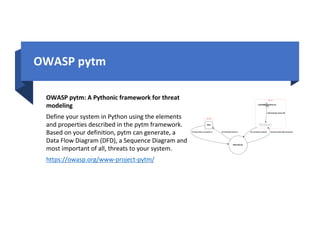
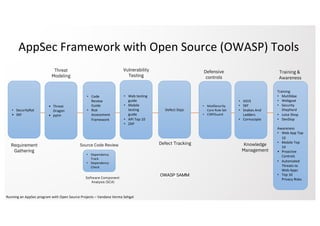
This document outlines how to run an application security (AppSec) program using various open source tools from the Open Web Application Security Project (OWASP). It discusses tools for requirements gathering, threat modeling, source code review, vulnerability testing, defect tracking, defensive controls, training and awareness, and knowledge management. Many of the tools are linked, including the OWASP Security Knowledge Framework, Dependency Check, ModSecurity Core Rule Set, Juice Shop, DevSlop, the OWASP Top 10, and the OWASP Testing guides. The document provides an open source framework for implementing an AppSec program.