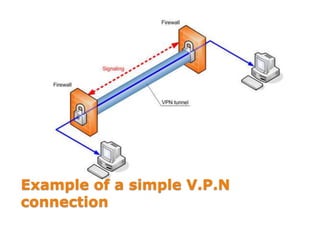
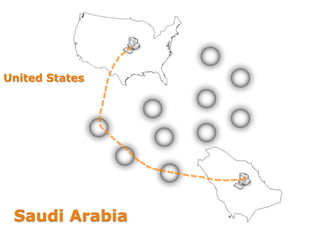
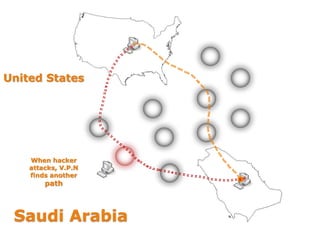
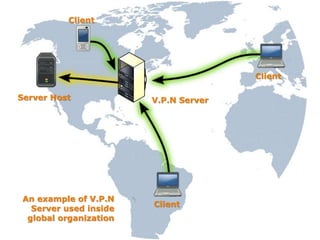
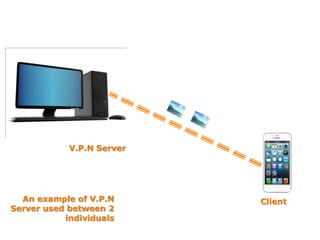
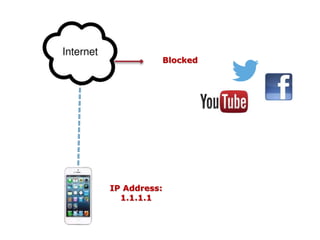
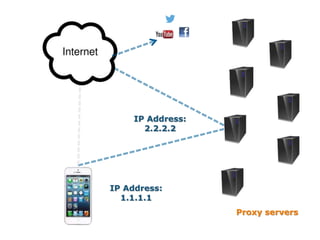
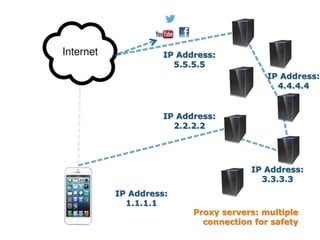
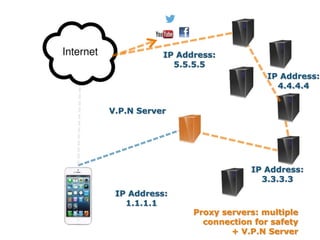
This document discusses VPN and proxy servers. It defines a VPN as enabling secure transmission of data across shared public networks as if directly connected to a private network. A proxy server allows indirect network connections and is used for anonymously accessing blocked websites and removing online surveillance. Both VPNs and proxy servers can improve security, but VPNs find alternative routes when attacked and encrypt transmitted files, while proxy servers may slow connection speeds and be tracked by governments. Care should be taken in choosing servers to avoid theft of information or transmission of viruses.