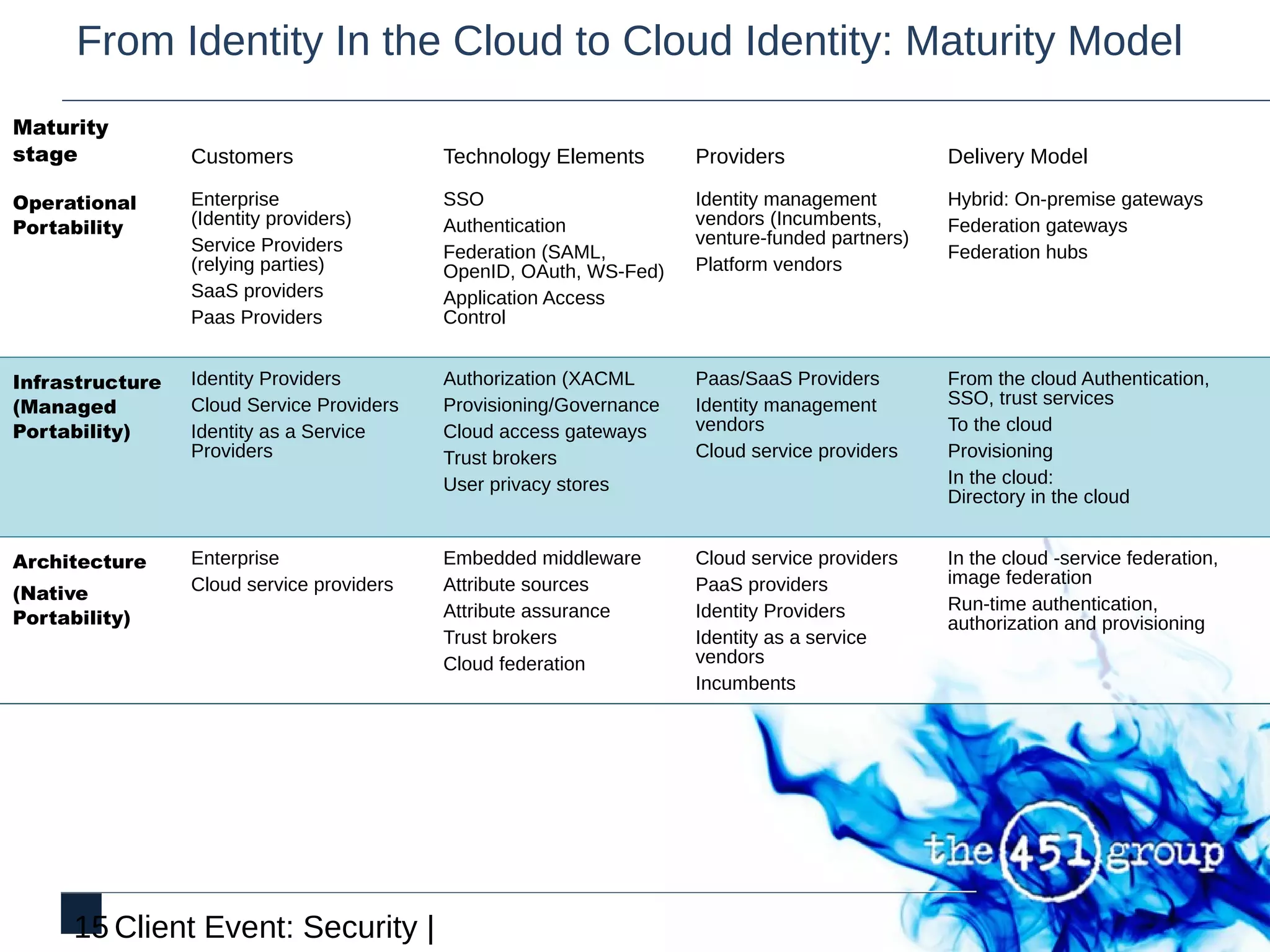
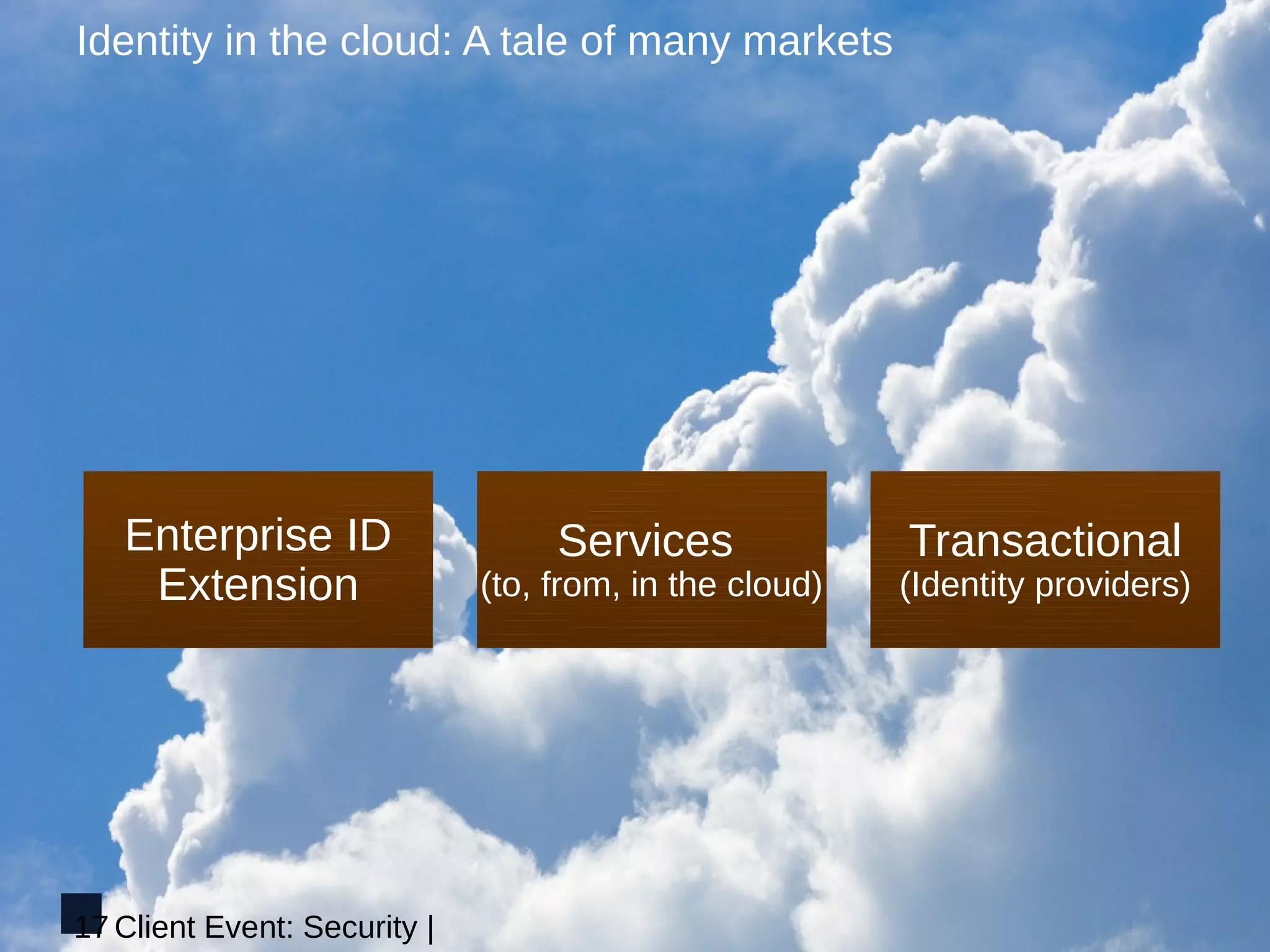
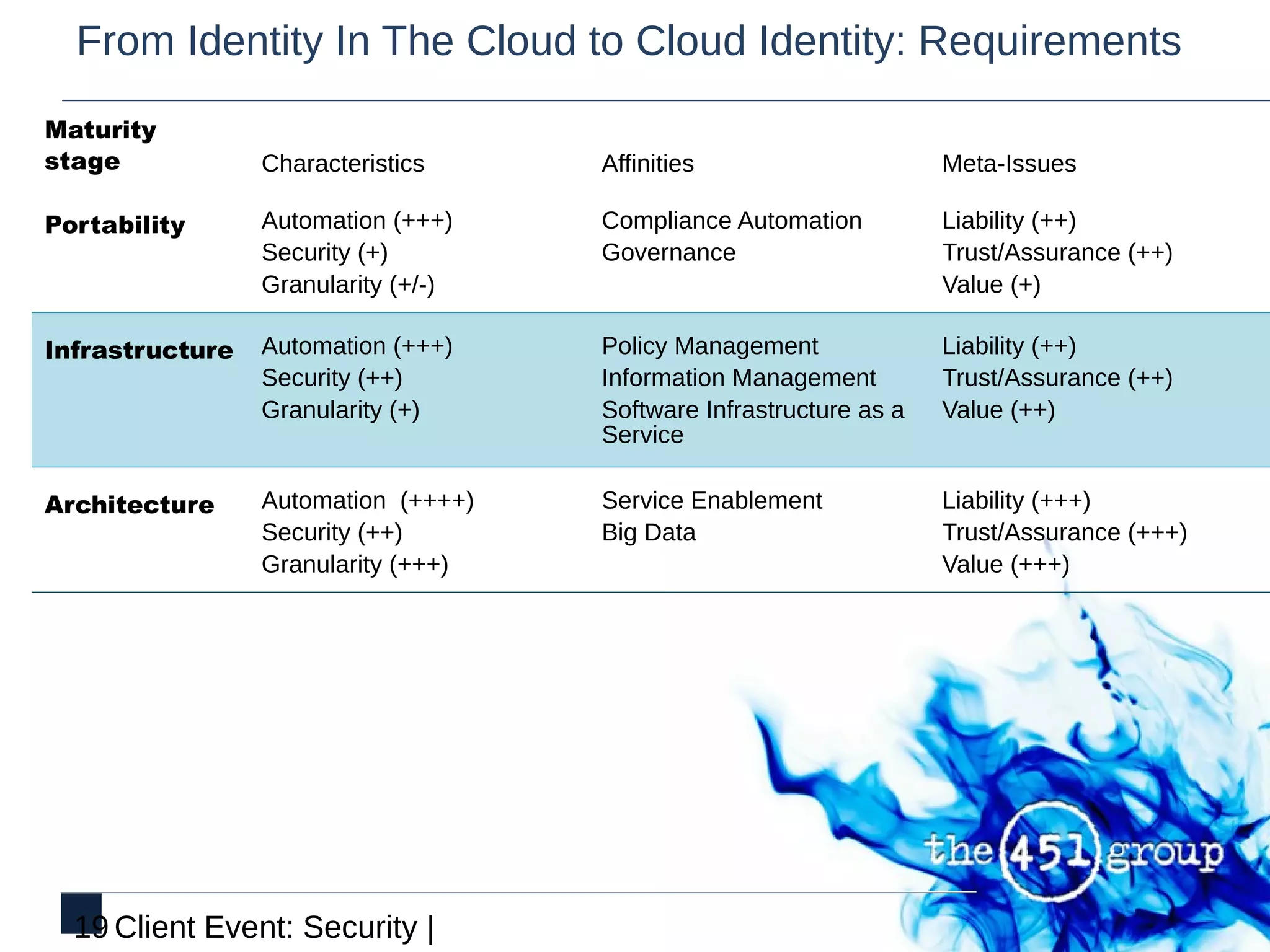
