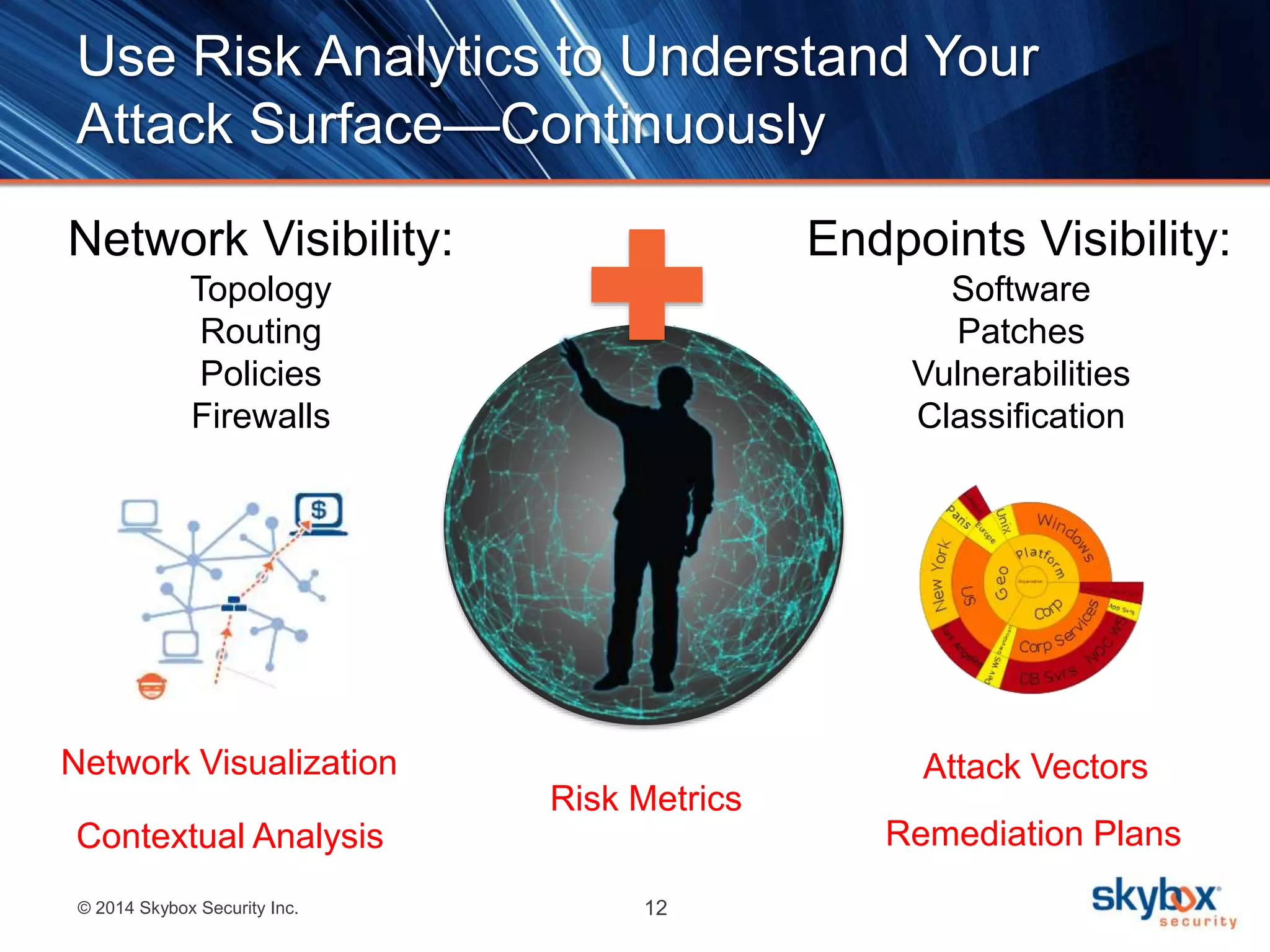
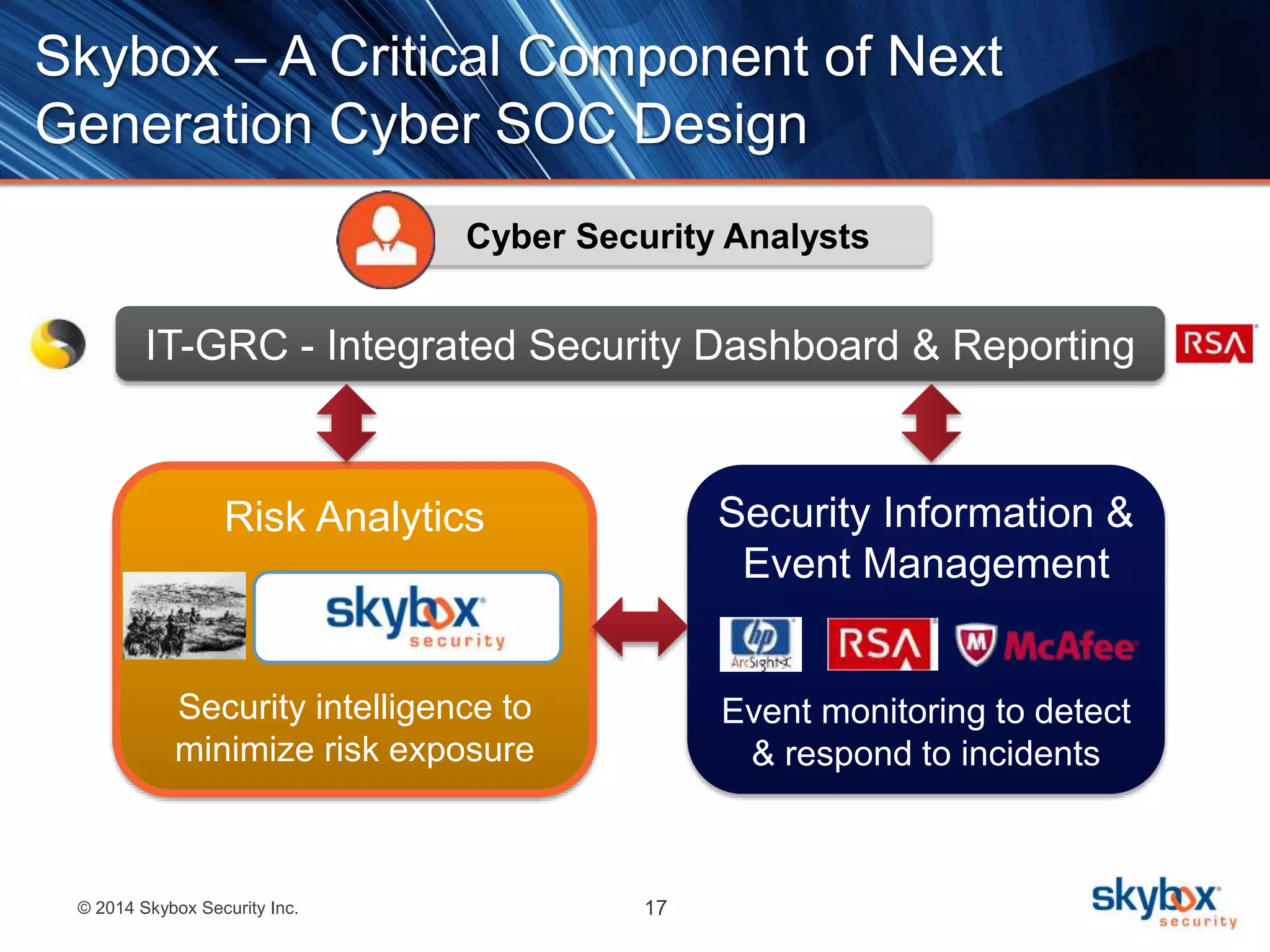
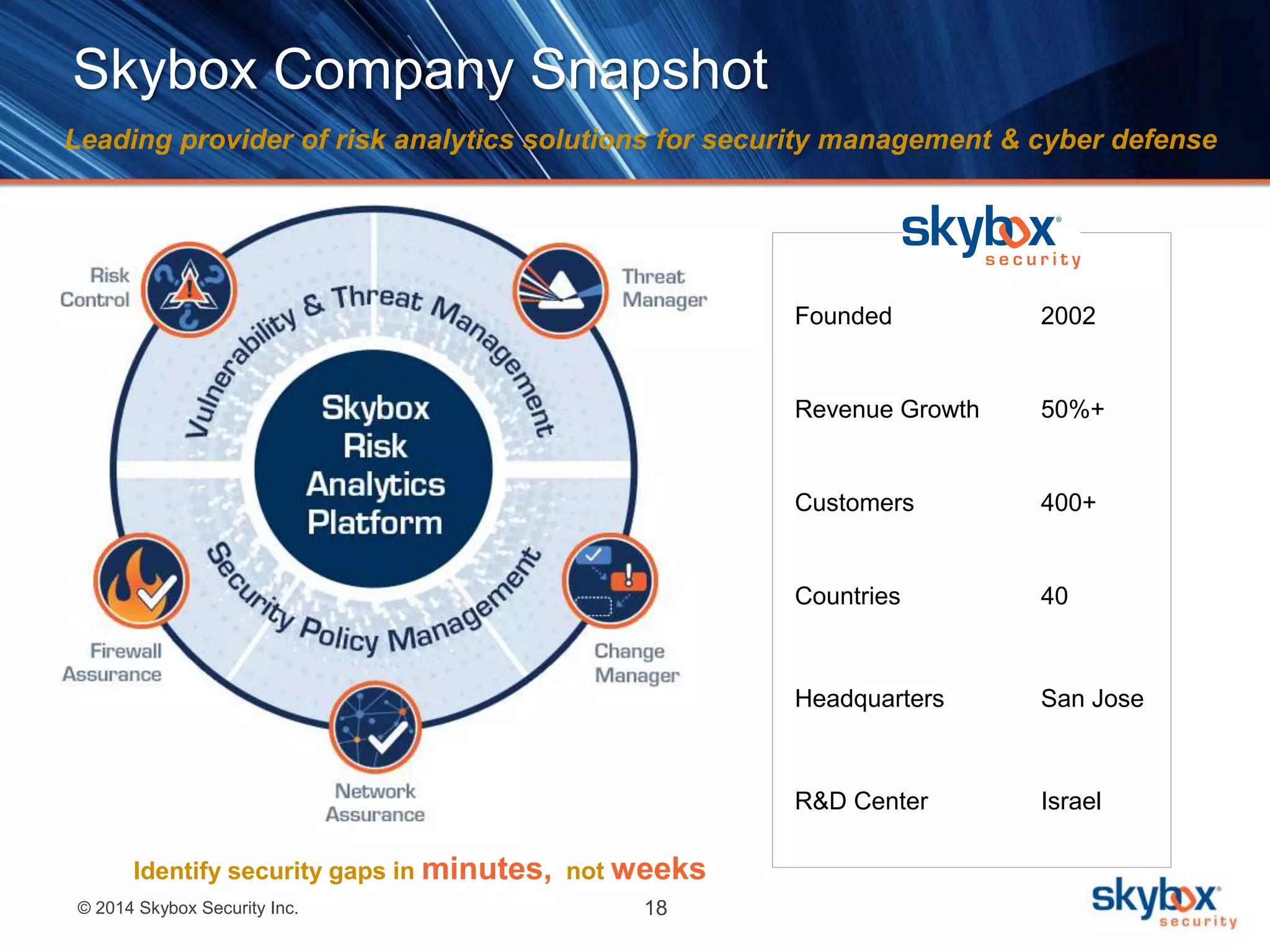
