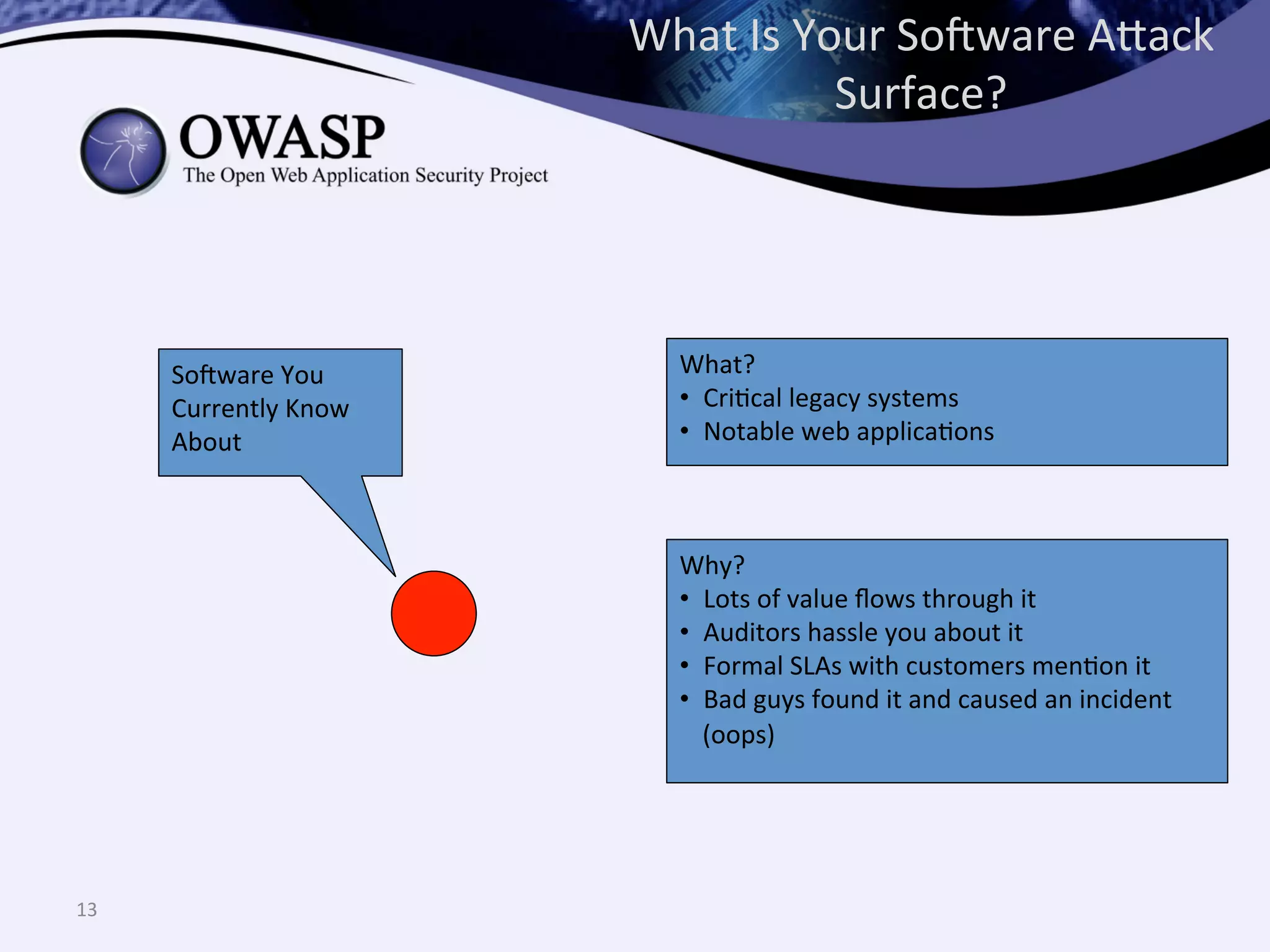
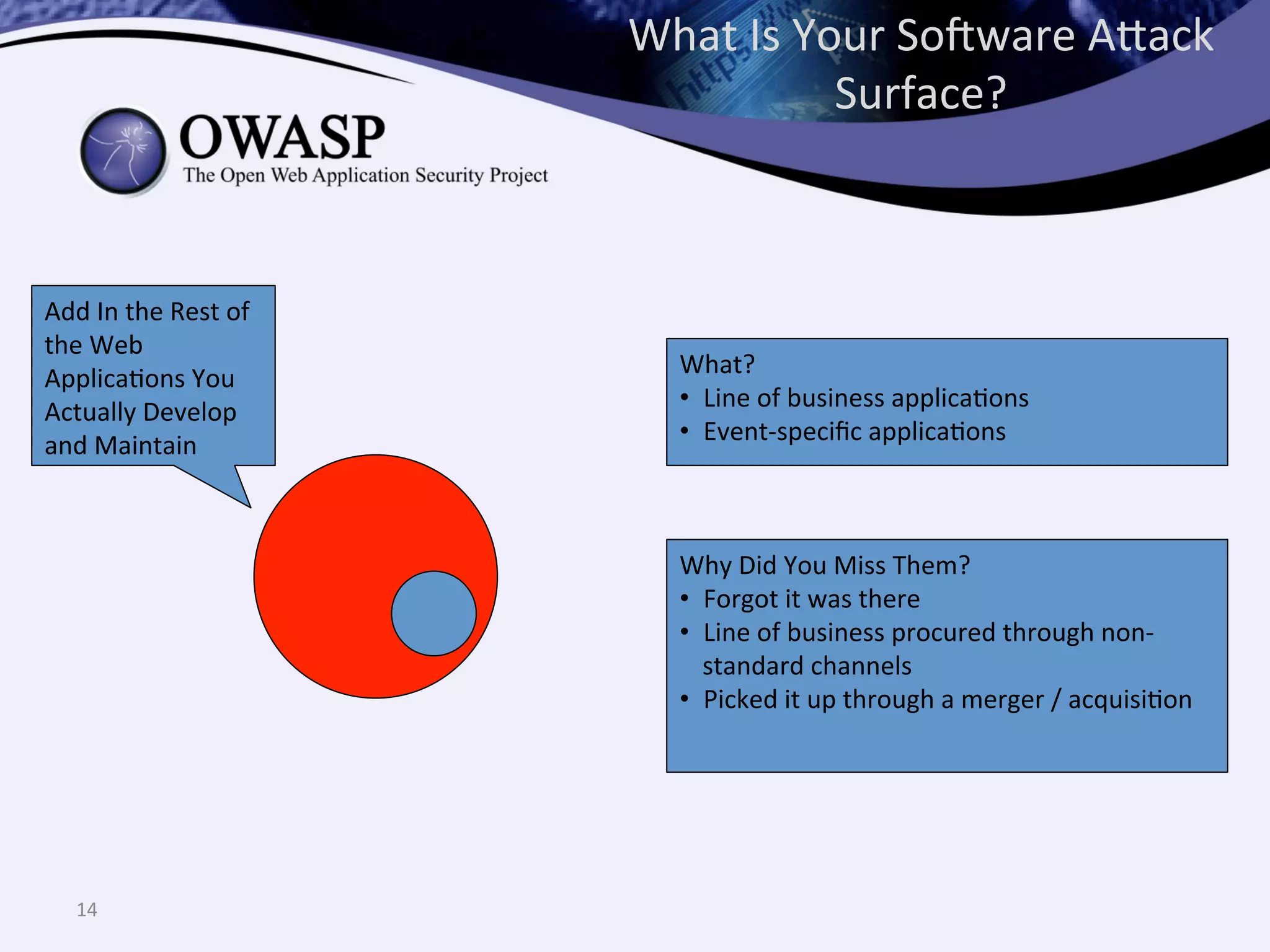
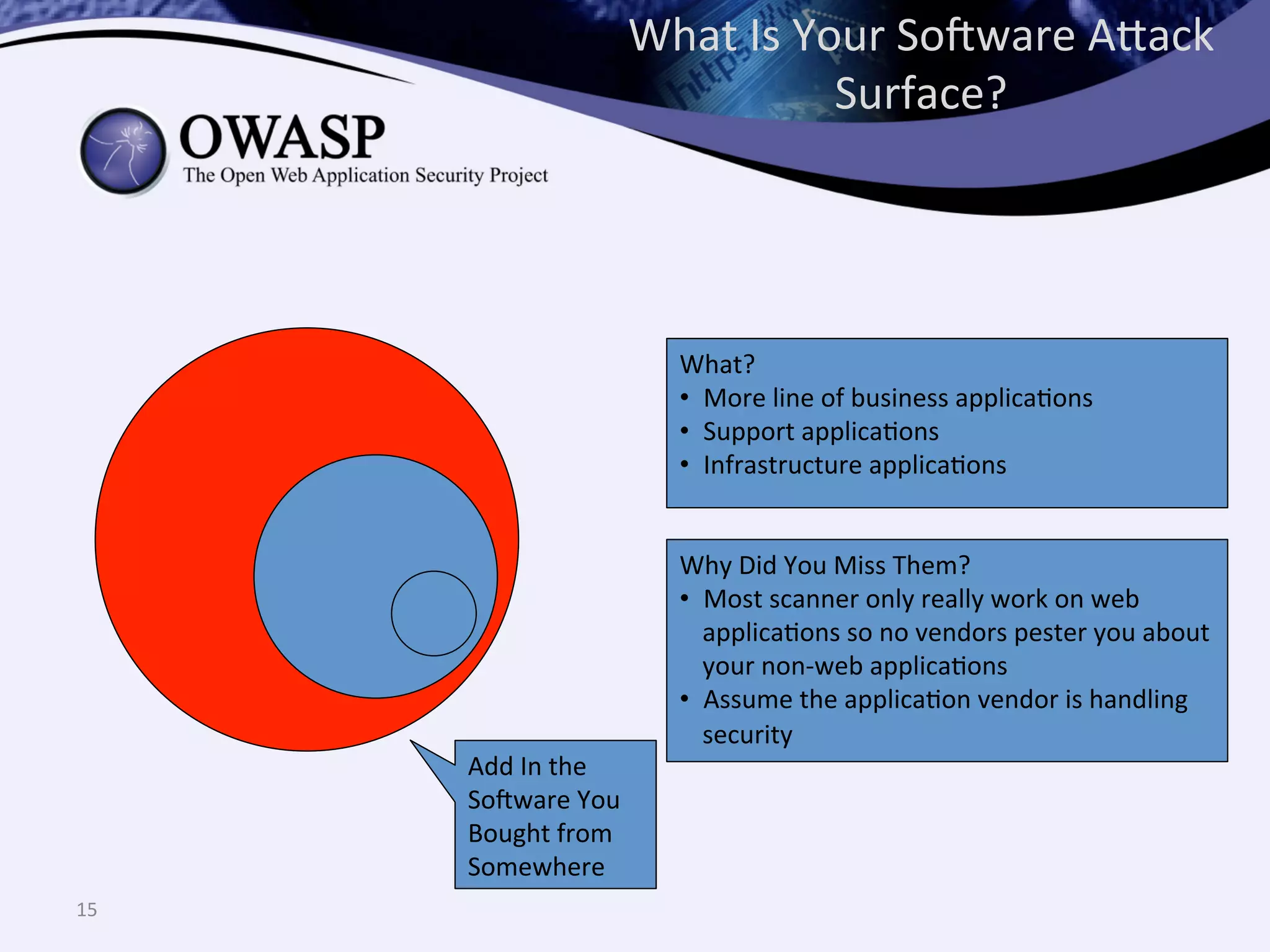
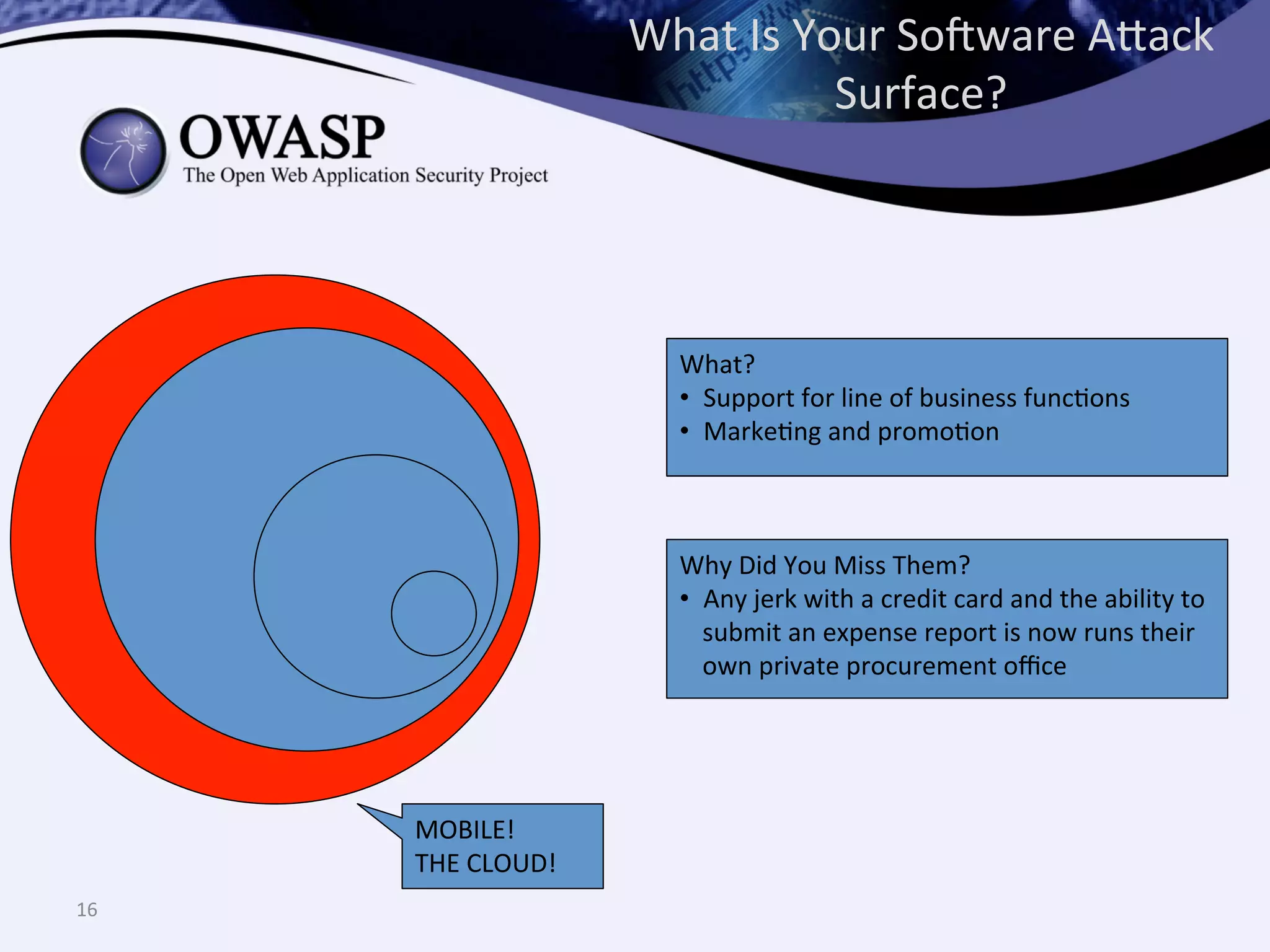
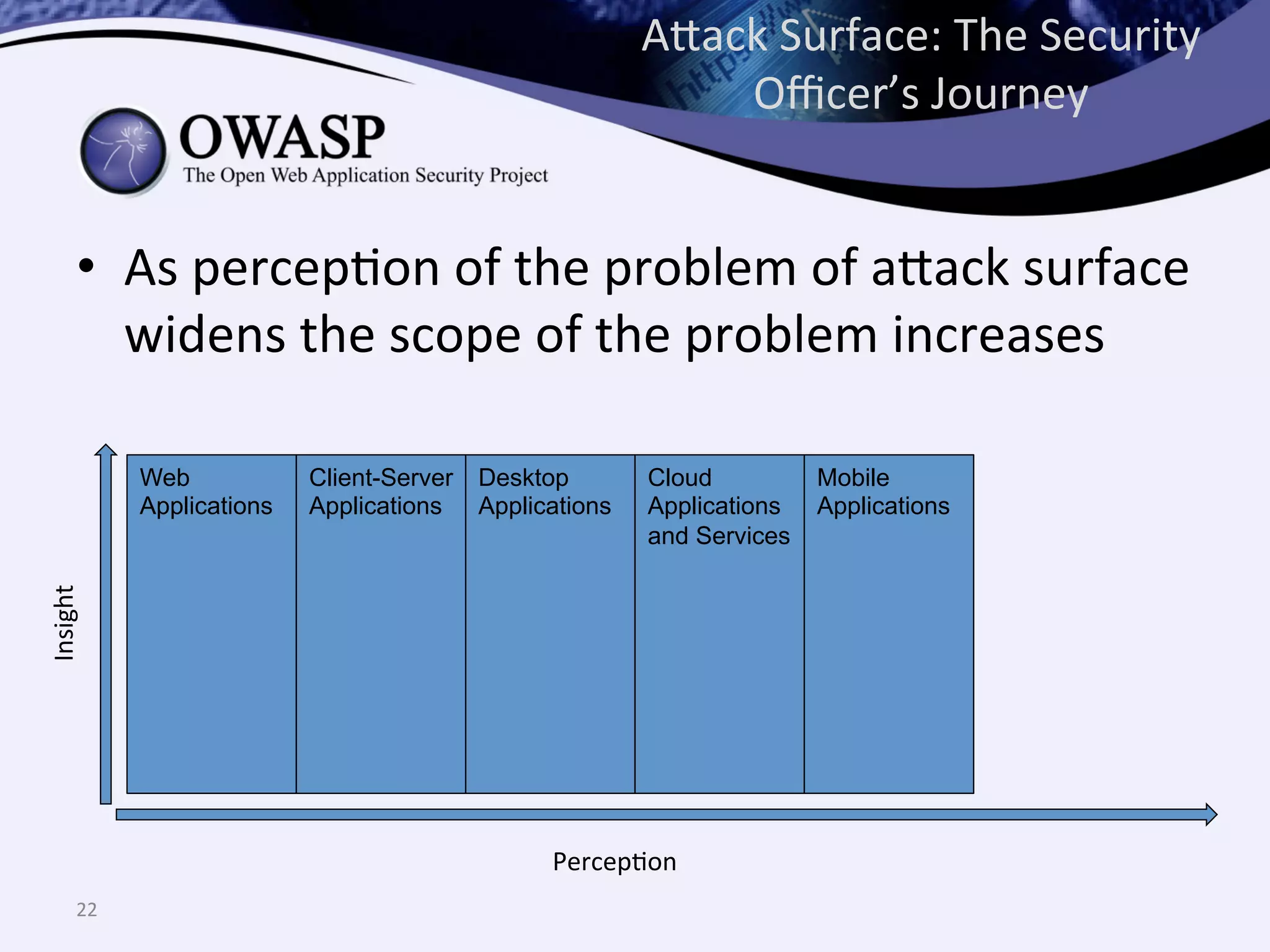
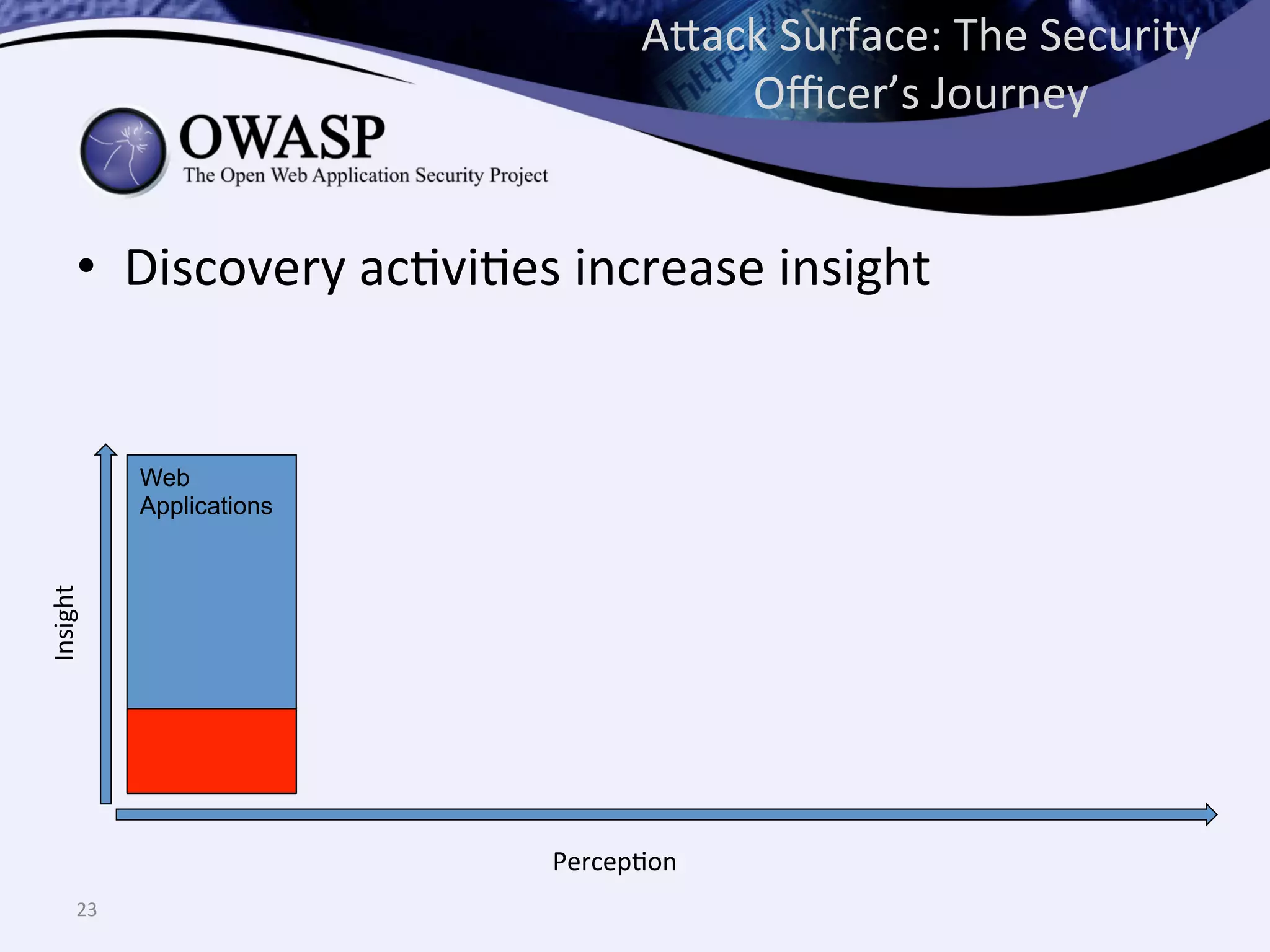
