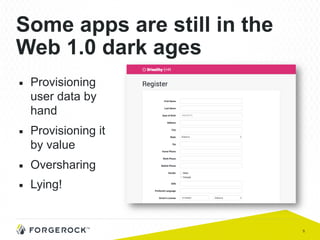
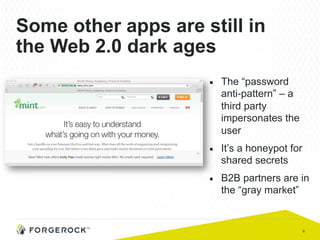
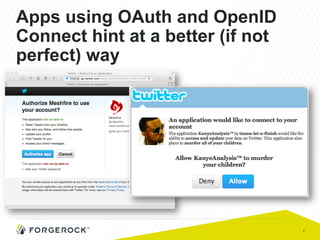
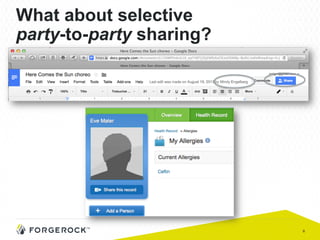
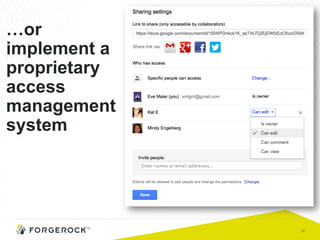
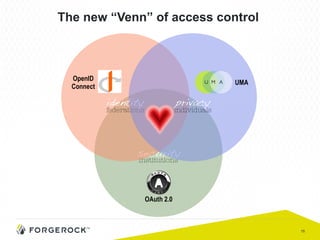
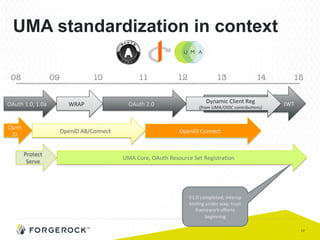
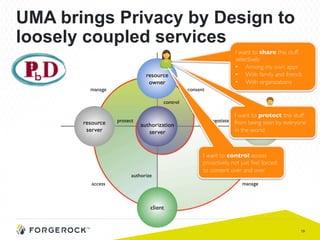
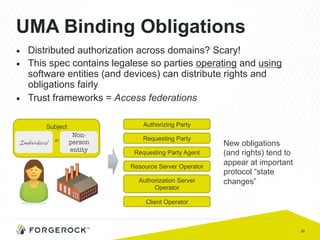
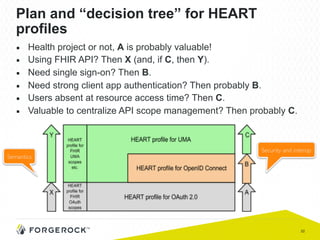
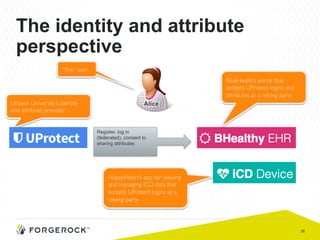
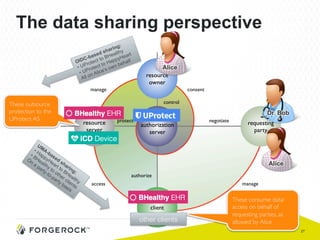
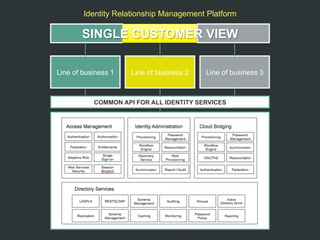
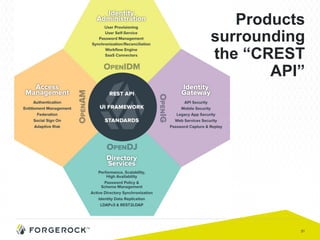
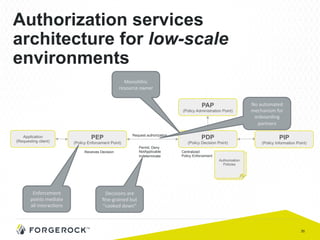
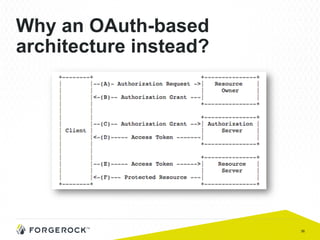
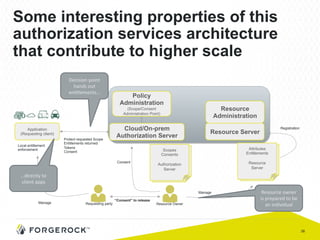
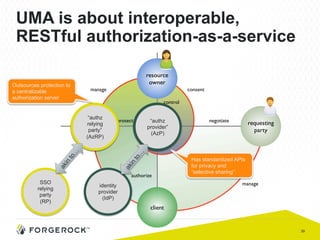
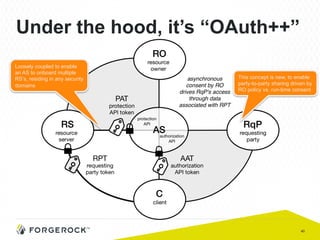
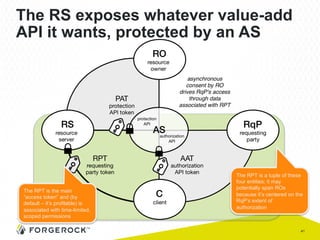