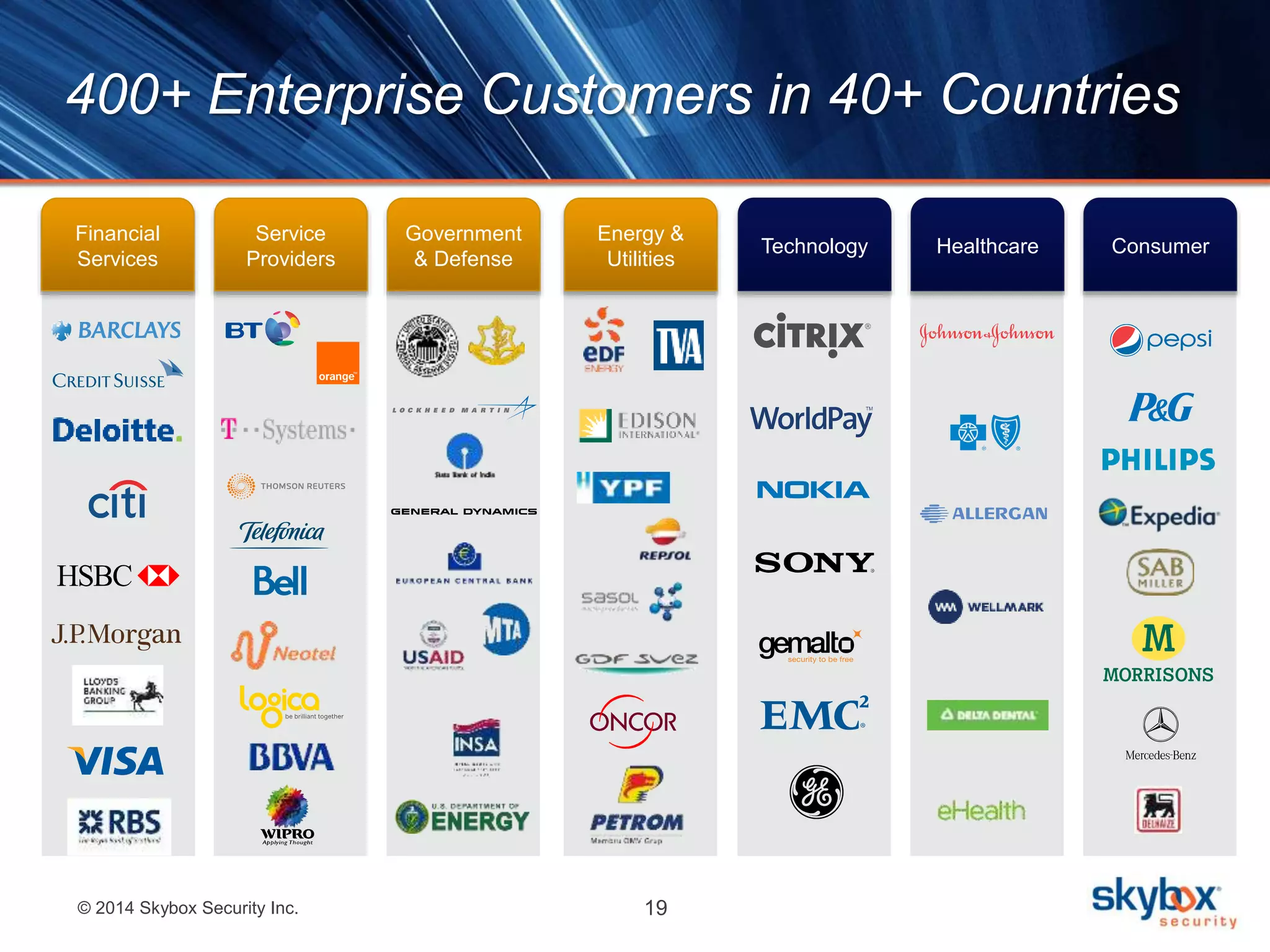
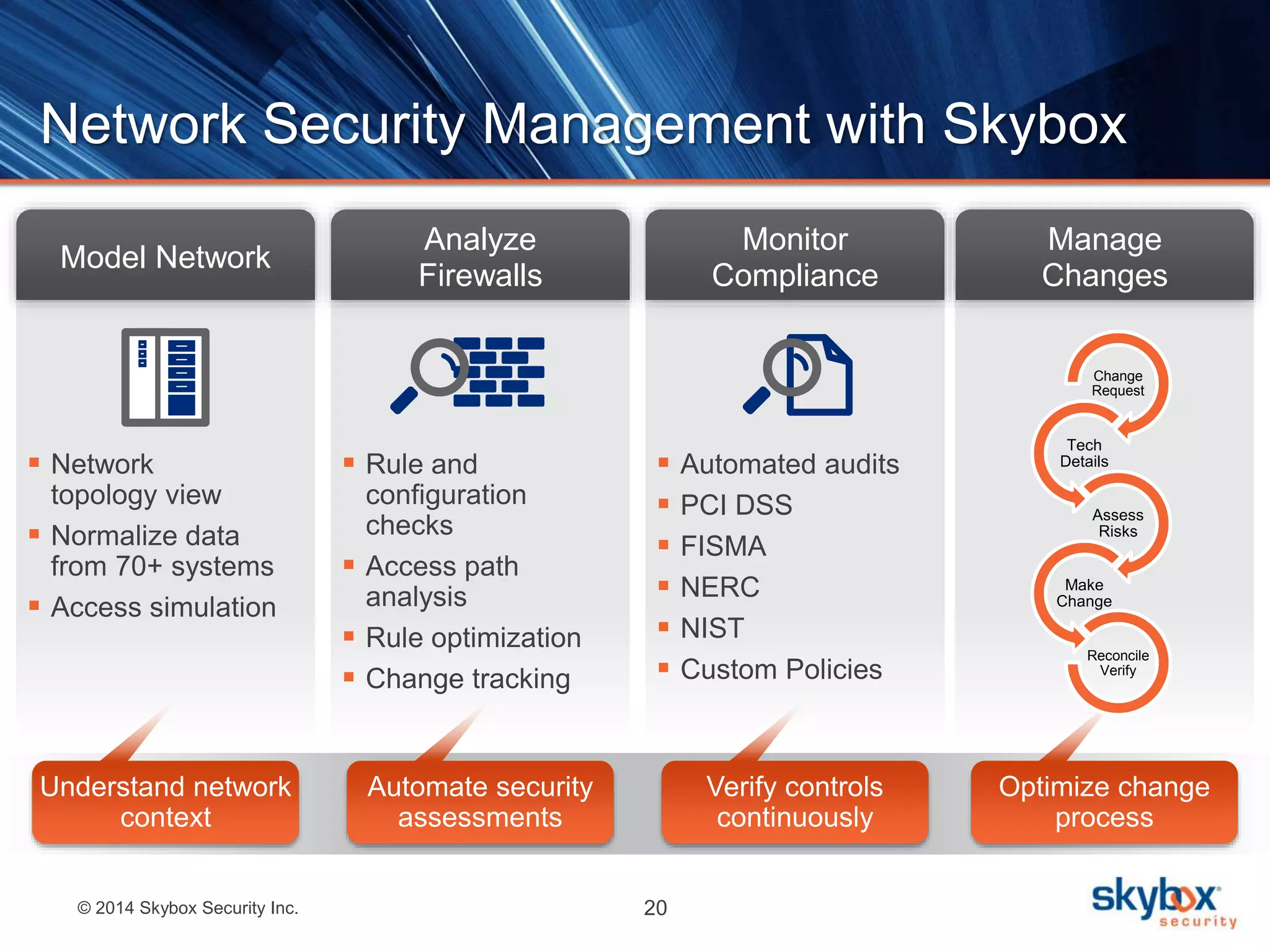
The document discusses the challenges of cybersecurity management and highlights the need for risk analytics to better understand and mitigate cyber threats. It includes statistics about cyber incidents, emphasizes the importance of visibility and compliance, and presents Skybox Security's capabilities in helping organizations manage their security risks effectively. The agenda features a live demo and concludes with insights on the integration of data for enhanced security measures.