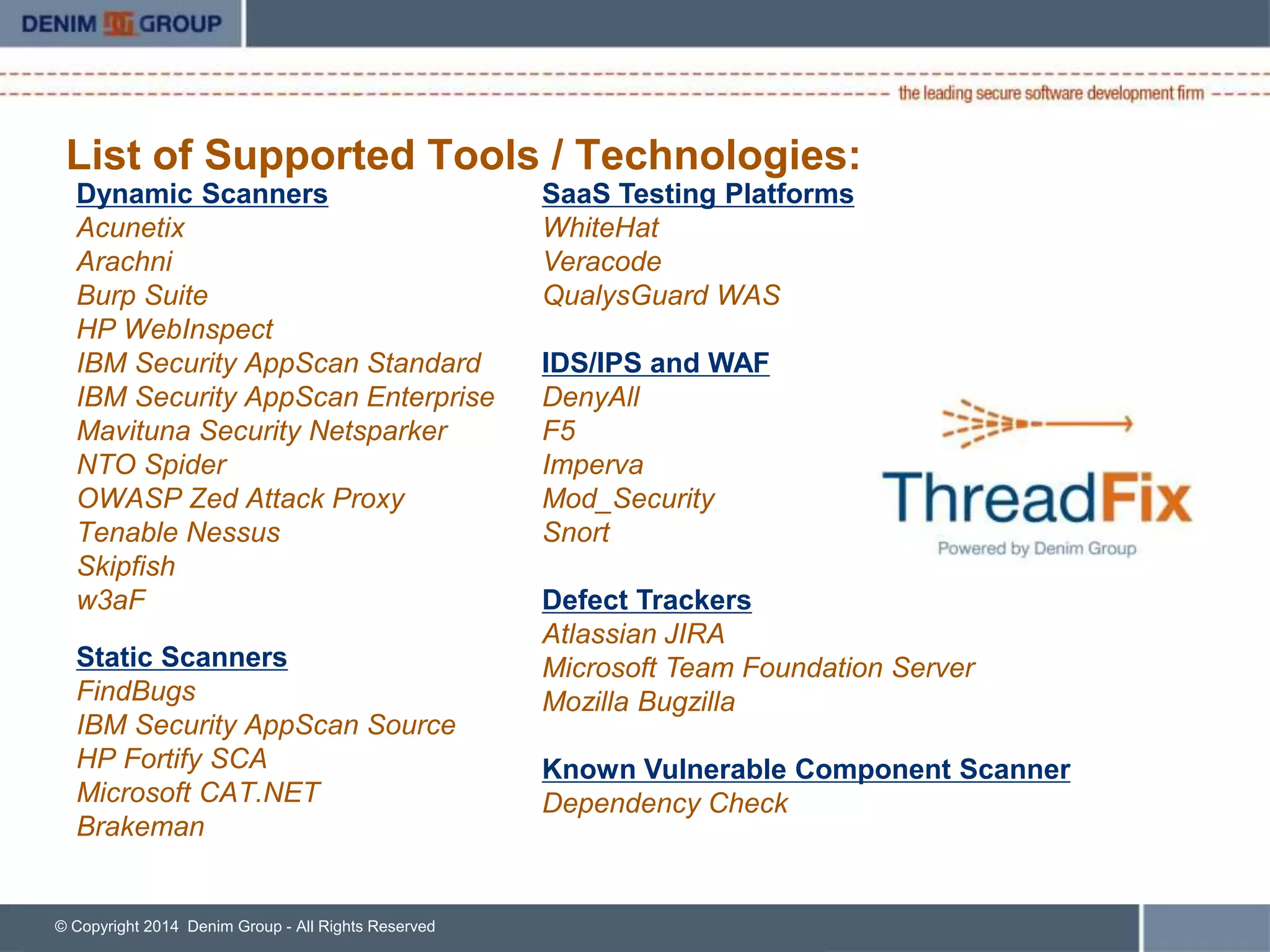
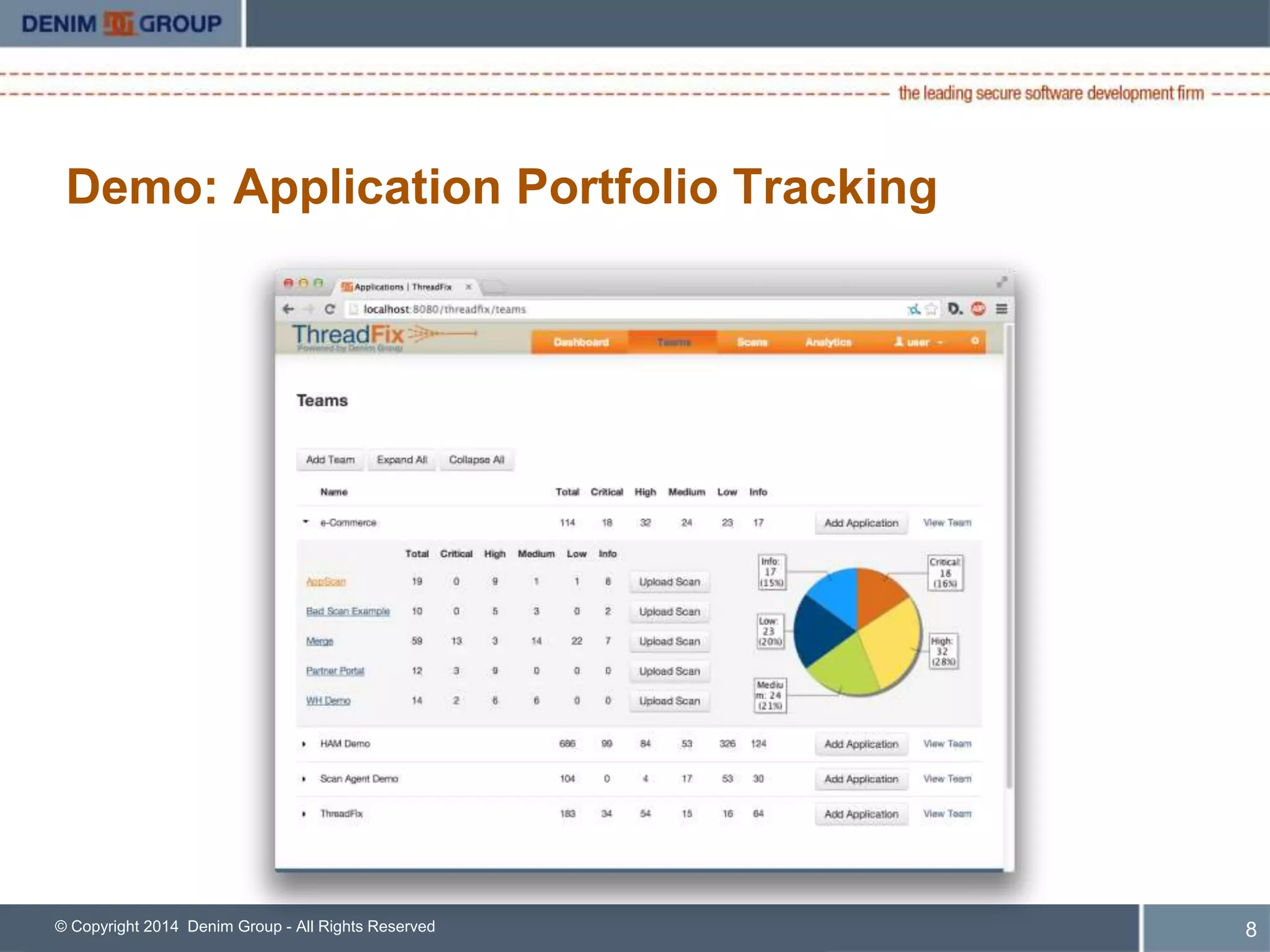
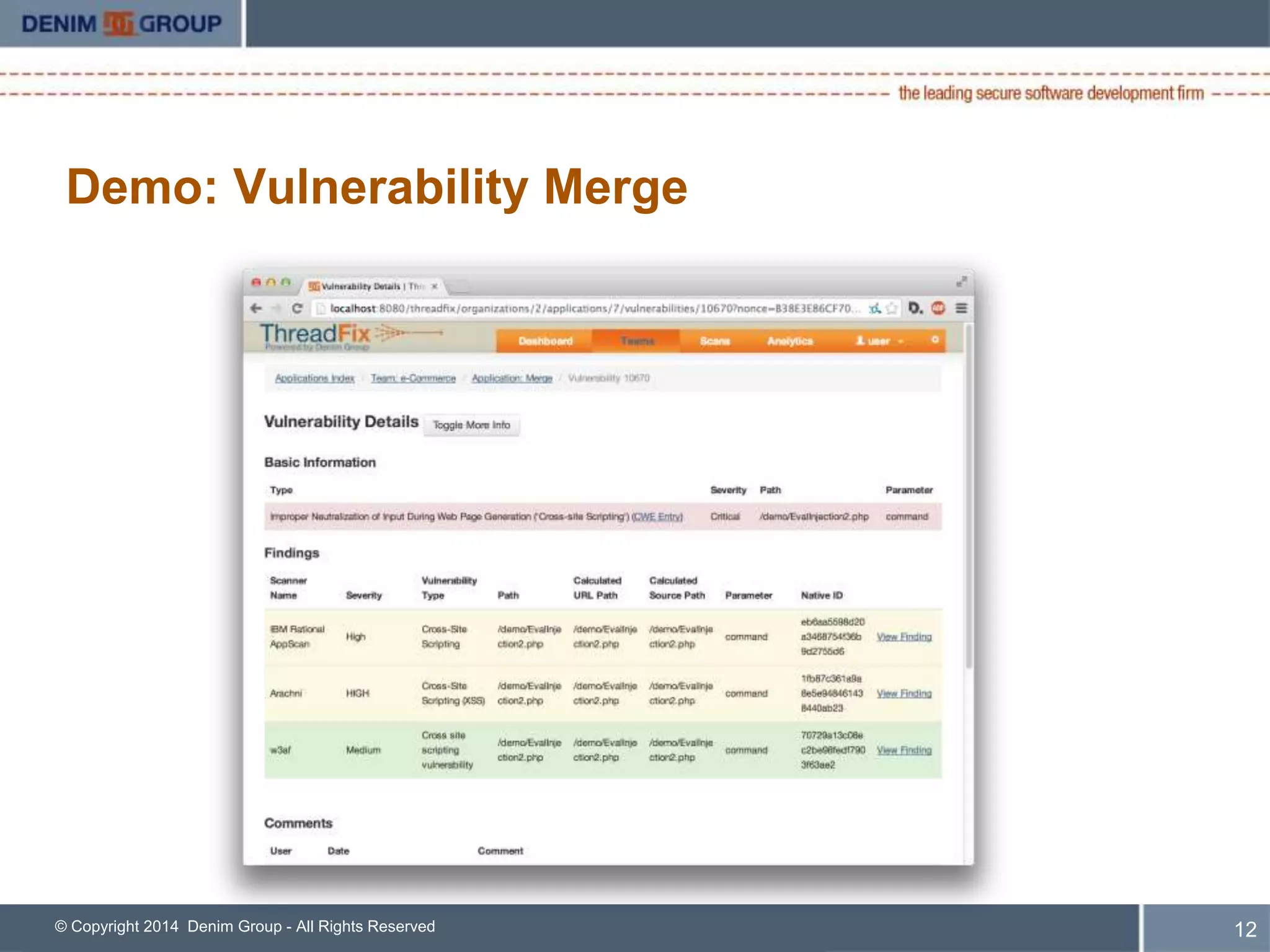