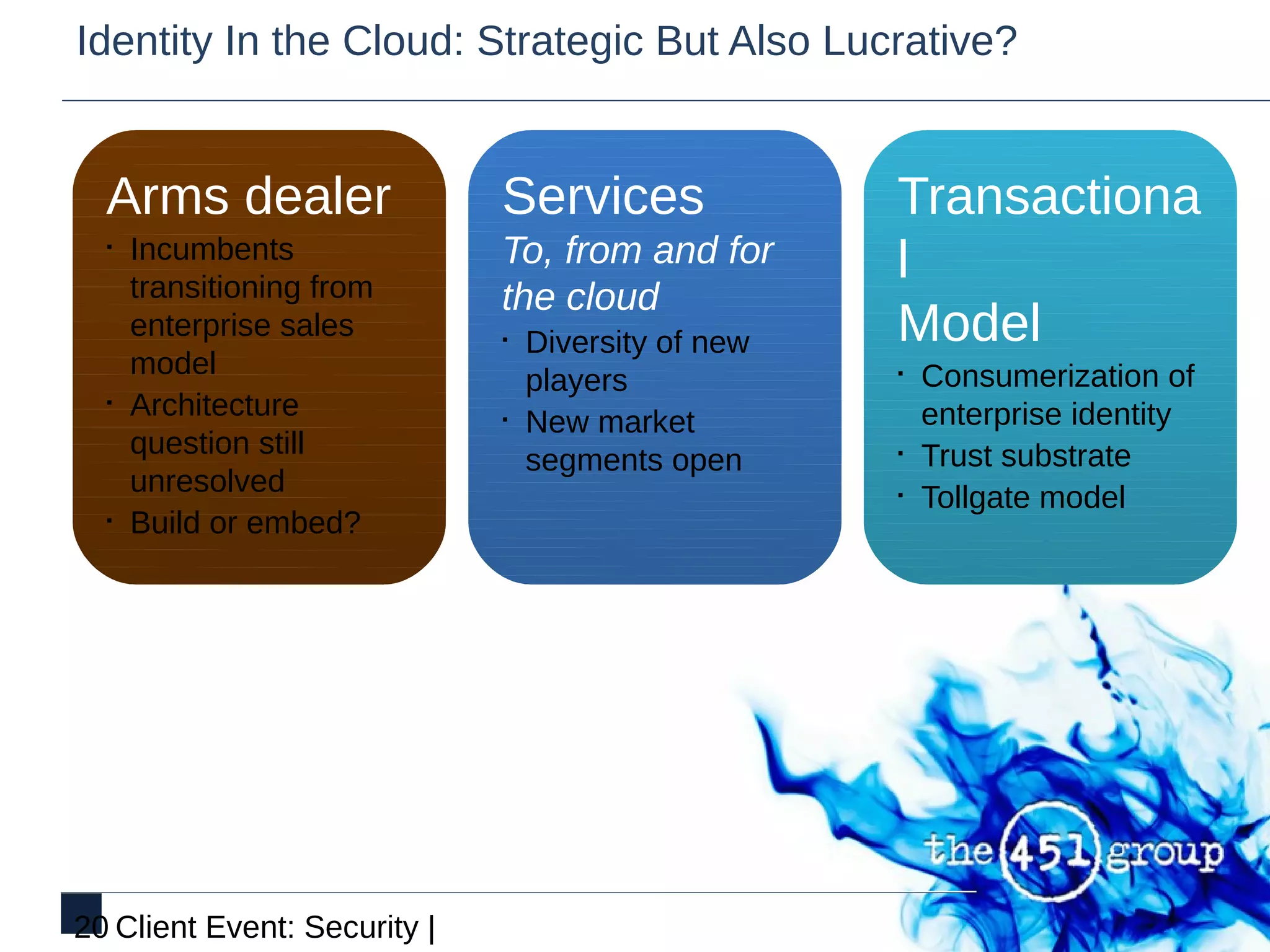
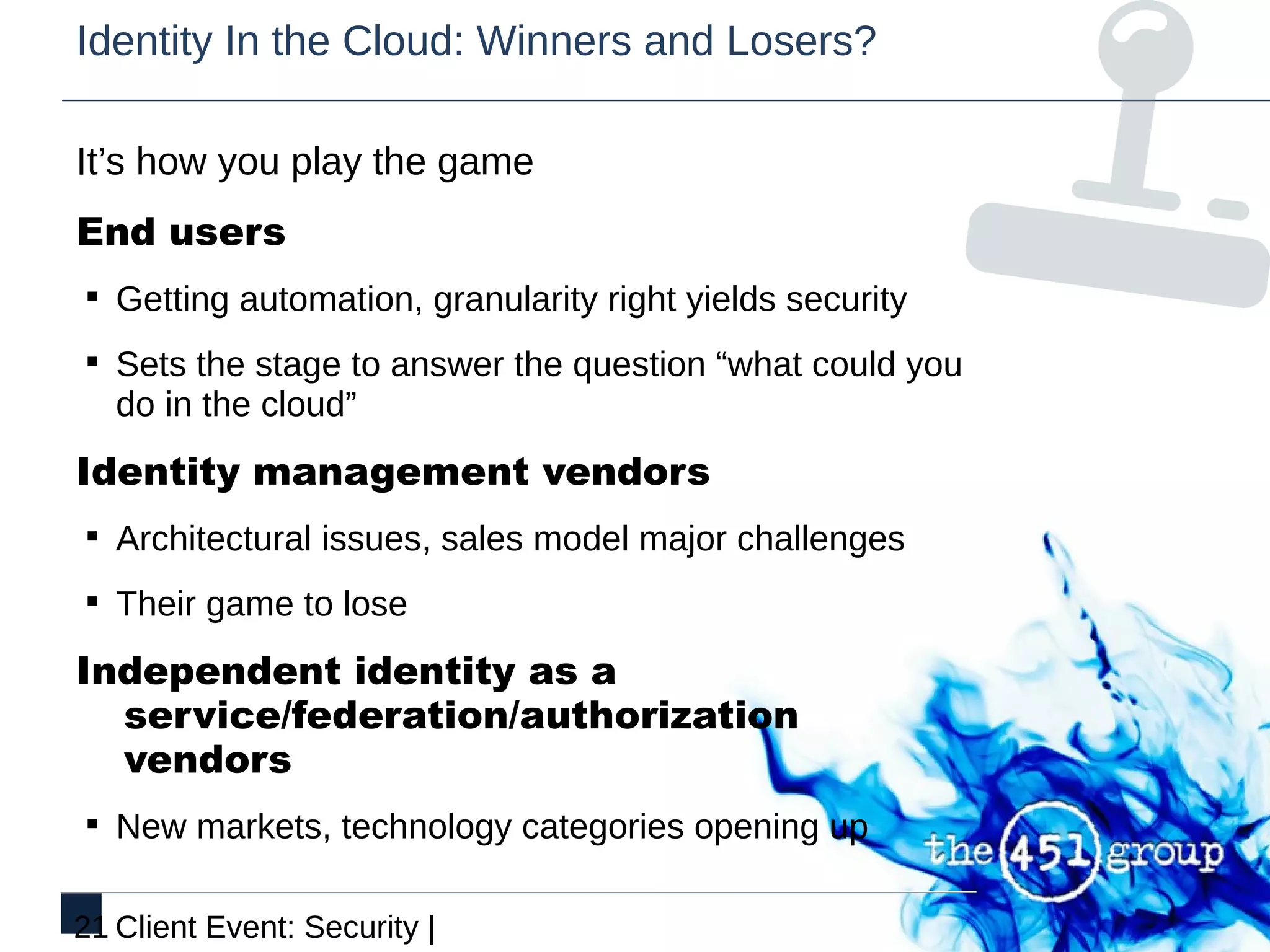
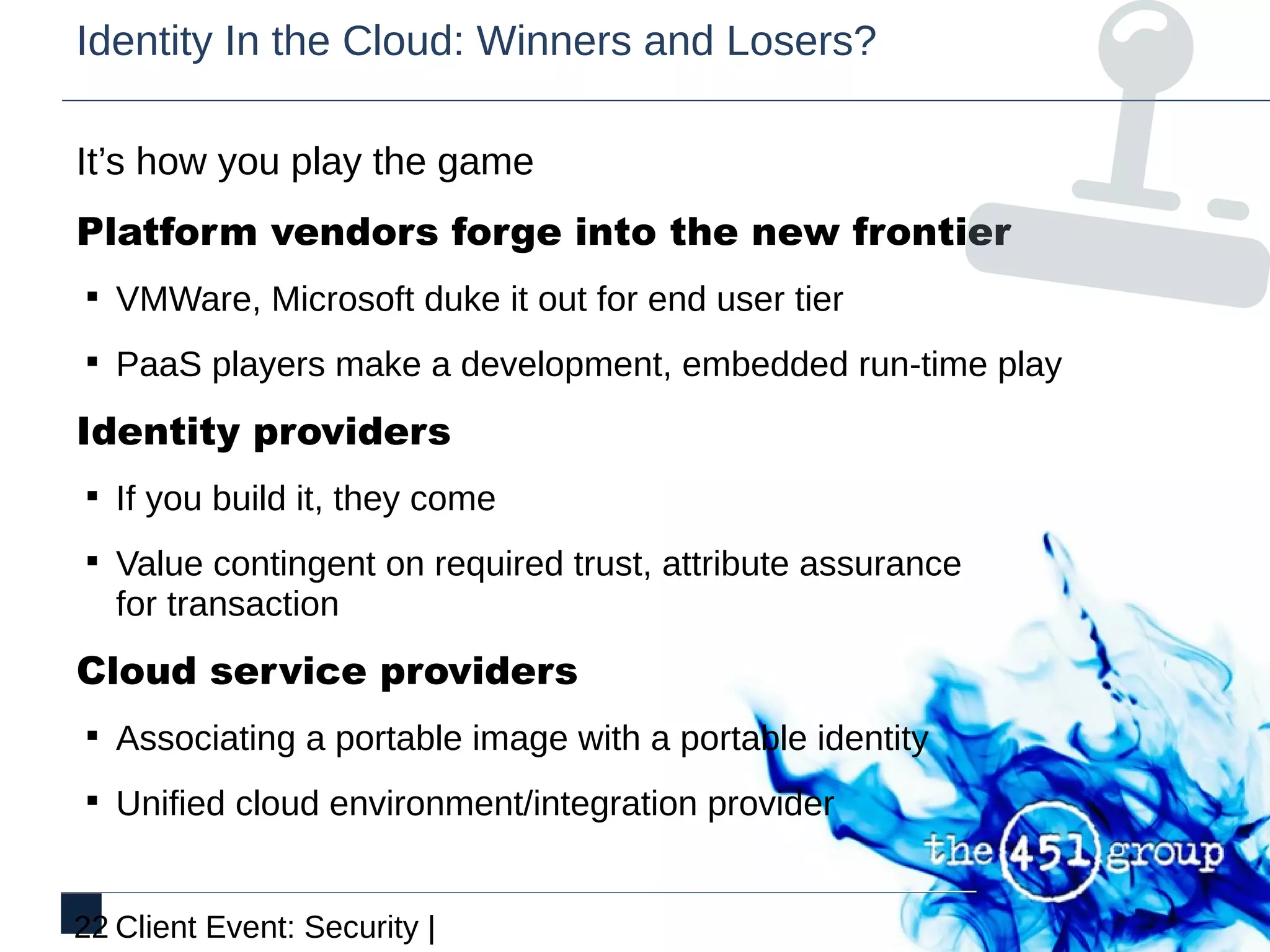
This document discusses identity and security in discontinuous cloud infrastructure. It outlines an agenda covering what identity means in the cloud, cloud security models from an identity and access management perspective, and how security models relate to compliance. The document also discusses how cloud, security and identity intersect, the transition from identity in the cloud to cloud identity, and the opportunity around identity in the cloud.