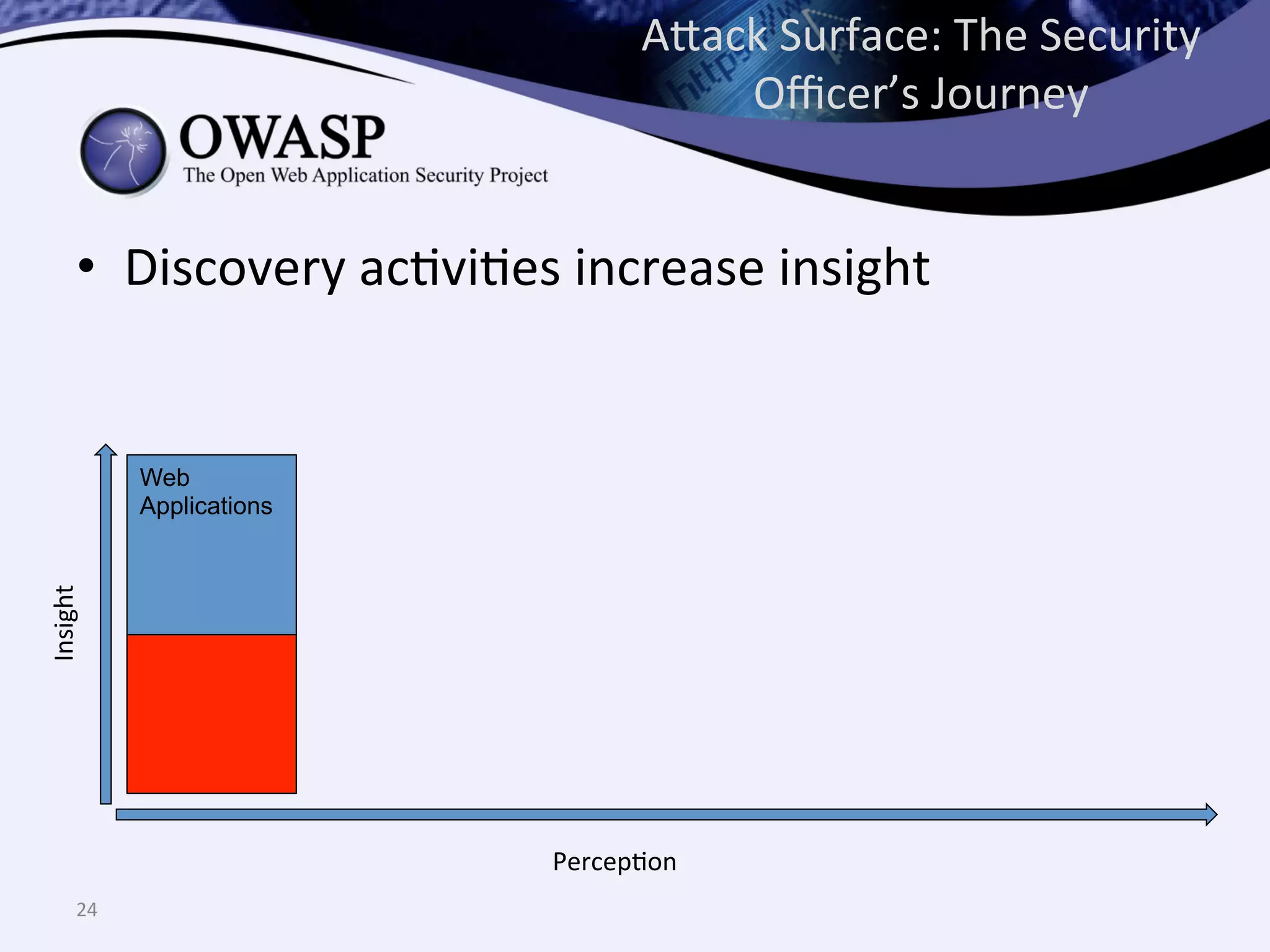
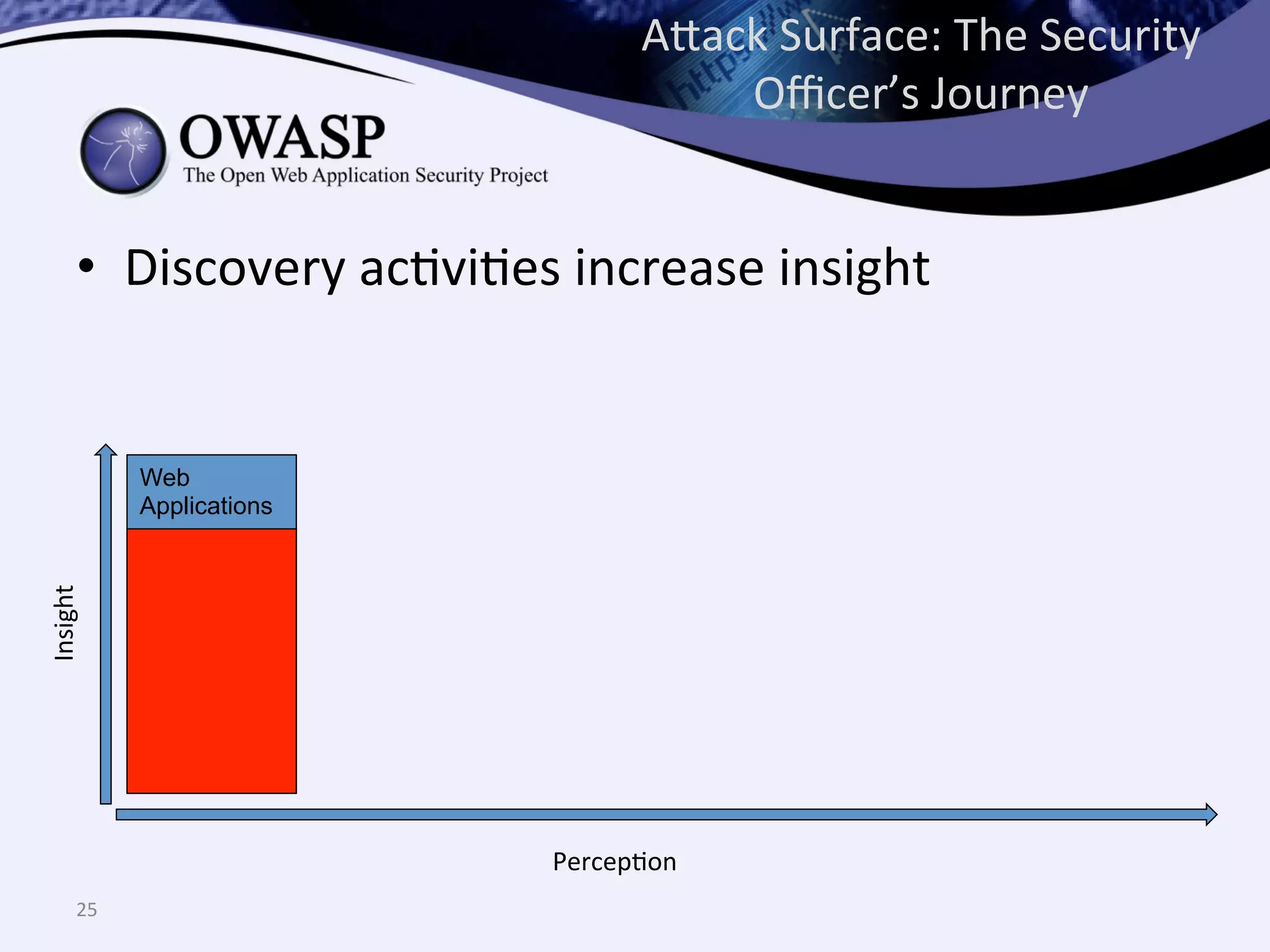
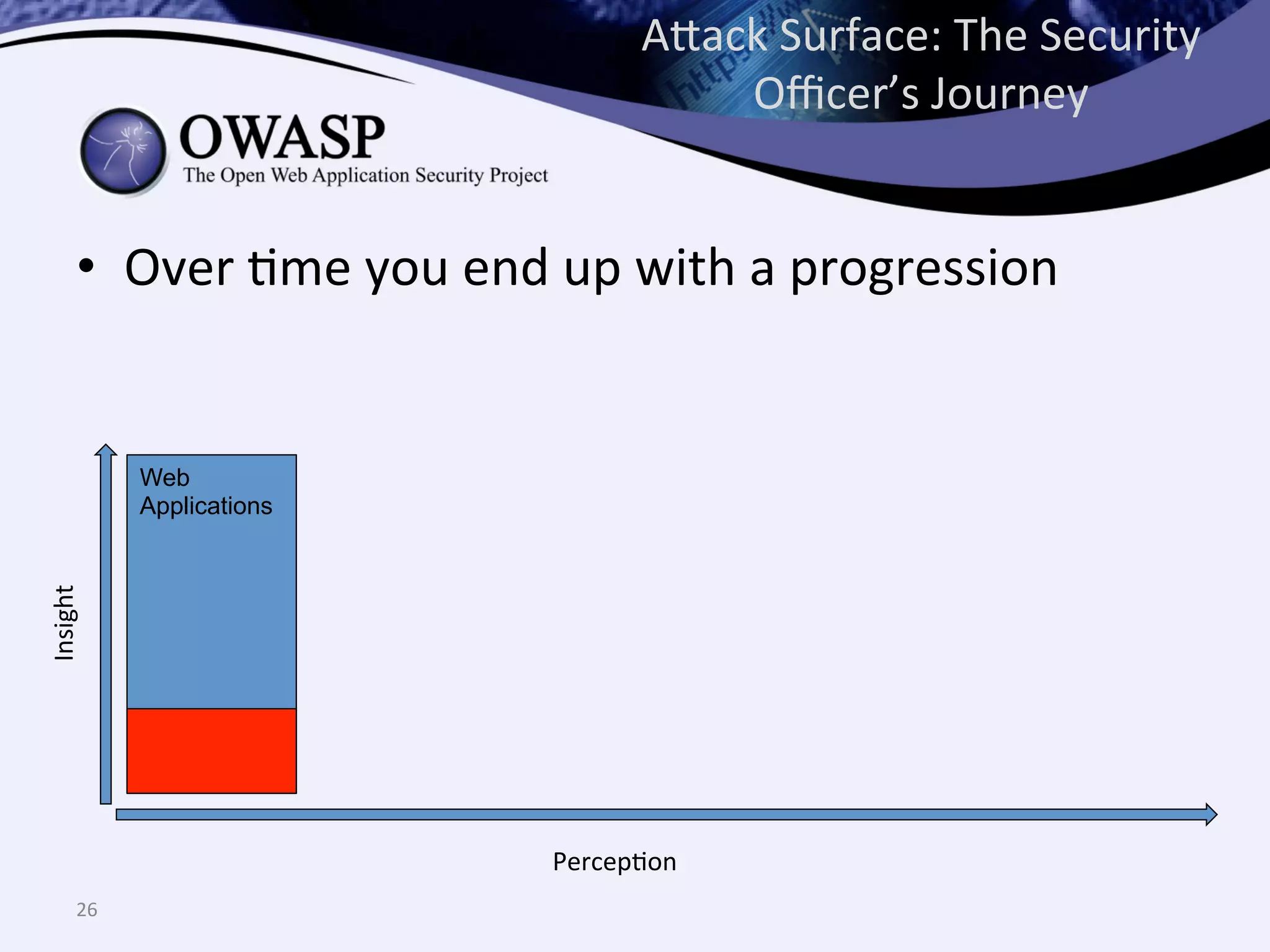
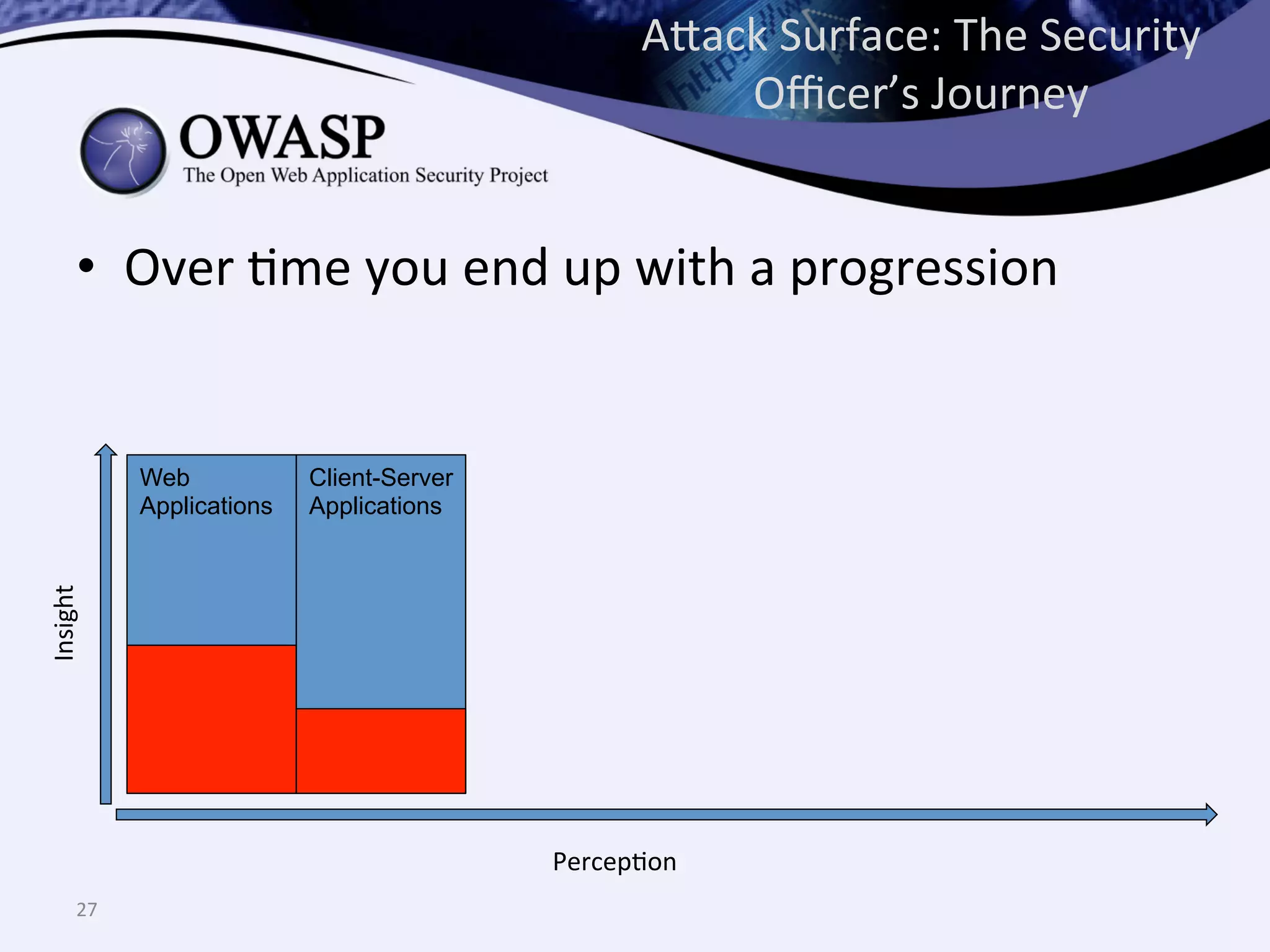
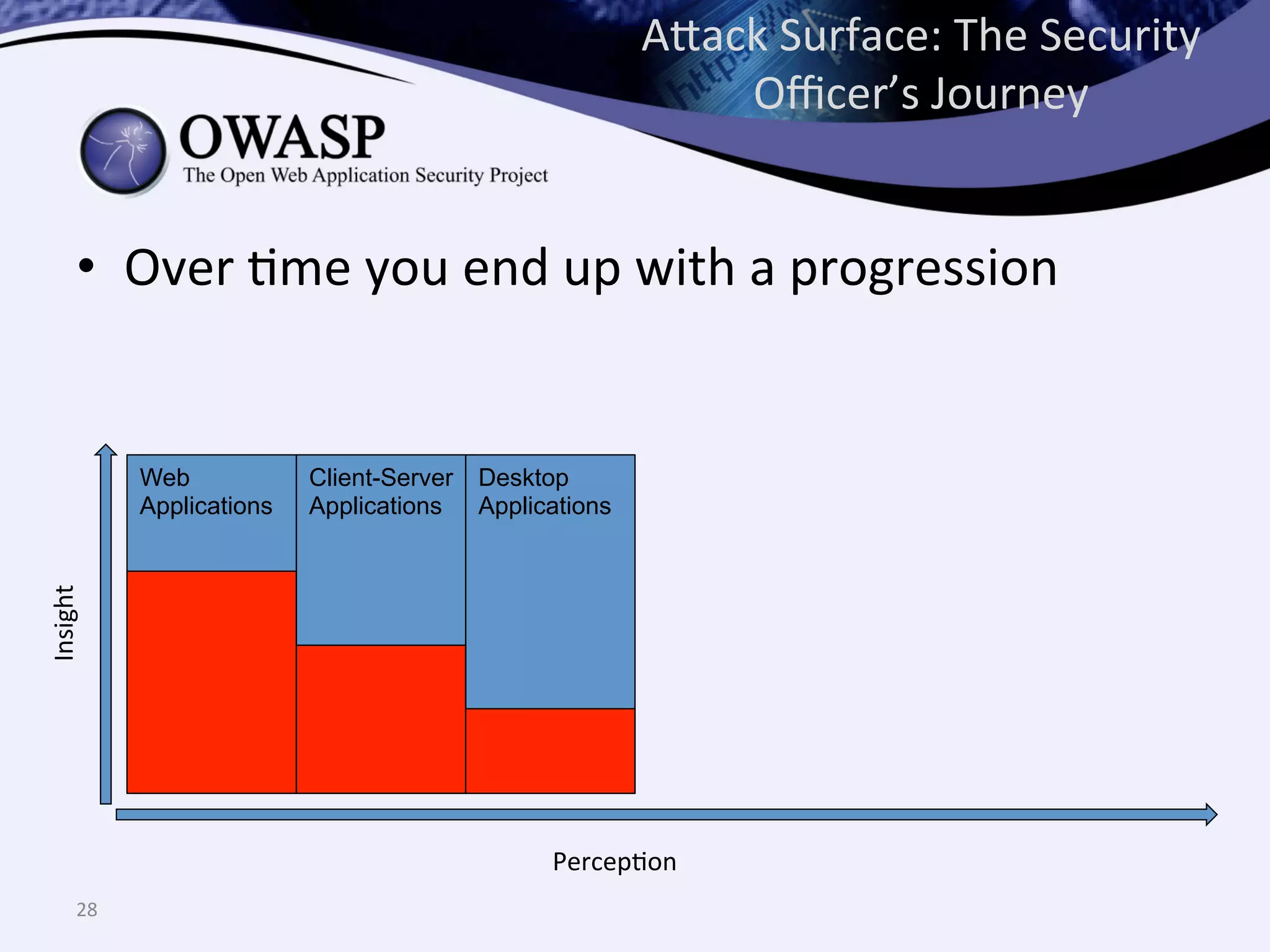
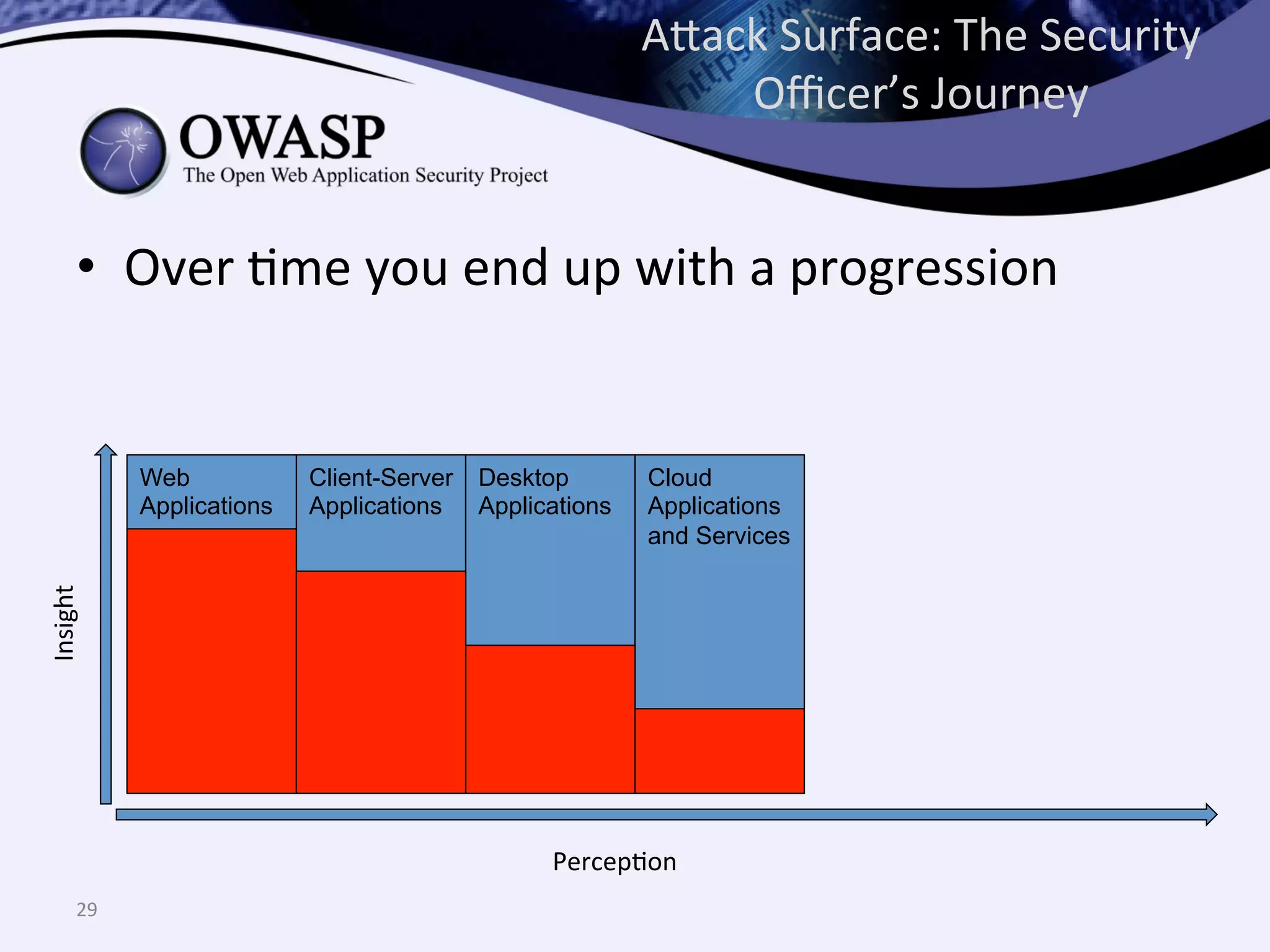