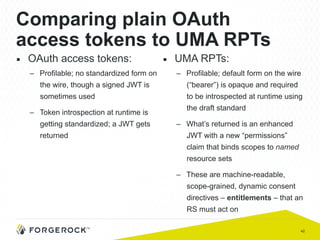
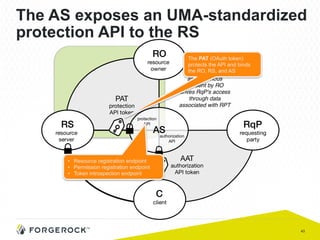
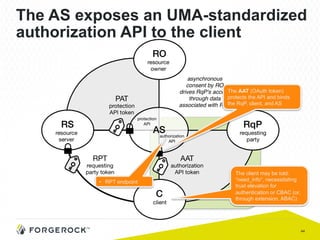
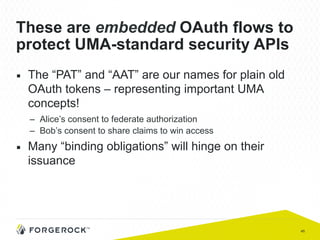
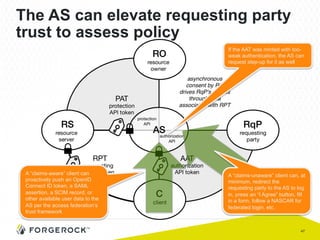
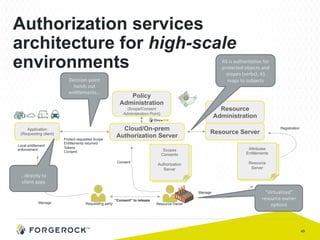
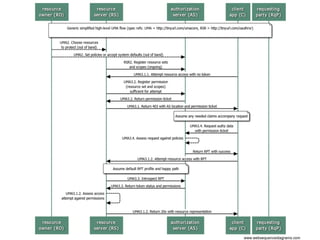
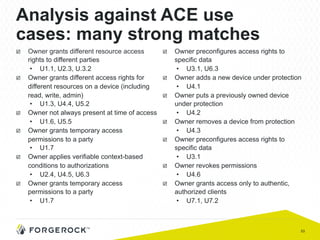
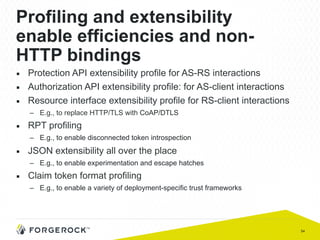
The document discusses the implementation of user-managed access (UMA) and its role in enhancing digital identity and privacy through lightweight access control protocols. It emphasizes the challenges of personal data sharing and the importance of robust security and privacy measures in delegated authorization scenarios. UMA aims to empower users with selective sharing capabilities while maintaining control over their personal data across various applications and services.