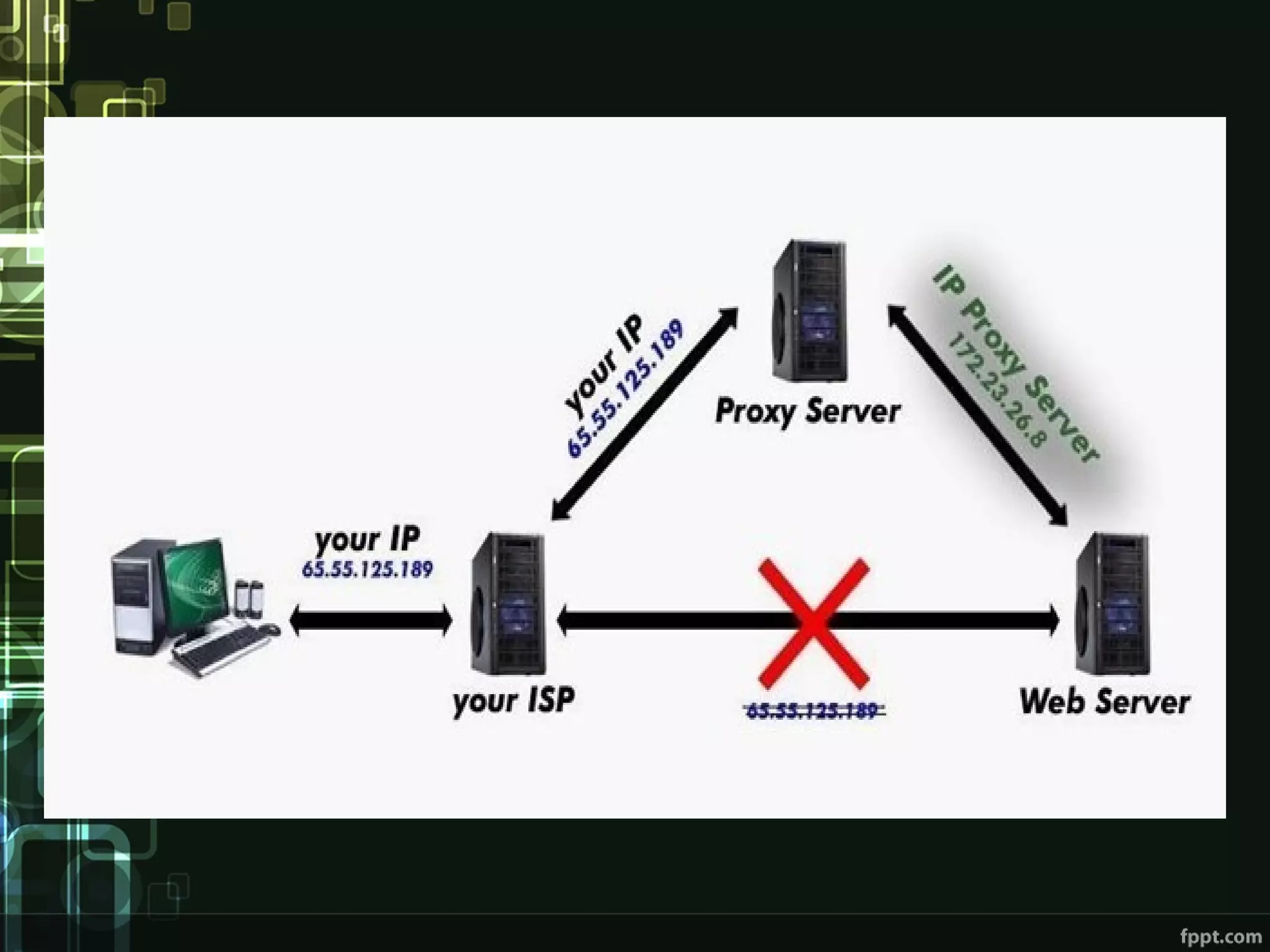
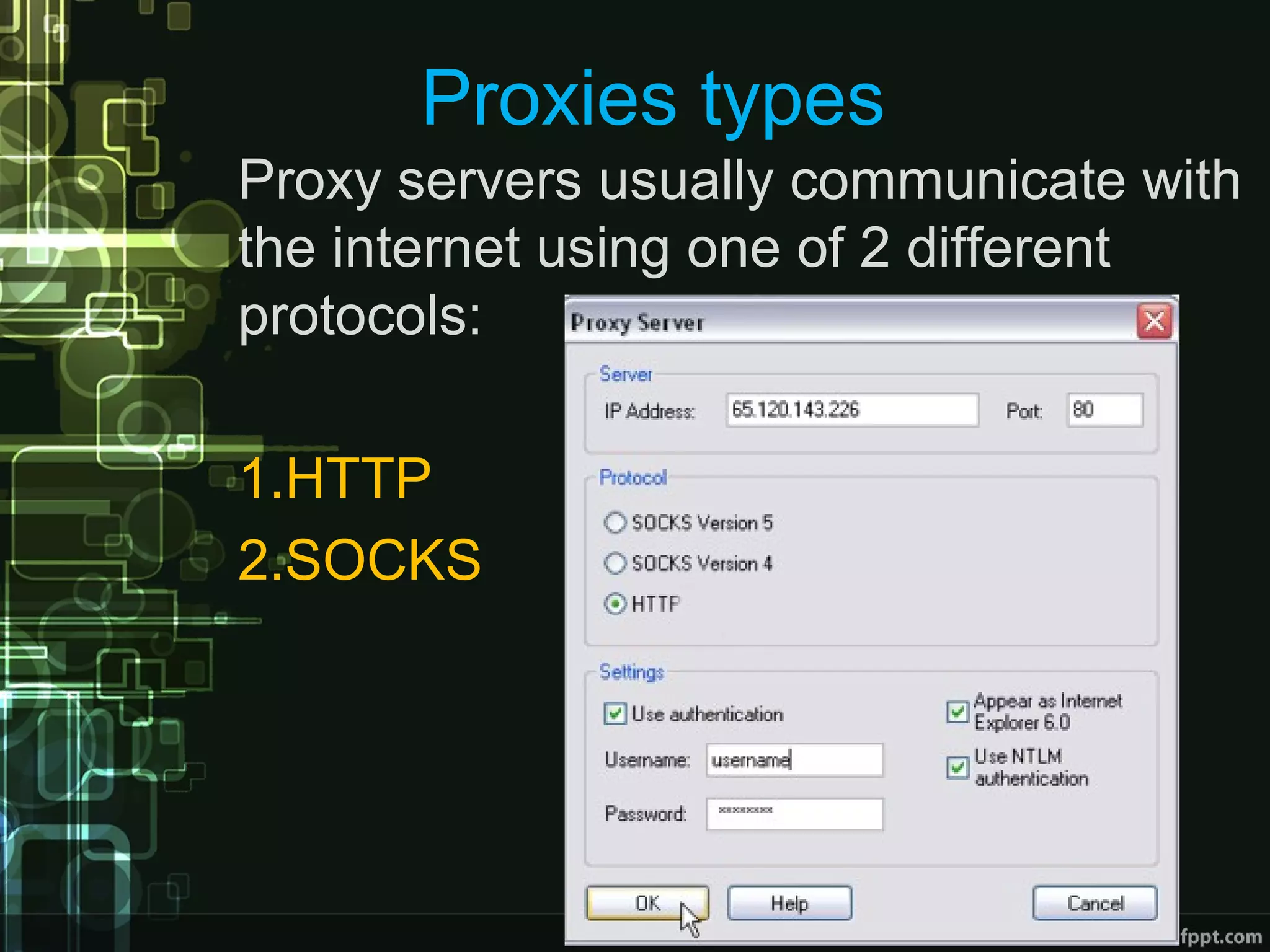
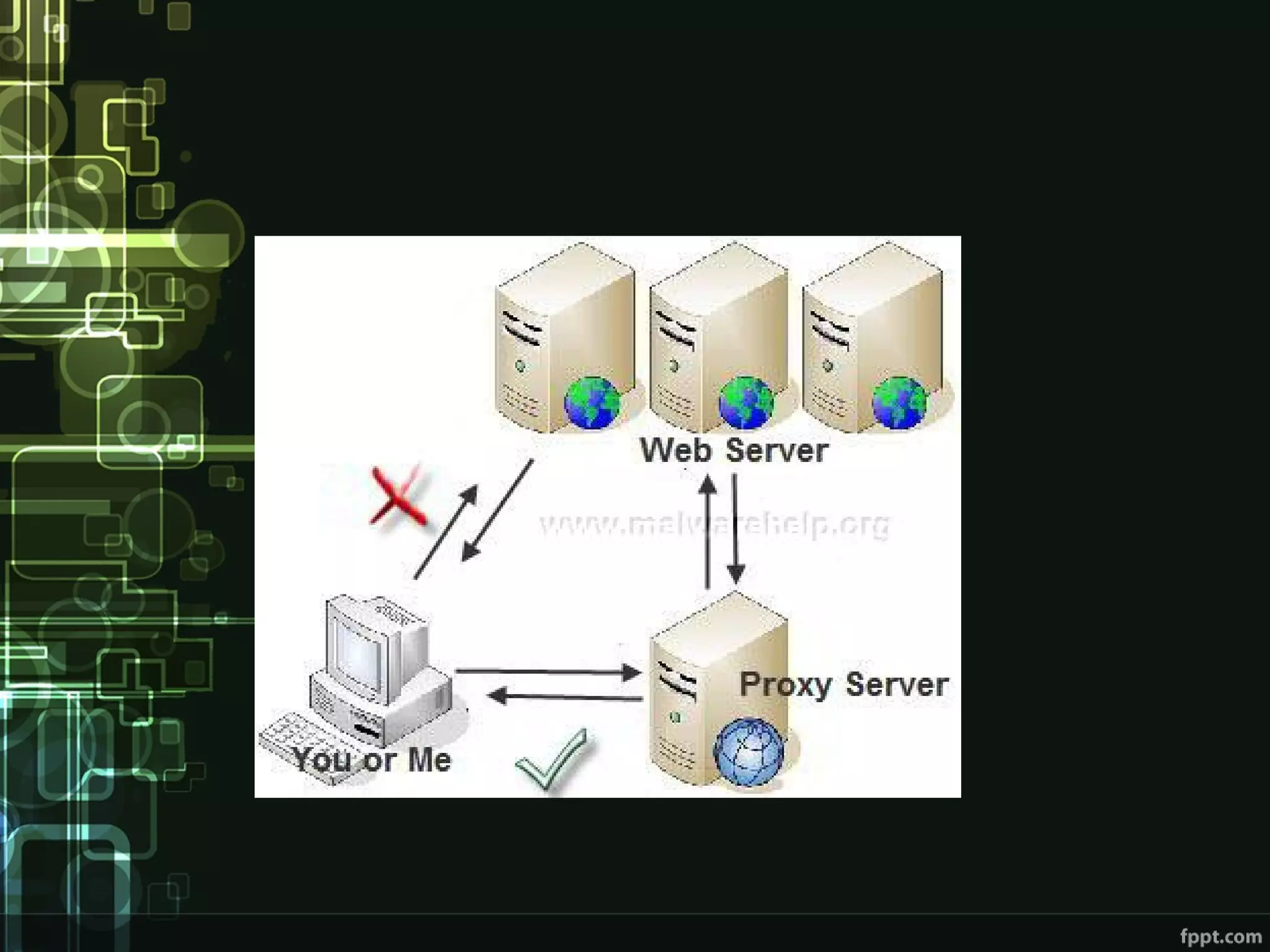