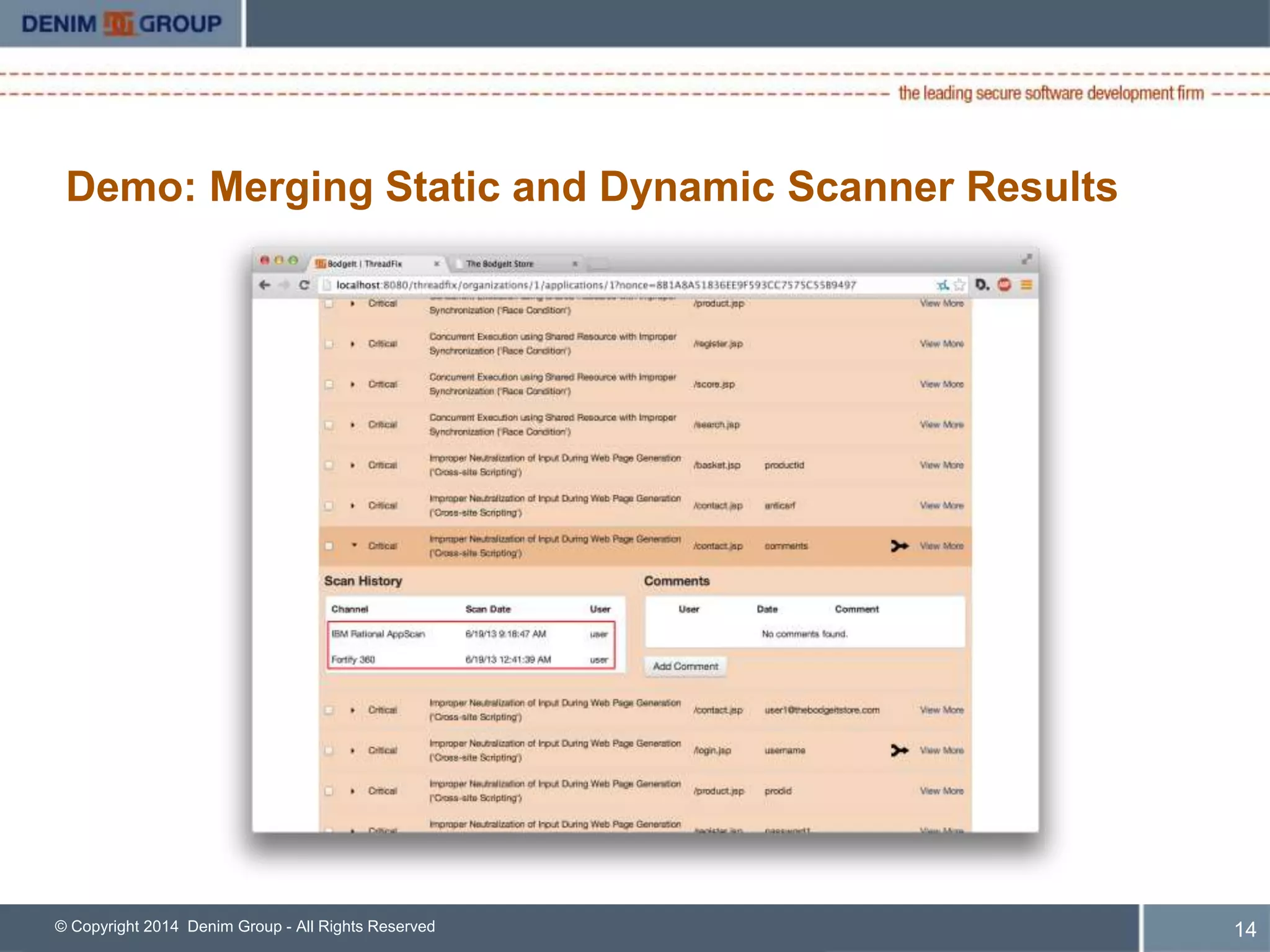
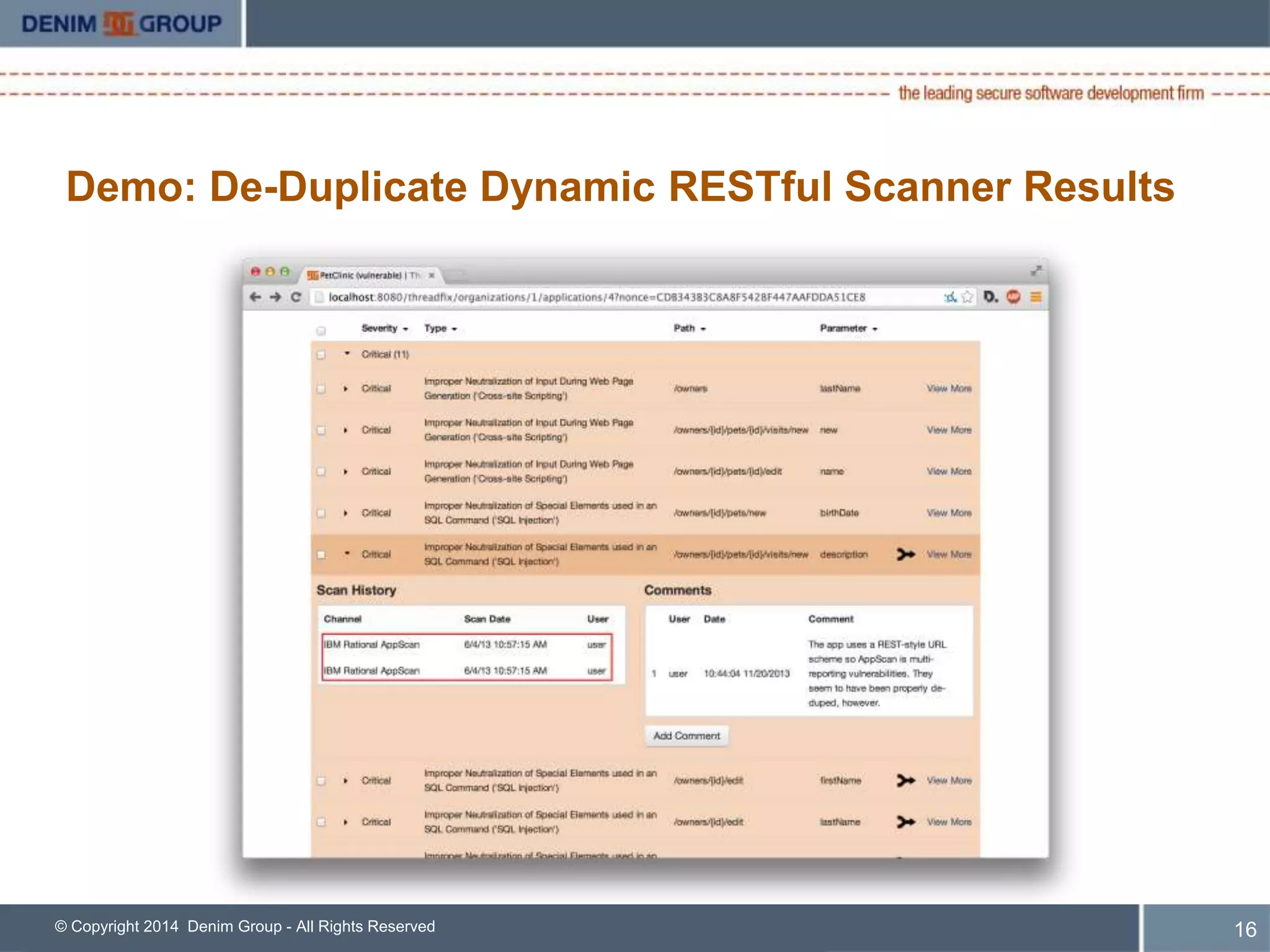