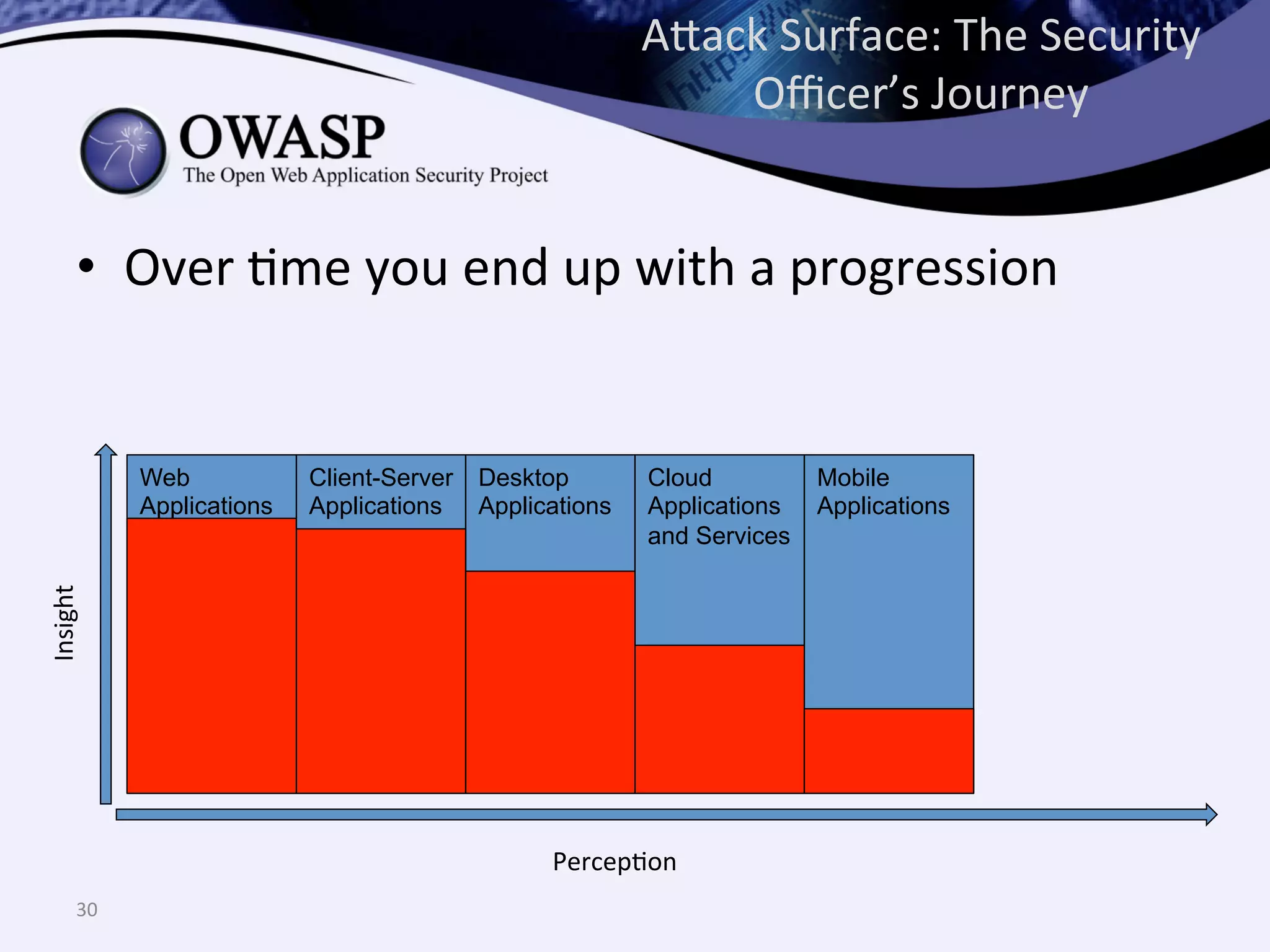
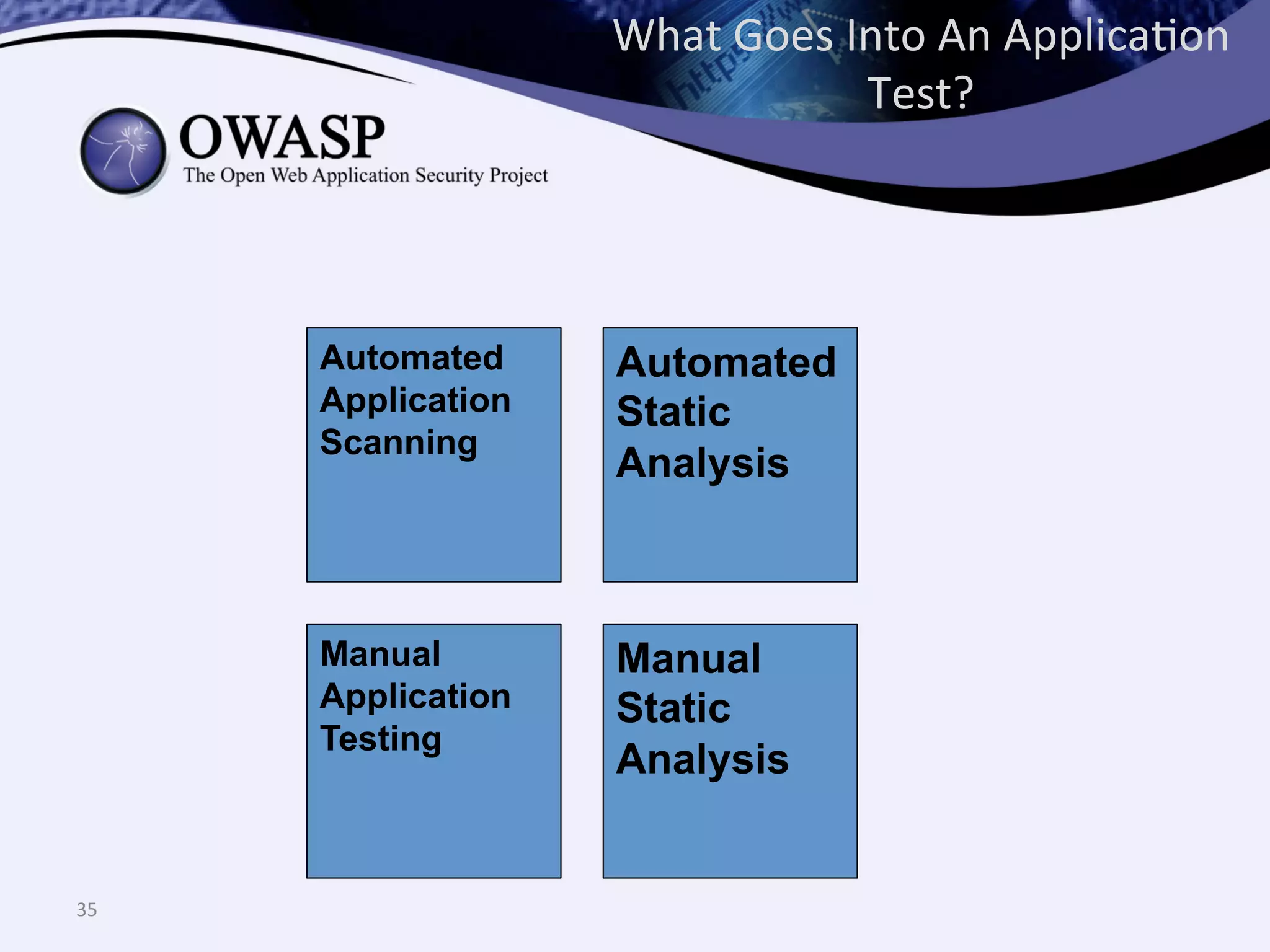
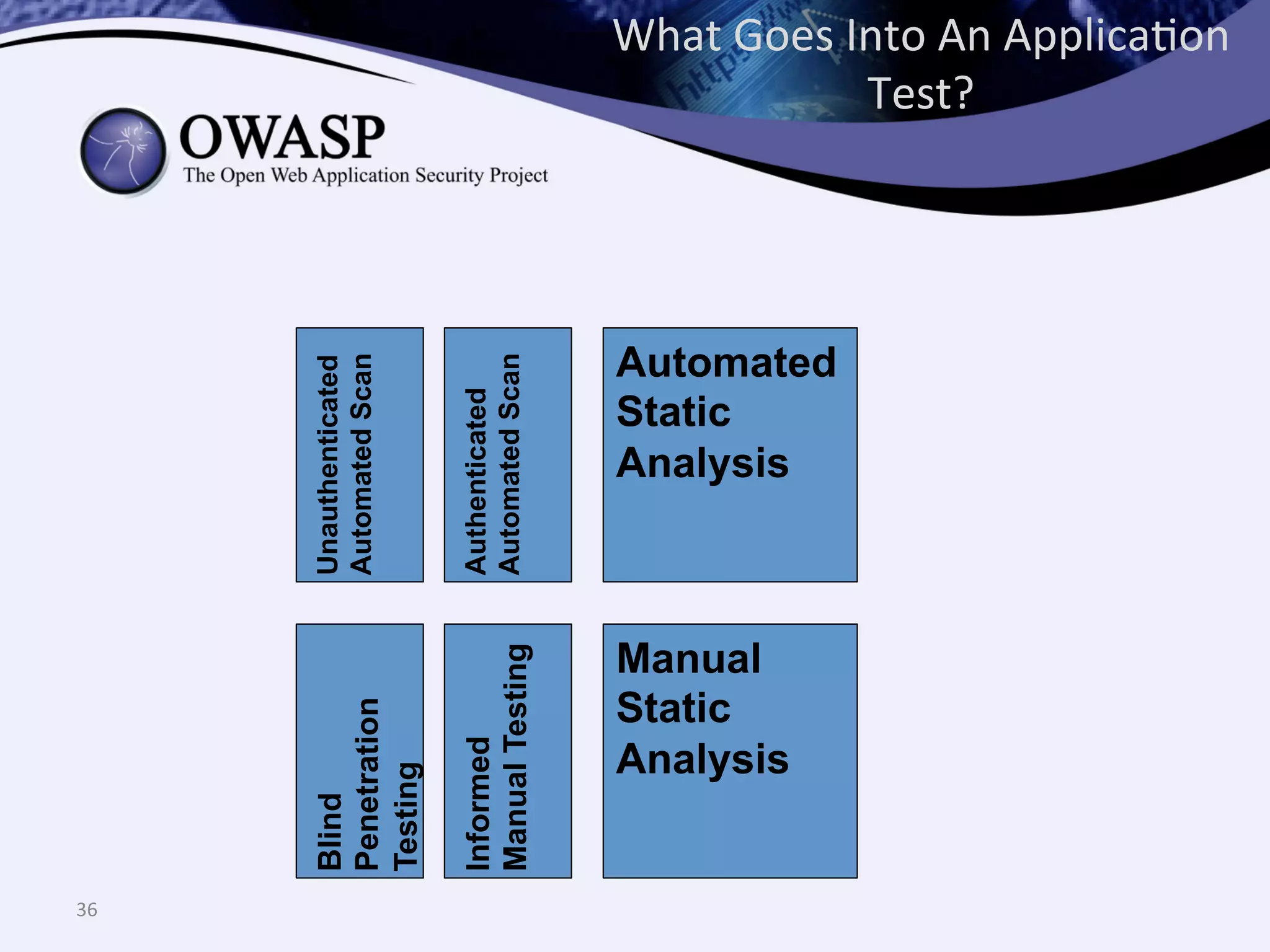
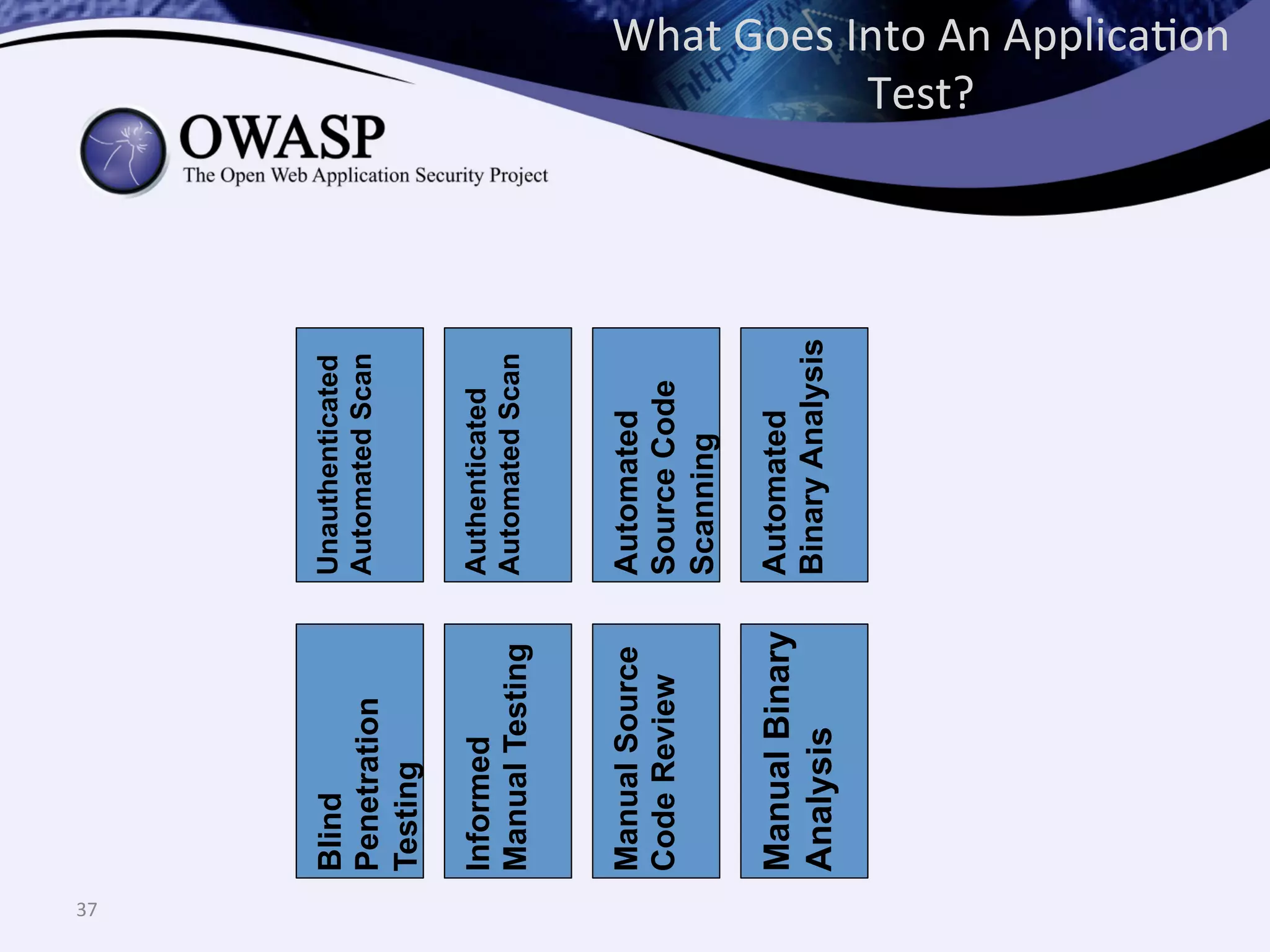
The document discusses the importance of automated scanning in software