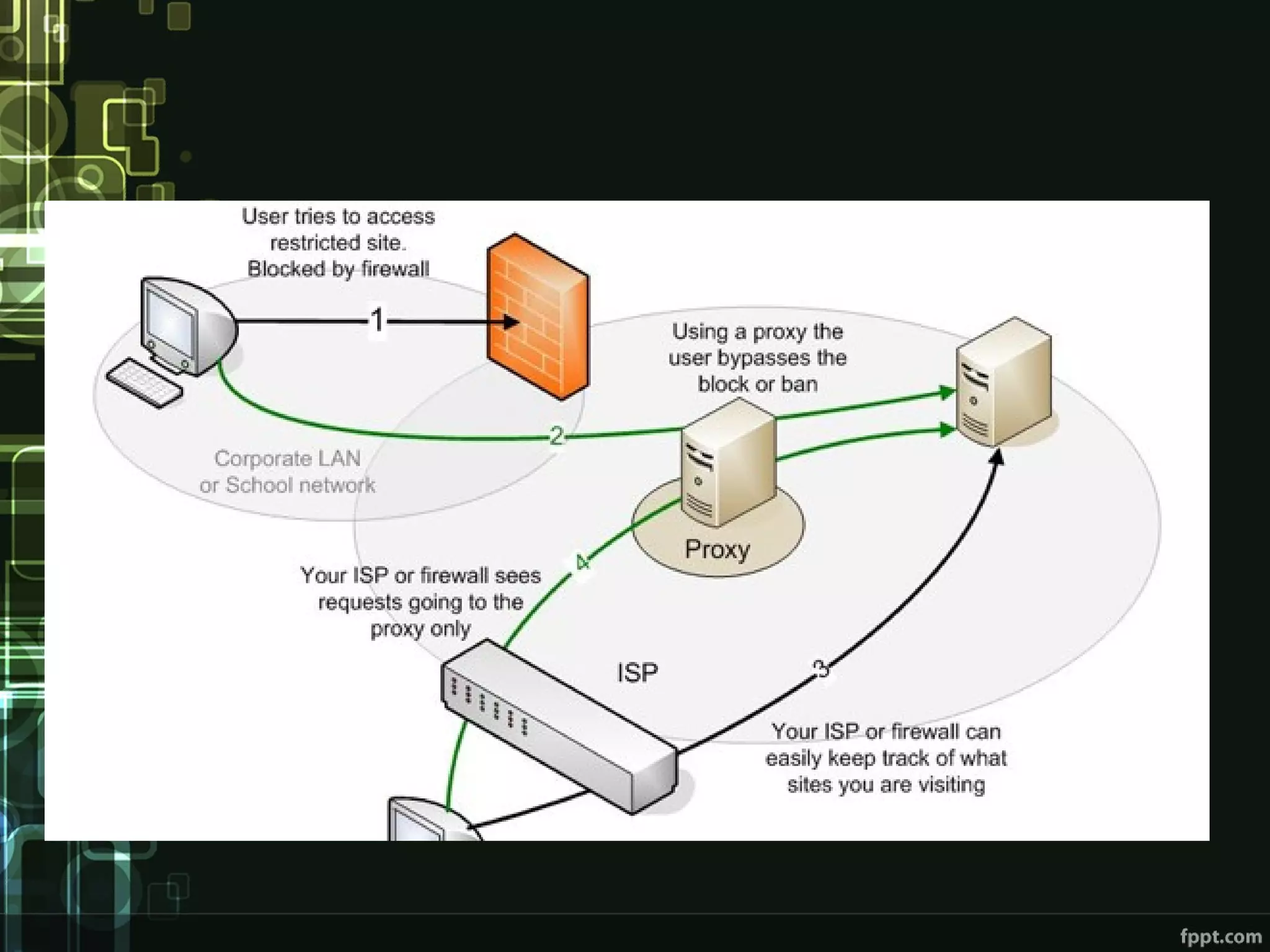
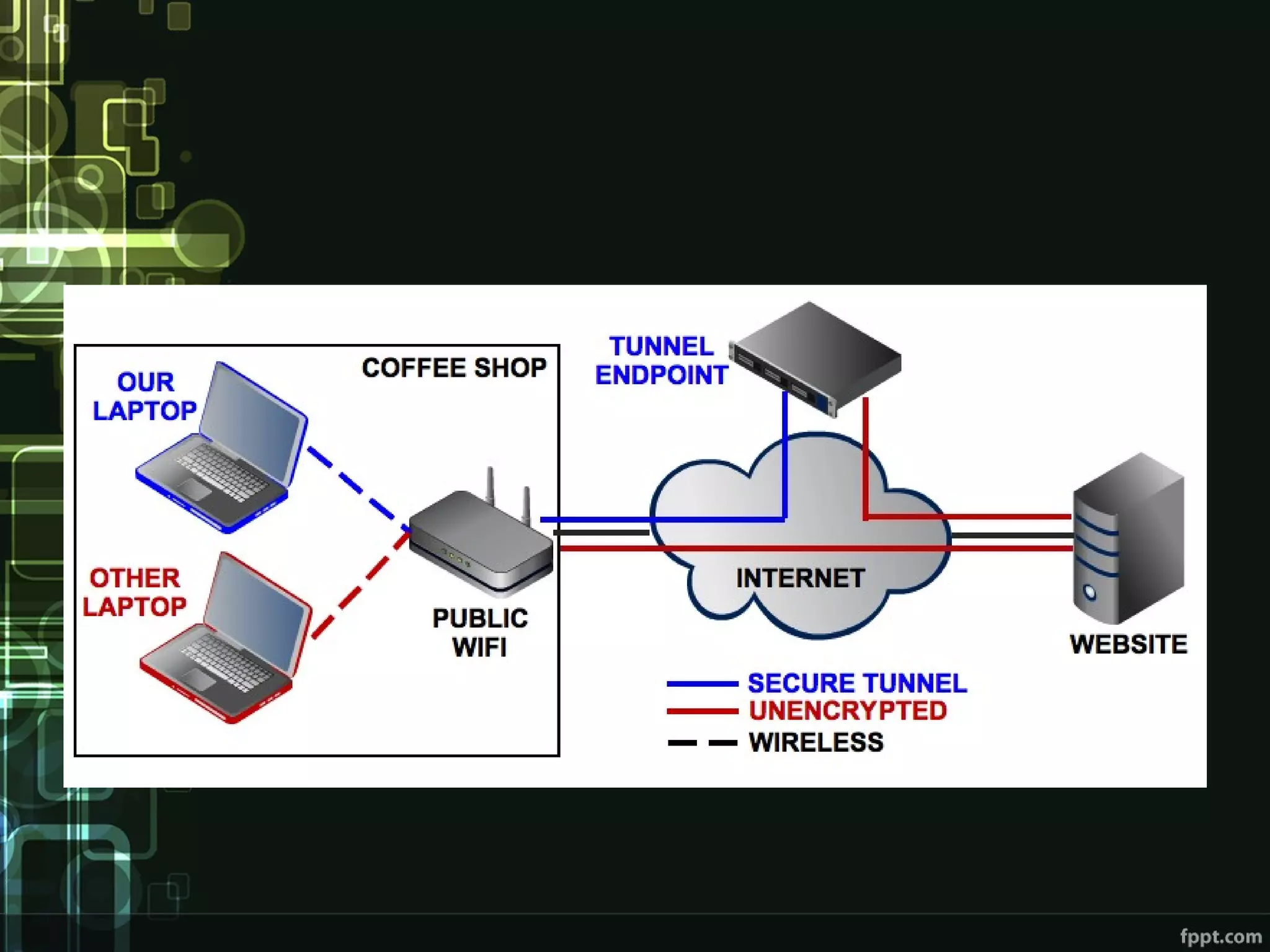
