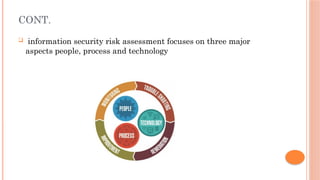
The document outlines the objectives and processes of vulnerability assessments and penetration testing, including key tasks such as risk assessment and remediation. It details various tools used for vulnerability assessment, such as Rapid7 InsightVM, Nessus, and QRadar Vulnerability Manager, while explaining the processes of both vulnerability assessment and penetration testing, along with their respective methodologies. Additionally, the document touches upon information security risk assessments, emphasizing the importance of identifying gaps in IT security architecture.