security, emphasizing its role in reducing risks and improving software security programs. It outlines common practices, metrics, and patterns for effective scanning programs, highlighting the need for a tailored approach that considers the attack surface of an organization. Additionally, it introduces ThreadFix, a free platform for vulnerability management that aids in the remediation of software vulnerabilities and enhances communication among development, security, and QA teams.






![What
Part
Does
Scanning
Play?
• OpenSAMM
-‐
Automated
scanning
is
part
of
both
the
“Security
TesQng”
and
“Code
Review”
Security
PracQces
within
the
VerificaQon
Business
FuncQon
– Dynamic
scanning
and
staQc
scanning,
respecQvely
• Common
starQng
point
for
many
organizaQons
embarking
on
so@ware
security
programs
– There
are
lots
of
commercial
and
freely
available
products
that
can
be
used
in
support
of
this
acQvity
RED
FLAG:
Q:
What
are
you
doing
for
so:ware
security?
A:
We
bought
[Vendor
Scanner
XYZ]
***
BEWARE
FOSTERING
A
CHECKBOX
CULTURE
***
7](https://image.slidesharecdn.com/scannerorscanningprogramappseceu-130825140910-phpapp02/75/Do-You-Have-a-Scanner-or-Do-You-Have-a-Scanning-Program-AppSecEU-2013-7-2048.jpg)