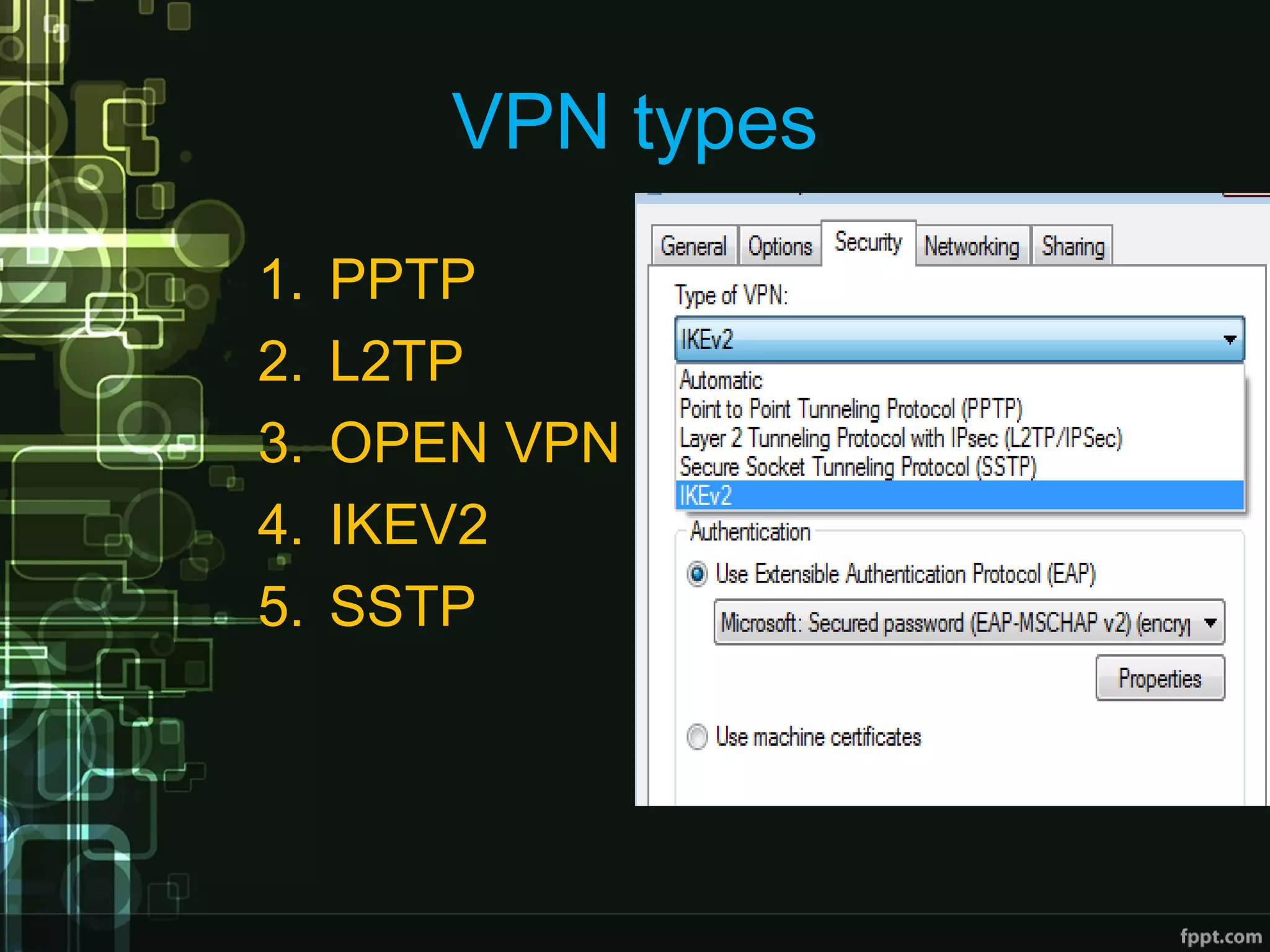
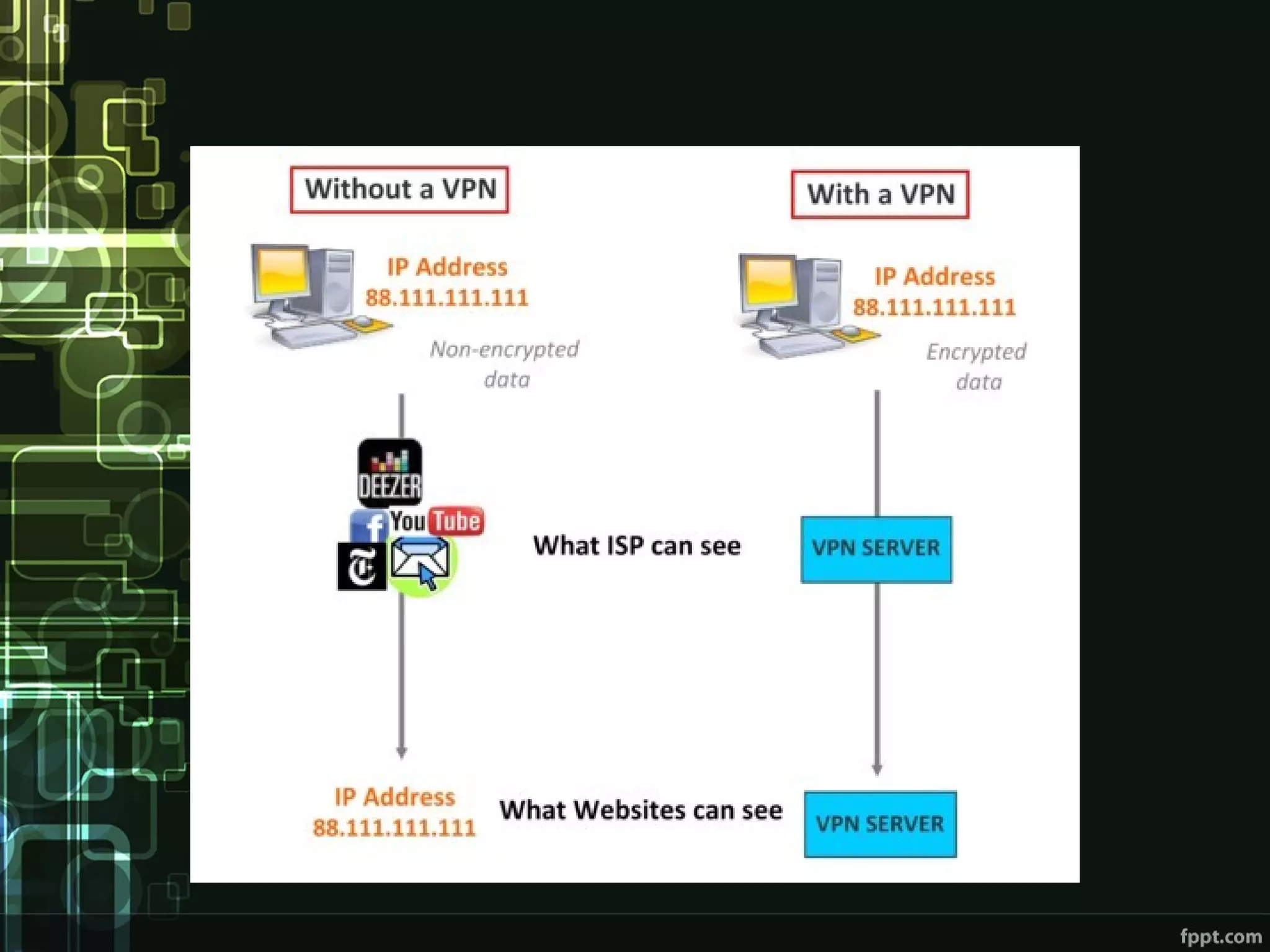
This document compares proxies and VPNs. Proxies act as intermediaries between a user's device and the internet and do not encrypt traffic, while VPNs create an encrypted tunnel protecting a user's online activity and hiding their IP address. The document outlines the advantages and disadvantages of HTTP, SOCKS, and various VPN protocols. It concludes that while proxies are cheaper, VPNs provide superior anonymity and security by encrypting all internet activity.