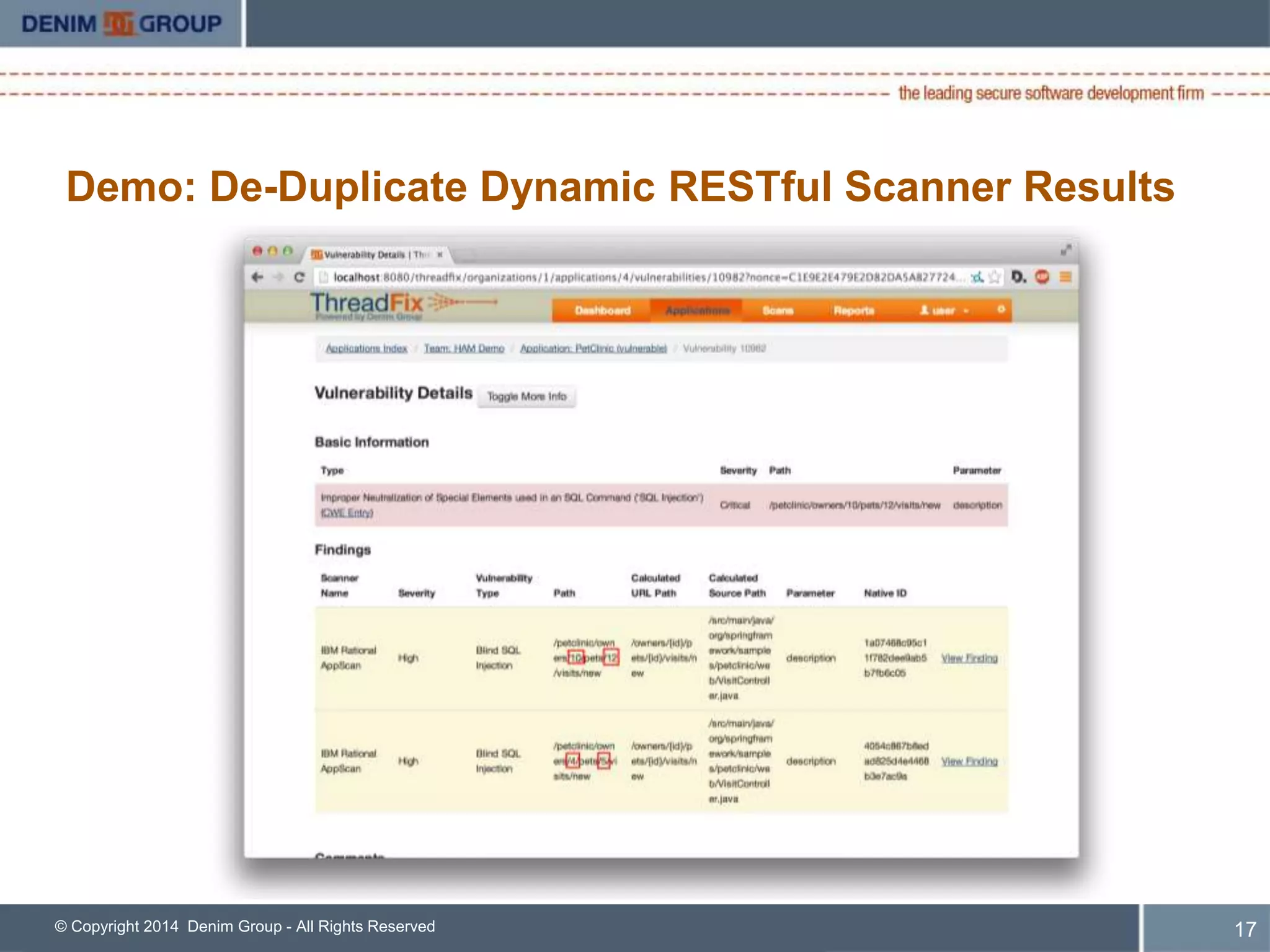
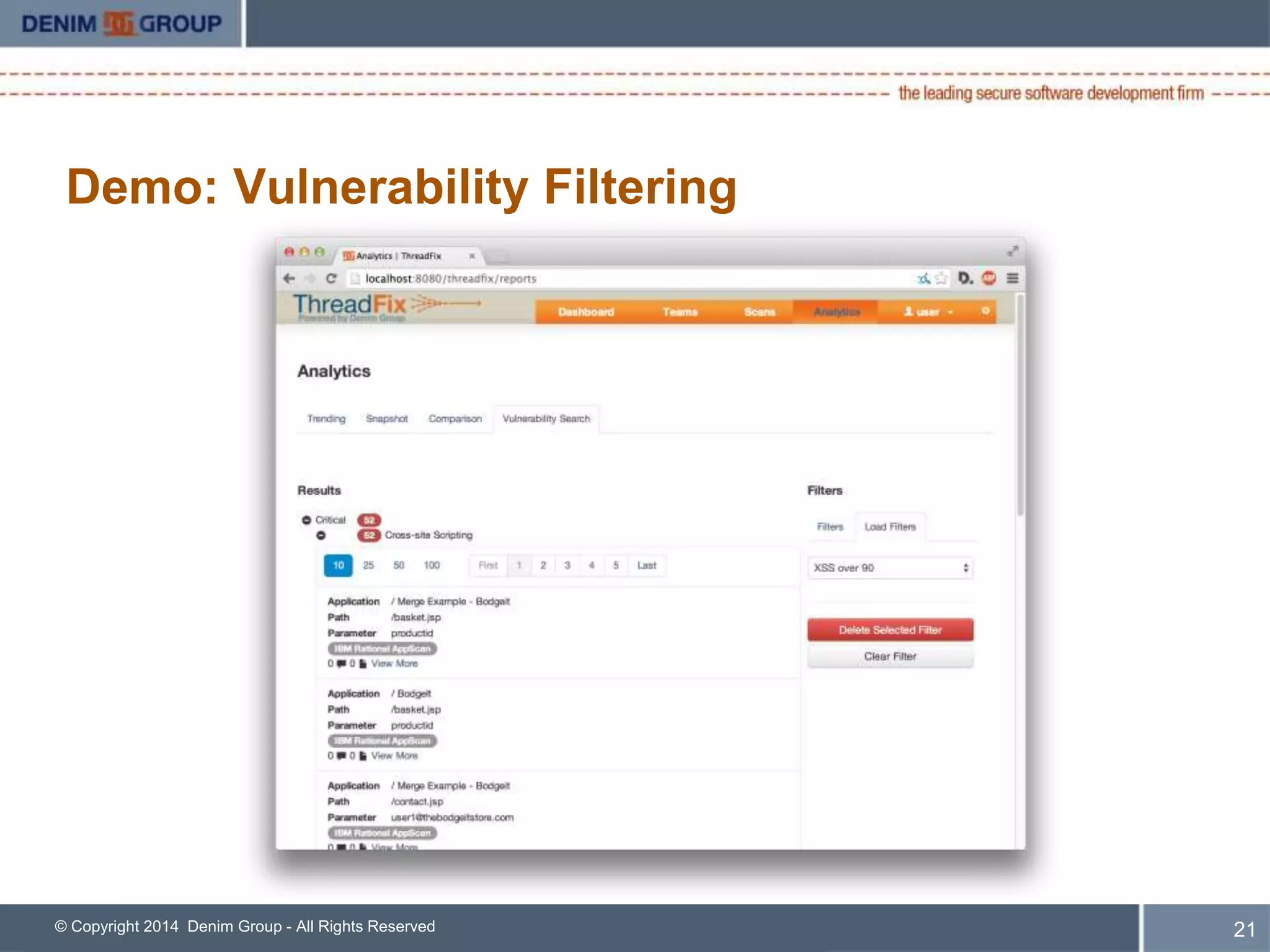
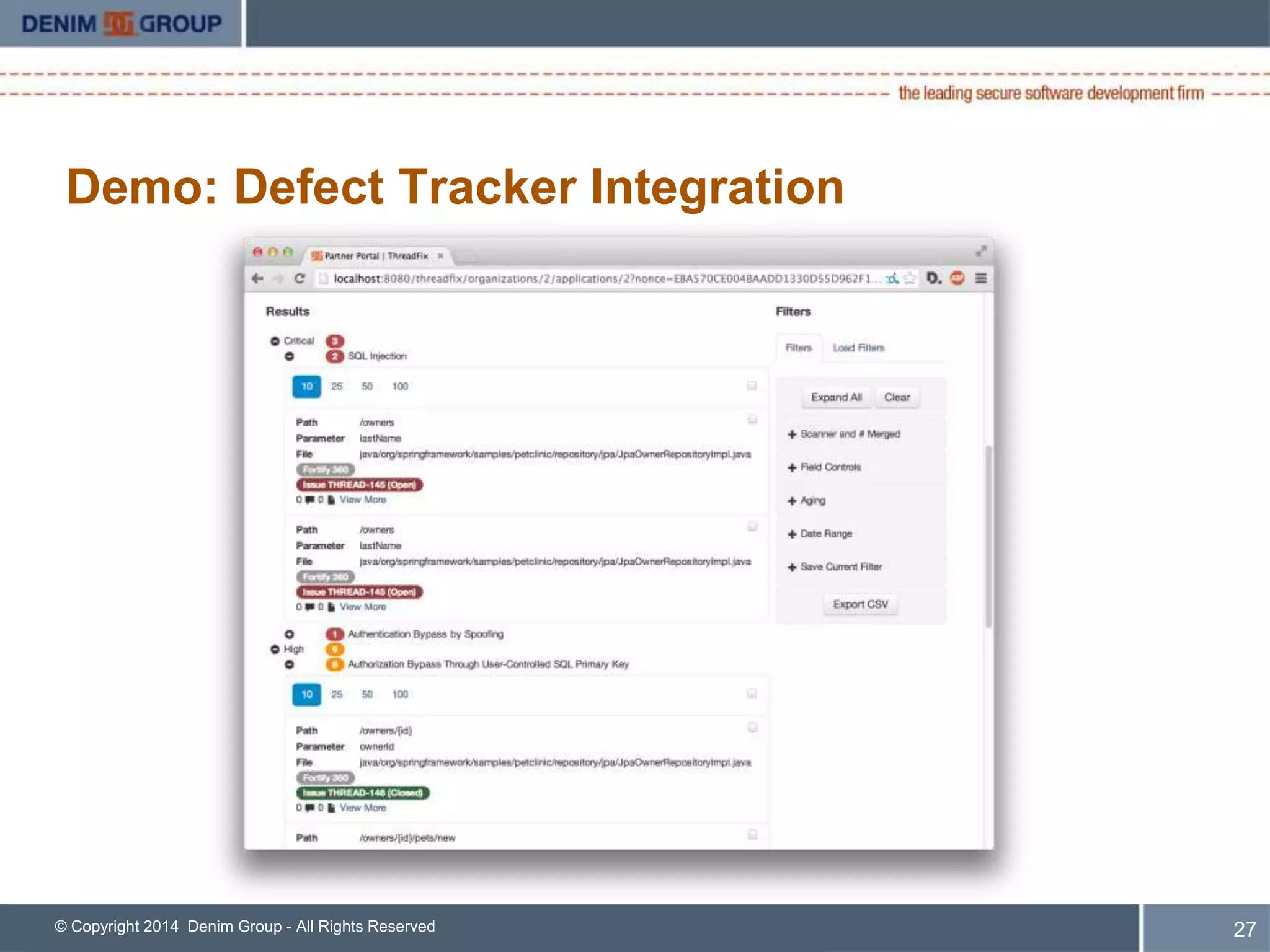
ThreadFix is an open source tool developed by Denim Group to help organizations manage application security programs. The presentation discusses new features in version 2.1 including support for additional vulnerability scanning tools and defect trackers. It demonstrates how ThreadFix consolidates scan results, merges findings across scanners, and maps vulnerabilities to defects in development tools to prioritize remediation. The speaker also outlines upcoming enhancements and how the enterprise version provides additional support and capabilities.