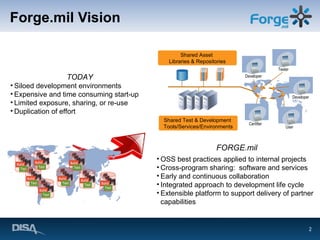
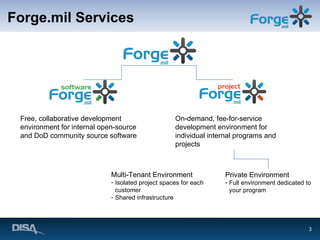
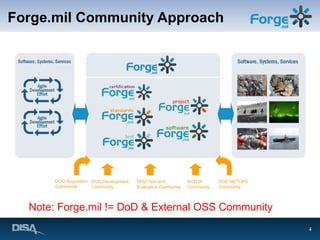
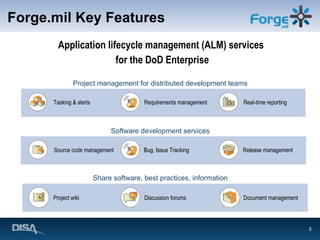
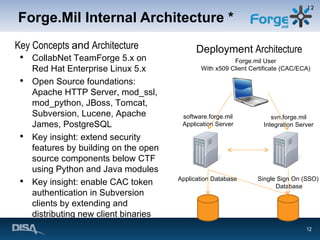
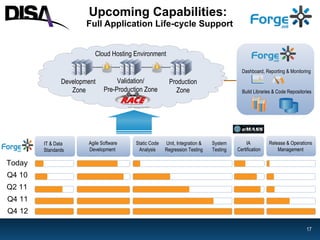
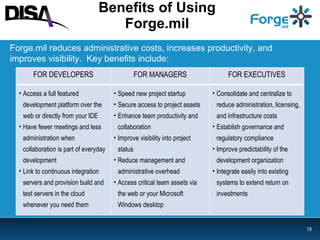
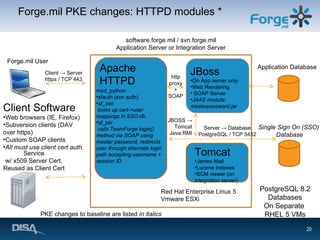
Forge.mil is a collaborative software development platform that aims to overcome siloed development, reduce duplication of effort, and enable cross-program sharing of software and services. It provides application lifecycle management services and tools for collaborative development within a shared, multi-tenant environment for Department of Defense programs and partners. Forge.mil has grown to support over 2700 software releases from various DoD projects across different services since its initial launch in 2009.
![Forge.mil – DoD Collaborative Software Development Guy Martin, Forge.mil Community Manager [email_address] Richard Bullington-McGuire, Director, Technology [email_address] IT Innovators Award](https://image.slidesharecdn.com/introductiontoforgemil-nasa-oss-110329122456-phpapp02/75/2011-NASA-Open-Source-Summit-Forge-mil-1-2048.jpg)